Step 4. Identify the Threats
In this step, you identify threats that might affect your system and compromise your assets. To conduct this identification process, bring members of the development and test teams together to conduct an informed brainstorming session in front of a whiteboard. This is a simple yet effective way to identify potential threats. Ideally , the team consists of application architects , security professionals, developers, testers, and system administrators.
You can use two basic approaches:
-
Use STRIDE to identify threats . Consider the broad categories of threats, such as spoofing, tampering, and denial of service, and use the STRIDE model from Chapter 2, "Threats and Countermeasures" to ask questions in relation to each aspect of the architecture and design of your application. This is a goal-based approach where you consider the goals of an attacker. For example, could an attacker spoof an identity to access your server or Web application? Could someone tamper with data over the network or in a store? Could someone deny service?
-
Use categorized threat lists . With this approach, you start with a laundry list of common threats grouped by network, host, and application categories. Next, apply the threat list to your own application architecture and any vulnerabilities you have identified earlier in the process. You will be able to rule some threats out immediately because they do not apply to your scenario.
Use the following resources to help you with the threat identification process:
-
For a list of threats organized by network, host, and application layers , as well as explanations of the threats and associated countermeasures, see Chapter 2, "Threats and Countermeasures."
-
For a list of threats by technology, see "Threats and Countermeasures" at the beginning of each of the "Building" chapters in Part III of this guide.
During this step, you perform the following tasks :
-
Identify network threats .
-
Identity host threats .
-
Identify application threats .
Identify Network Threats
This is a task for network designers and administrators. Analyze the network topology and the flow of data packets, together with router, firewall, and switch configurations, and look for potential vulnerabilities. Also pay attention to virtual private network (VPN) endpoints. Review the network defenses against the most common network layer threats identified in Chapter 2, "Threats and Countermeasures."
Top network threats to consider during the design phase include:
-
Using security mechanisms that rely on the IP address of the sender. It is relatively easy to send IP packets with false source IP addresses (IP spoofing).
-
Passing session identifiers or cookies over unencrypted network channels. This can lead to IP session hijacking.
-
Passing clear text authentication credentials or other sensitive data over unencrypted communication channels. This could allow an attacker to monitor the network, obtain logon credentials, or obtain and possibly tamper with other sensitive data items.
You must also ensure that your network is not vulnerable to threats arising from insecure device and server configuration. For example, are unnecessary ports and protocols closed and disabled? Are routing tables and DNS server secured? Are the TCP network stacks hardened on your servers? For more information about preventing this type of vulnerability, see Chapter 15, "Securing Your Network."
Identify Host Threats
The approach used throughout this guide when configuring host security (that is, Microsoft Windows 2000 and .NET Framework configuration) is to divide the configuration into separate categories to allow you to apply security settings in a structured and logical manner. This approach is also ideally suited for reviewing security, spotting vulnerabilities, and identifying threats. Common configuration categories applicable to all server roles include patches and updates, services, protocols, accounts, files and directories, shares, ports, and auditing and logging. For each category, identify potentially vulnerable configuration settings. From these, identify threats.
Top vulnerabilities to consider include:
-
Maintaining unpatched servers, which can be exploited by viruses, Trojan horses, worms, and well-known IIS attacks.
-
Using nonessential ports, protocols, and services, which increase the attack profile and enable attackers to gather information about and exploit your environment.
-
Allowing unauthenticated anonymous access.
-
Using weak passwords and account policies that lead to password cracking, identity spoofing, and denial of service attacks if accounts can be locked out deliberately.
Identify Application Threats
In the previous steps, you defined the architecture, data flow, and trust boundaries of your application. You also created a security profile that describes how the application handles core areas, such as authentication, authorization, configuration management, and other areas.
Now use the broad STRIDE threat categories and predefined threat lists to scrutinize each aspect of the security profile of your application. Focus on application threats, technology-specific threats, and code threats. Key vulnerabilities to consider include:
-
Using poor input validation that leads to cross-site scripting (XSS), SQL injection, and buffer overflow attacks.
-
Passing authentication credentials or authentication cookies over unencrypted network links, which can lead to credential capture or session hijacking.
-
Using weak password and account policies, which can lead to unauthorized access.
-
Failing to secure the configuration management aspects of your application, including administration interfaces.
