E-Mail Threats
Most e-mail threats fall into a handful of categories: malicious file attachments, devious embedded links, cross-site scripting, spam, and phishing. Each of these threats will be discussed below after you learn why e-mail is such a popular malicious attack mechanism.
Main E-Mail Problems
Behind each of these categories are two main problems: lack of authentication and HTML-enabled e-mail. Like most security vulnerabilities, the real underlying issue is the lack of authentication — unauthenticated senders, untrustworthy content, and trojan file attachments. Malware and malicious coders know that the most frequently used application in the world is e-mail, and almost all of it is unauthenticated. Its ubiquitous use also ensures that a higher than normal percentage of users will be untrained in computer security and gullible to social engineering attacks. Unfortunately, most e-mail users almost universally open every e-mail and file attachment sent their way.
Ultimately, the safety of e-mail will only be improved by better authentication, from the first character typed in by the authenticated sender to the reception of the authenticated message by the receiver. There are a few e-mail protection standards and protocols that do this; unfortunately, none are widely used or accepted.
Most e-mail clients support HTML-enabled e-mail messages, meaning that everything that can be sent maliciously to an Internet browser can also be sent in e-mail. With many e-mail clients, including Microsoft Outlook and Outlook Express (OE), HTML e-mail content is rendered using the parsing engine and capabilities of Internet Explorer. Without HTML-enabled e-mail, it would be hard to trick many users into visiting untrusted sites. With e-mail, a massively productive worm, trojan, virus, or bot can send a link that claims to point to a legitimate resource but which really points to a site that the user would not normally trust. For instance, in Figure 11-1, the e-mail claims to be from eBay but really is from a malicious phishing site (as the underlying link reveals).
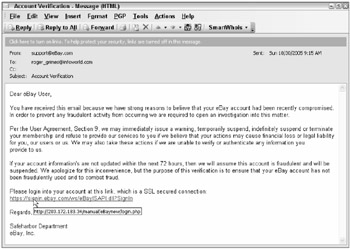
Figure 11-1
The dangerous combination of a ubiquitous application accepting unauthenticated content from around the world off the Internet is an attractive target for malware writers and hackers.
Malicious File Attachments
Malicious code runs in waves. Two decades ago, boot viruses ruled the landscape. Executable file viruses took over until 1995, when macro viruses became popular for four or five years. Although not the first e-mail worm (not even the first Internet e-mail worm), the success of the Melissa macro virus (www.cert.org/advisories/CA-1999-04.html) of March 1999 launched the next decade and a half of malicious attacks — Internet worms. Computer viruses started having less success because of Windows file protection features (Windows File Protection/System File Protection). Worms, which contain their own malicious program files and don't modify or overwrite other executables, were matched with e-mail to become a voracious combination.
The typical e-worm arrives as a malicious file attachment or embedded link along with message text engineered to fool the unsuspecting user into opening the attached file. Cybertrust's 2004 ICSA Labs Virus Prevalence Survey (www.cybertrust.com/pr_events/2005/20050405.shtml) shows that 92% of all malware infections arrive via an e-mail attachment. The accompanying message text comes in many forms:
-
It may claim to be from an acquaintance of the recipient (i.e., sender address spoofing).
-
The attached file executable name may be spoofed to appear as a non-executable (e.g., picture file, text file, etc.), as covered in previous chapters.
-
The message may claim to contain something humorous or pornographic.
-
It may pose as official communications from a trusted source (i.e., Internet service provider, bank, etc.).
-
It may purport to be an antivirus program or software patch.
-
It may be as vague as possible.
The key is enticing the unwary user (or system) into opening the attached file and running the malware. The malware can be a worm, virus, trojan, or bot. Figure 11-2 shows two bogus e-mails with malicious file attachments. The top example shows a social engineering trick whereby the e-mail claims to be from the user's e-mail administrator. It asks the user to run the attached program to check for a suspected trojan proxy server. Of course, if run, the attachment will install a new trojan proxy server. I noticed the maliciousness of this e-mail right away because in my company's domain (i.e., banneretcs.com), I'm the e-mail administrator and I didn't send myself the message. Still, it's a cause of concern that these automated e-mail attacks are smart enough to be DNS domain—specific. I can imagine that many users receiving a similar e-mail from their Internet service provider would be fooled.
