Section 7.6. Securing Your System on a Network
|
7.6. Securing Your System on a NetworkSecurity is a very real concern for any computer connected to a network or the Internet. There are three main categories of security threats:
Defending your computer (and your network) against these attacks essentially involves fixing the vulnerabilities they exploit, as described in the next section.
7.6.1. Closing Back Doors in Windows XPWindows XP includes several features that will enable you to implement a reasonable level of security without purchasing additional software or hardware. Unfortunately, none of these features are properly configured by default. The following steps will help you close some of these "back doors:"
7.6.2. Using the Windows Security CenterNext to the new wireless support highlighted in Section 7.5.2 earlier in this chapter, one of the biggest changes in Windows XP Service Pack 2 is the addition of the Windows Security Center, shown in Figure 7-25. You can get to the Security Center from the Windows Control Panel. Figure 7-25. The new Security Center that comes with Service Pack 2 goes a long way to make Windows appear safer (not that it does anything to actually improve security . . . )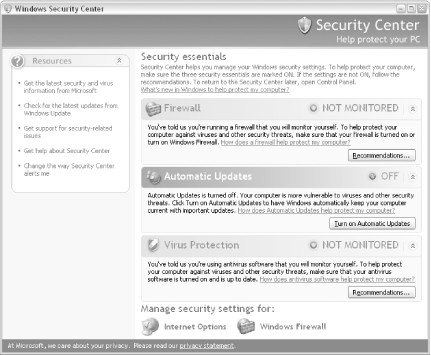 The Windows Security Center, unfortunately, is big on appearances and short on functionality. In fact, it's dangerous in that it may lull users into a false sense of security (it's effectively a placebo). The Security Center does nothing more than report the status of these three so-called "security essentials":
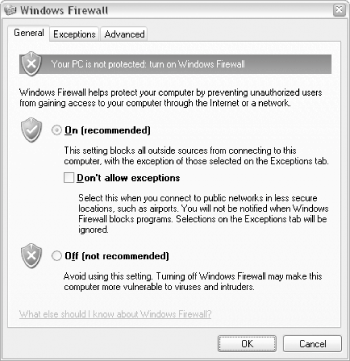
So, if you really want to protect your system, you'll basically ignore the Security Center and scrutinize each of these "essentials" individually. See the next section, for instance, for help setting up the Windows Firewall. 7.6.2.1 Setting up the Windows FirewallA firewall is a layer of protection that permits or denies network communication based on a predefined set of rules. These rules restrict communication so that only certain applications are permitted to use your network connection. This effectively closes backdoors to your computer that otherwise might be exploited by viruses, hackers, and other malicious applications. The Windows Firewall is the firewall software built into Windows XP Service Pack 2. It replaces the nearly worthless Internet Connection Firewall (ICF) found in earlier versions of Windows XP; while it's better than its predecessor, it's not nearly as effective as a router. See Section 7.1.2 and Section 7.5.1, both earlier in this chapter, for more information on routers.
To illustrate the difference between the security offered by the Windows Firewall and that afforded by a router, consider Figure 7-26. Figure 7-26. The larger dotted box shows the scope of protection offered by a router; the smaller box shows the scope of the Windows Firewall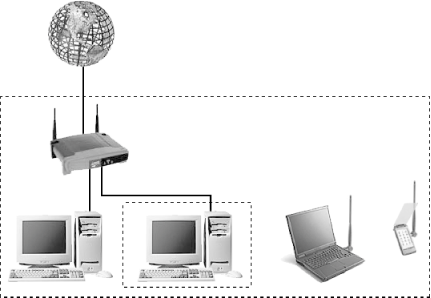 The larger dotted rectangle shows what's protected by your router's firewall, and the smaller rectangle shows what's protected by Windows. In addition to the larger scope of the router's protection, it's also much less likely to be compromised than a software-based solution like the Windows Firewall. Now, assuming you've bought the previous argument, you might think that more firewall is better, that using Windows Firewall along with a router will protect your system better than a router alone. The problem with this approach is that, again referring to Figure 7-26, the Windows Firewall isolates your PC somewhat from the other computers in your workgroup. This causes real problems when you try to share files across your workgroup, among other things. Now, there is the chance that another computer in your workgroup can become infected with a virus (presumably through someone else's carelessness) and then infect yours if you're not using the Windows Firewall. Naturally, you'll need to assess the risk of such an attack and decide for yourself if enabling the Windows Firewall is worth the hassle.
