Objective 5.3: Securing Client Computers
While the MCSE Core Four exams focus a great deal of attention on securing the server operating system, services, and processes, most network administrators will tell you that securing end- user desktops can present a far greater challenge in a real-world network. Servers exist in a tightly secured environment: software is (hopefully) installed and updated only under well-controlled conditions, and only after thorough testing. Moreover, security patches and updates for server services often receive more visibility and attention from vendors and security watchdogs alike. However, securing network clients is a critical process, if for no other reason than that your network clients outnumber your servers 10, 100, or even 1000 to 1. Staying abreast of any new vulnerabilities for your client computers and patching those vulnerabilities in a timely and efficient manner can mean the difference between a well-secured network and a Code Red infestation waiting to happen. In this section, we ll discuss some of the important concepts in hardening client computers, including the importance of anti-virus software and patch management.
Objective 5.3.1: Hardening Client Operating Systems
When you receive a new workstation from a major manufacturer, you ll often find that the operating system has been installed in an insecure fashion. Often, a vendor will create a default operating system installation designed to make a new computer easy to use and navigate for an inexperienced user; however, this can have major ramifications in terms of the security of a newly installed computer. You ll often find new operating systems installed with any number of development tools and utilities, or automatic access to a poorly secured Administrator account. Although this type of behavior can be beneficial to a new user, it also provides potential back-door access to an organization s systems.
Hardening client operating systems is a critical first step in safeguarding your client operating systems from internal or external intrusion and attackers . At a minimum, this involves the removal of any nonessential tools, utilities, or other administrative options that could be exploited by an attacker to gain access to your systems. The hardening process will also ensure that all necessary security features have been activated and configured correctly for any administrative or nonadministrative user accounts used to gain access to the client system, rather than simply providing easy access to an Administrator account.
Minimizing Attack Vectors
A term that you ll hear quite often when dealing with computer and information security is the notion of an attack vector . Put simply, an attack vector is the exploit that a malicious user uses to gain access to a system, whether it s through guessing weak passwords or using a buffer overflow attack against an unpatched system. When designing secure systems, one of your goals should be to minimize the potential avenues of attack that a hacker can use to gain access to your company s systems. You can think of this as a castle with a drawbridge that s surrounded by a moat: since there s usually only one way into and out of the castle, the people defending that castle can concentrate on defending the main gate and the drawbridge. This makes securing a castle much simpler than a building with many easily reached doors and windows that can all provide a means of access to gain entry. (To further the analogy, it s still necessary to defend other parts of the castle, since a determined attacker could probably find a way to cross the moat and scale the castle walls, given enough time and resources.)
So, what does this mean for securing computing systems? It means that, when configuring and installing clients within your secure network design, you should only install the software and services that are necessary for your clients to perform their job duties effectively. For example, there have been one or more software vulnerabilities attached to the Microsoft Windows Media Player, but if your client computers did not have Windows Media Player installed to begin with, then this vulnerability would have no chance of affecting the security of your systems. Likewise, most modern Windows client operating systems are capable of running a stripped-down version of IIS called Personal Web Server (PWS) from a client desktop; if this option isn t necessary for your clients to function, then it should be disabled as well. (The Code Red and Nimda worms exploited many Windows desktops where the users didn t even realize that they d had this desktop version of IIS installed to begin with.) Any steps that you can take to minimize or eliminate any unnecessary software or services running on your desktop computers will go a long way in preventing attackers from finding these different (and often superfluous) vulnerabilities to exploit.
Creating an Antivirus Protection Scheme
In Chapter 1, Designing a Secure Network Framework, we discussed the threat posed to a modern network by malicious attackers using viruses, Trojans, and worms to affect the confidentiality, integrity, and availability of the data on a corporate network. It s not enough to provide virus protection at the server level; each client on your network needs to have antivirus software installed and updated with the latest virus definitions in order to provide the best defense for your systems and data. Viruses can often enter a corporate network through a single end user either opening an infected e-mail attachment or browsing to a Web site that contains malicious code. Because of this, you need to design virus protection for all systems on your network that interact with the Internet and the rest of the world at large. Are you running an e-mail server? Be sure that you are scanning incoming and outgoing e-mail messages for virus infections. Do your end users have Internet access from their desktops? Be sure that each network-connected workstation has anti-virus software that provides real-time antivirus scanning. You can also install antivirus software at other points on your network, including at the firewall or proxy server that will scan all incoming network traffic for virus infections. While there are any number of commercial and freeware options available for virus protection, it s critical that a secure network design make allowances for its installation, use, and management.
