Objective 1.2: Designing a Framework for Implementing Security
Designing a secure network framework can be broken into four conceptual pieces:
-
Attack prevention
-
Attack detection
-
Attack isolation
-
Attack recovery
While the measures we ll be discussing in this guide are specific to different aspects of the Windows Server 2003 infrastructure, each topic will map back to one of these four key principles. This can include disabling unnecessary Windows services to prevent network attacks, installing an IDS to alert you of any suspicious network activity, or designing an Incident Response Plan to facilitate recovery from an attack. In this section, we ll take a broad look at topics relating to each of these four principles.
To adequately prevent attacks against your network, you ll first need to determine what form they might actually take. We ll look at the STRIDE model of classifying network attacks as a starting point for both attack prevention and detection. While the number of network attacks has grown exponentially in recent time, understanding how a specific threat is acting against your network will greatly assist you in acting to circumvent any damage. Another component of attack prevention that we ll discuss is Risk Management, where you prioritize your resources to create a secure yet cost-effective network structure. Finally, we ll look at Incident Response as a way to both detect and respond to any malicious activity on your network.
Objective 1.2.1: Predicting Threats to Your Network
Predicting network threats and analyzing the risks they present to your infrastructure is one of the cornerstones of the network security design process. Understanding the types of threats that your network will face will assist you in designing appropriate countermeasures, and in obtaining the necessary money and resources to create a secure network framework. Members of an organization s management structure will likely be resistant to spending money on a threat that they don t understand; this process will also help them understand the very real consequences of network threats, and to make informed decisions about what types of measures to implement. In this section we ll discuss some common network attacks that you will likely face when designing a secure Windows Server 2003 network, and how each of these attacks can adversely affect your network.
When classifying network threats, many developers and security analysts have taken to using a model called STRIDE, which is an acronym for:
-
Spoofing identity These include attacks that involve illegally accessing and using account information that isn t yours, such as shoulder-surfing someone s password while he types it into his keyboard. This type of attack affects the confidentiality of data.
-
Tampering with data These attacks involve a malicious modification of data, interfering with the integrity of an organization s data. The most common of these is a man-in-the-middle (MITM) attack, where a third party intercepts communications between two legitimate hosts and tampers with the information as it is sent back and forth. This is akin to sending an e-mail to Mary that says The meeting is at 3 p.m . , but a malicious attacker intercepts and changes the message to The meeting has been cancelled.
-
Repudiation These threats occur when a user can perform a malicious action against a network resource and then deny that she did so, and the owners or administrators of the data have no way of proving otherwise . A Repudiation threat can attack any portion of the CIA triad .
-
Information disclosure This occurs when information is made available to individuals who should not have access to it. Information disclosure can occur through improperly applied network permissions that allow a user the ability to read a confidential file, or an intruder s ability to read data being transmitted between two networked computers. Information disclosure affects the confidentiality of your company s data and resources.
-
Denial of service So-called DoS attacks do not attempt to alter a company s data, but rather attack a network by denying access to valid users, by flooding a Web server with phony requests so that legitimate users cannot access it, for example. DoS attacks affect the availability of your organization s data and resources.
-
Elevation of privilege This type of attack takes place when an unprivileged , nonadministrative user gains administrative or root level access to an entire system, usually through a flaw in the system software. When this occurs, an attacker has the ability to alter or even destroy any data that he finds, since he is acting with administrative privileges. This type of threat affects all portions of the CIA triad, since the attacker can access, change, and remove any data that he sees fit.
When you are analyzing a potential network threat, try to remember the STRIDE acronym as a means of classifying and reacting to the threat. You can use the STRIDE model, not only to assist you on the 70-298 exam, but also throughout the life of your corporate network when designing and maintaining security policies and procedures.
Recognizing External Threats
Now that we ve discussed a model for classifying network threats, we can look at some of the more common attacks in more detail. While entire books can (and have been) be written solely discussing the kinds of threats that we ll be looking at in this section, we ll be giving you a birds-eye view of the kinds of attacks that your network security design will need to guard against.
| Test Day Tip | For more detailed information on the attacks we ll discuss in this section, check out the Syngress Publishing Security+ Study guide, Security+ Study Guide and DVD Training System (ISBN 1-931836-72-8). |
Denial-of-Service Attacks
As we ve already mentioned, the DoS attack (and its first cousin, the Distributed DoS attack) works to disrupt services on a network so that legitimate users cannot access resources they need. Some examples include attempts to disrupt the connection between two specific machines, or more commonly, attempts to flood an entire network with traffic, thereby overloading the network and preventing legitimate traffic from being transmitted. There can also be instances where an illegitimate use of resources can result in denial of service. For example, if an intruder uses a vulnerability in your FTP server to upload and store illegal software, this can consume all available disk space on the FTP server and prevent legitimate users from storing their files. A DoS attack can effectively disable a single computer or an entire network.