Should you decide to use the Windows Firewall, here's how to enable it:
Verify that Internet Connection Sharing is enabled; it should say "Enabled, Firewalled" or "Enabled, Shared, Firewalled" in the Type column of the Network Connections window. The real test, however, is to see if the Windows Firewall has broken anything. Verify that your Internet connection still works by attempting to open a web page. 7.6.2.2 Poking holes in the firewallAs you use your computer, you may find that a particular network program or task no longer works properly after enabling the Windows Firewall (or after installing SP2). For example, you may lose your ability to access shared files and folders (as described in Chapter 8) when the firewall is activated. Or, if you use the Internet Time feature (Control Panel When Service Pack 2 was initially released, it got a bad rap for breaking many different kinds of network-sensitive applications. In reality, this was simply due to the firewall doing what it was designed to do, combined with the fact that it has different exceptions than its predecessor, the Internet Connection Firewall. |
If you suspect that the Windows Firewall is preventing an application from working, verify that the firewall is actually causing the problem by temporarily disabling it (as described in the previous section) and then trying the task again.
Assuming the firewall is indeed the culprit, you can add a new rule to permit the program to communicate over your Internet connection.
Open the Network Connections window.
Right-click the connection icon corresponding to your Internet connection, select Properties, and choose the Exceptions tab.
There will likely be a few entries already present in your Programs and Services list, shown in Figure 7-28.
Figure 7-28. The Exceptions tab lists the programs and services permitted to receive data through all your network connections
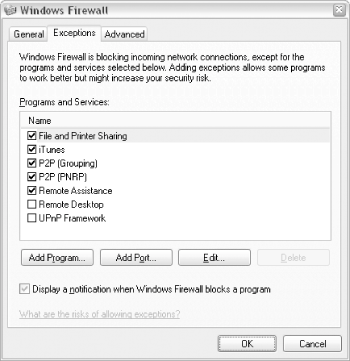

This dialog can be a little misleading. Placing a checkmark next to an entry here won't turn on the service, but rather only lift the firewall's restriction for that service. Open the Services window (services.msc) to actually enable or disable services like the FTP server or Telnet server on your system.
At this point, you can modify an existing exception by highlighting it and clicking Edit, but you're here to add a new exception, so click one of the Add buttons:
- Add Program
-
Use this to give a specific application free rein over your Internet connection. This is the easiest way to fix an application that has been broken by the Windows Firewall's restrictions. Just select an application from the list, or click Browse to choose one anywhere on your hard disk.
- Add Port
-
Click Add Port to create a new rule based on a TCP/IP port. Use this to permit incoming data based on the type of data, as opposed to the application that uses the data. Type a Name for the new exception (it can be anything you want) and then specify a Port number, as illustrated in Figure 7-29. For instance, type 123 here to get the Internet Time feature to work. See Appendix C for more information on TCP/IP port numbers.
Figure 7-29. Add a new rule to the Windows Firewall to permit certain types of incoming data
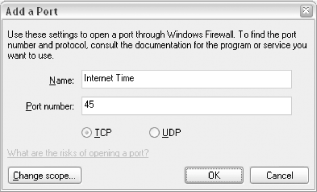
Click OK when you're done. Place a checkmark next to the new exception to activate it, or clear the checkmark at any time to ignore it.
Click OK to close the Windows Firewall window, and then click OK to close the properties window.
The new exception will take effect as soon as all the windows are closed, at which point you can test the new exception. You may have to experiment with different firewall rules until your software or service works properly.
|
7.6.2.3 Alternatives to the Windows Firewall
Strictly speaking, the Windows Firewall is pretty feeble. For example, it's only capable of blocking incoming communication; it won't block any communication originating from your computer, which means it may not protect you (or the other computers on your network) from viruses and Trojan horses (described in Chapter 6). It's also incapable of allowing incoming data from some remote computers while restricting data from others, which means that in order to enable a service, such as file sharing (explained in Section 7.6.2.2, earlier), for one computer, you'll have to enable it for any and every computer that has access to your PC.
Probably the best firewall available, at least one that's reasonably affordable, is that built into an ordinary router, described in Section 7.1.2 and Section 7.5.1, earlier in this chapter. In addition to protecting your Windows XP machine, however, a router will also protect all the computers on your network from a single interface, which means that you don't have to install and configure a firewall on each computer individually.
