13-10 IPSec VPN Tunnels
-
IP Security (IPSec) protects and authenticates IP packets between peers at the network layer using encryption, data integrity, origin authentication, and rejection of replayed packets.
-
IPSec is useful for building intranet, extranet, and remote user access VPNs.
-
IPSec supports the following standards:
-
"Security Architecture for the Internet Protocol" (RFC 2401), as well as RFCs 2402 through 2410
-
IKE (Internet Key Exchange)
-
DES (Data Encryption Standard)56-bit DES-CBC with Explicit IV and 168-bit 3DES
-
MD5 (Message Digest 5: HMAC variant) hash algorithm
-
SHA (Secure Hash Algorithm: HMAC variant) hash algorithm
-
AH (Authentication Header) data authentication and anti-replay services
-
ESP (Encapsulating Security Payload) data privacy, data authentication, and anti-replay services
-
-
"Tunnels" or s ecurity associations (SAs) are set up between two peers when sensitive packets are transported. Sensitive traffic is defined by access lists, applied to interfaces through crypto map sets. Security protocols and settings are negotiated by transform sets.
NOTE
IPSec ESP and AH protocols use protocol numbers 50 and 51, and IKE uses UDP port 500. Be sure that these protocol and port numbers are not blocked. Also, if NAT is used, use static translations so that IPSec works with global addresses.
Configuration
-
Configure IKE for key management.
If IKE is to be used, it must be configured according to Section 13-9. If IKE is not used, it must be manually disabled with the (global) no crypto isakmp enable command. Otherwise, IKE is enabled on all interfaces by default and needs to be configured.
-
(Optional) Define the global lifetimes for SAs:
(global) crypto ipsec security-association lifetime seconds seconds (global) crypto ipsec security-association lifetime kilobytes kilobytes
SAs times out when one of two conditions is met: the "timed" lifetime after seconds has elapsed (the default is 3600 seconds, or one hour ), or the "traffic volume" lifetime after kilobytes of traffic has passed through the tunnel (the default is 4608000 KBps or 10 MBps for one hour). These lifetimes are negotiated when an SA is established, using the smaller of the values from the two peers.
-
Define crypto access lists to define protected traffic.
-
Create an access list:
(global) access-list access-list-number ...
-OR-
(global) ip access-list extended name
The extended access list (named or numbered) must define which IP traffic is to be protected by IPSec. A crypto map references this access list to identify traffic to protect at an interface. Select the outbound traffic to be protected with a permit. Both inbound and outbound traffic is evaluated against this "outbound" access list. Try to use only one permit to identify the traffic, and avoid using the any keyword so that protected traffic will be accurately identified.
NOTE
On the remote IPSec peer, you need to define a similar crypto access list. However, that access list should be a "mirror image" of this one. In other words, the source and destination addresses should be reversed in the remote peer's crypto access list.
-
-
Define transform sets of IPSec features.
-
Create a transform set:
(global) crypto ipsec transform-set transform-set-name transform1 [ transform2 [ transform3 ]]
A transform set named transform-set-name (a text string) is defined with up to three different transforms, defining IPSec protocols and algorithms. Transform sets are negotiated between peers when an SA initiates. Therefore, multiple transform sets can be defined within a crypto map. If IKE is not used, only one transform set can be defined.
You can choose up to three transforms, as follows :
(Optional) Pick one AH transform:
-
ah-md5-hmac AH with MD5 authentication
-
ah-sha-hmac AH with SHA authentication
-
ah-rfc-1828 Older legacy AH authentication
(Optional) Pick one ESP encryption transform:
-
esp-des ESP with 56-bit DES encryption
-
esp-3des ESP with 168-bit 3DES encryption
-
esp-rfc-1829 Older legacy ESP (no authentication)
-
esp-null Null encryption
and one of these authentication methods :
-
esp-md5-hmac ESP with MD5 authentication
-
esp-sha-hmac ESP with SHA authentication
(Optional) Pick an IP compression transform:
-
comp-lzs IP compression with the LZS algorithm
AH provides data authentication and anti-replay services, and ESP provides packet encryption and optional data authentication and anti-replay services.
Use an ESP encryption transform to maintain data confidentiality. Use an ESP authentication transform to maintain data integrity, or an AH authentication transform to maintain the integrity of the payload and the outer IP header. The SHA authentication algorithm is stronger than MD5 but more CPU- intensive (it is slower).