A common venue of attack for DoS is against an organization s network bandwidth and connectivity; the goal of the attacker is to prevent other machines from communicating because of the traffic flood. An example of this type of attack is the SYN flood attack. In this type of attack, the attacker begins to establish a connection to the victim machine, but in such a way that the connection is never completed. Since even the most powerful server has only a certain amount of memory and processor cycles to devote to its workload, legitimate connection attempts can be denied while the victim machine is trying to complete these fake half- open connections. Another common DoS is the so-called PING of Death, where an attacker sends so many PING requests to a target machine that it is again overloaded and unable to process legitimate network requests.
An intruder might also attempt to consume network resources in other ways, including generating a massive amount of e-mail messages, intentionally generating system errors that need to be included in Event Viewer logs, or misusing FTP directories or network shares to overload available disk space. Basically, anything that allows data, whether on a network cable or hard drive, to be written at will (without any type of control mechanism) can create a denial of service when a system s finite resources have been exhausted by the attacker.
Distributed Denial-of-Service Attacks
Distributed denial-of-service (DDoS) attacks are a relatively new development, made possible (and attractive to attackers ) by the ever-expanding number of machines that are attached to the Internet. The first major wave of DDoS attacks on the Internet appeared in early 2000, and targeted such major e-commerce and news sites as Yahoo!, eBay, Amazon, Datek, and CNN. In each case, the Web sites belonging to these companies were unreachable for several hours at a time, causing a severe disruption to their online presence and effectiveness. Many more DDoS attacks have occurred since then, affecting networks and Web sites large and small.
| Exam Warning | While most publicity surrounding DDoS attacks has focused on Web servers as a target, remember that any computer attached to the Internet can fall victim to the effects of a DDoS attack. This can include everything from file servers or e-mail servers to your users desktop workstations. |
The DDoS attack begins with a human Attacker using a small number of computers, called Masters . The Master computers use network scanners to find as many weakly secured computers as they can, and use system vulnerabilities (usually well-known ones) to install a small script or a service (referred to in the UNIX world as a daemon ) onto the insecure computer. This machine has now become a Zombie, and can now be triggered by the Master computer to attack any computer or network attached to the Internet. Once the organizer of the DDoS attack has a sufficient number of Zombie machines under his control, he will use the Zombi-fied machines to send a stream of packets to a designated target computer or network, called the Victim . For most of the attacks, these packets are directed at the victim machine. Figure 1.4 provides a graphical illustration of the Master-Zombie-Victim relationship.
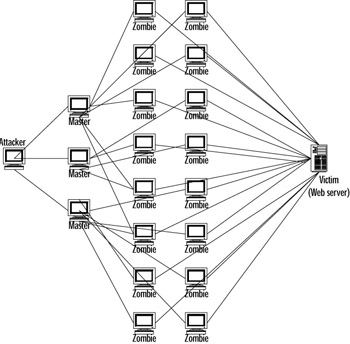
Figure 1.4: Illustration of a DDoS Attack
The distributed nature of the DDoS attack makes it extremely difficult to track down the person or persons who began it; the actual attacks are coming from Zombie machines, and the owners of these machines are often not even aware that their machines have been compromised. Making matters even more difficult, most network packets used in DDoS attacks use forged source addresses, which means that they are essentially lying about where the attack is coming from.
Viruses, Worms, and Trojan Horses
Viruses, Trojans, and worms are quite possibly the most disruptive of all of the security threats that we ll be discussing in this section. These three types of threats, working alone or in combination, can alter or delete data files and executable programs on your network shares, flood e-mail servers and network connections with malicious traffic, and even create a back door into your systems that can allow a remote attacker to take over control of a computer entirely. While you ll often hear these three terms used interchangeably, each one is slightly different. A virus is a piece of code that will alter an existing file, and then use that alteration to recreate itself many times over. A worm simply makes copies of itself over and over again for the purpose of exhausting available system resources. A worm can target both hard drive space and processor cycles.
| |
Combating Network Attacks
Given the widespread nature of DDoS attacks and the difficulty in tracing their source, you might wonder if there is anything you can do to protect your corporate network against this ever-growing threat. While nothing will ever render your network 100 percent immune, there are a number of practices that you can follow that will help to minimize your exposure to DDoS and other types of network attacks.