| Test Day Tip | Real-time protection refers to anti-virus software s ability to scan files as they are created or accessed, thus providing instant notification if a downloaded file contains a virus or other form of malicious code. Most commercial anti-virus software packages provide this feature. |
Enabling Patch Management
While Microsoft s focus on security is evident in Windows Server 2003, the fact remains that the discovery of new security vulnerabilities (and attacks that exploit them) is often simply a fact of life. As an administrator, you need to be able to determine which patches and updates are required by your enterprise computing systems, and the best way to deploy those updates as quickly and efficiently as possible. Creating an effective patch management scheme will reduce downtime and costs on your network associated with system outages or data corruption, and increase the overall security and integrity of your company s assets and intellectual property.
As a part of the Trusted Computing Initiative, Microsoft has attempted to streamline the patch management and installation process using both built-in functionality within Windows Server 2003 and freely available services and add-ons. The first step in effective patch management is obviously the ability to know that a patch is necessary and available. The Security Bulletin Notification Service provides e-mail bulletins whenever a security vulnerability for a Microsoft product has been reported and confirmed, usually along with information on how to obtain necessary patches or otherwise reconfigure vulnerable systems. The notification service classifies security vulnerabilities into one of four categories, as shown in Table 10.1. By remaining alert to the presence of security updates and patches, you can then define processes to distribute the necessary software updates to all of your network clients.
| Rating | Definition |
|---|---|
| Critical | A vulnerability of this severity could allow an Internet worm or virus to spread without user action, or even awareness. |
| Important | A vulnerability of this level can compromise the confidentiality, integrity, or availability of a user or company s data, or the availability of other network resources. |
| Moderate | The risk of this type of vulnerability is often greatly mitigated by factors such as the default configuration of the operating system, auditing, or difficulty of exploitation. |
| Low | A vulnerability whose exploitation is extremely difficult or whose impact is minimal. |
Group Policy
One of the most powerful tools for installing software updates is actually freely available for download from the Microsoft Web site, and integrates right into the Windows Server 2003 operating system. By using the Software Installation settings within Group Policy, you can automatically distribute security updates to an entire domain, site, or organizational unit (OU), or even to a single user or computer, from one centralized location. (For more information on configuring Software Installations in Group Policy, see MCSA/MCSE Exam 70-290: Managing and Maintaining a Windows Server 2003 Environment (ISBN: 193226660-7) from Syngress Publishing.) Unfortunately, there are a few drawbacks to relying solely on Group Policy. Remember that Software Installation settings do not apply when a client is logging on to Active Directory over a slow link (anything slower than 56Kbps.) This means that if you have a remote office that connects to a corporate LAN via a dial-up modem, no software installation settings will be propagated to the remote systems; if Group Policy is your only means of distributing patches, then these systems will remain unprotected . Group Policy also requires you to manually create and distribute software installation patches. However, the freely available Software Update Services (which we ll discuss next ) goes a long way toward improving this process for a corporate LAN.
Software Update Services
Microsoft Software Update Services (SUS) was designed to simplify the process of keeping your Windows client and server systems updated with the latest critical updates. SUS will enable you to quickly and efficiently deploy critical updates to your Windows 2000 and Windows Server 2003 systems, and any client systems running Windows 2000 Professional or Windows XP Professional. You can use SUS to deploy critical updates, security patches, and Windows service packs for all supported operating systems (with SUS SP1 or later). The SUS service relies on two major components :
-
Microsoft Software Update Services This is the server component that you ll install on a computer running Windows 2000 Server or Windows Server 2003 that s located inside your corporate firewall. The server component synchronizes with the Microsoft Windows Update site to download all critical updates and service packs for Windows 2000, Windows Server 2003, and Windows XP. This synchronization process can be configured to occur automatically, or you can perform the process manually. Once you ve downloaded any updates, you can then test them within your environment and then approve updates for installation throughout your organization.