There are also third-party firewall software products available for Windows XP, all of which promise to do a better job protecting your PC than the Windows Firewall.
|
Here are a few third-party firewall solutions, most of which have free versions available:
Agnitum Outpost. http://www.agnitum.com
Kerio Personal Firewall. http://www.kerio.com
Norton Personal Firewall. http://www.symantec.com
Sygate Personal Firewall. http://soho.sygate.com
Tiny Firewall. http://www.tinysoftware.com
No matter which firewall solution you choose, however, you'll most likely still need to take the time to configure custom rules using a similar procedure to the one described earlier in this section. For example, a common problem when installing an incorrectly configured firewall is that images will stop appearing in web pages, a situation that can be remedied by massaging the firewall's settings.
|
7.6.3. Scan Your System for Open Ports
Each open network port on your computer is a potential security vulnerability, and Windows XP's tendency to leave more ports open than it needs is a common cause for concern (even with XP Service Pack 2). Fortunately, there's a way to scan your computer for open ports so you know which holes to patch.
Start by opening a Command Prompt window (cmd.exe). Then, run the Active Connections utility by typing:
netstat /a /o
The /a option is included so that all open ports are shown. Without it, only ports participating in active connections would appear. The /o option instructs the Active Connections utility to show the owning process of each port (explained below). The report will be displayed in the Command Prompt window, and will look something like this:
Active Connections Proto Local Address Foreign Address State PID TCP annoy:pop3 localhost:4219 TIME_WAIT 0 TCP annoy:3613 javascript-of-unknown:0 LISTENING 1100 TCP annoy:3613 localhost:3614 ESTABLISHED 1100 TCP annoy:3614 localhost:3613 ESTABLISHED 1100 UDP annoy:1035 *:* 1588 UDP annoy:1036 *:* 1588 UDP annoy:1037 *:* 1588 UDP annoy:1038 *:* 1588 UDP annoy:1039 *:* 1588
|
The Active Connections utility displays information in these five columns:
- Proto
-
This will either be TCP or UDP, representing the protocol being used, as explained in Appendix C.
- Local Address
-
This column has two components, separated by a colon. The first part is the computer name, which will typically be the name of your computer. The second part will be either a port number or the name of a service. See Appendix C for help deciphering the port numbers that appear here (and in the Foreign Address column).
- Foreign Address
-
For active connections, this will be the name or IP address of the remote machine, followed by a colon, and then the port number being used. For inactive connections (showing only the open ports), you'll typically see only *:*.
- State
-
This shows the state of the connection (TCP ports only). For example, for server processes, you'll usually see LISTENING here, signifying that the process has opened the port and is waiting for an incoming connection.
For connections originating from your computer, such as a web browser downloading a page or an active Telnet session, you'll see ESTABLISHED here.
- PID
-
This is the Process Identifier of the application or service that is responsible for opening the port.
To find out more, open Task Manager (launch taskmgr.exe or right-click an empty area of your taskbar and select Task Manager), and choose the Processes tab. If you don't see a column labelled PID, go to View
 PID (Process Identifier) option, and click OK. Finally, turn on the Show processes from all users option at the bottom of the Windows Task Manager window.
PID (Process Identifier) option, and click OK. Finally, turn on the Show processes from all users option at the bottom of the Windows Task Manager window.You can then sort the listing by PID by clicking the PID column header. The program filename is shown in the Image Name column.
This means that you can use the Active Connections utility in conjunction with the Windows Task Manager, as described here, to look up the program responsible for opening any network port on your computer.
|
You may see svchost.exe listed in the Windows Task Manager, and reported by the Active Connections utility as being responsible for one or more open ports. This program is merely used to start the services listed in the Services window (services.msc). For an example of a service that is running by default, but should be disabled for security reasons, see the discussion of Universal Plug and Play in Section 7.6.1, earlier in this chapter.
7.6.3.1 Using an external port scanner
If you're using a firewall, such as the Windows Firewall feature built into Windows XP SP2 (discussed in the previous section), it should block communication to most of the currently open ports, even though they're listed by the Active Connections utility.
For this reason, you may prefer to use an external port scanner, a program that can connect to your computer through its Internet connection to check for all open ports, and do it more aggressively than the Active Connections utility. Here are some utilities that you can run from your own computer:
Nmap Security Scanner. http://www.insecure.org
AATools Port Scanner. http://www.glocksoft.com/port_scanner.htm
Furthermore, these web sites will allow you to perform port scans right from your web browser:
Sygate Security Scan. http://scan.sygatetech.com
PCFlank http://www.pcflank.com
Among other things, you can use these services to test the effectiveness of your firewall. If a port scanner cannot detect any open ports, cannot determine your computer name, and cannot detect any running services, then you're in pretty good shape!
|
EAN: 2147483647
Pages: 97