-
Stay up to date with Microsoft Security Bulletins. Most DDoS attacks target well-known operating system vulnerabilities that have a patch available. Some particularly damaging DDoS attacks have targeted OS vulnerabilities that had had a patch available for two years , but that most administrators had not bothered to install.
-
Use built-in operating system security measures. Using System File Checking (SFC) for your Windows 2000 and Windows XP workstations will alert your users to any attempt to update any critical system files. Windows XP also has a built-in personal firewall that will greatly strengthen your workstations defenses.
-
Keep your antivirus software updated. If you don t use anti-virus software, now would be a great time to investigate some. The major vendors have become quick to respond to any new threats, greatly reducing the likelihood that a machine with updated anti-virus definitions will fall prey to a DDoS or Trojan.
-
If you are an administrator, use your administrative account with discretion. Create a second nonadministrative user account to perform everyday activities ”a Trojan can do far more damage if it is allowed to run as an administrative account.
| |
| Exam Warning | A computer virus typically targets the integrity of data by altering its contents. A worm primarily attacks data s availability by targeting system resources as a whole. Of course, a major virus attack will eventually affect the availability of your data as well, but its initial attack vector is concerned with attacking data integrity. |
Trojan horses take their name from a Greek myth, in which attackers from Sparta infiltrated the Greek city of Troy by hiding inside a horse statue masquerading as a gift. When the Trojans brought the gift inside the city walls, they discovered too late that it was filled with Spartan soldiers who emerged from within the horse and took over the city. In similar fashion, a computer-based Trojan will disguise itself as a friendly file, usually an e-mail attachment. This file, when executed, can damage computer data or install a back door into the operating system that will allow a remote attacker to take over the system entirely.
| Note | For more information about computer viruses and other similar threats, check out the Syngress Publishing book guide to Configuring Symantec AntiVirus Corporate Edition (ISBN: 1-931836-81-7). |
Software Vulnerabilities
Some network attacks target vulnerabilities in the way that a software application or entire operating system has been programmed. For example, a buffer overflow attack occurs when a malicious user sends more data to a program than it knows how to handle. For example, you ve all seen Web forms that ask you to fill in your personal information: first name, last name, telephone number, and so forth. A careless developer might program the First Name field to only be able to handle 10 characters ; that is, a name that is 10 letters long. If the Web application does not check for buffer overflows, an attacker can input a long string of gibberish into the First Name field in an attempt to cause a buffer overflow error. At this point, the attacker could even embed the name of an executable file into that long string of text and actually pass commands to the system as if he or she were sitting at the server console itself. A similar software vulnerability is a format string vulnerability that would allow an attacker to insert random data into a file or database, once again including malicious code that can be executed against the server as if the attacker were sitting right in front of the keyboard.
Another attack that is specifically common to Web and FTP servers is a directory traversal vulnerability . This type of vulnerability allows a user to gain access to a directory on a server that he hasn t been specifically given permissions to, by virtue of having permissions to a parent or child directory. Say someone goes to the following URL: www.airplanes.com/biplanes/cessna/model1.html. He decides to manually change this URL (in other words, not following an <HREF> link on the site itself) to www.airplanes.com/biplanes/piper, to see if the directory structure holds any information there. If the Web site hasn t been properly patched and configured with the correct security settings, the user might find that he now has access to every single file in the piper / directory. Even worse , he can once again execute a command from the Web browser by changing the URL to something like www.airplanes.com/biplanes/piper/del%20*.*. ( %20 is used in HTML to represent a space, so that command would read del *.* on a regular command line.) Another common attack also occurred in NetMeeting and Windows Media Player some time ago, where an attacker could insert special characters during a file transfer that would allow him to browse an unsuspecting user s hard drive directory structure.
