SPECTER
 |
| |||||||||||
| | |||||
SPECTER, by Network Security (http://www.specter.com), is an $899 GUI honeypot with a bunch of unique features. If you believe that a good offense is a good defense, then SPECTER may be for you. Contact sales@specter.com to obtain an evaluation copy of SPECTER.
SPECTER runs as an application-level honeypot on Windows 2000 Service Pack 2 or Windows XP Service Pack 1 and automatically checks online for weekly program updates. I reviewed version 7.0 for this chapter. It emulates 14 different OSs, including Windows 98, Windows NT, Windows 2000, Windows XP, MacOS, and a host of Unix flavors. It also offers 14 different TCP services: SMTP, FTP, telnet, finger, POP3, IMAP4, HTTP, SSH, DNS, SUN-RPC, a single customizable port, plus a few trojans (NetBus, Back Orifice 2000, and SubSeven). As shown in Table 8-1, SPECTER classifies seven of these as traps and seven as emulated services.
| Traps | Services |
|---|---|
| DNS | FTP |
| IMAPv4 | SMTP |
| SSH | HTTP |
| SUN-RPC | Telnet |
| Sub-7 | Finger |
| BOK2 | POP3 |
| Generic | NetBus |
Traps are simply ports that listen for and record probes, and terminate any connection attempts. The Generic trap is any TCP port you choose, but it can be only one, which is a bit limiting. The services will attempt to emulate services that would be present on the OS you choose. For instance, if you choose the Windows OS, it will emulate IIS, FTP, Exchange Server, and so on. The seven services can be customized slightly by adding your own content, banner screens, and user accounts. Some of the emulated services, like telnet, offer the remote hacker a login attempt (although the hacker never gets to log in). Others, like HTTP and POP3, allow more interaction, including logging in and getting content. On the downside, SPECTER cannot emulate anything besides these 14 TCP ports, and it doesn’t listen on UDP ports or ICMP.
SPECTER has many unique features, including markers, custom content, fake password files, and trace-back intelligence. SPECTER’s most interesting feature is its ability to mark the remote hacker. SPECTER can dynamically generate more than 100 different executable programs and can leave up to 32 markers on a hacker’s system. Theoretically, these markers might be used by law-enforcement agencies to prosecute hackers (although I don’t think they have been used this way yet).
SPECTER is at the top of its class in the area of built-in content. It contains documents, e-mail messages, web pages, and even fake user accounts and passwords. It also is the only honeypot I know to dynamically generate fake content. And when it does its weekly program update, it can change its content, vulnerabilities, and markers. It can generate fake Windows password files with varying levels of difficultly for hackers to download.
SPECTER’s automatic intelligence options include finger, traceroute, port scanning, whois, DNS lookups, and even banner grabbing. This allows, at the administrator’s option, for the remote hackers to be probed and fingerprinted while they are doing the same. This feature should be used with caution, as the aggressive response might alert the attacker.
Setting Up SPECTER
Installing SPECTER is as simple as running the Setup.exe file. Once installed, SPECTER’s very busy Control screen comes up, as shown in Figure 8-3. SPECTER’s GUI doesn’t follow the normal conventions of placing the less important features and branching selections under higher-level menus, so you see a lot of details on this one screen. But if you are looking for a honeypot with all its configuration settings in one place, this is the GUI for you.
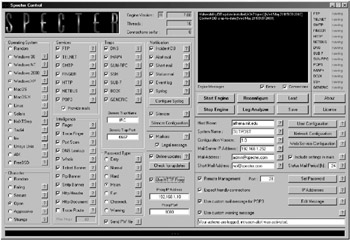
Figure 8-3: SPECTER’s main Control screen
SPECTER has limited context-sensitive help text that you can access by clicking the ? button beside each option. Enabling or disabling many settings, such as OSs, port listeners, and characters, is as easy as a mouse click. There are six different characters available for each emulated OS:
-
Random: The system randomly rotates through the next three character states.
-
Open: The system behaves like a poorly secured OS.
-
Secure: The system behaves like a well-configured OS.
-
Failing: The system behaves like a machine with various hardware and software problems.
-
Strange: The system behaves unpredictably and leaves the intruder wondering what’s going on.
-
Aggressive: The honeypot collects information on the hacker, and then reveals its true role and ends communication. That could shake up the remote attacker.
The vulnerabilities presented by each character changes randomly to make honeypot identification harder. The settings can be changed remotely.
Logging and Alerting with SPECTER
SPECTER can log events to the screen, a local ASCII database, a Windows event log, mail message, or a remote Syslog. Figure 8-4 shows an example of an on-screen log.
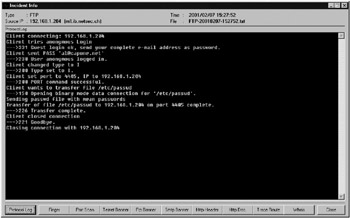
Figure 8-4: SPECTER’s on-screen log
SPECTER’s Log Analyzer, shown in Figure 8-5, lets you filter events by port and inspect the details of each attack. For example, you can view FTP passwords attempted, documents viewed, and directories changed. Multiple SPECTER computers can log their activity to the same remote database.
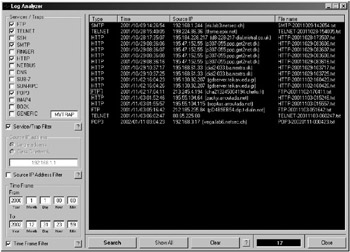
Figure 8-5: SPECTER’s Log Analyzer tool
On the downside, SPECTER, like most application-level honeypots, does not collect full packet decodes. For that reason, you should also run a packet sniffer along with SPECTER. Packet sniffing is discussed in Chapter 9.
Even when SPECTER is not detecting events or tracing hackers, it sends out periodic messages to let you know the honeypot is up and running. This heartbeat feature is a welcome administrative nicety when your honeypot is located remotely. SPECTER, like KFSensor and PatriotBox, comes with built-in anti-DoS coding. It keeps track of system utilization, and it will stop accepting new connections and probes when a limit is reached.
The vendor expects version 8.0 to be out soon. Its provisional feature set upgrades include second-generation markers, Windows Server 2003 emulation, MacOS X simulation, RPC emulation, NetBIOS emulation, ICMP detectors, and active protection of production servers.
| | |||||
EAN: 2147483647
Pages: 119