Software Update Services Setup and Configuration
| You can configure the Automatic Update client to use Software Update Services (SUS) rather than public update servers by manually changing the system Registry (not recommended) or using the system's Control Panel. You can also configure settings through a local Group Policy on a standalone system or through a domain Group Policy object (GPO) for a domain member system. The Automatic Update client software is included by default with the following Microsoft products:
If you're running an earlier version of Windows that supports automatic updates, you can download the component separately from the Microsoft Web site and install it on your system. You can find the available download by following http://www.microsoft.com/windows2000/downloads/recommended/susclient/ to the download page. The Automatic Update client software can be installed on the following operating systems if it's not already present:
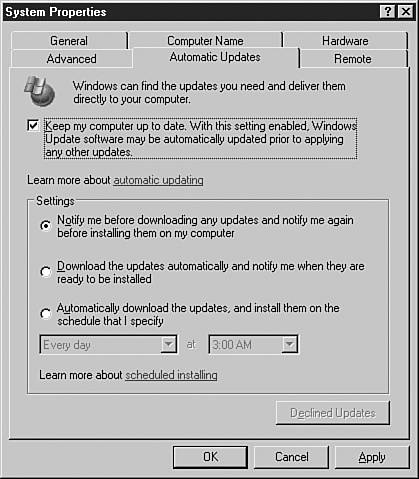
When configuring the settings manually, an administrator needs to access the System Properties dialog box through Control Panel or by right-clicking My Computer and choosing Properties. Either method opens the dialog box to the Automatic Updates tab, as shown in Figure 7.8. Figure 7.8. The Automatic Updates tab in the System Properties dialog box. You can use this dialog box to configure update options for your system. You can notify users before any updates are downloaded and notify them before any updates are installed after the download is finished. You can change the default settings so that the system automatically downloads any available updates whenever it's connected to the Internet. You can also notify users after the download is finished and updates are available to install. Given the choice, users can install updates immediately or later. To download updates automatically at a specified interval, select the Automatically Download the Updates, and Install Them on the Schedule That I Specify radio button. The Automatic Update client on Windows Server 2003 uses the Background Intelligent Transfer Service (BITS) built into the operating system. BITS allows downloading updates to the local system using only the available idle bandwidth so that update downloads do not unnecessarily slow down other network activity the client system might be engaged in. BITS runs on the local system, logs on with the local system account, and depends on Remote Procedure Calls (RPC) to function. The Automatic Update client is available on Windows XP SP1 and Windows Server 2003 by default. If you are running Windows 2000 Server and Professional (SP2 or earlier) or the original release of Windows XP, you can download the Automatic Update client from the Microsoft Web site or have it automatically installed by applying the required service packs. The least amount of administrative effort (and the best security practice) involves testing and deploying service packs on your systems because one of the main goals of installing clients is to use the Windows Update site to remind you that those service packs need to be installed.
For a client system using Automatic Update via the Windows Update site, the update process involves the Automatic Update client checking servers at the Windows Update Web site daily in an effort to download new update packages. The client then installs them automatically or notifies the user that the updates are available locally for installation. SUS is a server component installed on your Windows 2000 Server or Windows Server 2003 system behind a secure firewall on your corporate network. It synchronizes with the public Windows Update site on behalf of your clients and is designed to support up to 15,000 clients. As the administrator, you can create an SUS distribution point for downloaded updates to be made available to clients in your environment in one of two ways:
The Automatic Update client is available by default on the following operating systems:
Earlier versions of Windows 2000 and XP can be configured with the Automatic Update client through a separate download. From the standpoint of least administrative effort, installing service packs on the operating system rather than manually installing the client is recommended. After the Automatic Update client is installed on systems, they can connect to a server running SUS on your internal network and receive any available updates from it instead of connecting to the Internet to download updates from the Microsoft site. As the administrator, you control which server each Windows client should connect to for its updates (if you are running more than one SUS server across multiple sites) and schedule when the client should install critical updates. You can also decide which updates can be installed by allowing only approved updates to be made available to clients. Currently, SUS allows distribution of Windows critical updates, critical security updates, and security rollups. It does not deploy service packs or driver updates, and it does not have a mechanism for deploying software packages outright , as Systems Management Server (SMS) does. SUS is based on clients going through the SUS server to download updates. Clients check with their registered SUS server (or the Windows Update site, if that is what they're configured to use) on a regular specified basis, such as once a night, for updates that are ready to be deployed. SMS 2.0 can be configured in many different ways and is predominantly deployed using push technology, in which updates ready to be deployed to SMS clients are pushed to them, instead of clients going through the server for update downloads. The SUS server component can be installed on Windows 2000 Server or Windows Server 2003 systems and should meet the following system requirements:
You can install SUS on your IIS-enabled server by downloading the software from http://www.microsoft.com/windows2003/windowsupdate/sus/default.asp. After the download is finished, run the SUSSetup.msi file to begin the installation and follow the menu prompts for a Typical installation. After the setup is complete, you can continue with the Setup Wizard to open the SUS Administration Web site in Internet Explorer. When you install SUS on a computer running Windows 2000 Server, Windows Server 2003, or Microsoft Small Business Server 2000 with SP1, the IIS Lockdown v2.0 tool is also installed during setup, if it is not already installed on the local system, and includes URL Scanner v2.5. The SUS updating procedure starts when the SUS server runs a scheduled synchronization with Windows Update and receives new packages of updates. The administrator then reviews the newly downloaded packages and establishes the severity and criticality of the updates for the enterprise. An administrator then deploys the updates on test systems so that they can be verified against standard desktop, laptop, and server build standards. This verification helps ready the new packages of updates for distribution in the enterprise. After updates have been approved, clients configured to use Automatic Update and SUS check their SUS server daily and download any approved update packages from the SUS server that aren't already installed locally. At the scheduled update time, SUS checks whether a user with appropriate permissions is logged on to run the update installation. By default, users need to be logged on using an account with administrator access (or the equivalent) to the local system.
