7.3 Securing Your System on a Network
Security is a very real concern for any computer connected to a network or the Internet. There are three main categories of security threats:
- A deliberate, targeted attack through your network connection
-
Ironically, this is the type of attack most people fear, but realistically, it is the least likely to occur, at least where home and small office networks are concerned. It's possible for a so-called hacker to obtain access to your computer, either through your Internet connection or from another computer on your local network; it's just not terribly likely that such a hacker will bother.
- An automated invasion by a virus, robot, or Trojan horse
-
A virus is simply a computer program that is designed to duplicate itself with the purpose of infecting as many computers as possible. If your computer is infected by a virus, it may use your network connection to infect other computers; likewise, if another computer on your network is infected, your computer is vulnerable to infection. The same goes for Internet connections, although the method of transport in this case is typically an infected email message.
There also exist so-called robots, programs that are designed to scan large groups of IP addresses, looking for vulnerabilities. The motive for such a program can be anything from exploitation of credit card numbers or other sensitive information to the hijacking of computers for the purpose of distributing spam, viruses, or extreme right-wing propoganda.
Finally, a Trojan horse is a program that works somewhat like a virus, except that its specific purpose is to create vulnerabilities in your computer that can subsequently be exploited by a hacker or robot. For example, a program might open a port on your computer (see Appendix D) and then communicate with a remote system to announce its presence.
- A deliberate attack by a person sitting at your computer
-
A person who sits down at your computer can easily gain access to sensitive information, including your documents, email, and even various passwords stored by your web browser. An intruder can be anyone, from the person who steals your computer to a co-worker casually walking by your unattended desk. Naturally, it's up to you to determine the actual likelihood of such a threat and to take the appropriate measures. Such measures are discussed in Chapter 8.
7.3.1 Closing Back Doors in Windows XP
Windows XP includes several features that will enable you to implement a reasonable level of security without purchasing additional software or hardware. Unfortunately, Windows is not configured for optimal security by default. The following steps will help you close some of these "back doors:"
-
By default, the file sharing service is enabled for Internet connections, but in most cases, there's no reason for this. Open the Network Connections window, right-click the icon corresponding to your Internet connection, and select Properties. In the General tab, clear the checkmark next to the File and Printer Sharing for Microsoft Networks entry, and then click OK. If you have more than one Internet connection icon, repeat this procedure for each of the others. Make sure to leave it enabled for the connection to your workgroup (if applicable).
-
One of the main reasons to set up a workgroup is to share files and printers with other computers. But it's wise to only share those folders that need to be shared, and disable sharing for all others.
A feature called Simple File Sharing, which could allow anyone, anywhere, to access your personal files without your knowledge, is turned on by default in Windows XP. Go to Control Panel
 Folder Options
Folder Options  View tab, and turn off the Use simple file sharing option.
View tab, and turn off the Use simple file sharing option. Details on sharing resources can be found in Chapter 8.
-
Another feature, called Universal Plug-and-Play (UPnP), can open additional vulnerabilities on your system. UPnP would more aptly be called Network Plug & Play, since it only deals with network devices. UPnP is a collection of standards that allow such devices to announce their presence to UPnP servers on your network, much in the same way as your PnP sound card announces its presence to Windows when you boot your system.
Windows XP supports UPnP out of the box, which, on the surface, sounds like a good idea. However, UPnP is a service that most users don't need, and unless you specifically need to connect to a UPnP device on your network, you should disable UPnP on your system immediately. Leaving a service like UPnP running unnecessarily exposes your system to several security threats.
To disable UPnP, open the Services window (services.msc). Find the SSDP Discovery Service in the list and double-click it. Click Stop to stop the service and change the Startup type to Disabled to prevent it from loading the next time Windows starts. Click OK and then do the same for the Universal Plug and Play Device Host. Close the Services window when you're done.
