The FTP User
| After installing Ubuntu, an FTP user will be created. This user is not a normal user per se, but a name for anonymous FTP users. The FTP user entry in /etc/passwd looks like ftp:x:14:50:FTP User:/home/ftp:/bin/false Note The FTP user, as discussed here, applies to anonymous FTP configurations and server setup. Also, note that other Linux distributions might use a different default directory, such as /usr/local/ftp, for FTP files and anonymous users. This entry follows the standard /etc/passwd enTRy: username, password, User ID, Group ID, comment field, home directory, and shell. To learn more about /etc/password, see the section "The Password File" in Chapter 14, "Managing Users." Each of the items in this entry is separated by colons. In the preceding example, you can see that the Ubuntu system hosting the server uses shadowed password because an x is present in the traditional password field. The shadow password system is important because it adds an additional level of security to Ubuntu; the shadow password system is normally installed during the Ubuntu installation. The FTP server software uses this user account to assign permissions to users connecting to the server. By using a default shell of /bin/false for anonymous FTP users versus /bin/bash or some other standard, interactive shell, an anonymous FTP user, will be unable to log in as a regular user. /bin/false is not a shell, but a program usually assigned to an account that has been locked. As root inspection of the /etc/shadow file shows (see Listing 23.2), it is not possible to log in to this account, denoted by the * as the password. Listing 23.2. Shadow Password File ftp User Entry
The shadow file (only a portion of which is shown in Listing 23.2) contains additional information not found in the standard /etc/passwd file, such as account expiration, password expiration, whether the account is locked, and the encrypted password. The * in the password field indicates that the account is not a standard login account; thus, it does not have a password. Although shadow passwords are in use on the system, passwords are not transmitted in a secure manner when using FTP. Because FTP was written before the necessity of encryption and security, it does not provide the mechanics necessary to send encrypted passwords. Account information is sent in plain text on FTP servers; anyone with enough technical knowledge and a network sniffer can find the password for the account you connect to on the server. Many sites use an anonymous-only FTP server specifically to prevent normal account passwords from being transmitted over the Internet. Figure 23.4 shows a portion of an ethereal capture of an FTP session for an anonymous user and his password ("foobarbaz"). The ethereal client is a graphical browser used to display network traffic in real time, and it can be used to watch packet data, such as an FTP login on a LAN. Figure 23.4. The ethereal client can filter and sniff FTP sessions to capture usernames and passwords.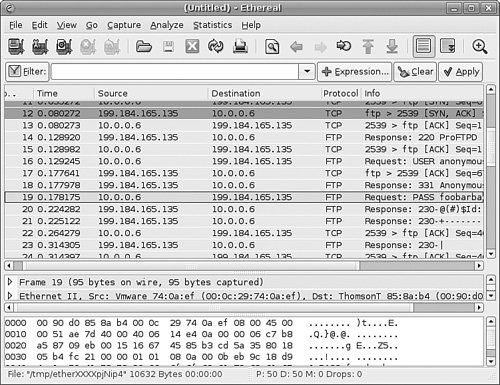
|
EAN: 2147483647
Pages: 318