| Before going further, let's quickly address a special class of GroupWise users. GroupWise has a special kind of GroupWise object called a GroupWise external entity. An external entity is a full-blown GroupWise account that has an eDirectory object, but the object class is a GroupWise external entity and not an eDirectory user object. This kind of a GroupWise account cannot authenticate to eDirectory. The reason for this is that these types of users do not have "real" eDirectory user objects. They have a placeholder in eDirectory, but this object is far from a full eDirectory user class object. These users will still use a GroupWise password to authenticate. Enabling LDAP authentication will not break authentication for users who are external entities. How LDAP Authentication Works What follows is a high-level explanation of how GroupWise uses LDAP authentication to allow users to access their GroupWise mailboxes: GroupWise user loads the GW client (Windows, WebAccess, wireless, or other). The user sends his or her user ID and password to the post office agent (POA). The POA uses the LDAP protocol to query an external LDAP service provided database. The LDAP requires a login or authentication. The POA validates user credentials against the LDAP provided database. The POA denies or grants access to the user depending on LDAP validation.
As explained in this section, it's important to note that the LDAP authentication logic is all in the POA. How to Configure LDAP Authentication The following is a high-level explanation of how to configure LDAP authentication to GroupWise: Define the LDAP server(s). Modify post office security. Set the security level to High. Configure LDAP server settings.
Step-by-Step Instructions for Enabling LDAP Authentication Now roll up your sleeves; you are going to enable LDAP authentication. When you actually set up LDAP authentication in your system, it's a good idea to do so using a test post office and a few test users at first. This way, you can get familiar with the process of enabling LDAP prior to affecting your live GroupWise system. Educate Users When you are ready to cut over to LDAP authentication, educate your users about the fact that they now must use their eDirectory passwords instead of their GroupWise passwords. In the following scenario, you are going to enable LDAP authentication for a post office called CORPPO on the CORP domain in the WorldWide Widget's GroupWise system. Define the LDAP Server Use these steps to define an LDAP server in the GroupWise system: 1. | Load ConsoleOne, and connect to the primary domain. From the Tools menu select GroupWise System Operations, LDAP Servers.
| 2. | In the Configure LDAP Servers menu, you might see an existing LDAP server. For example, in the WorldWide Widgets system, there is already an LDAP server defined called LDAP CORP CORPPO. The GroupWise snap-ins create LDAP server definitions for new GroupWise post offices. However, if you have upgraded your system from a prior version of GroupWise, you might not have any LDAP servers defined in this dialog box.
| 3. | Delete the existing LDAP server. In the WorldWide Widgets system, we will use a naming convention such as LDAP1. This naming convention is more logical for the LDAP pooling architecture, which is explained later in this chapter in the section "LDAP Server Pooling."
| 4. | For ease of configuration, the LDAP servers should be generic in nature, meaning that each post office should not have its own LDAP server defined for that post office, so the name of the LDAP server should not correlate with the name of the post office. In the case of WorldWide Widgets, the name of the LDAP server is LDAP1.
Tip The name of the LDAP server must comply with the GroupWise domain naming standards. For example, you cannot use characters such as periods or commas. | 5. | Give the LDAP server a description; this can be the same description as the name of the LDAP server.
| 6. | The next field is the Use SSL field. We strongly encourage you to enable SSL. Do so after you have tested this entire solution in a testing environment, without SSL. The complete instructions for enabling SSL are in Chapter 27, "Securing Your GroupWise System via SSL."
| 7. | Fill in the LDAP server address, and keep the port of 389. When you enable SSL, the port will be 636.
| 8. | Choose the user authentication method. Most customers will want to use Bind over Compare. These two methods are explained just a little later, in the section "LDAP Bind and LDAP Compare."
| 9. | Click the Select Post Offices button, and select the CORPPO post office. Only the CORPPO post office should use this LDAP server.