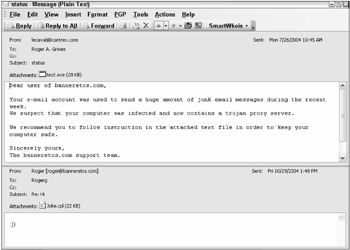
Figure 11-2
The latter example in Figure 11-2 is courtesy of the Beagle.AV worm (http://securityresponse.symantec.com/avcenter/venc/data/w32.beagle.av@mm.html). This variant of Beagle looks for and disables over 30 different antivirus programs. It contacts a remote mothership server and updates itself. It then harvests new e-mail addresses by looking in over 30 different file types on the local computer, including e-mail address books, web pages, and databases. It contains its own SMTP engine and will send itself out to every e-mail address it can find. This Beagle variant arrived with a .CPL file attachment, which is the file extension for a Microsoft Windows Control Panel applet. Since it's almost unheard of, for a legitimate reason, to send a Control Panel applet via e-mail, this file type should have been blocked at the e-mail gateway.
Even though we know that e-mail worms and trojans are the most popular method of malicious attack, and even though most organizations have implemented several layers of e-mail defense, the problem is still getting worse. MessageLabs' August 2005 report (www.messagelabs.com/publishedcontent/publish/threat_watch_dotcom_en/intelligence_reports/august_2005/DA_123226.chp.html) reveals that the number of e-mail-based trojan programs has increased dramatically throughout 2005 in comparison with 2004. The peak number of trojans stopped in any one month in 2004 was 234, while in 2005 the highest number stopped in a month was 151,559.
Devious Embedded Links
While malicious file attachments are still responsible for the largest portion of automated malware attacks, hackers are changing their methods as network administrators get better at blocking suspicious attachments. Starting in 2005, a larger and larger percentage of malicious e-mails are arriving in inboxes with rogue embedded HTML links. The links either trick the end user into visiting a malicious web site (often another innocent victim web site that has been compromised by the same hacker or worm) and downloading the malicious file or automatically execute using an HTML vulnerability.
A currently unpatched Outlook exploit (http://secunia.com/advisories/12041) allows a malicious link with the HTML OBJECT tag descriptor to exploit e-mail when Microsoft Word is used as the e-mail editor and the e-mail is forwarded to another user. Outlook prevents the attack during the user's normal downloading and reading sessions but circumvents the default security checks when the mail is forwarded to another user.
January 2006 started off with one of the most devastating Microsoft Windows attacks, known as the WMF exploit (www.microsoft.com/technet/security/advisory/912840.mspx). It was the first widespread zero-day exploit successful against all fully patched versions of Windows. Worms and hackers exploited it using a malicious URL link that arrived in e-mail or via IM. If the user clicked on the link, it automatically loaded a malformed WMF file, which then buffer-overflowed the Windows graphics rendering engine and allowed complete control of the computer. Until Microsoft provided a patch, there were no guaranteed defenses.
Nearly every popular Internet browser suffers from exploits that allow remote execution of malicious code, privilege escalation, and security bypasses. Internet Explorer, as covered in the last chapter, certainly has its share of remotely exploitable vulnerabilities each year, but so does its closest competitors. Unfortunately, Internet Explorer is the most popular browser and a huge hacker target. According to Secunia (www.secunia.com), IE suffered 12 vulnerabilities in 2005 (as of October). A full 100% of the IE vulnerabilities were remotely exploitable, and half of those remain unpatched. Nearly half allowed system access or bypassed security. Many programs, such as Outlook and OE, are susceptible to the same exploits because they rely on IE for rendering HTML content. Whether through a file attachment or a malicious embedded web link, if an end user can be tricked into executing an untrusted executable, there is no perfect defense that can prevent all malware from successfully compromising the PC.