-
The Remote Desktop feature, described in Section 7.2.8, earlier in this chapter, is enabled by default in Windows XP. Unless you specifically need this feature, it should be disabled. Go to Control Panel
 System
System  Remote tab, and turn off both of the options in this window.
Remote tab, and turn off both of the options in this window. -
Make sure each and every user account on your system has a unique password. Even though you may not be concerned about security between users, unprotected accounts can be exploited by an attack over a network. See Chapter 8 for more information on user accounts.
-
Set up a firewall, as described in the next section, to further protect your computer by strictly controlling network traffic into and out of your computer.
-
Finally, look for vulnerabilities in your system by scanning for open ports, as described at the end of this chapter.
7.3.2 Using the Internet Connection Firewall
A firewall is a layer of protection that permits or denies network communication based on a predefined set of rules. These rules restrict communication so that only certain applications are permitted to use your network connection. This effectively closes backdoors to your computer that otherwise might be exploited by viruses, hackers, and other malicious applications.
7.3.2.1 Part 1: enable ICF
To enable the Internet Connection Firewall (ICF) on your computer, follow these steps:
-
Open the Network Connections window. If you haven't already done so, select Details from the View menu.
-
Right-click the connection icon corresponding to your Internet connection, and select Properties. In most cases, it will be the Ethernet adapter connected to your Internet connection device.
However, if you're using a DSL or cable connection that requires a login with a username or password, the icon to use is the Broadband connection icon corresponding to your PPPoE connection. See Section 7.2.2.2, earlier in this chapter, for further instructions.

If you're using Internet Connection Sharing, as described earlier in this chapter, you can protect your entire network by simply enabling the Internet Connection Firewall option for the single shared Internet connection on the host computer.
-
Choose the Advanced tab, and turn on the Protect my computer and network by limiting or preventing access to this computer from the Internet option, as shown in Figure 7-9 (earlier in this chapter).
If you don't have such an option in your dialog, there are two possibilities. Either the connection you're using is for your LAN (it's only avaialble for Internet connections), or your your Internet connection isn't set up properly (as described earlier in this chapter). Try running the Network Setup Wizard if neither of the above are helpful.
-
By default, Windows XP does not log communication blocked by the Internet Connection Firewall. To enable firewall logging, open the Advanced Settings window as described earlier, and turn on the Log dropped packets option. The log is simply a text file that can be opened your favorite text editor (or Notepad); by default, it's stored in \Windows\pfirewall.log.
-
Click OK when you're done. The change will take effect immediately.
-
Verify that Internet Connection Sharing is enabled; it should say "Enabled, Firewalled" or "Enabled, Shared, Firewalled" in in the Type column of the Network Connections window, as shown in the example way back in Figure 7-5.
Lastly, verify that the Internet connection still works on the host by attempting to open a web page.
7.3.2.2 Part 2: configure ICF to accomodate file sharing or other software
As you use your computer, you may find that a particular network program or task no longer works properly after enabling ICF. For example, if you access your workgroup and Internet connection through a single connection,[2] your ability to share files and folders (as described in Chapter 8) would be disabled by the firewall. Or, if you use the Internet Time feature (Control Panel ![]() Date and Time
Date and Time ![]() Internet Time tab), you'll find that it won't work from behind the firewall.
Internet Time tab), you'll find that it won't work from behind the firewall.
[2] Examples include using a router or using multiple IP addresses, as described in Section 7.2.3, earlier in this chapter.
First, verify that the firewall is actually causing the problem by temporarily disabling the Internet Connection Firewall, and then trying the task again. If indeed the firewall is the culprit, you can add a new rule to permit the program to communicate over your Internet Connection.
-
Open the Network Connections window, right-click the firewalled connection icon corresponding to your Internet connection, and select Properties.
-
Choose the Advanced tab, click Settings, and choose the Services tab.
-
Here you'll see a list of optional services, all disabled by default. This dialog can be misleading. Note that enabling an option here won't turn on the service, but rather only lift the firewall's restriction for that service. Open the Services window (services.msc) to actually enable or disable such services on your system.
