Securing E-mail and the Internet
Outlook Express, Internet Explorer, and Internet Information Server have been improved as well.
Windows Mail
Windows Mail is the new name of Outlook Express. It has been re-written to include intelligent anti-spam and anti-phishing filters. Per the Microsoft development team, the filtering technologies are more sophisticated than the standard Bayesian filters used by most e-mail vendors.
One of the biggest changes from Outlook Express is that each e-mail is stored as a separate .eml file under the \mail folder. Contrast this to the single monolithic file used in the past. Having separate e-mail files means improved performance and improved integration with Windows Explorer. e-mails will be heavily indexed and available in other Explorer content views. Users can also directly access .eml files to reply to a particular e-mail or recipient. Of course, Windows Mail continues Outlook Express's blocking of Active Content in e-mail and opens all e-mail in the Internet Explorer Restricted sites zone. Chapter 10 covers e-mail security.
Internet Explorer
Microsoft has done a fairly good job regarding computer security on nearly every current product with the possible exception of Internet Explorer (IE). With IE running on 95 percent of users' desktops and functionally embedded with every current version of Windows, it gets more attacks than any other Microsoft application. Over the last three years it has announced dozens of vulnerabilities (http://www.secunia.com/product/11). Although competing products are not doing any better. Mozilla Firefox was announced as the browser product that was supposed to be better at security as IE, but in the two years since its release, it has nearly as many vulnerabilities as IE (http://www.secunia.com/product/4227), with a significantly lower market share. Unfortunately, IE is still a prime target and its success or failure is often the only impression most users have of Microsoft computer security.
Microsoft understands this and has invested years of time and dozens of team members in making IE 7.0 as strong a security product as it can. Chapter 8 covers IE 7.0 in detail. Here are some highlights.
First, by default on Windows Vista, it runs in Protected Mode (IE-PM). With IE-PM, IE runs as a low integrity process, and even if the logged on user is an administrator, IE-PM, its add-ons, toolbars, or child processes cannot access higher level integrity resources. Because most applications and resources are medium level integrity it effectively means that IE-PM doesn't have a lot of default access. Even content downloaded from the Internet or Restricted sites zones to the \Temporary Internet Files (TIF) folder is no longer a huge threat. TIF is another virtualized folder marked with low integrity (low integrity files are actually stored in a sub-folder called TIF\Low). IE's History, Cookie, and Favorites files are also marked with low integrity if they were created during a low-integrity browser session. As far as the registry is concerned, IE can access only the low integrity HKCU\Software\Low registry key.
Another huge feature of IE is its new phishing filter. IE has new intelligence to scan incoming web content looking heuristically for signs that might indicate a malicious phishing Web site. By default, IE will also check with Microsoft on every incoming Web site URL to see if it has been previously reported as a malicious Web site. Users can report any Web site to Microsoft as potentially malicious, and Microsoft will verify the site's intent before adding it to its database as malicious.
Other improved IE features are:
-
Parental controls
-
Privacy improvements
-
Pop-up blocking
-
Improved add-on controls
-
Cross domain scripting (XSS) scripting protections
-
URL handling protections
-
Improved digital certificate handling
-
Improved ActiveX control handling
-
Over a dozen new security options
-
Security status bar (easier and quick identification of Internet problems)
-
One-click Fix My Settings feature
-
Single-click Browser Content Cache Deletion
Another much need security improvement is the default prevention of ActiveX controls from being called though IE when they were never intended to be used in IE. Windows, and other installed applications, contain dozens of ActiveX controls. Prior to Windows Vista, if the installed ActiveX control was marked "safe for scripting," any IE content could launch the control and use it against the system. The new model is an opt-in policy, where all controls are disabled from being able to be launched in IE, except the ones the administrators or end users add as approved.
Windows CardSpace is Microsoft's new way for managing and providing credentials and other information (for example, credit card numbers, personal identity information) to participating Web sites and network resources. Users create individual "cards" (see Figure 1-6), which can then be securely transmitted to requesting sites. When creating and transmitting cards, CardSpace opens on the secure desktop, in order to prevent malicious interactions on the user's desktop. There is a great wiki discussion on CardSpace located at http://www.en.wikipedia.org/wiki/Windows_CardSpace.
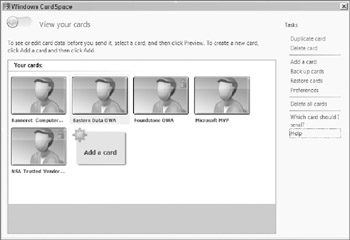
Figure 1-6: Windows CardSpace can represent credentials for many sites as "cards."
Many reviewers have called CardSpace a replacement for Microsoft Passport services. This is too simple an explanation. CardSpace is an entirely new way of delivering logon credentials and other confidential information between two hosts. Passport is being depreciated and active Passport accounts will be moved into a new Microsoft offering called Windows Live ID.
| Note | CardSpace fully supports the new OpenID open standard. |
Internet Explorer (IE) 7.0 is a huge improvement over its earlier predecessors. Whether IE can stand up to the volume of attacks that accompanies being the world's most exposed Internet application we will not know until some time passes.
IIS 7
Internet Information Services (IIS) 7 hopes to continue on the very positive security tradition of IIS 6. IIS 7 is an optional component in Windows Vista, but by default is not installed or enabled. The single biggest security change in IIS 7 is the compartmentalization of its code. In previous versions, most features were contained in large monolithic code bases. For instance, regardless of which authentication method you wanted to use for your Web site (for example, Anonymous, Basic, Windows Integrated, Digest Authentication, and so on), the code for all four methods was contained in one file and was loaded into memory together.
IIS 7 changes this by separating the code into individual modules. If you only want to load Digest Authentication, only that code will be loaded into memory. The same thing applies for dozens of other components. The less code that is loaded into memory the fewer potential exploits. This is an idea available in the open source competitor, Apache (http://www.apache.org), for years, but only now being added to IIS.
Configuration and management of IIS has been completely revamped. The dreaded metabase file has been traded in for an .XML formatted file with a simpler interface. Values can easily be directly viewed and edited, and the XML configuration files can be readily copied and replicated. IIS 7 is the focus of Chapter 9.
EAN: N/A
Pages: 163