Using Typical Extended Services
Several basic services are controlled by xinted . These services include RSH, Telnet, POP3, and FTP, among others. For a list of currently installed xinetd services, review your /etc/xinetd.d directory.
The xinetd daemon includes two levels of configuration files. The first is /etc/xinetd.conf , which sets basic parameters. By default, it refers to configuration files in /etc/xinetd.d for service-specific parameters.
Many of the xinetd services are not encrypted. However, they do have their own levels of security. If you use the security measures associated with each service to limit their use to trusted users and computers, you limit the risks. As a Linux administrator, you need to make a judgment whether this is good enough for you and your organization.
The xinetd Configuration File
The first Extended Internet Services Daemon configuration file is /etc/xinetd.conf . The settings in this file set basic parameters for all services managed by xinetd . The default Red Hat Linux configuration file is fairly straightforward, as shown in Figure 23.1.
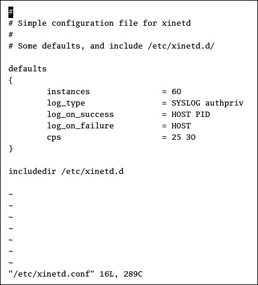
Figure 23.1: /etc/xinetd.conf
Table 23.1 explains the parameters shown in this file. As you can see, this file uses instances to regulate the load on xinetd , specifies logging parameters, stops excessive connections, and includes the files in /etc/xinetd.d .
| Command | Description |
|---|---|
| instances | Maximum number of active xinetd servers. |
| log_type | Specifies logging; SYSLOG authpriv specifies logging per /etc/syslog.conf , per Chapter 13 . |
| log_on_success | Specifies logging information when a service starts and stops; useful parameters include PID , HOST , and USERID . |
| log_on_failure | Specifies logging information when a user requests a service that can t start; useful parameters include HOST and USERID . |
| cps | Regulates the rate of incoming connections; if connections exceed 25/sec, xinetd is disabled for 30 seconds, which can slow attempts to crack an xinetd service. |
| includedir | Every file in the specified directory is read as an xinetd configuration file. |
| only_from | Notes the IP addresses allowed to access the service. |
| no_access | Service is not allowed to computers with these IP addresses. |
| access_times | Specifies the times that access to the service is allowed; e.g., access_times = 08:00-23:00 means service is allowed between 8:00 a.m. and 11:00 p.m. |
You can configure any of these parameters in other configuration files in the /etc/xinetd.d directory. When IP addresses are required, use regular or CIDR notation.
Activating xinetd Services
You activate an xinetd service in one of two ways: Either you directly edit the appropriate configuration file, or you activate it with the appropriate chkconfig command. For example, if you ve installed the telnet-server-* RPM package, open the telnet configuration file from the /etc/xinetd.d directory in a text editor. This and other xinetd configuration files contain a key parameter:
disable = yes
In other words, the service is disabled by default. You can enable it by changing this to
disable = no
You can make this change by editing this file directly in a text editor, or by using the following command, where service_name is the name of the service (such as Telnet) that you want to activate:
# chkconfig service_name on
Of course, you can reverse the process with the following command:
# chkconfig service_name off
After making a change, you need to make xinetd reread the appropriate configuration file with the following command:
# service xinetd reload
Alternatively, you could reboot Linux, which would restart xinetd and make it reread the /etc/xinetd.d configuration files. But as you ve probably noticed, rebooting Linux is rarely required.
| Tip | The service command runs any of the scripts in the /etc/rc.d/init.d directory. For example, the service xinetd reload command is functionally equivalent to /etc/rc.d/init.d/xinetd reload . |
The Remote Shell
If you have the same account on multiple computers, the Remote Shell (RSH) is an easy way to connect to different accounts on the computer of your choice. For example, once you ve enabled and properly configured RSH, you can access different accounts on different Linux computers. RSH requires the rsh-* RPM package on clients and the rsh-server-* RPM package on a server.
There are four RSH commands, also known as the r commands: rsh , rlogin , rexec , and rcp . Once the RSH server is installed, the first three of these commands have their own configuration files in /etc/xinetd.d . Activate the "r" commands that you want by using the techniques we described earlier. Don t forget to reload the xinetd service. The following command allows user mj to open his account on the computer named RHL9:
[mj] $ rlogin RHL9 Password: Last login: Tue Mar 17 10:27:43 from tty2
In this case, user mj needs to enter his password. But that isn t even necessary; he can create a .rhosts file on his home directory on each computer. As long as it includes the names of both the client and server computers, a password isn t even required. Alternatively, a Linux administrator can include the same information in /etc/ hosts .equiv , and every user with an account on both computers wouldn t need a password to check files on the other computer.
