Bibliography
|
Attacks
Steganography Attacks
-
Stego-only attack: Attack is one where we have only the stego-medium, and we want to detect and extract the embedded message (Figure 9.2).

Figure 9.2 -
Known-cover attack: Attack is used when we have both the stego-medium and the cover-medium, so that a comparison can be made between the two (Figure 9.3).
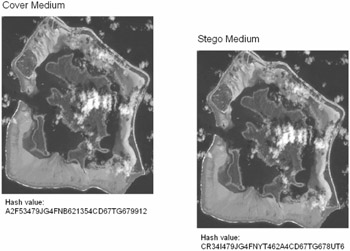
Figure 9.3 -
Known-message attack: Attack assumes that we know the message and the stego-medium, and we want to find the method used for embedding the message (Figure 9.4).

Figure 9.4 -
Chosen-stego attack: Attack is used when we have both the stego-medium and the steganography tool or algorithm (Figure 9.5).
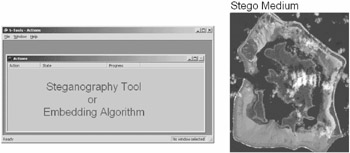
Figure 9.5 -
Chosen-message attack: Attack is one where the steganalyst generates a stego-medium from a message using a particular tool, looking for signatures that will enable the detection of other stego-media (Figure 9.6).
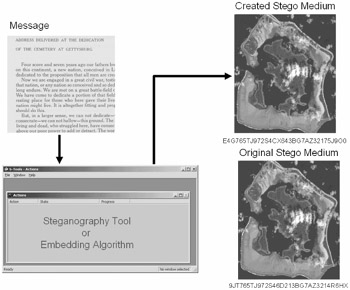
Figure 9.6
Disabling or Active Attacks
-
Blur: Smoothes transitions and decreases contrast by averaging the pixels next to the hard edges of defined lines and areas where there are significant color transitions.
-
Noise: Random noise inserts random-colored pixels to an image. Uniform noise inserts pixels and colors that closely resemble the original pixels.
-
Noise reduction: Reduces noise in the image by adjusting the colors and averaging pixel values.
-
Sharpen: Sharpening is the opposite of blur. It increases contrast between adjacent pixels where there are significant color contrasts, usually at the edge of objects.
-
Rotate: Rotation moves an image around its center point in a given plane.
-
Resample: Resampling involves an interpolation process to minimize the "raggedness" normally associated with expanding an image.
-
Soften: Applies a uniform blur to an image to smooth edges and reduce contrasts, and causes less distortion than blurring.
Watermark Attacks
-
Collusion attack: By looking at a number of different objects with the same watermark, one can find, isolate, and remove the watermark by comparing the copies.
-
Jitter attack: The jitter attack works the same in watermarking as it does steganography. Its purpose is to upset the placement of the bits that identify the watermark by applying "jitter" to the image. How robust the watermark is depends on how much jitter it can take; in the case of a fragile watermark, just cropping one row of pixels from the perimeter of the image will change it significantly enough to destroy the watermark. But then again, a fragile watermark is not supposed to be able to endure a jitter attack.
-
StirMark: The StirMark attack applies small distortions that are designed to simulate the printing or scanning process. If you have ever scanned in a hard-copy photograph, you know that subtle distortions are introduced no matter how careful you are. The placement of the picture on the scanning bed, the conversion process from tangible to digital — all of these shifts can put a watermark to the test. StirMark does all of these automatically and adds multiple distortions on top of one another. Some of the distortions StirMark uses are JPEG, scaling, rotation and cropping, rotation, scale and cropping, shearing, flip, change of aspect ration, row and column removal, and random bending, just to name a few. This attack is particularly effective because some watermarks are more resistant to one type of modification as opposed to another, but usually are not immune to all of them at the same time.
-
Anti soft bot: A benefit of watermarking in the realm of the Internet is the ability to use software robots, sometimes called soft bots or spiders, to search through Web pages for watermarked images. If the soft bot finds a watermarked image, it can use the information to determine if there is a copyright violation.
-
Attacks on echo hiding: Echo hiding is a signal-processing technique that places information imperceptivity into an audio data stream in the form of closely spaced echoes. These echoes place digital tags into the sound file with very little sound degradation. Echo hiding is also very resistant to jitter attacks, so a removal attack is the usual method for getting rid of the watermark. In echo hiding, most echo delays are between 0.5 and 3 milliseconds; in anything above 3 milliseconds, the echo becomes noticeable. To remove the echo, the attacker uses the same method as detecting it, only with some modifications. The process of echo detection is called cepstrum analysis and the attacker would use this process with an opposite signal to damage the watermark.
-
Additive noise: This attack is fairly straightforward; it simply involves adding additional, imperceptible noise to the image to hinder or stop the watermark detection process. Because each pixel in the image has a tolerance for the amount of noise that can be introduced and still remain invisible, the additive noise attack uses that tolerance value to introduce the maximum amount of uncertainty that the decoder will have to deal with.
-
Linear filtering: Linear filtering is used when an attacker wants to eliminate a watermark or destroy any information that identifies the author or owner. This attack is carried out by removing an estimate of the watermark from the marked image, restoring the original image. Sometimes this "estimate" watermark can cause damage to the data, depending on the complexity of the information the watermark is embedded into.
-
Resampling: Resampling combines analysis and interpretation of a data file to change it by a certain factor. What that essentially means is a program will look at an image file, for example, interpret the pixels it "sees," and assign a new approximate value to them. It will also look at the surrounding pixels for more information about the image. Then it takes these new values, based on estimations, and puts everything back together, creating a new image. The tolerances set in the beginning determine how much variance happens during the resampling process.
-
Cropping: Often a watermark is embedded in a linear fashion, meaning that the pixels that comprise the watermark follow a pattern that cropping can do significant damage to, depending on the extent of cropping. If the watermark is embedded in a pseudorandom fashion, the watermark may be more resilient to cropping, but removing pixels is still removing pixels, and it will weaken the energy of the watermark.
-
The mosaic attack: This attack relies on the fact that a watermark cannot be embedded into a small image. This attack disables the watermark by splitting the image into small pieces and then putting them back together. This creates the illusion that the image is really one picture, not a series of small ones. But as far as the detection method is concerned, it does not see one image; it sees a number of them, and none of them contain the watermark it is looking for.
|
EAN: 2147483647
Pages: 220