How Hotspot Hacking Works
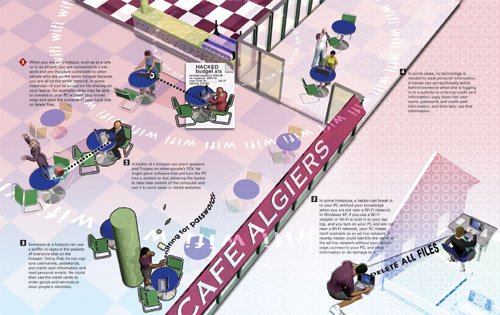 |
How Personal & Internet Security Works
ISBN: 0789735539
EAN: 2147483647
EAN: 2147483647
Year: 2004
Pages: 161
Pages: 161
Authors: Preston Gralla
- Step 1.1 Install OpenSSH to Replace the Remote Access Protocols with Encrypted Versions
- Step 3.2 Use PuTTY / plink as a Command Line Replacement for telnet / rlogin
- Step 3.3 Use WinSCP as a Graphical Replacement for FTP and RCP
- Step 3.4 Use PuTTYs Tools to Transfer Files from the Windows Command Line
- Step 4.2 Passphrase Considerations