5.6 Macro Virus Technologies
5.6 Macro Virus Technologies This section of the chapter will cover how macro viruses work and the different technologies they use to spread. I will give more coverage to Word and Excel viruses because they represent the vast majority of macro viruses in the wild. Viruses for Access, PowerPoint, Corel Draw, etc. spread using similar concepts with different replication approaches and macro commands. 5.6.1 Word InfectionsWhen Word opens any document, it looks for macros included in the document, or its associated template. All macros are loaded into memory and any automacros are executed, if allowed by security. If the document or template contains any macro viruses they can infect other documents and templates, including the global template. Now, Word is infected, and any new documents created are infected by default (see Figure 5-10). Figure 5-10. Word macro virus infection pathway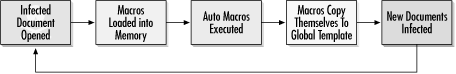 Typically, menu options are rewritten by malicious macros to help the infection process. For example, a macro with the name FileSave will allow a programmer to redirect what happens when a Word user chooses File
5.6.2 Excel InfectionsThe Excel macro virus, Laroux, is one of the most widely reported virus infections in the world today and is a good example to talk about. Written in 1996, it used VBA 3.0 to infect Excel 5.0 and later versions. When an infected workbook is opened, the virus uses the Auto_Open macro to hand over control to the main virus macro, check_files . The virus then checks to see if it has infected the current workbook and looks to see if an infected copy is stored in Excel's startup directory. If not, it infects the current workbook by creating a hidden infected sheet, and saves a copy of itself to a file created in the startup directory so that it gets loaded every time Excel starts. It then infects every sheet that is clicked on. It contains no intentionally destructive routines, but can still cause problems because of its lack of error checking. Macros and data can inadvertently be overwritten as the virus goes to work. 5.6.3 General Macro Virus TechniquesAdvances in antivirus technology and Microsoft security changes forced macro virus writers to learn new tricks. This next section talks about macro virus technologies beyond the early examples. 5.6.3.1 Class module virusesVisual Basic for Applications, Versions 5 and later, can be used to write class modules for Office 97 and later applications. A class module is a programming construct that creates a new object type (an object is a programming element that has a name, associated properties, methods , and events) that can be manipulated and extended with a minimal amount of coding. Objects can be other modules, documents, or graphics. More relevant to us, virus writers can use class modules to write viruses that infect documents, much like macro viruses, but they aren't classified as macros. If modules are declared private then they will not show up in Organizer, although they can usually be seen and removed with VBE. Office applications come with many built-in class objects, and class viruses will often use the built-in objects to do their work, much like a macro virus would with a global template. For example, every Word document (97 and above) contains a class module called ThisDocument and Excel contains ThisWorkbook . The polymorphic Poppy virus was the first class virus. It copies its code from a temporary file it creates on the hard drive to the ThisDocument object that is always attached to a Word document. It eventually displays a message on the 14 th of the month saying, "VicodinES Loves You/Class.Poppy. I Think <user name> is a big stupid jerk." The <user name> variable is replaced with the current document's author's name, as registered in Office. Initially, class modules were not interrogated by antivirus scanners, and as such, class viruses had a free ride for a few months. But then the antivirus scanners were rewritten to look for and scan documents with class modules, and began to detect the new types of viruses. Class viruses haven't proven to be anymore difficult to detect than regular macro viruses. However, they were a bit harder to remove. The ThisDocument module must always remain attached to a Word document and cannot be removed. Thus, antivirus scanners have to remove the virus coding in such a way that it doesn't cause the document to crash. 