How the OSI Model Works
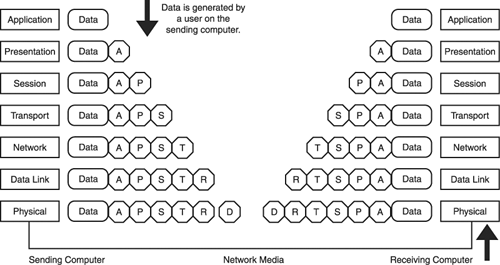
| The model actually is used to describe how data that's generated by a user , such as an email message, moves through a number of intermediary forms until it is converted into a stream of data that can actually be placed on the network media and sent out over the network. The model also describes how a communication session is established between two devices, such as two computers, on the network. Because other types of devices, such as printers and routers, can be involved in network communication, devices (including computers) on the network are actually referred to as nodes . Therefore, a client computer on the network or a server on the network would each be referred to as a node . When data is sent by a network node (for example, a computer sending an email message, as already mentioned), that data moves down through the OSI stack and then is transmitted over the network media. When the data is received by a node, such as another computer on the network, it moves up through the OSI stack until it is again in a form that can be accessed by a user on that computer. As you already saw in Table 5.1, each of the layers in the OSI model is responsible for certain aspects of getting user data into a format that can be transmitted on the network. Some layers are also for establishing and maintaining the connection between the communicating nodes, and other layers are responsible for the addressing of the data so that it can be determined where the data originated (on which node) and where the data's destination is. An important aspect of the OSI model is that each layer in the stack provides services to the layer directly above it. Only the Application layer, which is at the top of the stack, would not provide services to a higher-level layer. The process of moving user data down the OSI stack on a sending node (again, such as a computer) is called encapsulation . The process of moving raw data received by a node up the OSI stack is referred to as de-encapsulation . To encapsulate means to enclose or surround, and this is what happens to data that is created at the Application layer and then moves down through the other layers of the OSI model. A header, which is a segment of information affixed to the beginning of the data, is generated at each layer of the OSI model, except for the Physical layer. This means that the data is encapsulated in a succession of headersfirst the Application layer header, then the Presentation layer header, and so on. When the data reaches the Physical layer, it is like a candy bar that has been enclosed in several different wrappers. When the data is transmitted to a receiving node, such as a computer, the data travels up the OSI stack and each header is stripped off of the data. First, the Data Link layer header is removed, then the Network layer header, and so on. Also, the headers are not just removed by the receiving computer; the header information is read and used to determine what the receiving computer should do with the received data at each layer of the OSI model. It is by using these headers that the sending computer is able to communicate with the receiving computer and provide the receiving computer with either information or actual instructions related to the disposition of the data at the various levels of the OSI model. Using the candy bar analogy again, the situation on the receiving computer would be like opening a candy bar enclosed in many layers of wrapping, with each individual wrapper providing important instructions on how to unwrap the candy further and eventually eat the candy bar. Figure 5.2 provides a diagram of the encapsulation and de-encapsulation processes. The header information supplied at each layer of the OSI model by the sending computer will be used by the receiving computer as it massages the data into a format that can actually be accessed by a user on that computer. Figure 5.2. Data is encapsulated on the sending computer and then de-encapsulated on the receiving computer. One thing you should keep in mind as you review the different functions of the layers in the OSI model is that there are real protocols found in real network protocol stacks that actually perform the functions that we discuss in the sections that follow. Later in the chapter we will map a number of the LAN protocols in use today to the OSI model to show how the real protocol stack performs the functions that we have discussed in relation to each of the layers of the OSI model. Now that we have some of the basic theory related to the OSI model out of the way, let's take a more detailed look at the various layers of the OSI model and how they relate to encapsulation and de-encapsulation. Tip
Tip
Application LayerThe Application layer provides the tools that the user actually sees (but handles processes that the user does not see). Because it is at the top of the OSI model, it does not provide services to layers above it (because there are no layers above it), but it does provide network services related to user applications such as message handling, file transfer, and database queries. It also synchronizes applications between the client and server and makes sure that the resources are available for error recovery and to provide data integrity. When a user working in a particular application, such as a spreadsheet program like Excel, decides to save a worksheet file to his home directory on the network file server, the Application layer of the OSI model provides the appropriate service that allows the file to be moved from the client machine out onto the appropriate network volume. This transaction is actually transparent to the user. Presentation LayerThe Presentation layer can be considered the translator of the OSI model. This layer takes the data from the Application layer and converts it to a format that can be read by the Application layer of the receiving computer. The Presentation layer is also responsible for data encryption (if required by the application used in the Application layer) and data compression, which will reduce the size of the data. You are probably already familiar with a number of the different file formats that serve as Presentation layer standards. These include standards for text, sound, graphics, and even video. Table 5.2 provides a summary of some of these file formats by standard category. Table 5.2. Presentation Layer Standards