For example, if you enable the FTP Server option here, it will mean that other computers will be able to access the FTP server service running on your computer, but it will have no effect on your computer's ability to connect to an FTP service on another computer.

There's a reason that only services are listed here. The Internet Connection Firewall is only able to restrict incoming network traffic; it's incapable of restricting data sent from your computer. See "Part 3: Alternatives to the Internet Connection Firewall," later, for details.
-
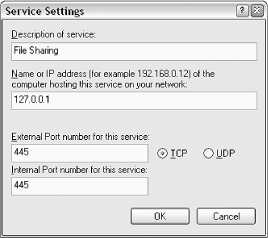
In most cases, you'll want to add a new entry to this list to accomodate the task you're trying to perform. Click Add to display the Service Settings window as shown in Figure 7-13.
Figure 7-13. Add a new rule to the Internet Connection Firewall by opening the Service Settings window.
-
The Description of service is simply a name you assign to the new service; it can be anything that doesn't already exist on the list. The description should be clear and easily recognizable, such as "File Sharing," "Peer-to-Peer Sharing," or "Whiteboard software."
-
The Name or IP address field can be somewhat confusing. In most cases, you'll be configuring a new firewall rule for a service running on your own computer. If this is the case, just specify 127.0.0.1; this is known as the "loopback address," which simply refers to your own computer. (You can also try specifying a single period here, although it's usually better to type the full loopback address.)
The only situation in which you'd specify an actual remote address here is if this computer is acting as a gateway (such as if you're using Internet Connection Sharing) and one of the other computers in your workgroup is responsible for the corresponding service.
-
Port numbers are how ICF distinguishes one service from another. Type the external and internal port numbers in the two remaining fields; in most cases, both of these values will be the same. And unless you specifically need to specify UDP ports, leave the TCP option enabled.
For example, if you're trying to get ordinary file sharing to work, as described in the beginning of this section, you'd type 445 for both the external and internal port numbers, as shown in the example in Figure 7-13. Or, to get the Internet Time feature to work, type 123 for both port numbers.
See Appendix D for a list of commonly-used port numbers, although you may still need to consult the documentation of the particular software or service to determine the appropriate port number it uses.
-
Click OK when you're done. Place a checkmark next to the newly-added service, as well as any other services you wish to permit, and click OK. Finally, click OK to close the properties window.
-
Test the newly permitted service now. You may have to experiment with different firewall rules until your software or service works properly.
7.3.2.3 Part 3: alternatives to the Internet Connection Firewall
Strictly speaking, Windows XP's Internet Connection Firewall is pretty feeble. For example, it's only capable of blocking incoming communication; it won't block any communcation originating from your computer, which means it may not protect you from viruses and Trojan horses (described in the beginning of Section 7.3, earlier in this chapter).
ICF is also incapable of allowing access to some computers while restricting access for others, which means that in order to enable a service, such a file sharing (explained in Part 2, earlier), for one computer, you'll be enabling it for any and every computer in your workgroup or on the Internet.
There are several different kinds of third-party firewall solutions available that might provide a higher level of security or more options; the one you choose, if any, depends on your needs and budget:
|
- Firewall built-into a router
-
If you use a router, as described in Section 7.2.3, earlier in this chapter, your router may have a firewall feature built-in. More often than not, this firewall will be much more capable than the one built-into Windows XP.
Furthermore, this single firewall will protect all the computers on your network from a single interface, which means that you don't have to install and configure a firewall on each computer individually.
