Password Sniffing
In most cases, authorization on the site is carried out using weak authentication mechanisms developed by the Webmaster. As a rule, these mechanisms transmit passwords as plaintext. Consequently, intruders can easily sniff such passwords by installing a sniffer on one of machines located within internal network or DMZ (Fig. 28.1). As a variant, intruders can create an exact copy of the attacked Web server for luring naive users, in which case users would themselves supply both login names and passwords.
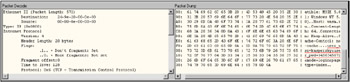
Figure 28.1: Password for accessing the database, captured by a sniffer
Lots of servers store authorization information in the form of cookies located on machines of remote users. Thus, instead of attacking a strongly protected corporate server, the hacker can attack unprotected client hosts . The main difficulty in this case is that their network coordinates are not known beforehand; therefore, the attacker must use trial-and-error method. As a rule, this problem is solved by sending massive amounts of spam with an attachment infected by a Trojan. If the attacker is lucky, at least one corporate client among the naive users will start the Trojan. After that, retrieving a cookie is a matter of technique.
Some database servers (including early versions of Microsoft SQL Server) automatically set the default password that provides full access to the database and allows you to do whatever you choose to it (for Microsoft SQL Server, this is the sa password).
EAN: 2147483647
Pages: 164