Cross-Site Scripting
Cross-site scripting (XSS) attacks are as possible in e-mail as they are in Internet browsers. As covered in Chapter 10, XSS attacks occur when an attacker is allowed to insert actionable HTML content into a web site or e-mail (or other HTML-enabled content) in such a way that it is unknowingly executed by the recipient. For example, when an attacker replies to a victim's online auction offering via an e-mail, the attacker's e-mail can contain code that steals the recipient's auction logon name and password when the e-mail is opened. eBay was hit by a JavaScript-enabled XSS worm called Ebayla in April 1999.
Cross-site scripting attacks remain one of the most popular attacks occurring today. When an XSS attack is executed, it normally executes in the context of the logged in end user. Those privileges are usually enough to carry out all sorts of maliciousness.
Spam
The spam problem is so bad that it no longer needs defining. Even though some of the majority producers of spam are being brought to justice and being put out of business, albeit slowly, it still compromises the majority of e-mail on the Internet today. The real questions are why do spammers do what they do and how?
Why Spammers Do What They Do
Spammers are motivated by easy money. The money is made either by selling products (legitimate or bogus), scamming money, or by selling validated e-mail addresses to other spammers. Spamming started out primarily as a cheap way to advertise, with spammers sending out millions of e-mails a day. According to The Spamhaus Project, the top 200 spammers (www.spamhaus.org/rokso/index.lasso) send out 80% of the spam. Each top spammer sends out tens of millions of e-mails a day.
Although this is no official accounting, most educated guesses put the spammer's conversion rate (i.e., the number of purchases made by spam readers) at somewhere around 3.6 sales per 1 million spams sent (i.e., 0.000036). Initially, that incredibly low conversion rate might seem unprofitable, but if the spammer makes a 100% markup (as they have claimed in many interviews) on a product with a sales price averaging $80 (this is the average sales price for products advertised by spam), then their daily revenue is $1,440 per 10 million spams. If they send 50 million spams a day, that is a daily revenue value of $7,200. Conservative estimates suggest that a spammer's operating expenses cost one-fourth of their revenue, leading to a potential profit of $1.5 million a year. Much of this money is made offshore, so taxes are little to non-existent.
Lest you think I'm overstating the money to be made, two convicted spammers successfully prosecuted in 2005 had to turn their assets gained from spam over to AOL and Microsoft. The turned-over assets included gold bullion, multi-million-dollar houses, Hummers, Porsches, and rare art. As another spammer (a former long haul trucker) said to attest to his wealth, "I know what it feels like to want, and I'll never have to know that feeling again."
In "Nigerian" scams, the spammer sends an e-mail claiming to be a close relative of somebody who recently died or was murdered. They ask for assistance in converting millions of dollars, and tell the recipient that they will receive 25% of the proceeds for assisting in laundering the money. Eventually, the scammers ask the recipient for financial or banking information so they can transfer the money, but instead (of course) steal the recipient's money. Because what the recipients are doing in the first place is illegal, they are hesitant to report the loss. Conversion rates have been reported to be as high as 2–3%, with victims losing tens of thousands of dollars. At one point, Nigerian scams were the second largest industry in Nigeria, but of course many scammer countries are competing now. Closely related to the Nigerian scams are foreign lottery winning notices. They claim the recipient has won some sort of lottery worth millions and ask for financial information (or money) to verify the recipient's identity.
Another major source of revenue for the spammer is selling verified, legitimate e-mail addresses. Although anyone can buy a CD containing over 2 million supposedly verified e-mail addresses, the CDs are often full of more bad addresses than good ones. Many spammers send e-mails selling no product, only hoping to confirm that the e-mail address it was sent to is valid and active. Spammers do this by inserting an HTML link in the e-mail that "dials" home when the e-mail is opened. The e-mail link often points to a one-pixel, transparent graphic (called a web beacon) that no normal user would notice. By opening the e-mail, most e-mail clients will automatically download any graphics referenced by the embedded links. The web beacon is uniquely named for each e-mail sent. When the graphic is downloaded, the e-mail address is positively identified as valid and active. The spammer then sells the validated address to hundreds of other spammers, and the whole cycle starts again.
Spammers are also spreading malware specifically coded to assist in criminal activities: mostly identity and credit card theft. The spammers can often make faster profit by creating large bot nets that can then be rented or sold to the highest bidding criminal enterprise. Symantec's September 2005 Internet Security Threat Report (http://enterprisesecurity.symantec.com/content.cfm?articleid=1539) said that 74% of the top 50 malware programs detected in 2005 had the ability to steal confidential information.
