| Deciding whether or not to run an antivirus scanner is a no-brainer. Yes, you should. Deciding where to run it is harder. Antivirus products need to be placed in areas where new malicious code can be introduced. Antivirus scanners can run at the following locations: -
Desktop -
Email server -
File server -
Internet border 14.4.1 Desktop Almost every antivirus vendor offers a software solution designed to run on a PC's desktop. It was the first model type and is still the most popular. Desktop solutions offer the greatest reassurance when properly implemented and kept up to date. Three drawbacks exist. First, it is difficult to keep a large number of desktops updated and current, even with automated tools. It is easy for one workstation to get missed or bypassed, and one weak link can harm the rest of the network. Second, when located on a desktop, end users have the ability to disable the protection. And third, when loaded on the desktop, local performance can be severely impacted. Because of these three considerations, network administrators often look to place the antivirus software elsewhere. 14.4.2 Email Server Because most new malicious code is arriving via Internet email these days, installing antivirus software on email servers is popular. And for the most part it works. Incoming and outgoing email messages are scanned for malicious code. Regrettably, a large flaw exists. Email antivirus software can do nothing to malicious code located elsewhere. If it arrives on a floppy diskette, via FTP, from the Web, or from any other file server, email-based protection will do little to prevent its spread. Even if you have email-based antivirus scanning, users with third-party, HTML-based email accounts like Hotmail, can download and execute malicious code. For these reasons always install email-based scanners as an adjunct solution. 14.4.3 File Server Installing the antivirus scanner on the file server is another popular option. Located there, the software can scan all incoming and outgoing files. Local desktop performance is not affected because the scanning is being done on the server, and only one location, the file server, needs to be updated as new malicious code appears. There are a few drawbacks. One, file server-based scanners can be buggy , and cause the entire file server to crash. Two, only files stored or sent to the file server can be scanned. An infected document file opened on a floppy diskette will not trigger file server-based protection. Lastly, in most cases, the local PC has to be infected in order for the infection to eventually be noticed by the server. A locally infected MS Word document will infect the local MS Office copy, and be able to make modifications prior to the server-based software's involvement. 14.4.4 Internet Border Placing antivirus software on an Internet-connected firewall, router, or gateway, is becoming an ever more accepted place to run an antivirus scanner (see Figure 14-3). First, and foremost, it allows all incoming Internet packets (although in practice usually only HTTP, FTP, and SMTP packets) to be scanned for malicious code. Border devices can be preconfigured with the scanning software built-in, added as an internal or external adjunct feature, or used as a centralized update location, like SonicWALL 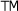 's (http://www.sonicwall.com) Internet Firewall's relationship with McAfee VirusScan. SonicWALL Network Anti-Virus 's (http://www.sonicwall.com) Internet Firewall's relationship with McAfee VirusScan. SonicWALL Network Anti-Virus  works by verifying that every PC connecting to the Internet has the most up to date signature database. New updates from McAfee are sent directly to the firewall, which then distributes it to the desktops. Even if a user uninstalls their desktop antivirus software, the SonicWALL device reinstalls it on their next Internet connect. works by verifying that every PC connecting to the Internet has the most up to date signature database. New updates from McAfee are sent directly to the firewall, which then distributes it to the desktops. Even if a user uninstalls their desktop antivirus software, the SonicWALL device reinstalls it on their next Internet connect. The most common method for software-based firewalls is for the antivirus program to reside on the same server. The customer buys the firewall from one vendor and purchases the scanning software from another. The scanning software intercepts the traffic headed through the firewall before it arrives to the network. Figure 14-3. Firewall with integrated antivirus scanning functionality  Another alternative that is becoming more popular is border devices that allow a secondary interfaced device or software to do the scanning. Internet border devices are relying on an interfacing standards like Common Content Inspection Application Programming Interface (CCIAPI) and Open Platform for Security's Content Vectoring Protocol (OPSEC's CVP). Each defines a standard way of interfacing content-scanning software to border devices, like gateways, routers, and firewalls. For example, antivirus scanning software can be added to a firewall or HTML-content scanning can be added to a proxy server. Check Point Software's CVP open standard arose out of the early work done on CCIAPI. The scanning software is considered a CVP server , while the border device is considered a CVP client (see Figure 14-4). CVP, and other border device interfaces being developed like it, are a boon for antivirus vendors and consumers. For example, Finjan's software can be plugged into Check Point's Firewall-1 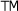 product, Microsoft's Proxy Server product, Microsoft's Proxy Server  , Axent's Raptor Firewall , Axent's Raptor Firewall  , and F-Secure's Policy Manager , and F-Secure's Policy Manager  tool. No less than 20 different security products integrate with Check Point's Firewall-1 tool. No less than 20 different security products integrate with Check Point's Firewall-1  product. Norton's Antivirus for Firewalls product. Norton's Antivirus for Firewalls  works with Network Associates' Gauntlet works with Network Associates' Gauntlet  Firewall, Check Point, and Microsoft Proxy Server, among others. When considering a new firewall, proxy server, or router, it cannot hurt to see if it supports an antivirus interface. Firewall, Check Point, and Microsoft Proxy Server, among others. When considering a new firewall, proxy server, or router, it cannot hurt to see if it supports an antivirus interface. Figure 14-4. Content Vectoring Protocol model 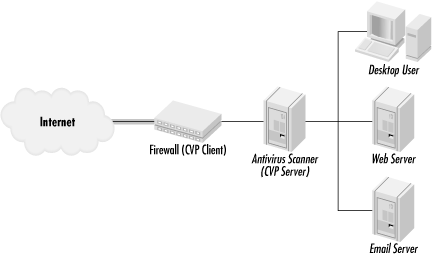 Although placing scanning software at the border does prevent the malicious content from making it inside the network perimeter, it has three problems. First, like file and email server antivirus software, it does not help when malicious code arrives via another method. Second, it is difficult to impossible for secured communication protocols (PGP, SSL, etc.) to