Recommended transform sets are
(global) crypto ipsec transform-set name esp-des esp-sha-hmac
-OR-
(global) crypto ipsec transform-set name ah-sha-hmac esp-des esp-sha-hmac
-
-
(Optional) Select the mode of the transform set:
(crypto-transform) mode { tunnel transport }
IPSec can protect data using two methods. With tunnel mode (the default), the original IP packet is encrypted and/or authenticated and is encapsulated in a new IP packet. Only the peers' outside addresses are seen; the protected inside addresses are hidden from view. With transport mode, only the payload of the original IP packet is encrypted and/or authenticated. The protected inside addresses still appear in the original IP headers.
If a router requests tunnel mode, only tunnel mode can be negotiated between the peers. However, if transport mode is requested , either transport or tunnel mode (more secure) can be negotiated.
-
-
Define crypto maps with IPSec policies.
Crypto maps link a crypto access list and identify remote peers, the local address, a transform set, and a negotiation method.
-
(Optional) Use manual security associations (no IKE negotiation).
-
Create the crypto map:
(global) crypto map map-name sequence ipsec-manual
The crypto map is named map-name (a text string). It is assigned a priority or sequence number to be tried during negotiation. A lower sequence is tried first.
-
Reference the crypto access list to identify protected traffic:
(crypto-map) match address access-list
The access list can be a named or numbered extended IP list.
-
Identify the remote IPSec peer:
(crypto-map) set peer { hostname ip-address }
-
Specify the transform set to use:
(crypto-map) set transform-set transform-set-name
The transform set must be identical to the one used on the remote peer.
-
(AH authentication only) Manually set the AH keys:
(crypto-map) set session-key inbound ah spi hex-key-data (crypto-map) set session-key outbound ah spi hex-key-data
The security parameter index, spi (256 to 4,294,967,295, or FFFF FFFF), is set to uniquely identify an SA. The hex-key-data field is used to enter a session key (hexadecimal; 8 bytes for DES, 16 bytes for MD5, and 20 bytes for SHA).
-
(ESP only) Manually set the ESP SPIs and keys:
(crypto-map) set session-key inbound esp spi cipher hex-key-data [ authenticator hex-key-data ] (crypto-map) set session-key outbound esp spi cipher hex-key-data [ authenticator hex-key-data ]
The security parameter index, spi (256 to 4,294,967,295, or FFFF FFFF), is set to uniquely identify an SA. The cipher hex-key-data field is used to enter a session key (hexadecimal; 8 bytes for DES, 16 bytes for MD5, and 20 bytes for SHA). The authenticator keyword can be used to set a hex-key-data string for ESP authentication.
-
-
(Optional) Use IKE established security associations.
-
Create the crypto map:
(global) crypto map map-name sequence ipsec-isakmp
The crypto map is named map-name (a text string). It is assigned a priority or sequence number to be tried during negotiation. A lower sequence is tried first.
-
Reference the crypto access list to identify protected traffic:
(crypto-map) match address access-list
The access list can be a named or numbered extended IP list.
-
Identify the remote IPSec peer:
(crypto-map) set peer { hostname ip-address }
-
Specify the transform set to use:
(crypto-map) set transform-set transform-set-name
The transform set must be identical to the one used on the remote peer.
-
(Optional) Define the SA lifetimes if they are different from the global defaults:
(crypto-map) set security-association lifetime seconds seconds (crypto-map) set security-association lifetime kilobytes kilobytes
SAs time out when one of two conditions is met: the "timed" lifetime after seconds has elapsed (the default is 3600 seconds, or one hour), or the "traffic volume" lifetime after kilobytes of traffic has passed through the tunnel (the default is 4608000 KBps or 10 MBps for one hour). These lifetimes are negotiated when an SA is established using the smaller of the values from the two peers.
-
(Optional) Use a separate SA for each source/destination host pair:
(crypto-map) set security-association level per-hostBy default, all traffic between two IPSec peers that matches a single crypto map access list permit entry shares one SA. In other words, SAs are defined at the granularity of the crypto access lists. Use this command to create separate SAs for each pair of hosts . Be aware that this can create too many individual SAs, overwhelming the router's resources.
-
(Optional) Use Perfect Forward Secrecy (PFS) for each new SA:
(crypto-map) set pfs [ group1 group2 ]
PFS allows the router to exchange a new Diffie-Hellman key each time a new SA is negotiated. If one SA key is cracked, only that SA can be compromised. The next SA will have a different key. The PFS groups are group1 (use the 768-bit Diffie-Hellman prime modulus group ) and group2 (use the 1024-bit Diffie-Hellman prime modulus group). Generating new Diffie-Hellman keys requires more CPU time.
-
-
(Optional) Use dynamic security associations with IKE (one peer is mobile, or not fixed).