It s almost as easy to access a different account on a remote computer; the following sequence accesses the account of user lula on RHL9:
[mj] $ rlogin -l lula RHL9 Password: Last login: Tue Mar 17 10:29:26 from tty2
In other words, if a cracker knows the accounts on your Linux server, and can overwrite the .rhosts or /etc/hosts.equiv file on that computer, she can access the files of her choice.
If you need to create .rhosts or /etc/hosts.equiv files, set their immutable flags. Once you do, these files can t be deleted. You can do this with the chattr +i filename command, as follows :
# chattr +i .rhosts # chattr +i /etc/hosts.equiv
Unfortunately, a cracker who gains root user access can unset the immutable flag with the chattr -i /etc/hosts.equiv command.
Telnet
The Telnet service is a simple way to connect to a remote computer. Many users are familiar with this service, and it is fairly easy to use. Telnet lets you quickly configure a number of different Linux terminals. In addition, you can practice configuring other xinetd services by using Telnet. Unfortunately, it also sends messages, including passwords, in clear text. Therefore, your use of Telnet should be limited to networks that are already secure.
In Red Hat Linux, there are separate Telnet client and server RPM packages: telnet-* and telnet-server-* .
Once the network connection is made, Telnet is just like any other Linux command-line interface. One advantage is that Telnet is available on a variety of operating systems; Figure 23.2 shows an example of a Telnet connection to a Linux computer from a Windows XP operating system.
Figure 23.2: Telnet connection from a Microsoft computer
If you re having trouble with a Telnet connection or terminal, your Telnet client may be having a problem with the terminal messages sent from the Linux server that you re administering. One command that sets the environment variable to an older but standard terminal program is
TERM=vt100
As with other xinetd services, you need to activate it through the /etc/xinetd.d/telnet configuration file and reload xinetd before the Telnet server is active. Then you can access it from other computers with the telnet hostname command.
FTP Servers
The File Transfer Protocol, FTP, is one of the oldest protocols in the TCP/IP protocol suite. Because it is built for transferring files, it is still more efficient than newer protocols such as HTTP that can also transfer files. When I download the files to create Red Hat Linux CDs, I use an FTP server.
We cover FTP servers in detail in Chapter 27 , so we ll look at only the activation requirements here. One of the most common FTP servers is WU-FTP, maintained by Washington University in St. Louis. It s no longer included with Red Hat Linux; but you can download it from the FTP site at ftp.wu- ftpd .org or the SpeakEasy RPM library at www. rpmfind .net . As you d expect, when you install the wu-ftpd-* RPM, it installs a wu-ftpd configuration file in the /etc/xinetd.d directory.
As with other xinetd services, you need to activate it by setting disable = yes in the wu-ftpd configuration file.
Other Super Server Services
A number of other xinetd servers are available. They range from finger , which can give you more information about a specific user, to pop3s and imaps , which allow remote users to access their e-mail securely through your server. Some basic xinetd services are listed in Table 23.2. The list is not comprehensive.
| Service | Function |
|---|---|
| amanda | Configures the advanced Maryland automatic network disk archiver for backups |
| finger | More information for a user, specified via chfn , stored in /etc/passwd |
| imap | Supports remote access to an IMAP4 mail server |
| ipop3 | Supports remote access to a POP3 mail server |
| rlogin | Allows use of the rlogin command |
| rsh | Configures the RSH server |
| swat | Supports the Samba Web Administration Tool; see Chapter 29 |
| telnet | Sets up the Telnet server |
| wu-ftpd | Configures the WU-FTP server; see Chapter 27 |
EAN: 2147483647
Pages: 220
- Chapter II Information Search on the Internet: A Causal Model
- Chapter III Two Models of Online Patronage: Why Do Consumers Shop on the Internet?
- Chapter VI Web Site Quality and Usability in E-Commerce
- Chapter XIII Shopping Agent Web Sites: A Comparative Shopping Environment
- Chapter XIV Product Catalog and Shopping Cart Effective Design