Section 11-2. Configuring Network Address Translation
|
|
11-2. Configuring Network Address TranslationYou can use Network Address Translation (NAT) to translate the IP address of a host on one IOS firewall interface to a different address on another interface. This is useful for conserving IP address space, as well as for isolating or hiding internal hosts behind public IP addresses so that they don't have a presence on the public network. Address translation is triggered by packets moving across NAT boundaries. The boundaries are marked by an inside and outside NAT interface. For example, when a packet arrives on an inside NAT interface and is forwarded on an outside NAT interface, address translation is triggered. The reverse is also truea packet arriving on the outside NAT interface triggers address translation on its way to an inside NAT interface. Naturally, the packet addresses must then match a configured NAT entry for the translation to actually take place. For example, you can configure NAT to translate a source or destination address that appears on an inside NAT interface. This is usually called inside NAT because it occurs on an inside NAT interface. You can also configure NAT to translate a source or destination address on an outside interface. This is called outside NAT. Inside NAT is typically used when host addresses on an inside private network need to appear as global addresses on an outside public network. Outside NAT is useful when host addresses on an outside interface need to appear as something else on an inside private network. NOTE Don't confuse inside and outside NAT interfaces with inside and outside firewall interfaces. These are two different conceptsone involving address translation boundaries and the other involving security policy boundaries. To avoid confusion, interfaces involved with NAT are always called NAT interfaces in this section. NAT OperationYou can configure NAT to translate addresses on an inside or outside NAT interface. NAT also can translate either source or destination addresses in IP packets passing through the IOS firewall. Because of its flexibility, NAT can be somewhat confusing to understand and configure. To simplify matters, NAT is based on the following concepts:
The local and global addresses apply to inside and outside hosts as well. For example, a host's inside local address is that host's original address as it appears on an inside NAT router interface. The inside global address is the inside host's translated address as it appears on an outside NAT interface. Figure 11-2 illustrates the NAT process. In this case, Host A is located on an inside NAT interface, and Host B is on an outside NAT interface. When Host A initiates a connection with Host B, the IOS firewall is configured to perform inside source address translation. In other words, for every packet that Host A sends through the IOS firewall toward Host B, the firewall translates the source address in the IP header. The inside source address is rewritten to become the corresponding global source address. Figure 11-2. NAT Through an IOS Firewall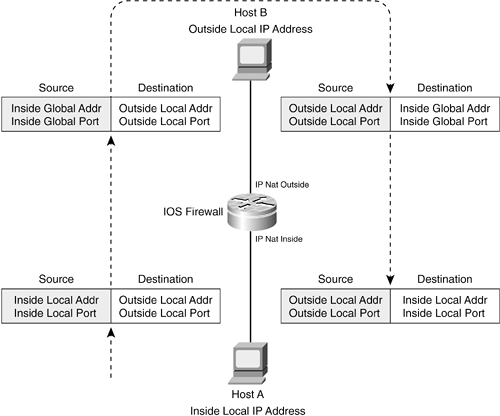 When packets return from Host B to Host A, the process is reversed. The object of the translation is now located in the destination address field of inbound packets. As the packets cross the NAT boundary, the inside global addresses are rewritten to the inside local address. This occurs automatically, without any configuration to translate the destination address. The firewall can determine the reverse translation based on the fact that the inbound packets pass in the reverse direction, from an outside NAT interface to an inside NAT interface. When connections are initiated between hosts and NAT is triggered, the IOS firewall adds an entry to its IP translation table. This entry can be one of two types:
Notice that the simple translation entry describes only the translation of a host's address. It isn't specific about UDP or TCP ports that need translating or about any target host addresses or ports. The idea is to use a simple translation as a catchall so that the translation occurs any time that host crosses the NAT boundary in the firewall. A simple translation entry can become ambiguous when several different types of NAT are configured for the same inside or outside addresses. For example, suppose an inside host with local address 192.168.1.1 is configured to be translated to global address 10.1.1.1. That NAT table entry might look like this: IOSFirewall# show ip nat translations Pro Inside global Inside local Outside local Outside global --- 10.1.1.1 192.168.1.1 --- --- IOSFirewall# This works fine as long as 192.168.1.1 can always appear as 10.1.1.1. Now suppose a second type of NAT is configured so that 192.168.1.1 is translated to a different global address (10.2.1.1) when the host opens a connection to a specific target address. You might expect that the firewall would create a second NAT translation table entry for 192.168.1.1. However, if the previous translation entry to global address 10.1.1.1 is already present in the table, the firewall incorrectly uses that one before creating a new one. When a local address needs to be translated in multiple ways, the simple translation entry doesn't have enough information to make each one unique. In other words, the translation becomes ambiguous and probably won't occur correctly. The extended translation entry, however, has enough information to be unique and unambiguous. For example, the following entry triggers a translation from the inside local address and port to the inside global address and port when the target is the outside local address and port listed: IOSFirewall# show ip nat translations Pro Inside global Inside local Outside local Outside global tcp 10.1.1.1:4383 192.168.17.1:4383 10.71.4.4:80 10.71.4.4:80 IOSFirewall# The extended entry is unique right down to the protocol (TCP) and ports being used, allowing the translations to be made correctly. You might have noticed that the extended entry looks very much like it is defining a TCP connection between the hosts. In fact, extended translation entries are often created dynamically as connections initiate. Security is one other aspect of the translation table that you need to consider. Address translation alone cannot provide a sufficient level of security. You should couple address translation with stateful packet inspection to become fully secure. However, a simple translation entry can introduce vulnerabilities. The simple entry specifies only the translation of the local host to the global address, which also means that hosts on the outside can potentially reach the inside host by using its global address. If the firewall is configured to permit the inbound traffic, a malicious host on the outside can freely contact the inside host. This scenario is not true with the extended translation. The translation occurs only for traffic passing between two specific hosts using a specific protocol and two specific port numbers. Hosts other than those in the extended entry would not be able to send traffic through the translation and through the firewall. As you work through NAT configuration, be aware that certain types of NAT create simple translation entries, and other types create extended entries. For example, static NAT and NAT triggered by an access list both create simple entries. Static PAT and NAT triggered by a route map create extended entries. Using Static Address Translations
Static translations can be defined for a single host or for all addresses contained in an IP subnet. Port static address translations allow a specific UDP or TCP port on a global address to be translated to a specific port on a local address. In other words, both address and port numbers are translated. Several inside local addresses can be translated into a single global address, each having a distinct global port number. Outside hosts can access one global address for many different services, depending on the port number used. The port numbers are translated to individual local hosts on the inside. Port static translation can be very handy if your service provider gives you only one IP address to use for the outside IOS firewall interface. In this case, no additional global addresses are available for static translations to inside hosts. Figure 11-4 shows how port static translation can be used. One global address, 172.17.3.3, is configured to represent three unique inside servers and their applications. Connections to 172.17.3.3 on TCP port 80 actually go to Host A at 192.168.5.100 on TCP port 80. Connections to 172.17.3.3 on TCP port 25 go to Host B at 192.168.5.101 on TCP port 25. Finally, connections to 172.17.3.3 on UDP port 53 go to Host C at 192.168.5.102 on UDP port 53. Figure 11-4. Port Static NAT Operation Across an IOS Firewall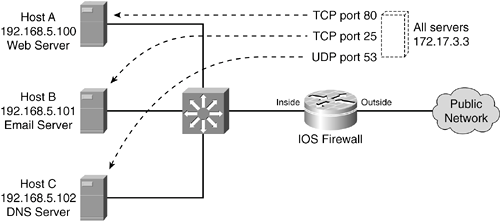 To configure static NAT on an IOS firewall, follow these steps:
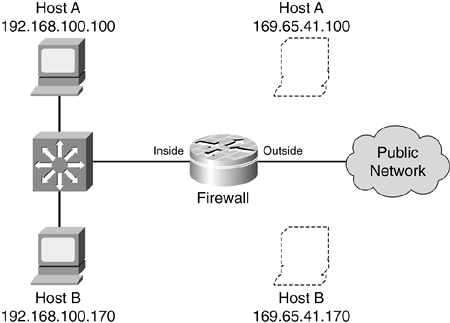
Static NAT ExampleFor the example shown in Figure 11-3, the IOS firewall can be configured with the following commands: IOSFirewall(config)# ip nat inside source static 192.168.100.100 169.65.41.100 IOSFirewall(config)# ip nat inside source static 192.168.100.170 169.65.41.170 IOSFirewall(config)# interface fastethernet 0/0 IOSFirewall(config-if)# description Inside NAT interface IOSFirewall(config-if)# ip address 192.168.100.1 255.255.255.0 IOSFirewall(config-if)# ip nat inside IOSFirewall(config-if)# exit IOSFirewall(config)# interface fastethernet 0/1 IOSFirewall(config-if)# description Outside NAT interface IOSFirewall(config-if)# ip address 169.65.41.1 255.255.255.0 IOSFirewall(config-if)# ip nat outside After this configuration, the NAT translation table has the following contents: IOSFirewall# show ip nat translations Pro Inside global Inside local Outside local Outside global --- 192.168.100.100 169.65.41.100 --- --- --- 192.168.100.170 169.65.41.170 --- --- IOSFirewall# Conditional or Policy Static NAT ExampleYou can also reference a route map to identify specific conditions or policies that trigger a static translation. Even though the static NAT entry is created and put into the NAT table, the actual translation entries that are used are generated dynamically as traffic matches the route map. For example, inside host 192.168.17.1 should be translated to global address 10.1.108.251 when it exchanges packets with any address in the 10.1.111.0/24 subnet. Likewise, the same host should be translated to global address 10.1.108.252 when it communicates with any address in the 10.1.89.0/24 subnet. You can configure the IOS firewall for these policy NAT operations as follows: IOSFirewall(config)# ip access-list extended acl-test1 IOSFirewall(config)# permit ip 192.168.17.0 0.0.0.255 10.1.111.0 0.0.0.255 IOSFirewall(config)# exit IOSFirewall(config)# ip access-list extended acl-test2 IOSFirewall(config)# permit ip 192.168.17.0 0.0.0.255 10.1.89.0 0.0.0.255 IOSFirewall(config)# exit IOSFirewall(config)# route-map test1 IOSFirewall(config-route-map)# match ip address acl-test1 IOSFirewall(config-route-map)# exit IOSFirewall(config)# route-map test2 IOSFirewall(config-route-map)# match ip address acl-test2 IOSFirewall(config-route-map)# exit IOSFirewall(config)# ip nat inside source static 192.168.17.1 10.1.108.251 route-map test1 IOSFirewall(config)# ip nat inside source static 192.168.17.1 10.1.108.252 route-map test2 The configuration is somewhat involved, but it follows a hierarchy. The ip nat commands reference route maps, which reference access lists to match traffic. After you enter the configuration, the NAT translation table looks like this: IOSFirewall# show ip nat translations Pro Inside global Inside local Outside local Outside global --- 10.1.108.251 192.168.17.1 --- --- --- 10.1.108.252 192.168.17.1 --- --- IOSFirewall# These entries look more like regular static NAT definitions in the output, with no hint about the underlying route map condition. You can add the verbose keyword to see specific flags for an entry. For example, the following output shows that the static NAT entry uses a route map when the inside local address passes through the firewall: IOSFirewall# show ip nat translations verbose Pro Inside global Inside local Outside local Outside global --- 10.1.108.251 192.168.17.1 --- --- create 13:06:05, use 05:03:57 timeout:0, Map-Id(In): 0, flags: static, route-map-static, use_count: 0, entry-id: 83, lc_entries: 0 When the static entry is actually triggered, the route map generates a fully extended entry in addition to the simple static entry. For example, inside local host 192.168.17.1 has attempted to ping outside host address 10.1.111.3 in the following output: IOSFirewall# show ip nat translations Pro Inside global Inside local Outside local Outside global icmp 128.163.108.251:9 192.168.17.1:9 10.1.111.3:9 10.1.111.3:9 --- 10.1.108.251 192.168.17.1 --- --- --- 10.1.108.252 192.168.17.1 --- --- IOSFirewall# Port Static Translation ExampleFor the example shown in Figure 11-4, you can configure the port static translations on the IOS firewall with the following commands: IOSFirewall(config)# ip nat inside source static tcp 192.168.5.100 80 172.17.3.3 80 IOSFirewall(config)# ip nat inside source static tcp 192.168.5.101 25 172.17.3.3 25 IOSFirewall(config)# ip nat inside source static udp 192.168.5.102 53 172.17.3.3 53 IOSFirewall(config)# interface fastethernet 0/0 IOSFirewall(config-if)# description Inside NAT interface IOSFirewall(config-if)# ip address 192.168.5.1 255.255.255.0 IOSFirewall(config-if)# ip nat inside IOSFirewall(config-if)# exit IOSFirewall(config-if)# interface fastethernet 0/1 IOSFirewall(config-if)# description Outside NAT interface IOSFirewall(config-if)# ip address 172.17.3.1 255.255.255.0 IOSFirewall(config-if)# ip nat outside After this configuration, the NAT translation table looks like the following: IOSFirewall# show ip nat translations Pro Inside global Inside local Outside local Outside global tcp 172.17.3.3:80 192.168.5.100:80 --- --- tcp 172.17.3.3:25 192.168.5.100:25 --- --- udp 172.17.3.3:53 192.168.5.100:53 --- --- IOSFirewall# Using Dynamic Address TranslationsDynamic address translations can be used when local hosts share or "hide behind" one or more common global addresses. In this mode, one local address can't permanently reserve a global add-ress for translation. Instead, address translation occurs on a many-to-one basis, and translation entries are created only as they are needed. As soon as a translation entry is free from use, it is deleted and made available to other local hosts. This type of translation is most useful for outbound connections, in which inside hosts are assigned a dynamic address or port number only as connections are made. Dynamic translation does not allow unsolicited connections to reach inside hosts from the outside, however. This is because the address translations are not put into place until they are needed. An IOS firewall can translate local addresses dynamically in two ways:
If both dynamic NAT and PAT are configured, an IOS firewall assigns a dynamic NAT entry first, until the entire address pool is exhausted. As soon as that occurs, dynamic PAT is used until a pool address becomes available again.
Follow these steps to configure dynamic address translation:
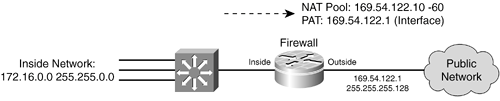
Each idle time can be given as seconds (1 to 536,870 seconds). To specify an unlimited time, use 0 or the never keyword. TIP After a translation table entry has been created, you can display its various time stamps by using the show ip nat translations verbose command. For example, the following output shows a fully extended translation entry for an HTTP connection after the FIN flag has been sent to close the connection. The connection was created 00:00:27 seconds ago, it was last used 00:00:25 seconds ago, and 00:00:34 seconds are left in the idle timer: IOSFirewall# show ip nat translations verbose Pro Inside global Inside local Outside local Outside global tcp 207.246.96.46:3294 192.168.199.56:3294 64.227.225.60:80 64.227.225.60:80 create 00:00:27, use 00:00:25, left 00:00:34, Map-Id(In): 1, flags: extended, timing-out, use_count: 0 Dynamic Address Translation ExampleFor the example shown in Figure 11-5, you can configure dynamic address translation on the IOS firewall with the following commands: IOSFirewall(config)# ip nat pool global-NAT-pool 169.54.122.10 169.54.122.60 netmask 255.255.255.0 IOSFirewall(config)# ip access-list standard NAT-trigger1 IOSFirewall(config-std-nacl)# permit 172.16.0.0 0.0.255.255 IOSFirewall(config-std-nacl)# exit IOSFirewall(config)# ip access-list standard NAT-trigger2 IOSFirewall(config-std-nacl)# permit 172.16.0.0 0.0.255.255 IOSFirewall(config-std-nacl)# exit IOSFirewall(config)# ip nat inside source list NAT-trigger1 pool global-NAT-pool IOSFirewall(config)# ip nat inside source list NAT-trigger2 interface fastethernet 0/0 overload IOSFirewall(config)# interface fastethernet 0/0 IOSFirewall(config-if)# ip nat outside IOSFirewall(config-if)# interface fastethernet 0/1 IOSFirewall(config-if)# ip nat inside Notice that the dynamic NAT and PAT configurations (the ip nat inside source commands) use two different access lists to trigger the translations. If you define multiple ip nat inside source list commands, you must use unique ACLs for each. Therefore, two ACLs are defined with exactly the same configuration and are applied to a dynamic NAT and dynamic PAT process. |
|
|
EAN: 2147483647
Pages: 120