-
Create a dynamic crypto map:
(global) crypto dynamic-map dyn-map-name dyn-seq-num
Remote peers can initiate an IPSec negotiation with the local router. If it is successful, an SA and a temporary crypto map entry are created. When the SA expires , the temporary crypto map is deleted. Notice that the crypto access list and the peer identification parameters are now optional for the dynamic map. Only the transform set must be defined.
-
(Optional) Reference the crypto access list to identify protected traffic:
(crypto-map) match address access-list
The access list can be a named or numbered extended IP list.
-
(Optional) Identify the remote IPSec peer:
(crypto-map) set peer { hostname ip-address }
-
Specify the transform set to use:
(crypto-map) set transform-set transform-set-name
The transform set must be identical to the one used on the remote peer.
-
(Optional) Define the SA lifetimes if they are different from the global defaults:
(crypto-map) set security-association lifetime seconds seconds (crypto-map) set security-association lifetime kilobytes kilobytes
SAs time out when one of two conditions is met: the "timed" lifetime after seconds has elapsed (the default is 3600 seconds, or one hour), or the "traffic volume" lifetime after kilobytes of traffic has passed through the tunnel (the default is 4608000 KBps or 10 MBps for one hour). These lifetimes are negotiated when an SA is established using the smaller of the values from the two peers.
-
(Optional) Use Perfect Forward Secrecy (PFS) for each new SA:
(crypto-map) set pfs [ group1 group2 ]
PFS allows the router to exchange a new Diffie-Hellman key each time a new SA is negotiated. If one SA key is cracked, only that SA can be compromised. The next SA will have a different key. The PFS groups are group1 (use the 768-bit Diffie-Hellman prime modulus group) and group2 (use the 1024-bit Diffie-Hellman prime modulus group). Generating new Diffie-Hellman keys requires more CPU time.
-
Add the dynamic crypto map set to a regular map set:
(global) crypto map map-name sequence ipsec-isakmp dynamic dyn-map-name [ discover ]
The dynamic crypto map named dyn-map-name is used as a template for new SA requests from peers. Therefore, the dynamic map must be added to the regular crypto map named map-name.
The dynamic keyword allows Tunnel Endpoint Discovery (TED) to discover remote peers. When the dynamic crypto map permits an outbound packet, a probe is sent to the original destination to try to discover a remote IPSec peer. As soon as the probe is answered , the peers have identified each other, and normal IKE negotiation can occur.
Dynamic crypto maps should always be referenced as the last map set to try during a negotiation. The sequence number should be higher than any other map sets so that more-specific map sets are matched against first.
-
(Optional) Use IKE mode client configuration:
(global) crypto map map-name client configuration address [ initiate respond ]
If IKE mode is configured (see Section 13-9), the crypto map must also be configured so that the router can either set the client's address ( initiate ) or offer an address to a requesting client ( respond ).
-
(Optional) Use preshared IKE keys from a AAA server:
(global) crypto map map-name isakmp authorization list list-name
VPN users can have secret preshared keys stored on a AAA server rather than using a CA to manage certificates for the users. The crypto map causes AAA authorization to be used to retrieve the preshared keys. The list-name field is the AAA authorization method list configured on the router. (See Section 13-2.)
-
-
-
Apply crypto maps to interfaces.
-
Specify a crypto map to use:
(interface) crypto map map-name
The crypto map named map-name is applied to the interface. Traffic matching the crypto access list referenced by the crypto map triggers IPSec to initiate and negotiate an IPSec SA with a peer. Inbound traffic matching the crypto access list, but unable to trigger a successful SA, is dropped. Outbound traffic not matching the crypto access list is forwarded normally.
-
(Optional) Share a crypto map with other interfaces:
(global) crypto map map-name local-address interface-id
All SAs use the same local interface IP address rather than using the addresses of each interface with a crypto map applied. This allows you to use a loopback interface as the IPSec endpoint for increased availability.
-
Example
The example from Section 13-9 is continued here, to add the commands necessary to implement IPSec. These commands appear below the dashed line in the configuration. Figure 13-1 shows a network diagram for this example.