be scanned. As encryption becomes more popular, gateway-scanning servers will either be impractical or the privates keys stored on the device. Lastly, in order for packet traffic to be scanned, all related packets that form a particular file must be assembled prior to scanning. Otherwise, the malicious code could be broken up between transmitted packets and its taletale bytes split between two packets. The scanner would scan each incoming packet, not find the malicious signature bytes, and pass it as clean. If a gateway device has to reassemble packets before they reach the intended host, then a performance penalty has to occur. Is the performance penalty worth the protection? Some administrators don't think so. 14.4.5 Where Should Antivirus Software Run? Like any question about a wide spectrum problem, there is no single answer that will satisfy everyone. It depends on the environment. If you only have the budget to buy software for one area, spend money on desktop scanners and become an expert at automating updates. There are two reasons for this advice. First, the desktop is a good location is that all malicious content must be executed on a desktop in order to spread. No matter how rogue code enters, it must eventually make its way to a PC to activate. An infected email message cannot spread on an email server without someone opening it up on a PC. An infected file lying in wait on a file server cannot harm anything until it is executed. A malicious Java applet has to be downloaded to the local PC before it can execute. Second, placing it anywhere other than on the PC will allow it slip by eventually. There are too many avenues for malicious mobile code to gain access to a PC, as previously shown in Figure 14-1. If properly configured and kept up to date, desktop placement will do a good job of preventing malicious from spreading within a networked environment. Putting antivirus software on an Internet email server is the next best option. In fact, I recommend placing scanners on desktops and on all email servers in most environments. In today's world of email worms and Trojans, placing protection there will result in a large cost/benefit. Shutting down an email worm before it gets started is paramount to keeping your environment running smoothly. Putting protection on the desktop covers most other ways malicious mobile code can enter. File server protection can be costly to provide scanning to every new server added to the network, especially when most workstations connect to multiple servers, causing a certain amount of redundancy. If you don't want to have to worry about distributing antivirus updates, then placing the protection on a file server, gateway, or router should be considered.  | Some security vendors are developing scanning products that scan any computer attempting to connect to a particular network site. For instance, Internet Security Systems (ISS) is developing a product that resides on a customer's web site and it does a local system scan on PCs trying to connect. Any rogue code is automatically removed. Connecting users must agree to the scan to be allowed access. | | 14.4.6 Other Antivirus Scanner Considerations Here are some other issues that need consideration before deploying antivirus scanning software. 14.4.6.1 When to scan If you place scanning software on a file server or desktop another decision has to be made: when to scan files? Most scanners allow you to scan files touched for any reason, including new incoming files, outgoing files, files copied , opened, or moved. Although this is the safest option, scanning all files touched for any reason can cause significant performance degradation. I've seen workstations slow down by as much as 300 percent when the virus scanner is enabled with this functionality. Scanning the same old application programming files again and again, every time a program is started gives little benefit and significantly decreases performance. Some administrators recognize that scanning all files all the time decreases performance too much, and instead schedule full file scans at preset dates, say every Monday morning. This isn't a bad idea if your end user population doesn't mind. However, many users resent having to wait 30 minutes while their PC is scanned before they can access their computers. If you are going to schedule full scans do it outside of peak hours. Other administrators go in the completely opposite direction and disable all scanning, allowing the user to determine when scans should be initiated, called on-demand scanning. Workstations with only on-demand scanning end up being run rarely, which is like having no protection at all. Relying on either scheduled scanning or on-demand scanning alone will allow new infections to take place between scans, and again isn't an optimal solution. In my experience, scanning incoming files with predefined file extensions (or all files) is the best cost/benefit trade off. If your system is clean before the antivirus scanner install, you need only scan new files anyway. Many organizations use a hybrid approach. Email servers are set to scan all emails, coming or going. File servers are set to scan all incoming files with predefined extensions, and set to run prescheduled full file scans on off peak hours. User workstations are set with real-time protection for predefined file types. This hybrid approach works well unless a new file type is introduced (e.g., .SHS files). In these instances, it is important that new file extensions be able to be added to default scans. 14.4.6.2 Internet-based scanning A few antivirus companies have products that launch themselves over the Internet to PC desktops, for example McAfee's myCIO.com (http://www.mycio.com). A client-portion of the software installs on the local machine, but updates, reports , and other capabilities are stored on the Internet. While admirable in their attempt, these products are not substitutes for normal desktop clients . They are slow to install, slow to scan, and I've seen horrible messes happen because users installed them on already infected machines. 14.4.6.3 Should you disable the antivirus scanner to install new software? Many software programs require that you disable antivirus scanning software before installing them. If the instructions or README file indicate this, follow the instructions. Of course, this gives infectious code a way into your system. Unless the instructions explicitly tell me to disable my protection software or I experience unacceptable installation times, I do not disable my antivirus software to install new software. If the new program does not work correctly after installing the first time, I uninstall it, disable the scanning software, and try again. While antivirus scanning is a must, sooner or later a rogue program is going to bypass your scanners. The following section discusses the specific actions that should be taken on every PC beforehand to minimize the impact of loose rogue code. |