Nontechnical Attacks
A final category of attacks that we ll discuss here are those that use less technical means to circumvent network security. So-called social engineering attacks rely on an unsuspecting user s lack of security consciousness. In some cases, the attacker will rely on someone s goodwill, using a tactic like I ve really got to get this done and I don t have access to these files, can you help me? (Since at heart, most of us really want to be helpful to those around us.) Other social engineering attacks will use a more threat-based approach, insisting that the attacker is the secretary for Mr. Big-Shot VP who needs his password reset right away and heaven-help-you if you keep him waiting. This relies on the assumption that a show of authority will cause someone without adequate training to bypass security procedures to keep the big-shot important user/client happy. Since social engineering attacks are nontechnical in nature, the measures required to defend against them are more administrative than anything else is. It s critical to have well- understood security policies in place that apply to everyone, regardless of their position in your company. This will assist in preventing an attacker from circumventing security procedures because a help desk or other staff member is unaware of them.
| |
Blended Threats
As if it weren t hard enough to keep track of viruses, worms, and other similar attacks, the information security industry has coined a new term for a type of attack that blends the worst of both. Blended threats combine many of the characteristics of viruses, worms, Trojan horses, and attacks against software vulnerabilities to increase the rate at which they can spread and cause damage. If you ve dealt with the fall-out of threats like Code Red (which began circulating in 2001), Klez, and the like, you ve already seen how insidious a blended threat can be.
Blended threats spread using multiple methods , usually beginning with a malicious e-mail attachment. Once the unsuspecting user launches the attachment, the now-infected machine will use a network-based attack to scan for vulnerabilities in other systems, including embedding code in HTML files on a Web server, sending a deluge of virus-infected e-mail from a compromised e-mail server, or altering files on an internal server s network shares. Even worse, these attacks are able to spread without any human intervention ”they continuously scan the local network or the Internet for new systems to attack and infect .
The Nimda worm presents a perfect example of how a blended threat operates and spreads . Machines were initially compromised by Nimda through an e-mail attachment that exploited a software vulnerability in Microsoft Outlook and Outlook Express. This software vulnerability allowed the infection to spread without the user s intervention, or even awareness. Once a desktop machine was infected, Nimda began to perform network scans to attack network shares and Web servers using a yet another software vulnerability in Internet Information Server.
The Internet Explorer vulnerability enabled Nimda to infect a Web server in such a way that any user who connected to the site would automatically have malicious code downloaded to his or her desktop, thus continuing the infection cycle. With so many venues to continue the spread of the virus, it s no wonder that Nimda caused worldwide havoc on many home and corporate networks.
The emergence of blended threats presents a huge challenge for Information Security professionals, since threats such as Nimda can now spread much more quickly than any of their nonblended predecessors. Without proper planning and monitoring, a network can become overloaded with a virus outbreak before an administrator is even aware of the problem. Moreover, since blended threats spread through methods other than just e-mail attachments, security professionals need to find new ways to secure other forms of network traffic such as Web server and file server traffic.
| |
What Motivates External Attackers?
Just as you need to know why? a company is designing a security infrastructure, it s also helpful to know the reasons why total strangers seem compelled to make your life as a network administrator that much more difficult. Network attackers, usually referred to colloquially as hackers , attempt to break in to corporate networks for any number of reasons, and sometimes knowing the reason why they are doing so can assist you in defusing the threat and tracking down the perpetrator.
The most common, although perhaps not the most obvious, reason for attacking a company s network is to gain fame or notoriety. Whether it is someone seeking acceptance from an online hacker community, or someone who simply wants to see his or her name in the papers, attacks motivated in this manner tend to be extremely public in nature. A common attack in this category is Web site defacement, where an attacker will exploit a vulnerability in a company s Web server and change their default Web page to read something embarrassing or self-aggrandizing. Imagine if you went to the Web site of a company you were accustomed to dealing with and you were presented, not with the familiar home page, but a page containing offensive images or phrases like The HAXOR Group 0WNS This Site! Companies that are the victims of these attacks find themselves facing public embarrassment and financial loss, while the perpetrators often brag about the successful attack or laugh at the news reports of the company s dismay.
Another common phenomenon is the hacker who breaks into networks for fun; they enjoy the challenge of defeating an undefeatable security system. This can be anyone from a college student attempting to flex his computing muscles against Internet-connected machines, to an internal employee who just wants to see what she can get away with on the office PC. In many cases, these attackers do not consider their actions unethical or immoral, their thinking being that if the vulnerability hadn t been there in the first place, I wouldn t have been able to exploit it.