5.6.3.2 Office disables macro copying commandsMost early Word macro viruses used the MacroCopy or OrganizerCopy commands to spread themselves . Microsoft's SR-1 Microsoft Office Update modified Office so that a macro could not copy its code from a template to a document, effectively ending the lives of many macro viruses. Virus writers learned to get around the new constraints by exporting their code into a temporary file on the hard drive (using VBA's PRINT or EXPORT commands). Often this file has a .SYS extension to fool the user into thinking it is a necessary system file, if found by mistake. These files are composed of text and can easily be read by any text editor. Virus writers then use VBA's import feature to copy their code to the appropriate place in the application; the global template in Word. The VBA code to export and import looks something like the code in Example 5-1. Example 5-1. Importing and exporting virus code with VBA Application.VBE.ActiveVBProject.VBComponents("Test").Export "C:\CDD.SYS" VBComponents.Import("C:\CDD.SYS") You should be highly suspicious of any code writing files to your root directory or system file areas. The first class infector, WM.Ethan , creates a hidden, system file in the root directory called ETHAN.__ _, which contains the virus code. The special file attributes can be removed and the file deleted. 5.6.3.3 MRU exploitsOther macro viruses have gotten around the template-to-document limitation by infecting files in the user's Most Recently Used list. It is the list of recently used documents that Office applications display when choosing the File menu option. These types of viruses figure that if it is on your Most Recently Used list then there is a good chance that the user will be opening it again. The listed documents effectively allow the virus to once again load into memory, and until Microsoft stops document-to-document copying, these types of viruses have a way to spread. 5.6.3.4 Email virusesUnfortunately, using VBA it is all too easy for a virus to send itself to other victims using email. VBA allows a virus writer to query the system to get all the necessary information (email application name, user's name and email password) and send an attachment via email. MAPI , or Messaging Application Programming Interface , is the de facto standard for Windows email programs. It can be used by many computer languages to send email from a user's workstation to another user. Example 5-2 shows how the Melissa virus read the address book of infected users to get 50 recipient's email addresses to send itself to: Example 5-2. Melissa virus code sample ;Comments by Roger A. Grimes Set UngaDasOutlook = CreateObject("Outlook.Application") ;creating an instance of Outlook If System.PrivateProfileString("", "HKEY_CURRENT_USER\Software\Microsoft\ Office\", "Melissa?") <> "... by Kwyjibo" Then If UngaDasOutlook = "Outlook" Then ;if Outlook is the email engine... DasMapiName.Logon "profile", "password" ;get email user's name and email password For y = 1 To DasMapiName.AddressLists.Count ;set up getting ready to count number of contacts in address book Set AddyBook = DasMapiName.AddressLists(y) x = 1 Set BreakUmOffASlice = UngaDasOutlook.CreateItem(0) For oo = 1 To AddyBook.AddressEntries.Count Peep = AddyBook.AddressEntries(x) BreakUmOffASlice.Recipients.Add Peep x = x + 1 If x > 50 Then oo = AddyBook.AddressEntries.Count Next oo ;get up to 50 email addresses from address book ;end of Melissa code sample Using those lines of code, Melissa was able to spread around the world in three days and shut down the world's biggest email servers. It also earned its programmer a guilty conviction . The malicious emailing is done in the background without the user noticing, with the exception of some temporary computer slowness. Hundreds of macro viruses now use VBA and MAPI to send themselves around the world, effectively becoming a new class of worms. The proliferation of emailing viruses has led most corporations to install a virus scanning engine on their email servers to remove the virus before it gets to the end user. 5.6.3.5 Add-in virusesMicrosoft Office supports the inclusion of add-in programs. These programs are attached to a particular application and automatically executed when the application is started. Macro viruses will sometimes load themselves as an add-in, accomplishing the same objective of always being active in memory without touching the global template. 5.6.3.6 Stealth macro virusesAs macro viruses have become more popular, Microsoft has developed different notification methods that should alert the user that something is wrong. Unfortunately, all of these notifications are easy for macro viruses to disable, and even when they aren't, most end users don't understand what the warnings are trying to communicate. With Office 97 and 2000, the macro virus warnings are written a bit more clearly. Macro viruses have a handful of ways to hide themselves from default end-user inspection, although most of the stealth routines will not take place until after the user has ignored the original warnings and accepted the virus first. A macro virus cannot disable preset warning prompts and settings during its first activation. The most common setting simply warns you of any document containing a macro, whether or not the macro is malicious.