So, the Presentation layer provides Application layer applications with a choice of data types for transmission over the network media. For example, if an application sends data in binary (pretty much the coin of the realmit's recognized by every computer), no further action is required by the Presentation layer because the binary data can be read by the receiving computer. However, if the data is sent in another format, the Presentation layer will have to convert it to a more generic standard. Session LayerThe Session layer is responsible for setting up the communication link or session between the sending and receiving computers. The Session layer also manages the communication session that is set up between these nodes. The Session layer actually offers three different modes for the communication sessions set up between the network nodes: simplex, half-duplex, and full-duplex . Simplex transmits data in only one direction (such as your thermostat connecting to your furnace ). Half-duplex allows for communication in two directions but only allows for the transmission of data in one direction at a time (such as a one-lane bridge). Full-duplex allows communication in both directions at the same time. Another function of the Session layer is to place special checkpoints in the data stream as it moves from the sending computer to the receiving computer. These checkpoints can then be used in situations where the connection between the computers is lost. Only the data in the data stream that is found after the most recently received checkpoint will have to be re-sent by the sending computer. Note
Transport LayerThe Transport layer is in charge of flow control as the data moves from the sending to receiving node. Up to this point, we have referred to the information created by a user on a networked computer as data. When this data reaches the Transport layer, it is actually segmented into small data packages; each of these packages is referred to as a packet . A number of packets will make up the original data that was generated by the user (such as the email message discussed earlier in the chapter). As far as flow control is concerned at the Transport layer, the communicating computers will use acknowledgements to verify the receipt of data. These acknowledgements are sent from the destination computer to the sending computer when an agreed-upon number of data packets have been sent by the sending node. For example, the sending node might send three bursts of packets to the receiving node and then receive an acknowledgement from the receiver. The sender can then send another three bursts of data. The Transport layer also provides two different types of data delivery methods: connection-oriented and connectionless. Connection-oriented transport uses a system of acknowledgements to ensure data delivery and defines a static route on the network so that the packets are delivered along the same route during the session. This is considered a reliable connection. Connection-oriented protocols operate in much the same way that you establish communications over the telephone. You establish a session with the person you are calling. A direct connection is maintained between you and the party on the other end of the line. When the discussion concludes, both parties typically agree to end the session. Connectionless transport at the Transport layer does not use acknowledgements or a static path for data delivery. Therefore, this is considered an unreliable method of data delivery. Connectionless transport does not require the network resources that connection-oriented communication requires, however. Connectionless protocols operate more like the regular mail system. They provide appropriate addressing for the packets that must be sent, and then the packets are sent off much like a letter dropped in the mailbox. It is assumed that the addressing on the letter will get it to its final destination, but no acknowledgment is required from the computer that is the intended destination. Tip
Note
Network LayerThe Network layer is charged with the duty of addressing the packets for delivery using a particular logical addressing strategy. For example, networks that use TCP/IP as their network protocol use IP addresses to address packets (every computer on the Internet has a different IP address). Networks that use IPX/SPX (Novell's network protocol stack) use IPX addresses. The Network layer is also responsible for determining the path that packets will take as they are routed on a network from source to destination. The Network layer is where routers operate, using the logical addressing assigned to a packet to determine the route for that packet on the network. We discuss routing and IP addresses in Chapter 12, "TCP/IP Network Administration." Routers determine the route for packets with the help of a special kind of protocol, called a routing protocol . These routing protocols, such as the Routing Information Protocol (which is a protocol found at the Network layer in both the TCP/IP and IPX/SPX protocol stacks), build routing tables that are then used by the router for path determination (routing is discussed in Chapter 12). Tip
Data Link LayerWe've already discussed the fact that as data on the sending computer moves down through the OSI layers, encapsulation takes place (the data is encapsulated with a header from each of the layers). At the Data Link layer, the data packet is actually placed inside a data frame . The frame type is defined by the type of network architecture that is being used on the network. For example, an Ethernet frame will be used on Ethernet networks, and a token ring frame will be used on token ring networks. The Data Link layer also is responsible for data movement across the actual physical link to the receiving node and therefore uniquely identifies each computer on the network based on its hardware address that is encoded into the network interface card. So that there is some mechanism for checking the validity of a frame sent over the network media, protocols that operate at the Data Link layer also will add a cyclical redundancy check (CRC) as a trailer on each frame (the trailer is placed at the end of the frame, whereas the header would be on the other end of the frame). The CRC is basically a mathematical calculation that takes place on the sending computer and then on the receiving computer. If the two CRCs match up, the frame was received in total and its integrity was maintained during the transfer. Physical LayerThe duties of the Physical layer seem quite mundane, when you compare them to the rest of the OSI model. But they are certainly no less important. As the frames from the Data Link layer are passed to the Physical layer, they are converted into a single bit stream. This means that all the bits (a stream of 1s and 0s) are queued up one after another as they move out onto the network media. The Physical layer is also responsible for the actual generation of a signal across the network media (this could be electrical, light impulses, or radio waves, depending on the type of network media the network uses). This means that the Physical layer defines the actual physical aspects of how the cabling (if actual physical cable is used) is hooked to the computer's network interface card. |
EAN: 2147483647
Pages: 188