How Spammers Do What They Do
Spammers purchase or rent a series of computers and load them with bulk e-mailing programs. Search the Internet using the terms "bulk e-mailer" and you'll be astounded by what you find. Hundreds of programs are custom built for the spammer. Although not all bulk e-mailers are specifically made to help spammers, some of the features, such as purposefully misspelling the subject many different ways in order to bypass spam detectors, can only be of benefit to the spammer, not to the legitimate bulk e-mailer. For $125, the spammer can find a program that will drive the whole operation from beginning to end. It will create the e-mails, randomizing the sender's name, subject, and text enough to circumvent many anti-spam products.
Besides the computers and software that actually send the e-mail, the spammer needs a lot of Internet bandwidth. Although you would think that all ISPs would try to stop spamming, many ISPs cater to bulk e-mailers. They promise that the bandwidth given will be high-speed with high availability. These ISPs promise to help the spammer keep sending messages, and to fight any and all attempts to block their client's attempts to send unsolicited mail. These types of ISPs call their guaranteed spam-friendly protection bullet-proofing. Spam is big business for many companies beyond the originating spammer.
Everyone involved in the spam industry skirts the illegitimacy of spamming by claiming that all their e-mail lists contain legally obtained e-mail addresses from people who want such e-mails. They all claim that they would never knowingly send spam to someone who didn't want it. But when spammers and their infrastructure partners claim to be able to send to 200 million supposedly opt-in e-mail addresses a day, or 15 million web sites a day, just waiting for unsolicited advertising, they know they are lying.
A spammer's only real hurdle, besides the law, is how to collect enough legitimate e-mail addresses to make a profit. As mentioned above, they often buy validated e-mail addresses from other spammers and bulk e-mailers, but that's expensive. Instead, most spammers harvest e-mail addresses from the Internet using automated programs. The address harvesting programs will crawl the web looking for web pages with valid e-mail addresses, or use the information already collected in the most popular search engines. Why crawl the web when Google has done it already? Google, widely abused by spammers and hackers alike, contains logic that attempts to stop harvesting abuse, but there are other ways for the spammers to collect valid e-mail addresses, including the following:
-
Mail server directory harvesting
-
Harvesting public newsgroups and mail lists
-
Address book harvesting (i.e., like most e-mail worms and bot do)
-
Searching chat channels
-
Query Ident and Finger servers (Unix services that can be used to identify individual users)
-
Querying web browsers
-
Utilize unpatched HTML exploits
-
Hacking into mail and other Internet-facing servers
-
Man-in-the-middle attacks
-
Guessing
With mail server directory harvesting, a program connects to an Internet-reachable e-mail server and queries it for valid versus invalid names. Many SMTP servers support commands that are supposed to allow a remote e-mail server to check for the existence of a valid e-mail address before sending the data. Spam bots will check as many possible combinations of e-mail addresses as they can before being disconnected. If the participating victim e-mail server allows it, a spammer can guess all the valid e-mail addresses managed by the e-mail server.
No matter what the collection method, the spammers either collect the e-mail addresses themselves or purchase them from another source. The addresses are then fed into a bulk e-mail computer and launched onto the Internet. To get past the blocking defenses accorded by real-time black lists (see below), which allow e-mail servers to block e-mail from reported unsolicited bulk e-mailers, spammers must constantly change their sending e-mail address and e-mail domain name. However, using a false e-mail address is against many anti-spam laws (including the U.S. CAN SPAM Act). Thus, the average spammer is constantly on the run from the authorities, using offshore ISPs, and trying to cover their tracks to avoid being caught. Their evading techniques are often just as illegal, so when they eventually get caught, the list of violated laws adds up. Not surprising, many spammers are convicted felons for other nefarious business violations.
Phishing
Phishing is the malicious act of sending a bogus e-mail to a user that falsely purports to be from a legitimate service. The Anti-Phishing Working Group defines phishing as "… attacks [that] use both social engineering and technical subterfuge to steal consumers' personal identity data and financial account credentials." Most phishing attacks pose as the user's bank, online auction center, or ISP.
