Chapter 10: Securing Network Clients
Chapter 10: Securing Network Clients
| 1. | You are the network administrator for the Blue Sky, LTD, airplane manufacturer. The vice president of the Finance department has reported that some technically savvy users within the department have been attempting to access confidential information by browsing the available network shares from the Network Connections desktop icon. He has requested that users within subdepartments of the Finance area not be able to map network drives or browse network shares that they have not been explicitly granted access to. However, you have assigned a word processing application to the entire organization using a default GPO, and you do not want to reconfigure this portion of the Active Directory structure. In response to the VP s request, you have configured your Active Directory environment as shown in Figure 10.13. (Please note that, in the illustration, Enforce means that the Enforce settings property has been applied to the GPO in question.) Which setting(s) will be applied to a workstation in the Collections OU? (Choose all that apply.) 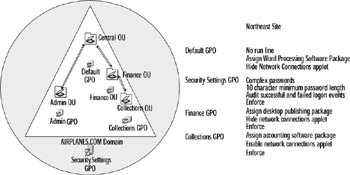 Figure 10.13: Question 1 Illustration
| |
| 2. | You are the administrator for a Windows Server 2003 domain. Your network consists of five locations connected by high-speed Internet connections. Your network servers are running solely Windows Server 2003, but you are supporting network clients that are a mixture of Windows XP Professional, Windows 2000, and Windows NT 4.0 Workstation. Because of the recent spate of critical security updates that have been released by Microsoft, you need to design a strategy to apply security updates to all of your workstations in a quick and efficient manner. Given the current environment, what option can you use to roll out updates for all of your network clients?
| |
| 3. | You are the network administrator for a Windows Server 2003 network with Windows XP Professional desktops. Your help desk has been inundated with support calls from users who have intentionally or accidentally altered their system settings in such a way that they have lost network connectivity or some other form of functionality. You create a new Group Policy Object (GPO) that restricts access to the Control Panel for all of your network users and link it to the domain level. You notice after several weeks that support calls have greatly diminished except for the Communications department. Upon further investigation, you discover that this department is contained within its own OU, and the OU has another GPO applied to it that explicitly grants access to the Control Panel, along with several other settings that the department manager insists are critical for his employees to perform their job functions. How can you enforce the Control Panel lockout without otherwise adversely affecting the Communications department?
| |
| 4. | You are the network administrator for a medical research facility running Windows Server 2003. Your firm is beginning a joint research operation with a major university, and many of your users will need to access files and folders on the university s network. The university that you are collaborating with is operating using a UNIX Kerberos environment with UNIX clients at each desktop. Your company s resources should also be accessible by the university staff. How can you accomplish this with the least administrative effort?
| |
| 5. | You are the network administrator for a large e-commerce site. Your Web developers have created a Web application to share information on the company intranet; this application relies on Digest Authentication to allow users to log on. For some reason, employees seem to be unable to access the new application. You check the account properties of one of the user accounts and see the screen shown in Figure 10.14. What is the most likely reason why your users cannot authenticate? 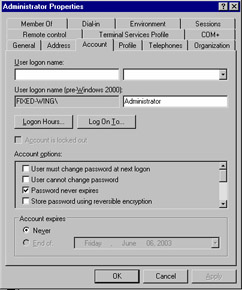 Figure 10.14: Administrator Properties Sheet
| |
| 6. | You are a local administrator within a large, multinational corporation. You would like to offer remote access capabilities for the users on your Windows Server 2003 domain. However, your corporation s security policies dictate that all remote access authentication needs to be processed by several UNIX-based RADIUS servers located at various points within the company s global infrastructure. How can you establish remote access authentication for your users that adheres to the corporation s security policies?
| |
| 7. | You are the network administrator for Blue Collar, Inc. clothing manufacturers. You have just installed a high-speed Internet connection at the corporate office, and you are designing a remote access scheme that will allow your branch offices and remote users to connect to the corporate LAN to access file shares and other resources. You create a single remote access policy that allows incoming VPN connections between 9 a.m. and 9 p.m., Monday through Friday. You have left all other policy settings at their default values. Most users are connecting to the VPN without issue, but your graphics designer who works from her home office is unable to connect to the VPN using her Macintosh desktop. What is the most likely reason why this is occurring?
| |
| 8. | You are the network administrator for a multisite Active Directory-based network. Your current network infrastructure consists of the following server machines:
Your network contains over 1,000 users on Windows 2000 and XP Professional workstations belonging to a single Windows Server 2003 domain. The load on the DCs is fairly high, with processor utilization spiking to over 90 percent at several points during the day, especially first thing in the morning and close to 5 p.m . MAX-APP1 is a dedicated application development server that receives similar processor-heavy requests from your department of application developers. With the recent spate of software vulnerabilities, you would like to implement a patch management solution for the clients and servers on your network. Because of some sensitive development environments and documents on your network, you want to be able to test any updates before you apply them to your network servers and clients. You do not have any available budget for new hardware upgrades or purchases. What would be your best course of action in this scenario? (Choose all that apply.)