The last category of attackers that we will discuss (although this list is by no means complete) are those who are motivated by personal gain, either hacking for pay or as a means of exacting revenge . In the case of the former, this can range from simple criminal actions to attackers performing industrial espionage (trying to steal the secret formula from the database server) or even information warfare between governments . The revenge attacker is typically a former employee of a company, who might plant a logic bomb to damage networking resources after he or she has been fired or laid off.
| Test Day Tip | A logic bomb is a type of attack, whether a virus, worm, DDoS or Trojan, that lies dormant until triggered by a specific event. This event is usually associated with a date, such as the now-famous Michelangelo e-mail virus that was triggered to be released on the date of the artist s birthday. |
Implementing Risk Analysis
A favorite Information Security lecturer of mine once commented that the only way to have a truly secure computer was to unplug the network cable from the wall, remove the keyboard, mouse, and monitor, and dump the CPU in the middle of the ocean. While this is a somewhat sarcastic statement, the message is clear: no computer network will ever be completely free from security risks. When designing security for your network, therefore, a large part of your job will actually be a matter of Risk Management ”deciding how to use finite resources to provide your company with the best security measures possible. When creating a Risk Analysis strategy, you should involve staff from areas other than IT, including your company s Legal and Finance departments, to assist you in assigning values to various projects and assets. Anyone who plays a leadership role in any project or product that your company is working on should have a say in the Risk Analysis process.
The first step in implementing a Risk Analysis strategy is assessing the value of your assets and resources. Some assets, such as physical servers, networking hardware, and cabling, are relatively simple to assign a value to, based on their purchase price minus any depreciation from the accountants . Other items will need to be valued according to the cost of producing them ”the salaries of programmers during the development of a new software application, for example ”or the cost to the company if something were lost. Assigning a concrete monetary value to something like a lost sales lead caused by an e-mail server outage can be difficult, but the Risk Analysis process cannot be successful without having this information available.
Next , you need to identify the potential risks to each asset in turn , including (but not limited to) the kinds of attacks that we ve already discussed in this chapter. For each potential attack, you ll define the potential damage that could be done to each asset, again in monetary terms. To use our example of a lost sales lead resulting from an e-mail server outage, let s say that the company Sales Manager does some research and determines that your company loses about $1,000 an hour when the e-mail server is unavailable. Last year, the e-mail server was unavailable for 20 hours when it became overloaded with messages created by the various viruses. You can use this to determine that virus threats cost your company $20,000 last year. You can use this sort of equation to assign a value to most types of security risks faced by your company, allowing you to prioritize your budget and resources where they will do the most good.
Addressing Risks to the Corporate Network
Once you have created a prioritized list of risks to your network, as well as their associated costs, your next step will be to determine a course of action in handling each risk. When deciding how to address risks to your network, you typically have one of four options:
-
Avoidance You can avoid a risk by changing the scope of the project so that the risk in question no longer applies, or change the features of the software to do the same. In most cases, this is not a viable option, since eliminating a network service like e-mail to avoid risks from viruses would usually not be seen as an appropriate measure. (Network services exist for a reason; your job as a security professional is to make those services as secure as possible.) One potential example of how avoidance would be a useful Risk Management tactic would be a case where a company had a single server that acted as both a Web server and a database server housing confidential personnel records, when there is no interaction whatsoever between the Web site and personnel information. Purchasing a second server to house the employee database, removing the personnel database from the Web server entirely, and placing the employee database server on a private network segment with no contact to the Internet would be a way of avoiding Web-based attacks on personnel records, since this plan of action removes a feature of the Web server (the personnel files) entirely.
-
Transference You can transfer a risk by moving the responsibility to a third party. The most well-known example of this is purchasing some type of insurance ”let s say flood insurance ”for the contents of your server room. While the purchase of this insurance does not diminish the likelihood that a flood will occur in your server room, by purchasing insurance you have ensured that the monetary cost of the damage will be borne by the insurance company in return for your policy premiums. It s important to note that transference is not a 100-percent solution ”in the flood example, your company will likely still incur some financial loss or decreased productivity in the time it takes you to restore your server room to working order. Like most risk management tactics, bringing the risk exposure down to zero in this way is usually an unattainable goal.
-
Mitigation This is what most IT professionals think of when implementing a Risk Management solution. Mitigation involves taking some positive action to reduce the likelihood that an attack will occur, or reduce the potential damage that would be caused by an attack, without removing the resource entirely as is the case with avoidance. Patching servers, disabling unneeded services, and installing a firewall would be some solutions that would fall under the heading of risk mitigation.