Most of the time, the phishing attack is not successful because the receiver of the e-mail is not affiliated with the bank or service the phishing e-mail claims to be from. But more and more often, phishers are making sure their victims belong to the hijacked brand name before they send the rogue e-mail. This is known as spearfishing, because the target is so narrow. Figure 11-3 shows a common phishing e-mail.
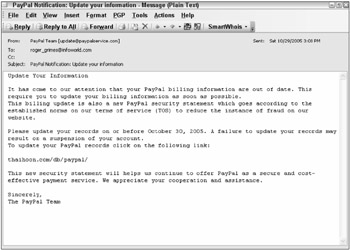
Figure 11-3
The recipient is being asked to update their PayPal account records, which most surely will include credit card information. The enclosed link, thaihoon.com/db/paypal, is not a PayPal-affiliated site. In this case, www.thaihoon.com is a Thailand-based web hosting service that allows users to put up free web sites. These types of sites are often used by the phishers, along with other exploited legitimate web servers, to avoid easy detection if the authorities get involved.
Conventional phishing attacks, where the user is sent an e-mail requesting confidential information, were on a slight decrease near the end of 2005. The newer phishing angle is to use another method to install a trojan to steal the confidential information without the user having to put the information into a bogus web site. According to both Symantec and the Anti-Phishing Working Group, the number of malware programs and phishing web sites hosting confidential information stealing trojans are both on the rise.
Related to phishing, pharming is a technique used to maliciously redirect a client's DNS request to a malicious server. Often what happens is that a vulnerable ISP DNS server is compromised, and rogue IP address data is installed. When the user or their e-mail client uses a URL, the connection request is routed to a malicious server coded to look like the real thing. For instance, a spearphishing e-mail arrives from a phisher claiming to be from the user's bank. The recipient independently verifies that the URL in the e-mail points to the bank's legitimate web site. When the receiver clicks on the e-mail's URL link, a poisoned DNS answer is sent to the client, redirecting them to a bogus site that is made to look like the user's real banking web site. The bogus web site may even redirect all requests to the legitimate web site so that the user can see their normal account information. Unbeknownst to the victim, their every keystroke, logon name, and password is being recorded.
Unauthorized Reading of E-Mail
Although not an issue largely reported at this time, most e-mail sent through the Internet is plaintext. It can be read by anyone intercepting it along the way. The average number of intermediate routers between the source and destination e-mail servers on the Internet is 12 to 22. That's a lot of places for man-in-the-middle and interception attacks to take place. People routinely send confidential and sensitive information through e-mail that they would otherwise hope that unintended parties did not read.
There have been many cases of e-mail administrators reading otherwise confidential e-mails of company employees and management, executives snooping on other executives, and entire e-mail domains hijacked by hackers. Several very large companies and ISPs have had their e-mail DNS records hijacked by unauthorized parties. The redirected e-mail is then captured on a rogue server, where it can be read at will. Panix, one of New York's largest ISPs, had their domain hijacked for several days in 2005 (www.panix.net/hijack-faq.html). When Panix called to get their domain restored to the legitimate IP addresses, their DNS domain registrar did not answer their phone for several days. It turned out the DNS registrar, which allowed the hijacking to happen because of poor security, was located in Australia and the only person on call was not answering the phone. DNS domain hijacking has happened to eBay, Google, and thousands of other businesses. Authenticated and encrypted e-mail protocols would solve the problem.
E-mail is a catch-all depository for all sorts of maliciousness — malicious file attachments, devious embedded links, cross-site scripting, spam, phishing, DNS poisoning, and unauthorized reading. Fortunately, most of these problems can be minimized by implementing the following best-practice recommendations.
EAN: 2147483647
Pages: 122
- Challenging the Unpredictable: Changeable Order Management Systems
- ERP System Acquisition: A Process Model and Results From an Austrian Survey
- Distributed Data Warehouse for Geo-spatial Services
- A Hybrid Clustering Technique to Improve Patient Data Quality
- Development of Interactive Web Sites to Enhance Police/Community Relations