Viruses can modify the registry settings to stop Office from notifying the user of any macros. Other security settings can be disabled in VBA by writing the appropriate macro command to an infected template. The following macro commands all contribute to hiding the virus's activities:
Another common stealth technique is to disable the Tools In Word Basic, macros can be marked as Execution-only with a simple command-line switch when copying a macro: Example: MacroCopy "Test.Dot:AAAZFSA", "Global:FileSaveAs", 1 The 1 tells WordBasic to make the macro Execution-only. Execution-only macros cannot be viewed or edited, although they are not especially encrypted. The Edit button will be grayed out whenever an Execution-only macro is selected. File editors can still view the file and make out subroutines, function names , and comments. VBA allows macro viruses to "lock" themselves from viewing and can only be viewed if the user knows the correct password. However, if the VBA project is password protected, no modules can be copied for it. So, only viruses that use a very limited set of replication mechanisms (ones that either copy the file as a whole -- like X97M/Papa.B -- or ones that copy the data of the target file to the one containing the virus and then overwrite the target file with the modified infected one -- like X97M/Jini.A does) can exist. 5.6.3.7 Encrypted and polymorphic macro virusesLike their executable counterparts, many macro viruses change their appearance to avoid scanning detection. Random encryption routines are used to hide the virus code, but the cipher routines tend to be weaker than their executable virus counterparts. Some viruses randomly rename the macro names and memory variables . Others create their macros on the fly. They do this by storing most of the macros as plain text within the document, and calling a built-in macro builder. The macro builder then builds the macros and executes them. 5.6.3.8 Dropping off a friendOne of the scariest mechanisms a macro virus can contain is a routine to install a more dangerous virus or Trojan. Although most macro languages limit the scope of what can be manipulated by the application, sophisticated macro languages (like WordBasic and VBA) allow the external file and operating system to be modified. VBA and WordBasic allow external files to be created and existing files to be deleted or modified. Many macro viruses create a text file containing hexadecimal byte codes (assembly language commands) on a user's hard drive, and then modify the AUTOEXEC.BAT file so that the next time the PC is rebooted, DEBUG.EXE is called to compile the text file and convert it to an executable, and then it is executed. Thus, an even more malicious virus or Trojan can attack a computer. And all the user did was open a Word document sent by a friend or coworker. An early macro virus named Nuclear was the first to including a virus dropper (although the first versions were too buggy to work). Example 5-3 shows sample coding that could be used in conjunction with DEBUG.EXE to spread a virus (code is deliberately crippled). Example 5-3. Example of macro virus coding to drop off a file virus;First part of code creates the source code file to be compiled later Open "C:\VIRUS.SCR" For Output as #1 ;Source code called VIRUS.SCR Print #1, "N VIRUS.COM" ;Compiled code will be called VIRUS.COM ;Next commands write in hexadecimal codes Print #1, "E 0840 81 3C 44 75 21 80 3C 4D 74 12 80 3C 54 74 0D 8B" Print #1, "E 0850 44 01 48 8E C0 03 44 03 8E D8 EB E9 8D 03 26 2B" Print #1, "E 0860 44 F2 26 89 44 F3 1F 8C D8 2B E8 95 05 4D 01 2E" Print #1, "E 0870 8C 1E 8E 05 0E 1F A3 95 05 8E C2 B0 D6 A2 B4 04" Print #1, "E 0880 B9 DC 14 33 F6 33 FF FC F3 A4 8E D9 8C 06 E3 04" Print #1, "Q" ;Quit DEBUG.EXE Close #1 ;next create a batch file that will compile the virus ;needs to be added to autoexec.bat so that the next time the PC is ;rebooted, virus will run Open "C:\GOTYA.BAT" For Output as #1 Print #1, "debug<virus.scr>nul" ;Feeds source code into DEBUG.EXE command to compile file Print #1, "echo @C:\VIRUS.COM>>C:\AUTOEXEC.BAT ;inserts compiled virus into autoexec.bat file so it gets run after the ;next reboot. Close #1 ChDir "C:\" Shell "GOTYA.BAT", 0 ;Shell command runs batch file to compile virus and modify autoexec.bat ;end of example If you see code resembling Example 5-3, you can be almost 100 percent sure it is a virus or Trojan. 5.6.3.9 More external manipulation with VBAVBA contains plenty of functionality to allow macro viruses to interact with the PC outside of the scope of the application. Here are a few examples:
These four example commands can make any PC vulnerable to numerous types of attack. 5.6.3.10 Startup directory files Most Microsoft Office applications have a Startup directory defined under Tools 5.6.3.11 Random evolutionBecause macro viruses can contain many of the same macro names, such as AutoOpen or FileSaveAs , it is not uncommon for a document infected with two different macro viruses to end up creating a new virus that includes routines from each of the former. The WM.Colors.B macro virus contains Colors and Concept virus routines. Randomly evolving viruses have been speculated from the start (Dr. Fred Cohen discussed them frequently), but they were not a reality until the forgiving nature of the macro language appeared. There have been a few other variants produced from executable viruses, but the complexity of moving file pointers and entry points usually produces a nonreproducing offspring or one virus completely disables the other. 5.6.3.12 Construction kitsThere are dozens of Macro Virus Construction Kits that can create hundreds of different macro viruses. They allow nonprogrammers to churn out macro viruses with different levels of encryption, varying damage routines, and different display symptoms, and to trigger key off different events to deploy their payload. Luckily, as with most automated virus tools, macro viruses created by the same construction kit can usually be recognized using a common signature string by antivirus scanners. 5.6.3.13 Cross-platform infectorsEven with a common macro language, writing a virus to infect different applications is difficult work. Although the language is the same, the differences between applications require different code for each type of infector. Thus, the macro coding used in an Excel virus differs substantially with a Word virus. To infect both, a virus writer must include both in every virus, even though it might only infect Word at the present time. Getting the virus from one application to another is still difficult. Early cross-platform virus writers used Microsoft's interapplication communication channel called Dynamic Data Exchange (DDE). The first macro virus that was a cross-platform infector is called Strange Days. Cross-platform viruses are huge by virus standards, but in today's world of big code, it isn't usually a factor garnering premature recognition. Strange Days wrote its virus code to a temporary file on the hard drive and used VBA's Import and Export commands to infect Word and Excel. It uses the registry to find the appropriate Word and Excel directories and creates infected PERSONAL.XLS and NORMAL.DOT using VBA's PRINT command and DEBUG.EXE . Strange Days was a call to arms for virus writers and several new cross infectors showed up within weeks, each with a different method of infection.