Figure 13-1. Network Diagram for the IKE/IPSec Example
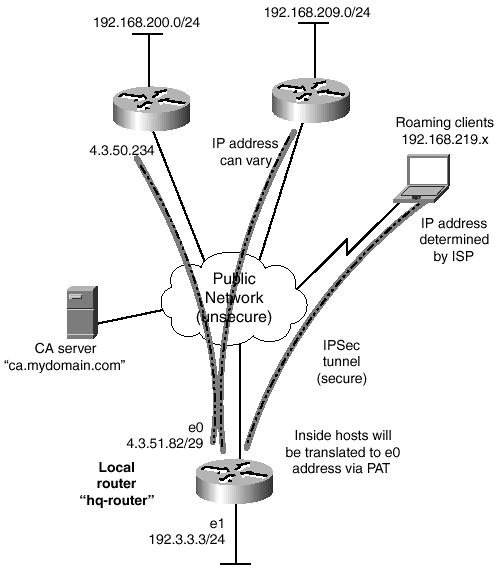
Here, an IPSec tunnel is configured between the internal protected network 192.3.3.0 and a client's private network 192.168.200.0 with access list 102. This list is used for a tunnel to a specific peer with a known fixed IP address. Two other private networks at client sites are 192.168.209.0 and 192.168.219.0, identified by access list 103. This list is used to match the addresses of dynamic clients , where the peer's IP address is unknown.
The IPSec transform set called basic-3des consists of esp-3des (ESP with 3DES encryption) and esp-md5-hmac (ESP with MD5 authentication). Remote peers attempting to bring up an IPSec tunnel with this router must have an identical transform set.
A crypto map called Clients contains several policies so that VPN peers with varying capabilities can negotiate parameters. The first crypto map policy (10) uses access list 102 to match traffic traveling between the local and remote private networks. The policy identifies a specific IPSec peer at 4.3.50.234 and associates the basic-3des transform set.
For dynamic VPN peers to negotiate a tunnel, a dynamic crypto map called ISPpeers is used. Access list 103 is used to match the local and remote private networks at the possible tunnel endpoints. (Address matching is optional in a dynamic crypto map; it is performed here for clarity.) The basic-3des transform is used for peer negotiations. The dynamic crypto map is applied to the Clients crypto map as policy 30. It will be matched against after negotiations for all lower-numbered policies fail.
The crypto map Clients is applied to the outside network interface, Ethernet 0. Outbound traffic matching the addresses identified in the crypto map will cause IPSec to be triggered.
Notice that Network Address Translation (NAT) is also configured on this router. The Ethernet 0 interface IP address is used for port address translation, according to traffic permitted by access list 101. Here, access list 101 denies traffic matching the source and destination addresses that are involved in the VPN tunnel so that NAT is not used. All other outbound traffic triggers NAT. This is known as a split tunnel, in which both VPN and non-VPN traffic must be forwarded out the same interface. In this case, some traffic must travel over the VPN tunnel, and other traffic must be forwarded normally.
hostname hq-router ip domain-name mydomain.com ip name-server 4.2.2.1 ip name-server 4.2.2.2 crypto isakmp policy 10 encryption 3des authentication rsa-sig crypto isakmp policy 20 encryption des authentication pre-share lifetime 900
NOTE
At this point, the crypto key generate rsa command should be run from the EXEC- level prompt.
crypto ca identity mydomain enrollment url http://ca.mydomain.com:80 crl optional
NOTE
At this point, the crypto ca authenticate mydomain command should be run from the EXEC-level prompt. This requests the CA's self-signed certificate. As soon as the CA sends it, the certificate is added to the configuration as something like this:
crypto ca certificate chain mydomain certificate ca 01 308201E5 ... quit
After that, the crypto ca enroll mydomain command can be run from the EXEC-level prompt. This requests a certificate from the CA for the local router. As soon as the CA approves and returns the certificate, it too is added to the configuration as something like this:
certificate 08 308201B2 ... quit
crypto isakmp key secretvpn1 address 192.168.219.1 ------------------------------------ access-list 102 permit ip 192.3.3.0 0.0.0.255 192.168.200.0 0.0.0.255 access-list 103 permit ip 192.3.3.0 0.0.0.255 192.168.209.0 0.0.0.255 access-list 103 permit ip 192.3.3.0 0.0.0.255 192.168.219.0 0.0.0.255 crypto ipsec transform-set basic-3des esp-3des esp-md5-hmac crypto map Clients 10 ipsec-isakmp match address 102 set peer 4.3.50.234 set transform-set basic-3des crypto dynamic-map ISPpeers 10 match address 103 set transform-set basic-3des crypto map Clients 30 ipsec-isakmp dynamic ISPpeers interface Ethernet0 description Outside network ip address 4.3.51.82 255.255.255.248 ip nat outside crypto map Clients interface Ethernet1 description Inside network ip address 192.3.3.3 255.255.255.0 ip nat inside ip nat inside source list 101 interface Ethernet0 overload access-list 101 deny ip 192.3.3.0 0.0.0.255 192.168.0.0 0.0.255.255 access-list 101 permit ip 192.3.3.0 0.0.0.255 any
EAN: N/A
Pages: 185