-
Acceptance After you have delineated all of the risks to your infrastructure that can be avoided, transferred, or mitigated, you are still left with a certain amount of risk that you won t be able to reduce any further without seriously impacting your business (taking an e-mail server offline as a means to combat viruses, for example). Your final option is one of acceptance, where you decide that the residual risks to your network have reached an acceptable level, and you choose to monitor the network for any signs of new or increased risks that might require more action later.
Test Day Tip When determining the cost-effectiveness of a safeguard, remember this formula: The total savings to your organization is the amount of money that the safeguard will be saving you, minus the cost of the safeguard itself. Therefore, if you install a $25,000 firewall that you estimate will save you $100,000 from downtime due to hacker intrusions, the total cost savings provided by the firewall is:
$100,000 (savings) “ $25,000 (cost of safeguard) = $75,000 net savings to the organization.
Objective 1.1.3: Analyzing Security Requirements for Different Types of Data
Once you ve gone through the Risk Analysis process, you should have a good idea of what types of data are present on your network and how much the loss of each type of data will cost your organization, both in a quantitative and qualitative sense. At this point, it s often helpful to classify data into discrete categories to assist you in securing your information in an efficient manner. Many organizations use a four-tiered classification system that organizes data and resources into one of four categories:
-
Public This might include informational items such as product listings on the corporate Web site and press releases issued by Marketing or Public Relations. There is probably little risk associated with someone attempting to steal this data, since it is assumed to be common knowledge among a company s customers and competitors . However, the integrity of this data still needs to be maintained to retain consumer confidence and potential sales. (Imagine the impact if a press release were altered to read that your company suffered a 10-percent loss in sales, rather than posting a 20-percent growth.)
-
Private This will include information that might be widely known within your company, but perhaps sufficiently sensitive that you do not want to share it with the world at large. Data contained on a corporate intranet might be included in this category, since it often includes contact information for specific personnel, as well as information concerning internal systems that might not be appropriate for release to the public.
-
Confidential This is the kind of information (along with Secret data) that most of us think of when we begin constructing a security plan. This can include information like customer financial records or corporate payroll information. The disclosure or alteration of data of this nature would almost certainly lead to real losses to the company, whether in terms of financial loss or reputation.
-
Secret This is the most confidential classification of data, and most often extends to intellectual property such as trade secrets, patent information, or upcoming products and ventures . The loss or defacement of secret data would be almost irreparable, since a trade secret that has been disclosed to the public or to competitors cannot simply be made secret again with the wave of a wand. Data at this level must be afforded the most stringent protection levels within your corporate network.
After you have classified your organization s data and resources, you can use this information to assign different security templates or policies to the different categories. This will increase the efficiency of your network security design, since you will be able to more easily assign similar or identical security measures to data that has similar security requirements. It will also save you from wasting time or effort assigning the same level of protection to, say, your company s softball schedule that you assign to more critical information such as sales or payroll data.
Objective 1.2.2: Responding to Security Incidents
Despite the best security infrastructure design, an unfortunate reality of modern networks is that it s usually not a case of if you will need to address an attack against your network, but when . This is why it s crucial to formulate a security response plan before you need one, so that your company s personnel (both technical and nontechnical) will know how to respond to a network security breach. If left unchecked, a security breach can lead to stolen or corrupted data, identity theft, and embarrassing negative publicity for your company. An Incident Response plan details the actions that you take when a security incident occurs, allowing you to react to any security breaches in a rapid and efficient manner. It s also critical that your Incident Response plan has support throughout your organization and is tested on a regular basis to ensure that it addresses all necessary concerns. This includes creating detailed procedures and defining the roles and responsibilities of everyone on your staff so that everyone can act in concert. By staging practice emergencies and measuring how well and how quickly your staff can respond to them, you can minimize the impact that a security breach will have against your organization.
