Threats and Countermeasures
Many threats to an application server come from within an organization because application servers should be isolated from Internet access. The main threats to an application server are:
-
Network eavesdropping
-
Unauthorized access
-
Viruses, Trojan horses, and worms
Figure 17.2 shows the main threats to an application server.
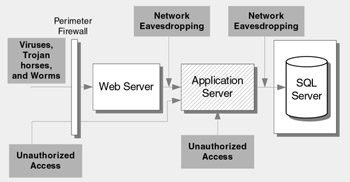
Figure 17.2: Top application server related threats and vulnerabilities
Network Eavesdropping
Attackers with network monitoring software can intercept data flowing from the Web server to the application server and from the application server to downstream systems and database servers. The attacker can view and potentially modify this data.
Vulnerabilities
Vulnerabilities that can make your application server vulnerable to network eavesdropping include:
-
Sensitive data transmitted in clear text by the application
-
Use of Microsoft SQL Server authentication to the database, resulting in clear text credentials
-
Lack of transport or application layer encryption
-
Insecure network-hardware administrative interfaces
-
Use of the .NET Remoting TCP Channel to remote components
Attacks
The attacker places packet-sniffing tools on the network to capture traffic.
Countermeasures
Countermeasures to prevent packet sniffing include the following:
-
Use secure authentication, such as Windows authentication, that does not send passwords over the network.
-
Encrypt SQL Server authentication credentials. If you use SQL Server authentication, you can encrypt credentials automatically by installing a server certificate on the database server.
-
Secure communication channels. Options include using Secure Sockets Layer (SSL) or Internet Protocol Security (IPSec).
-
Use remote procedure call (RPC) encryption with Enterprise Services applications.
-
Use a segmented network, which can isolate eavesdropping to compromised segments.
-
Use the HttpChannel and SSL with .NET Remoting.
Unauthorized Access
If you fail to block the ports used by applications that run on the application server at the perimeter firewall, an external attacker can communicate directly with the application server. If you allow computers other than the front-end Web servers to connect to the application server, the attack profile for the application server increases .
Vulnerabilities
Vulnerabilities that can result in unauthorized access include:
-
Weak perimeter network and firewall configurations
-
Superfluous ports open on the internal firewall
-
Lack of IPSec policies to restrict host connectivity
-
Unnecessary active services
-
Unnecessary protocols
-
Weak account and password policies
Attacks
Common attacks to gain unauthorized access include:
-
Port scanning that detects listening services
-
Banner grabbing that gives away available services and possibly software versions
-
Malicious application input
-
Password attacks against default accounts with weak passwords
Countermeasures
Countermeasures to prevent unauthorized access include:
-
Firewall policies that block all traffic except expected communication ports
-
TCP/IP filtering or IPSec policies to prevent unauthorized hosts from establishing connections
-
Disabling unused services
-
Static DCOM endpoint mapping that allows access only to authorized hosts
Viruses, Worms, and Trojan Horses
These attacks are often not noticed until they begin to consume system resources, which slows down or halts the execution of other applications. Application servers that host IIS are susceptible to IIS attacks.
Vulnerabilities
-
Unpatched servers
-
Running unnecessary services
-
Unnecessary ISAPI filters and ISAPI extensions
Countermeasures
Countermeasures that help mitigate the risk posed by viruses, Trojan horses, and worms include:
-
Promptly applying the latest software patches
-
Disabling unused functionality, such as unused ISAPI filters and extensions
-
Running processes with least privileged accounts to reduce the scope of damage in the event of a compromise
EAN: 2147483647
Pages: 613