Architecture and Design Issues for Web Applications
Web applications present designers and developers with many challenges. The stateless nature of HTTP means that tracking per- user session state becomes the responsibility of the application. As a precursor to this, the application must be able to identify the user by using some form of authentication. Given that all subsequent authorization decisions are based on the user's identity, it is essential that the authentication process is secure and that the session handling mechanism used to track authenticated users is equally well protected. Designing secure authentication and session management mechanisms are just a couple of the issues facing Web application designers and developers. Other challenges occur because input and output data passes over public networks. Preventing parameter manipulation and the disclosure of sensitive data are other top issues.
Some of the top issues that must be addressed with secure design practices are shown in Figure 4.1.
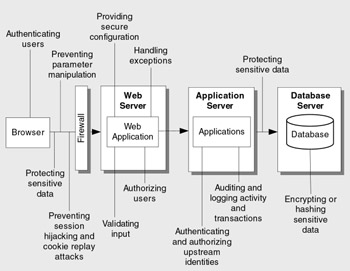
Figure 4.1: Web application design issues
The design guidelines in this chapter are organized by application vulnerability category. Experience shows that poor design in these areas, in particular, leads to security vulnerabilities. Table 4.1 lists the vulnerability categories, and for each one highlights the potential problems that can occur due to bad design.
| Vulnerability Category | Potential Problem Due to Bad Design |
|---|---|
| Input Validation | Attacks performed by embedding malicious strings in query strings, form fields, cookies, and HTTP headers. These include command execution, cross-site scripting (XSS), SQL injection, and buffer overflow attacks. |
| Authentication | Identity spoofing, password cracking, elevation of privileges, and unauthorized access. |
| Authorization | Access to confidential or restricted data, tampering, and execution of unauthorized operations. |
| Configuration Management | Unauthorized access to administration interfaces, ability to update configuration data, and unauthorized access to user accounts and account profiles. |
| Sensitive Data | Confidential information disclosure and data tampering. |
| Session Management | Capture of session identifiers resulting in session hijacking and identity spoofing. |
| Cryptography | Access to confidential data or account credentials, or both. |
| Parameter Manipulation | Path traversal attacks, command execution, and bypass of access control mechanisms among others, leading to information disclosure, elevation of privileges, and denial of service. |
| Exception Management | Denial of service and disclosure of sensitive system level details. |
| Auditing and Logging | Failure to spot the signs of intrusion, inability to prove a user's actions, and difficulties in problem diagnosis. |
EAN: 2147483647
Pages: 613
- ERP System Acquisition: A Process Model and Results From an Austrian Survey
- Context Management of ERP Processes in Virtual Communities
- Distributed Data Warehouse for Geo-spatial Services
- Healthcare Information: From Administrative to Practice Databases
- Relevance and Micro-Relevance for the Professional as Determinants of IT-Diffusion and IT-Use in Healthcare