- Third-party firewall software
-
Firewall software from other companies can also be installed and used in-place of Windows XP's ICF feature. A software solution will typically be more flexible than a hardware solution, earlier, and will certainly be better than Windows XP's built-in ICF. A few third-party firewall solutions, some of which are available for free, are listed in Table 7-3.
| Product name | Free version available | Commercial version available |
|---|---|---|
| | |
| | |
| | |
| | |
| | |
No matter which firewall solution you choose, however, you may still need to take the time to configure custom rules using a similar procedure to the one in Part 2, earlier. For example, a common problem when installing an incorrectly-configured firewall is that images will stop appearing in web pages, a situation that can be remedied by massaging the firewall's settings.
|
7.3.3 Scan Your System for Open Ports
As explained in the previous section (and in Appendix D), each open network port on your computer is a potential security vulnerability. Fortunately, there's a way to scan your computer for open ports so you know which holes to patch.
Start by opening a Command Prompt window (cmd.exe). Then, run the Active Connections utility by typing:
netstat /a /o
The /a option is included so that all open ports are shown. Without it, only ports participating in active connections would appear. The /o option instructs the Active Connections utility to show the owning process of each port (explained below).
The report will be displayed in the Command Prompt window. To send the report to a text file (say, report.txt) for easier viewing, type:
netstat /a /o > report.txt
The Active Connections utility displays its information in these five columns:
- Proto
-
This will either be TCP or UDP, representing the protocol being used. See Appendix D for details.
- Local Address
-
This column has two components, separated by a colon. The first part is the computer name, which will typically be the name of your computer. The second part will either be a port number or the name of a service.
See Appendix D for more information on decyphering the port numbers that appear here (and in the Foreign Address column).
- Foreign Address
-
For active connections, this will be the name or IP address of the remote machine, followed by a colon, and then the port number being used. For inactive connections (showing only the open ports), you'll typically see only *:*.
- State
-
This shows the state of the connection (TCP ports only). For example, for server processes, you'll usually see LISTENING here, signifying that the process has opened the port and is waiting for an incoming connection.
For connections originating from your computer, such as a web browser downloading a page or an active Telnet session, you'll see ESTABLISHED here.
- PID
-
This is the Process Identifier of the application or service that is responsible for opening the port.
To find out more, open Task Manager (launch taskmgr.exe or right-click an empty area of your taskbar and select Task Manager), and choose the Processes tab. If you don't see a column labelled PID, go to View
 Select Columns, turn on the PID (Process Identifier) option, and click OK. Finally, turn on the Show processes from all users option at the bottom of the Windows Task Manager window.
Select Columns, turn on the PID (Process Identifier) option, and click OK. Finally, turn on the Show processes from all users option at the bottom of the Windows Task Manager window. You can then sort the listing by PID by clicking the PID column header. The program filename is shown in the Image Name column.
This means that you can use the Active Connections Utility in conjunction with the Windows Task Manager, as described here, to can look up the program responsible for opening any network port on your computer.
|
You may see svchost.exe listed in the Windows Task Manager, and reported by the Active Connections utility as being responsible for one or more open ports. This program is merely used to start the services listed in the Services window (services.msc). For examples of services that are running by default, but should be disabled for security reasons, see the discussion of Universal Plug-and-Play in Section 7.3.1, earlier in this chapter.
7.3.3.1 External port scanners
If you're using a firewall, such as the Internet Connection Firewall feature built-into Windows XP (discussed in the previous section), it should block communication to most of the currently-open ports, even though they're listed by the Active Connections utility.
For this reason, you may prefer to use an external port scanner, a program that can connect to your computer through an Internet connection to check for all open ports, and do it more aggressively than the Active Connections utility. Here are some example utilities can can run from your own computer:
-
Nmap (Network Mapper) available at http://www.insecure.org
-
AATools Port Scanner available at http://www.glocksoft.com
Furthermore, these web sites will allow you to perform port scans right from your web browser:
-
http://scan.sygatetech.com
-
http://www.pcflank.com
Among other things, you can use these services to test the effectiveness of your firewall. If a port scanner cannot detect any open ports, cannot determine your computer name, and cannot detect any running services, then you're in pretty good shape!
EAN: 2147483647
Pages: 78