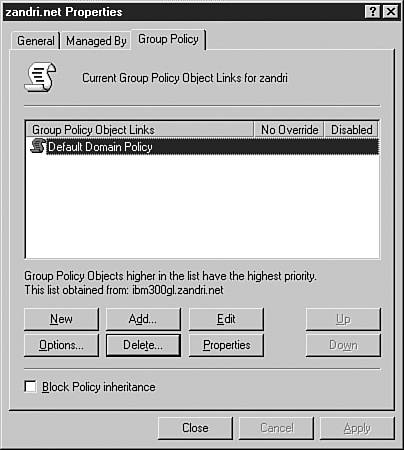
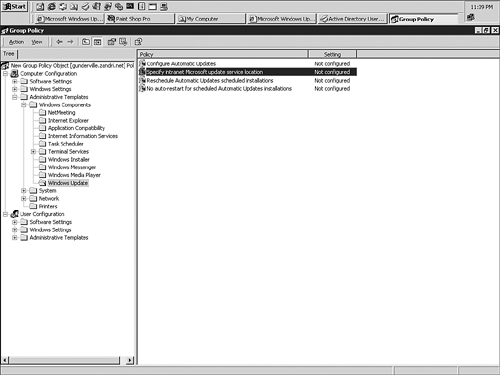
The Automatic Update client checks whether the newly applied updates require restarting the server or client; if so, it restarts the system after all packages are installed. If no restarts are needed, the installation simply ends. In either case, the updates are finished and Automatic Update waits for the next scheduled check before starting the process again. After SUS is up and running, you must configure client systems to use SUS instead of attempting to use the Windows Update site. You can do this locally in a system's local policy (remembering that in a domain, local policy is overwritten by GPOs linked to the site, domain, and OU), in the Control Panel, or by using Group Policies (when multiple domain members need to be configured at once). The configuration of Automatic Update through linked GPOs always takes precedence over user-defined options and Automatic Update Control Panel options are grayed out on the target computer. To configure the required settings via Group Policies, log on as Administrator to the domain, or open Active Directory Users and Computers using RUNAS and log on using an account with the required level of access. Right-click on the domain, choose Properties, and select the Group Policy tab, as shown in Figure 7.9. Figure 7.9. The Group Policy tab of the domain's Properties dialog box. You could edit the default domain policy, but creating another policy for these types of secondary settings is usually recommended. To do this, click the New button and name the new policy that appears in the window. Then click the Edit button to make changes in the Group Policy window. In this window, expand the Computer Configuration node, and then expand Administrative Templates and Windows Components to reach the Windows Update item. The four available settings are shown in Figure 7.10. Figure 7.10. Windows Update settings listed in the Group Policy window. In the pane on the right, double-click Configure Automatic Updates to enable the same settings for all systems in the domain. You can set domainwide behavior to any of the following:
Next, double-click the Specify Intranet Microsoft Update Service Location item and change its setting to Enabled. Enter the name of the internal SUS server that clients in the domain should use. You can use a server name, such as http://INT-SUS, or an IP address. If you need to make these changes immediately, you could enter secedit /refreshpolicy machine_policy /enforce at a command prompt and press Enter, which refreshes the Group Policy; otherwise , you could wait for the next refresh interval for domain controllers, which is five minutes by default. After either event has occurred, all your domain clients are configured through Group Policies to use Automatic Update in the manner you specified in the Configure Automatic Updates setting. These updates are performed against your internal SUS server, which is specified in the Specify Intranet Microsoft Update Service Location setting. |
EAN: 2147483647
Pages: 123