|
The LDAP server you have configured should look similar to the one shown in Figure 26.1. Figure 26.1. LDAP server configuration 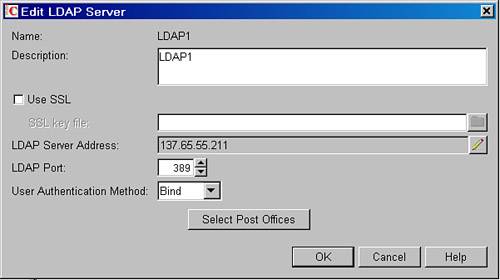
LDAP Bind and LDAP Compare Two user authentication methods are available for adding an LDAP server. Most customers will want to use Bind instead of Compare. Here's a look at each of these two methods: The Bind method Uses the user ID and password supplied by the client/user to authenticate to the LDAP server. Requires that the POA make a connection to the LDAP server for each user logging in. Supports password expiration.
The Compare method Requires that the POA use the provided user ID and password to authenticate to the LDAP server. Allows the POA to make only one connection to the LDAP server. Does not support password expiration.
Although the Bind method can be a little bit slower than the Compare method, in most cases we do recommend using the Bind method. Enable LDAP Authentication at the Post Office Now that the LDAP server is defined, you must enable LDAP authentication on the post office. Here are the steps for doing so: 1. | Edit the properties of the CORPPO post office object (not the POA object below the post office).
| 2. | From the GroupWise tab, select the Security property page.
| 3. | The Security level should be set to High. Place a check mark next to the LDAP Authentication option.
Note If you enable eDirectory authentication and LDAP authentication at the same time, the LDAP authentication is enforced. For example, with both LDAP and eDirectory authentication enabled, if the GroupWise account does not have a password and you are authenticated to the network, you must still enter your LDAP password to gain access to the GroupWise mailbox. We have found that having both eDirectory and LDAP authentication checked has no real advantages over simply using LDAP authentication. | 4. | The LDAP User Name field needs to be filled out only if the LDAP server that you defined earlier in this section uses the Compare user authentication mode. Fill out this field if you use LDAP Compare as your user authentication mode. The syntax for this field is as follows:
CN=eDirectory USERID, Organizational Unit unless the user is at the root of the tree, Organization
For example:
CN=LDAPUSER,OU=NY,OU=AMERICAS,O=WWW
The user does not have to be a super user with Admin equivalent rights. The user just must have Browse, Read, and Compare rights throughout the entire eDirectory tree, or at least in the OU or OUs that house the users that are associated with post office you are configuring.
| 5. | The LDAP Password field is also used only when using the Compare user authentication mode. If you're using Compare user authentication, fill in this field with a password. The password is the password for the user that you used in the LDAP User Name field.
| 6. | The Disable LDAP Password Changing option is an important one. The default is to allow users to change their passwords within GroupWise, which changes their eDirectory passwords. There's not necessarily any harm done in allowing users to change their eDirectory passwords from GroupWise, unless you are using some other technology that may need to be apprised of eDirectory passwords. When a password changes in a GroupWise client, there might not be a way for other software to know of that password change. The needs of your environment will dictate whether you want to check the Disable LDAP Password Changing option. Make your decision and select the choice if needed.
| 7. | The LDAP Pool Server Reset Timeout option has to do with the LDAP server pooling option, which is explained later in this chapter.
| 8. | Click the Select Servers button and make sure that the LDAP1 LDAP server is in the Selected Servers column.
|
Figure 26.2 shows the CORPPO's Security property page with LDAP authentication enabled for the post office. The post office supports Bind user authentication mode, and users can change their eDirectory passwords from within a GroupWise client. Figure 26.2. A post office with LDAP authentication configured 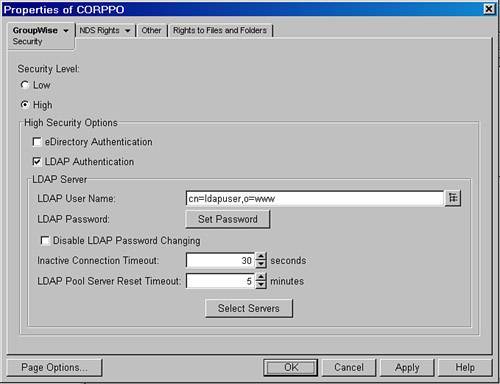
|