Recognizing Attack Indicators
When a network attack occurs, the key to minimizing any damage to your company s assets is rapid response. But how can you react to a network attack if you don t know that one is occurring? Recognizing the signs of an attack is the crucial first step in limiting the fallout of an incident such as a hack or virus attack. And you can only recognize when something is wrong on your network when you understand how things are supposed to look when they re right . Because of this, it s important to create a baseline of your network as early as possible. A network baseline will include such details as:
-
Average %processor utilization on a specific server
-
RAM usage and statistics such as average page faults/second
-
Average %network utilization on a network segment
You should also be aware of specific times of the day, week, or month when your network baseline is predictably higher or lower ”your network utilization might spike while transmitting sales figures at the end of each day. Alternately, a server s processor utilization might be extremely low at 2 a.m ., so that 40 percent utilization might be a cause for alarm at this time when it wouldn t necessarily be so during the 9 a.m. to 5 p.m . day. A good network baseline should include data sampled at several points during the day over several weeks or a month, so that you can obtain a complete picture of the state of your network when it s operating under normal conditions.
Perhaps the most important tool in obtaining a network baseline and subsequently recognizing any adverse conditions is the use of auditing . Using the audit logs in the Windows Server 2003 Event Viewer will alert you to any errors or system events that might be occurring on your network. If you are running a Web server using IIS or using ISA or a third-party firewall solution, you will also have detailed information available through the separate audit logs for these applications or hardware components .
| Exam Warning | For auditing to function correctly in an enterprise environment, you need to use time synchronization so that audit logs from multiple machines will all correctly reflect the time that events occurred. |
Creating an Incident Response Plan
Incident Response refers to how your organization reacts to a network attack or any other type of security incident. Without an Incident Response plan, your company s reaction to such an attack will be unorganized at best, chaotic at worst. This lack of organization in and of itself can cause additional damage stemming from confusion in the wake of a security incident. Now that we ve discussed how to recognize when an attack against your network is occurring, we ll move on to how to react to any breaches that occur. Whether you have a dedicated Incident Response Team, or include Incident Response with the duties of a network administrator or engineer, it s crucial to delineate exactly what those responsibilities are. You can separate the components of an Incident Response Plan into four logical steps:
-
Response
-
Investigation
-
Restoration
-
Reporting
The first step when drafting an Incident Response plan is deciding how you will respond to a network security incident. Your first instinct might be to power down the computer and immediately begin to work on resolving the incident. And while the restoration of network services is a crucial piece of Incident Response (and one we ll talk more about later), taking a few minutes to collect some information about the current state of the machine being attacked can assist immensely in determining how and why the attack occurred, and provide clues to better prevent a similar attack from happening in the future. At a minimum, you should record the following information before beginning to work on the machine:
-
Machine name and IP address
-
Operating system and service pack level
-
Running services and processes
-
Copies of all Event Viewer log files ”Application, System, Security, and any machine-specific logs like File Replication or DNS.
-
Evidence of intruder activity ”any files that have been changed or removed, rogue processes listed in Task Manager, and so forth. At this point, you should be able to define the type of attack ”is this a DoS attack? A software attack that has compromised your system integrity?
-
Source of the attack ”while you can t always be 100 percent accurate, you can use the Event Viewer and other access logs to determine where an attack is coming from. This can assist you in containing the attack, as we ll discuss in a moment.
-
A list of who is dependent on this server and who will need to be notified of any downtime ”developers, specific departments or offices, and so forth. Since a compromised system might need to be shut down or removed from the network rather quickly, any users who are dependent on this system need to be made aware of it so that they can plan their work accordingly .
Another critical step in responding to an incident is containing the intrusion so that no further damage is done to any additional network systems. Especially if the attack is ongoing, you need to prevent the intrusion from spreading. For example, if you are facing a DoS attack, you can set up filters at your firewall or border router to prevent any more packets coming from the attacker s IP address from reaching your network. In the case of a DDoS, there might be multiple points of attack, but measures such as these will at least minimize the effects of the attack on the rest of your network. And while you might not want to immediately power down the compromised computer so that you can collect information and evidence, you can certainly unplug the network cable to prevent the machine itself from further damaging any other resources, especially if the attack is one that has compromised the machine s operating system or other security functions.
| Test Day Tip | No matter what your plans for Incident Response are, you should disconnect any compromised machine from your network to prevent other machines from becoming infected or compromised. |
Analyzing a Security Incident
Once you ve recognized that a security incident is taking place, you should gather as much information as possible about the attack, the attacker, and the system that s being targeted. Take a snapshot of the machine, preferably before rebooting it or removing it from the network, and record a list of all running processes, open network connections, and any files and directories that are being accessed or altered. As we mentioned in the last section, having a baseline to compare this to can be immensely helpful in discovering what has gone amiss on the system in question. You or your system administrators should know which processes and services should (and should not) be running on any production server, and you should also have an idea of what sort of network traffic is normal or acceptable in order to detect any anomalies.
| |
Computer Forensics
Before you begin the recovery process, you ll need to decide whether your primary goal is restore the server to working order as quickly as possible, or to attempt to preserve the existing state of the machine in order to pursue (and potentially prosecute) the attackers. If your goal is to attempt to prosecute the attackers, it becomes critical not to tamper with any evidence that might be useful to law enforcement agencies. This begins to delve into the field of computer forensics.