-
Automatic Updates This is the component that actually installs all approved updates on your client machines. The Automatic Update component is included by default on Windows 2000 Service Pack 3 (SP3) and later, Windows XP SP1 and later, and Windows Server 2003. Any of your clients who are running Windows 2000 Service Pack 2 or earlier can install the Automatic Update component manually if they cannot be upgraded to the latest service pack level. Automatic Update allows your servers and client computers to connect to your internal SUS server and receive any updates. You can control which SUS server each Windows client should connect to, and schedule when the client should perform all installations of critical updates. This configuration is something you can perform manually for one or two machines, or through Group Policy settings for a large environment. You can configure the automatic updates to come from an internal SUS server, or directly from the Microsoft Windows Update site.
Exam Warning The most recent word from Microsoft is that SUS cannot be used to apply security updates to clients running Windows NT 4 or earlier operating systems, and it can only be used for critical updates and service packs. Updates for applications such as MS Office will need to be deployed using another means. For real-world use, check the most recent SUS release to see if this has changed.
Third-Party Tools
If you find that Group Policy and SUS don t fully meet your patch management requirements (you re supporting a number of down-level clients, for example), any number of third-party alternatives can assist you in deploying security patches in an efficient manner. A common option in this case is Microsoft Systems Management Server (SMS), which is a fully functional network management solution that will allow you to monitor and control many aspects of your network, not just the patch management process. The key differences between SUS and SMS are outlined in Table 10.2. Other third-party tools include HFNetCHK Pro from Shavlik Technologies, LANDesk from Intel, and many others. The 70-298 exam will not expect you to be able to select a specific third-party solution; however, you should be able to recognize a scenario where one would be required.
| Installation and Distribution Features | SUS | SMS |
|---|---|---|
| Content | Built-in synchronization service can automatically download the latest critical updates from Microsoft. | Automatic downloading of necessary updates. |
| Targeting | Basic targeting in which machines receive all applicable patches from the SUS server that they are assigned to. | Granular targeting based on criteria such as inventory, groups/OUs, and subnets. |
| Geographical Distribution | SUS can be scheduled to automatically synchronize content with the list of approved updates from other SUS servers or a distribution point within your network. | Site-site distribution that can be scheduled and is sensitive to WAN links. |
| Installation | Manual or simple scheduling based on group policy. Downloads are fault tolerant based on bandwidth, and can be scheduled. | Manual or advanced scheduling based on the targeting criteria listed. |
| Status | Status reported via Internet Information Services IIS logs. | Built-in filters and Reports |
Securing Laptop Computers
The increasing prevalence of laptop computers in a corporate network has created new challenges for providing network security. Securing mobile computers involves using technical measures, and increasing user awareness of the role that they play in keeping their computers and data secure. (We talked about the importance of user awareness in Chapter 1.) The first layer of security for laptop and mobile computers is securing the physical hardware itself, using hardware locks to prevent the computer from being stolen if it s left unattended. You can also enable a setup or boot password in the system BIOS to prevent the laptop from powering on if the correct password isn t provided.
Perhaps the best way to secure a mobile computer, however, is through the use of the Syskey utility. Most password-cracking software used in attacking computer systems will target the SAM database or the Windows directory services to access user accounts. The Syskey utility (located in the %systemroom%\system32 directory) will encrypt password information stored either on a local computer or in the Active Directory, thus providing an extra line of defense against would-be attackers. To use this utility on a workstation or member server, you need to be a member of the local Administrators group on the machine in question. (If the machine is a member of a domain, remember that the Domain Admins group is added to the local Administrators group by default.) On a domain controller (DC), you need to be a member of the Domain Admins or Enterprise Admins group.
| Test Day Tip | On workstations and member servers, password information is stored within the computer s Registry. DCs integrate password information into the directory services database that is replicated between controllers. |
In the following exercise, we ll go through the steps in enabling the System Key Utility on a Windows Server 2003 server.
| |
-
From the Windows desktop, click Start Run , then type syskey and click OK . You ll see the screen shown in Figure 10.1.
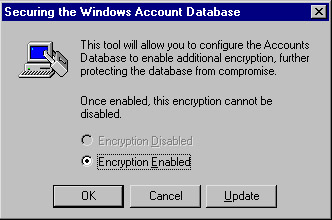
Figure 10.1: Enabling Syskey Encryption -
Click Encryption Enabled , and then click Update .