-
Storing configuration secrets, such as connection strings and service account credentials, in clear text.
-
Using over-privileged process and service accounts.
-
Using insecure data access coding techniques, which can increase the threat posed by SQL injection.
-
Using weak or custom encryption and failing to adequately secure encryption keys.
-
Relying on the integrity of parameters that are passed from the Web browser, for example, form fields, query strings, cookie data, and HTTP headers.
-
Using insecure exception handling, which can lead to denial of service attacks and the disclosure of system-level details that are useful to an attacker.
-
Doing inadequate auditing and logging, which can lead to repudiation threats.
Using Attack Trees and Attack Patterns
Attack trees and attack patterns are the primary tools that security professionals use. These are not essential components of the threat identification phase but you may find them useful. They allow you to analyze threats in greater depth, going beyond what you already know to identify other possibilities.
| Important | When you use previously prepared categorized lists of known threats, it only reveals the common, known threats. Additional approaches, such as the use of attack trees and attack patterns, can help you identify other potential threats. |
An attack tree is a way of collecting and documenting the potential attacks on your system in a structured and hierarchical manner. The tree structure gives you a descriptive breakdown of various attacks that the attacker uses to compromise the system. By creating attack trees, you create a reusable representation of security issues that helps focus efforts. Your test team can create test plans to validate security design. Developers can make tradeoffs during implementation and architects or developer leads can evaluate the security cost of alternative approaches.
Attack patterns are a formalized approach to capturing attack information in your enterprise. These patterns can help you identify common attack techniques.
Creating Attack Trees
While several approaches can be used in practice, the accepted method is to identify goals and sub-goals of an attack, as well as what must be done so that the attack succeeds. You can use a hierarchical diagram to represent your attack tree, or use a simple outline. What is important in the end is that you have something that portrays the attack profile of your application. You can then evaluate likely security risks, which you can mitigate with the appropriate countermeasures, such as correcting a design approach, hardening a configuration setting, and other solutions.
Start building an attack tree by creating root nodes that represent the goals of the attacker. Then add the leaf nodes, which are the attack methodologies that represent unique attacks. Figure 3.5 shows a simple example.
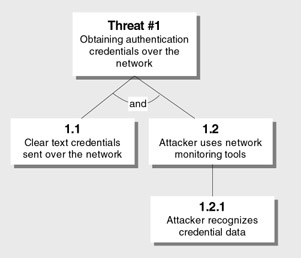
Figure 3.5: Representation of an attack tree
You can label leaf nodes with AND and OR labels. For example, in Figure 3.5, both 1.1 and 1.2 must occur for the threat to result in an attack.
Attack trees like the one shown above have a tendency to become complex quickly. They are also time-consuming to create. An alternative approach favored by some teams is to structure your attack tree using an outline such as the one shown below.
1. Goal One 1.1 Sub-goal one 1.2 Sub-goal two 2. Goal Two 2.1 Sub-goal one 2.2 Sub-goal two
| Note | In addition to goals and sub-goals, attack trees include methodologies and required conditions. |
Here is an example of the outline approach in action:
Threat #1 Attacker obtains authentication credentials by monitoring the network 1.1 Clear text credentials sent over the network AND 1.2 Attacker uses network-monitoring tools 1.2.1 Attacker recognizes credential data
For a complete example, see "Sample Attack Trees" in the "Cheat Sheets" section of this guide.
Attack Patterns
Attack patterns are generic representations of commonly occurring attacks that can occur in a variety of different contexts. The pattern defines the goal of the attack as well as the conditions that must exist for the attack to occur, the steps that are required to perform the attack, and the results of the attack. Attack patterns focus on attack techniques, whereas STRIDE-based approaches focus on the goals of the attacker.
An example of an attack pattern is the code-injection attack pattern that is used to describe code injection attacks in a generic way. Table 3.3 describes the code-injection attack pattern.
| Pattern | Code injection attacks |
|---|---|
| Attack goals | Command or code execution |
| Required conditions | Weak input validation Code from the attacker has sufficient privileges on the server. |
| Attack technique |
|
| Attack results | Code from the attacker runs and performs malicious action. |
For more information about attack patterns, see the "Additional References" section at the end of this chapter.
EAN: 2147483647
Pages: 613