Computer forensics is the application of computer skills and investigation techniques to aid law enforcement for the purposes of acquiring evidence relating to computer-based attacks. This primarily involves collecting, examining, preserving , and presenting evidence that is stored or transmitted in an electronic format, such as log entries and other files. Because the ultimate purpose of this evidence collection is that it might be used in court, you need to follow strict procedures in order for evidence to be usable in court or any internal action (like presenting information to Human Resources about an employee violating an AUP by using company resources to download unacceptable materials).
When a security breach has occurred, from a forensics standpoint you need to preserve the scene of the crime to the best extent possible. This means that any log files should not be changed in any way, and Last Accessed timestamps on files and folders must not be changed wherever possible. Additionally, you should make sure not to overwrite any data on the machine or transfer information to other systems without the use of encrypted transmission. This even extends to not powering down, rebooting, or changing any settings on the computer and photographing or otherwise documenting what is being displayed on the monitor in case power is lost while you are investigating. (Many computer-based attacks are only active as long as the machine is powered on; as soon as the machine reboots, all evidence of the attack and the attacker might be irretrievably lost.) There are now many specialized computer forensics tools that will allow you to make a complete copy of everything that is happening on a system so that the evidence of it can be preserved while you attempt to restore the compromised system to a working state. Finally, any evidence that is collected or removed from the scene needs to be stored in a detailed and systematic way. This chain of evidence documents who was in possession of the evidence at all times, and helps to prove that any information or data was not tampered with after the fact.
| |
Objective 1.2.4: Recovering Network Services After an Attack
Once you ve collected all of the incident tracking or forensics information you want, you can now turn to restoring a compromised machine to a healthy state. As with the rest of the Incident Recovery plan, you should document and test these steps beforehand as much as possible so that actual recovery times are as quick as possible, minimizing any downtime for your users. Unfortunately, once a system has been compromised, in many ways you can t trust any of the information that s stored on it because you don t know what the attacker has or has not changed. In most cases, for any system that has been breached, the best and most secure option is to reinstall the operating system from a clean copy of the installation media. Performing a full reinstallation will ensure that the affected system will be free of any Trojans, backdoors, or malicious processes that you might not even be aware of. Reinstallation also ensures that any data that s been restored from a known-good backup is also free of any unauthorized modifications. The obvious drawback to this is that rebuilding a system from scratch can be a time-consuming process. However, this downtime will be greatly lessened if you have redundant hardware that can be quickly brought online, as well as detailed system documentation. Your alternative to a full system recovery is to simply patch the affected system or run utilities designed to correct a specific attack. (Several major anti-virus vendors created utilities that were designed to remove the Nimda and Code Red worm infections from individual machines.) This method is less secure than a full reinstall and is only something you should do as a last resort. The danger with patching a system instead of reinstalling is that it s almost impossible to be sure if you ve completely cleared the system of Trojans, holes, or corrupted data.
The last step in recovering your system services is to address and correct the vulnerability that caused the security breach in the first place. This might seem self-explanatory, but without a well-defined Incident Response plan, many times you ll see an individual or organization simply place a machine back on the network only to have it attacked and breached again. This is where your initial analysis of the incident will become indispensable , since you need to determine the attacker s point of entry. Did the intruder enter your network through a buffer overflow attack? Be sure to patch the operating system and applications against this attack before returning the system to service. Were any passwords compromised? You should force any potentially compromised users to change their passwords, ensuring that they re using complex and hard-to-guess passwords for network access.
EAN: 2147483647
Pages: 122
- Chapter VIII Personalization Systems and Their Deployment as Web Site Interface Design Decisions
- Chapter IX Extrinsic Plus Intrinsic Human Factors Influencing the Web Usage
- Chapter XI User Satisfaction with Web Portals: An Empirical Study
- Chapter XIV Product Catalog and Shopping Cart Effective Design
- Chapter XV Customer Trust in Online Commerce