-
Choose from the security options shown in Figure 10.2. The different options available to you are as follows :
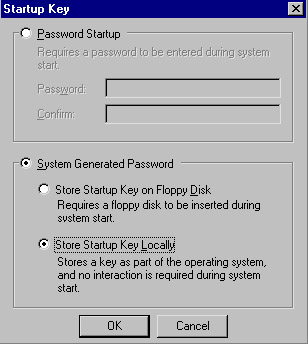
Figure 10.2: Selecting Syskey Encryption Options-
System Generated Password, Store Startup Key Locally This encrypts the SAM or directory services information using a random key that s stored on the local computer. You can reboot the machine without being prompted for a password or a floppy disk; however, if the physical machine is compromised, the System Key can be modified or destroyed . Of the three possible options when using Syskey, this is the least secure method.
-
Password Startup, Administrator-Generated Password Like the first option, this will encrypt the account password information and store the associated key on the local computer. In this case, however, you will select a password that will be used to further protect the key. You ll need to enter this password during the computer s boot-up sequence. This is a more secure option than storing the startup key locally, since the password used to secure the system key isn t stored anywhere on the local computer.
-
System Generated Password, Store Startup Key on Floppy Disk This option stores the system key on a separate floppy disk, which must be inserted during the system startup. This is the most secure of the three possible options, since the system key itself is not stored anywhere on the local computer, and the machine will not be able to boot without the floppy disk containing the system key.
Exam Warning If you lose the floppy disk or forget the password that you created when you ran Syskey, you won t be able to boot the computer in question without restoring the Registry or the Active Directory database from a point before you implemented Syskey.
-
-
Once you have selected the option that you want, click OK to finish encrypting the account information. You ll see the confirmation message shown in Figure 10.3.
Figure 10.3: Confirmation of Syskey Success
| |
Objective 5.3.2: Restricting User Access to Operating System Features
As we mentioned previously when talking about hardening client operating systems, sometimes the default installation of an operating system gives the users more control over their desktop than you, the administrator, would really like. Windows Server 2003 makes it a relatively simple matter to lock down operating system features using Group Policy Objects (GPOs). You can restrict access to items such as the command prompt, the run line, and Control Panel. You can prevent users from mapping or disconnecting network drives , adding or deleting network printers, and any number of other levels of granular control over the end-user experience. As with all GPO settings, these restrictions can be applied at the domain, site, or OU level, and you can set multiple policies and/or restrict how policies are inherited from a parent OU to any child OUs. (However, as you ll see, some security policies can only be set at the domain level.)
Here are some of the common operating system features that you can restrict through the use of group policies:
-
Hide all icons on desktop
-
Don t save settings at exit
-
Hide specified drives in My Computer
-
Remove the Run option from the Start menu
-
Prohibit user from using the Display icon in Control Panel
-
Disable and remove links to Windows Update
-
Disable changes to taskbar and Start menu settings
-
Disable/Remove the Shut Down command
-
Hide the My Network Places icon
-
Remove the Map Network Drive and Disconnect Network Drive
-
Disable Internet Options in Internet Explorer
When you are using GPOs to restrict this type of user access in a complex environment, keep the following points in mind:
-
If a user or computer has multiple GPOs that can be applied at the same level in the Active Directory structure, any conflict resolution will apply to individual GPO settings, not to the entire GPO. Therefore, you can have a single setting in a GPO encounter a conflict that needs to be resolved, while other settings in the same GPO are applied without issue.
-
Child OUs inherit Group Policy settings from parent OUs by default, but child domains do not inherit Group Policy settings from their parent domains.
-
Certain Group Policy settings can only be applied at the domain level, particularly password policies and account lockout policies.
-
The Enforce setting will force a GPO to apply to all Active Directory objects within a given site, domain, or OU regardless of what settings might be applied later. If multiple GPOs are applied with the Enforce option, the setting that is enforced first will win. This is the reverse of the usual GPO processing rules.
-
Block Inheritance applies to an entire site, domain, or OU, and prevents any GPO settings from being applied unless the GPO has the Enforce setting enabled.
-
Be aware of Enforce and Block Inheritance settings, since they will cause the usual inheritance and processing rules to no longer apply.
EAN: 2147483647
Pages: 122