| |
Answers
| 1. | ¾ A , B , D . Since the Collections GPO does not have the Block Inheritance property set, it will inherit the desktop publishing package installation from the Finance GPO. Therefore, Answer A is correct. Although the Collections GPO has the Enforce property set, the Finance GPO (which exists at a higher level in the OU hierarchy) also has the Enforce property set. In the case of conflicting enforced settings, the setting that occurs higher in the hierarchy takes precedence. This is the reverse of the usual GPO inheritance rules. Therefore, Answer B is correct. The Marketing OU will also inherit the No Run Line property from the Default GPO. Therefore, Answer D is correct. x Answer C is incorrect because even though the Marketing GPO has enabled the Network Connections applet enabled along with the Enforce property, it is overridden by the Enforce property in the Finance GPO. |
| 2. | ¾ D . Given the need to support down-level clients in this scenario, SUS and Group Policy will not be sufficient to deploy security updates to all of your network clients. In this case, a third-party solution is required. x Answer A is incorrect because SUS can only be used to deploy updates to Windows 2000, Windows XP, and Windows Server 2003 machines. Answer B is incorrect because security updates should be tested before being deployed in a production environment in case they interfere with any production services or applications. Answer C is incorrect because Windows NT 4 clients cannot use the software installation settings available through Group Policy. |
| 3. | ¾ B . Using the Enforce setting will ensure that all users in your domain will have access to the operating system features in the Control Panel restricted. x Answer A is incorrect because this will remove any other settings in the Communications OU GPO, which would adversely affect the Communications department s ability to work. Answer C is incorrect because the Block Inheritance setting will only ensure that GPOs applied at a higher level in the Active Directory structure will not be applied to the Communications OU. Answer D is incorrect because that would cause the Communications GPO settings to be applied to the entire Active Directory structure, rather than to the single OU. |
| 4. | ¾ A . A realm trust will allow users from UNIX clients to be able to connect to your network resources. x Answer B is incorrect because a realm trust will enable UNIX clients to access your network without the extra administrative effort. Answer C is incorrect because NTLMv2 can only be used by Microsoft clients; it isn t supported by UNIX. Answer D is incorrect because MS-CHAP is an authentication protocol used for remote access authentication from Microsoft clients, not for LAN access by UNIX clients. |
| 5. | ¾ D . For Digest Authentication to function properly, you must select this option for the user accounts that need to use Digest Authentication, either manually or through a policy. Once you ve enabled this setting, the users in question will need to change their passwords so that the reversibly encrypted value can be recorded in Active Directory. x Answer A is incorrect because a user s password is case sensitive when accessing any Windows application, but not the username. Answer B is incorrect because Digest Authentication will function under Internet Explorer version 5.0 or later. Answer C is incorrect because Digest Authentication will not fail simply because a user changes his or her Active Directory password. |
| 6. | ¾ A . In Windows Server 2003, IAS can function as a RADIUS proxy, forwarding authentication requests to a central RADIUS server regardless of the target server s platform or location. x Answer B is incorrect because realm trusts are used to create trust relationships between a Windows Server 2003 domain and a UNIX-based Kerberos 5 domain; they are not related to remote access authentication. Answer C is incorrect because enabling the Guest account on a production server such as a corporate RADIUS server creates a glaring security flaw. Answer D is incorrect because Digest Authentication is used to provide authentication for Web applications, not for remote access purposes. |
| 7. | ¾ A . The CHAP authentication protocol is the strongest protocol that Macintosh and UNIX remote access clients can support. By default, a remote access policy will only enable MS-CHAP and MS-CHAPv2. For the graphics designer to connect to the VPN using her Macintosh desktop, you need to manually add CHAP to the list of allowable authentication protocols. x Answer B is incorrect because you have not restricted remote access based on group membership in this scenario, only time of day/week. Answer C is incorrect because the RAS server does not necessarily require the AppleTalk protocol to communicate with a Macintosh client ”as long as both the client and the server have TCP/IP installed, they will be able to communicate. Answer D is incorrect because the time-of-day restriction is based on the time according to the RAS server, not the incoming client. |
| 8. | ¾ A , D . Answer A is correct because MAX-FPS1 is the best choice of the machines available to host an SUS server. It possesses the necessary hardware requirements, and is not already at the limits of its capacity to service network requests. Answer D is correct because, in a Windows 2000/XP client environment, you can use a GPO to automatically configure your clients to point to an update site. Pointing your clients to an internal SUS server will allow you to test any updates before deploying them in a production environment. x Answer B is incorrect because MAX-APP1 does not meet the minimum hardware requirement of 512MB of RAM. It is also heavily taxed already by the application developers in your environment. Answer C is incorrect because, while MAX-DC2 meets the minimum hardware requirements for a SUS server, it is already heavily taxed by servicing user logon requests. Adding a SUS installation to this server would negatively affect server performance and user productivity. Answer E is incorrect because Windows 2000 and XP clients can be configured automatically with a GPO, rather than manually scripting the necessary registry entries. Answer F is incorrect because you need to test all updates before deploying them to your network, which makes using the internal SUS server an appropriate choice for hosting client updates. |
EAN: 2147483647
Pages: 122