Chapter 4: Buffers Subject to Overflow (Lane of Monsters)
Overview
You cannot find a single popular program that can avoid overflow errors. Such errors are frequently detected in any software product, from Microsoft's applications to open -source products. It only remains to guess how many bugs remain undetected. This is a true gold mine! Buffers vulnerable to overflow represent the key to governing the entire world. However, to exploit them, it is necessary to go a long way and learn many aspects.
The overwhelming majority of remote attacks is carried out using buffer overflow. One particular case of this is overwriting the return address (stack overflow). Those who master the techniques of buffer overflow rule the world, and those who don't are ruled by circumstances. For example, it is possible to send a TCP/IP packet to a computer, overflow the stack, and ruin the entire hard disk.
What are these buffers that are subject to overflow? First, it is necessary to forget all that garbage your teachers of computer science tried to put into your head. Forget the term "RAM," because in this case you'll deal only with the address space of a vulnerable process. In its simplified form it can be imagined as a long ruler. All required objects, such as buffers and variables , are placed in order along this ruler. Each measurement unit corresponds to one unit length, but different objects take a different number of cells . For example, one BYTE variable takes one cell , a WORD variable takes two cells, and a DWORD takes four cells.
A set of variables of the same type joined to form an array can take lots of cells. At the same time, an individual cell has no information about the type of variable that it stores or about its boundaries. Two WORD variables can be interpreted as BYTE + WORD + BYTE , and it won't matter that the head of the WORD variable belongs to one variable and its tail belongs to another one. The situation is even worse when it comes to control over boundaries of arrays. This type of variable is not supported at the hardware level, and the processor cannot distinguish between an array and a set of several unrelated variables. Therefore, it is up to the programmer and the compiler to care about array integrity. However, programmers are humans (consequently, they tend to err), and compilers are programs (consequently, they do what the humans have ordered them, not what the programmer intended but did not articulate ).
Consider a simple program that prompts the user to enter his or her name and then cheerfully displays the greeting. To store the input string, it is necessary to allocate a buffer of sufficient size. Buffer allocation must be carried out beforehand. And what size can be considered sufficient ” ten, hundred, thousand, or several thousand characters ? This is of no importance. The only issue that matters is taking care to include the controlling code in the program, which would limit the length of the input string by the size of the allocated buffer. If this precaution isn't made, and if the input string is too long, the input will go beyond the buffer limits and overwrite variables located after the end of the buffer. Variables control program execution. Thus, by overwriting them in a strictly defined order, it is possible to do whatever you like at the target computer. The most promising target for all attackers is the command interpreter , also known as the shell in the UNIX community. If the hacker succeeds in starting it, then the fate of the computer under attack is predefined. And the hacker won't be out of job in the nearest future (Fig. 4.1).
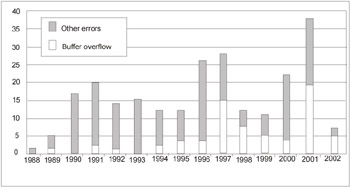
Figure 4.1: The number of security holes detected during the recent year (according to data reported by CERT)
EAN: 2147483647
Pages: 164