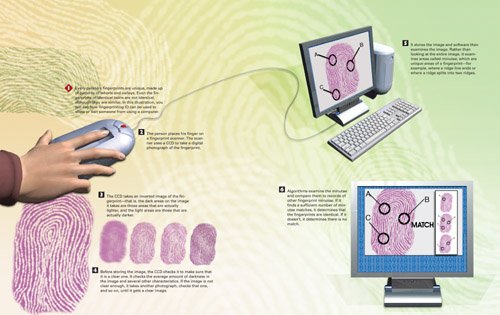
How Fingerprinting ID Works
 |
How Personal & Internet Security Works
ISBN: 0789735539
EAN: 2147483647
EAN: 2147483647
Year: 2004
Pages: 161
Pages: 161
Authors: Preston Gralla
- Chapter V Consumer Complaint Behavior in the Online Environment
- Chapter XI User Satisfaction with Web Portals: An Empirical Study
- Chapter XIII Shopping Agent Web Sites: A Comparative Shopping Environment
- Chapter XV Customer Trust in Online Commerce
- Chapter XVI Turning Web Surfers into Loyal Customers: Cognitive Lock-In Through Interface Design and Web Site Usability