5.6.3.14 Shiver cross-platform virusThe macro virus, Shiver, infects Word and Excel 97 documents and workbooks AutoOpen and Auto_Open macros. Within each application, Shiver spreads like any normal macro virus. It copies itself to the global template in Word and infects PERSONAL.XLS in the startup directory of Excel. It writes its viral code to a temporary file called SHIVER.SYS to import and export its code between applications. When exiting Word with the AutoExit macro, the virus uses DDE coding to run Excel in a minimized window and infects it by creating a PERSONAL.XLS document in Excel's Startup directory. From Excel, it uses DDE to copy the virus code stored in SHIVER.SYS into Word's global template, and creates a new template, WORD8.DOT that gets placed in Word's Startup directory. Shiver must start Word and Excel in a minimized state to do its dirty work. This symptom, Excel or Word suddenly starting and ending, should alert most users that something funny is going on. From Excel, Shiver sends the Alt-F11 keystroke to open Word's Visual Basic Editor. It then sends the keystrokes Ctrl-M to open VBE's Import feature. The virus code, SHIVER.SYS is then imported. It then closes VBE and Word with Alt-F4. To detect its own presence, Shiver creates and examines the following registry key: HKCU\Software\VBA Program Settings\Office\8.0\Shiver[DDE]. It leaves two new values, Alt-F11 and NoNos, to recognize itself. It has stealth capabilities as it disables menu commands in Excel and replaces menu commands in Word. It disables four different Office 97 macro virus warning options. The P98M.Corner macro virus uses similar infection techniques to infect both Word and Project. Shiver disables the Cancel key and delivers different random payloads. One payload renames the menu bar commands (File, Tools, etc.) in Word with lewd comments. A second one inserts "Shiver[DDE] by Alt-F11" into a random cell and changes its color in an infected Excel worksheet. A third routine uses VBA's WRITE command to display a bad poem that it wrote to a file called SISTER.DLL . 5.6.3.15 Language problemsDifferent language versions of Word present problems to macro virus writers. Although the automacro names are the same in most versions of Word, regardless of the language, the macros that control menu options are spelled differently in different languages. Thus, if a macro virus wants to control ToolsMacro functionality, the macro must be called ExtrasMakro in German and VerktygMarkro in Swedish. Most macro viruses are written for the English versions of Word, and thus won't work in other language versions if they contain menu macros. Some macro viruses, like WM.Telfonica, won't work in English versions of Word, and only works in the German version of Word. The WM.Friendly virus contains a complete set of macros in both English and German in its attempt to infect both types of systems (it contained a bug that prevented its spread on English systems). Some macro viruses, such as WM.Cap, attempt to solve the problem by assuming that even though the menu items are named differently in different languages, they are all located in the same position on the menu. This is not always true, and certainly isn't true between different versions of the same application. Thus, the virus can intercept calls to menu 1, position 6, instead of using FileSaveAs. Overall, there have been a few macro viruses that work in different languages, but they are the exception. Strangely, even macro viruses written in non-English countries are usually written for English versions of Word. I assume it's because most macro virus tutorials are in English or virus writers simply want to hit a bigger target audience. |
| | |
| Team-Fly |
| Top |
EAN: 2147483647
Pages: 176

