Drowned in the Honey
If the attacked host happens to be a honeypot (Fig. 26.2), then all actions of attackers either have no effect (a vulnerable server silently "eats" the shellcode and continues to operate as if nothing happened ) or display an empty resource that doesn't contain anything interesting. In this case, attackers can escape safely only if they don't panic and don't become flustered. First, it is necessary to get rid of the cellular phone, which is an important exhibit that compromises the attacker. (Getting rid of only the SIM card is not enough, because the cellular phone contains a unique identification number). After that, the intruder has to make off silently without attracting unneeded attention. If the attack was carried out from the LAN, the intruder must remove all software related to the attack and all the files, including temporary ones.
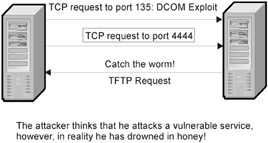
Figure 26.2: Attacked server happened to be a honeypot
EAN: 2147483647
Pages: 164