Section 8-4. Firewall Load-Balancing Appliance
|
|
8-4. Firewall Load-Balancing ApplianceA Cisco CSS acts as a multilayer switch and performs FWLB as well as many other types of content processing. A CSS interface can carry a single VLAN or a trunk with multiple VLANs. A CSS unit must be placed on each side of a firewall farm so that connections are load-balanced to the firewalls in each direction. Firewalls are defined individually rather than as a distinct firewall farm. The CSS performs a route lookup on each inbound connection to determine the possible firewalls that can be used. The CSS then computes the exclusive OR (XOR) of the source and destination IP addresses as a hash value to select which firewall will receive the connection. Keepalives (custom ICMP packets) are sent from one CSS to the other at regular intervals. If keepalives are not received from the opposite CSS through a firewall, that firewall is declared dead (failed). CSS FWLB ConfigurationYou can use the following steps to configure FWLB on one CSS device. Remember that FWLB requires a load-balancing device on each side of the firewall farm. Be sure to repeat the entire configuration process for the outside and inside CSS FWLB platforms.
Each CSS unit expects to receive keepalive probes at regular intervals from the CSS on the other side of the firewall farm. The keepalive probes are sent every seconds (3 to 16; the default is 3 seconds) and are expected to be received every seconds. TIP You must configure the keepalive timeout interval identically for the CSS units on both sides of the firewall farm. With identical configurations, both units correctly detect a failed keepalive from each other at the same time. At that time, each unit declares its side of the firewall to be dead, and subsequent connections are assigned to another firewall. Otherwise, if both units don't detect the same failure, connections could be improperly assigned to the firewalls in an asymmetric fashion. TIP Each CSS sends an ICMP packet as a keepalive to the target address of the opposing CSS unit. Each CSS also substitutes the destination MAC address of the specific firewall that is being tested so that the keepalive probe passes through that firewall. For this reason, you must make sure that each firewall in the firewall farm is configured to pass ICMP packets between the two CSS IP addresses. The ICMP packets (both echo and echo-reply) must be able to pass through the firewall in both directions (outside to inside and inside to outside). CSS Appliance Firewall Load-Balancing ExampleThe network from the example in section 8-2 is reused here so that you can get a feel for the difference between IOS FWLB, CSM FWLB, and CSS FWLB configurations. Performing FWLB using this method requires two CSS load-balancing devices:
Figure 8-7 shows a network diagram for this example. Figure 8-7. Network Diagram for the CSS FWLB Example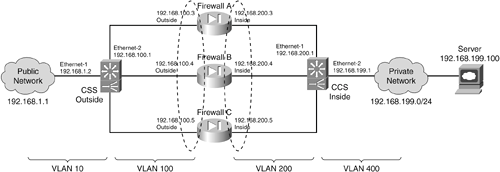 The firewall farm consists of three real firewalls. The outside (unprotected) interfaces of the three real firewalls are at 192.168.100.3, 192.168.100.4, and 192.168.100.5. On the outside, the default gateway to the public network is 192.168.1.1, and the outside CSS unit is at 192.168.1.2. The inside (protected) interfaces of the three real firewalls are at 192.168.200.3, 192.168.200.4, and 192.168.200.5. The inside CSS unit performs firewall load balancing for outbound traffic to the firewall farm. On the internal secure network (192.168.199.0/24), one server is in use at 192.168.199.100. This server supports both inbound HTTP and Telnet connections. Basic Firewall ConfigurationThis section begins with coverage of the firewall configurations. Firewalls A and B are FWSMs installed in the Catalyst A chassis. Firewall C is an external Cisco PIX Firewall, connected to Catalyst A through a Gigabit Ethernet link. This section shows the configuration commands to give you a basic idea of all the pieces that must be configured for FWLB using an FWLB appliance. Notice that all three firewalls have identical security policies configured. This is important because any of the three firewalls could be assigned connections from any pair of inside and outside hosts. Notice also that access list rules have been configured to allow the inside and outside CSS units to pass ICMP packets between each other. This is important to allow each CSS to monitor the health of each firewall: Firewall(config)# hostname fwsm-a fwsm-a(config)# nameif vlan100 outside security0 fwsm-a(config)# nameif vlan200 inside security100 fwsm-a(config)# ip address outside 192.168.100.3 255.255.255.0 fwsm-a(config)# ip address inside 192.168.200.3 255.255.255.0 fwsm-a(config)# icmp permit 192.168.100.0 255.255.255.0 outside fwsm-a(config)# icmp permit 192.168.200.0 255.255.255.0 inside fwsm-a(config)# static (inside,outside) 192.168.199.100 192.168.199.100 netmask 255.255.255.255 0 0 fwsm-a(config)# static (inside,outside) 192.168.200.1 192.168.200.1 netmask 255.255.255.255 0 0 fwsm-a(config)# static (inside,outside) 192.168.100.1 192.168.100.1 netmask 255.255.255.255 0 0 fwsm-a(config)# object-group icmp-type ICMP fwsm-a(config-icmp)# icmp-object echo fwsm-a(config-icmp)# icmp-object echo-reply fwsm-a(config-icmp)# icmp-object time-exceeded fwsm-a(config-icmp)# icmp-object unreachable fwsm-a(config-icmp)# exit fwsm-a(config)# access-list acl_out permit icmp host 192.168.100.1 host 192.168.200.1 fwsm-a(config)# access-list acl_out permit tcp any host 192.168.199.100 eq telnet fwsm-a(config)# access-list acl_out permit tcp any host 192.168.199.100 eq www fwsm-a(config)# access-list acl_out permit icmp any host 192.168.199.100 object-group ICMP fwsm-a(config)# access-list acl_in permit ip 192.168.199.100 255.255.255.255 any fwsm-a(config)# access-list acl_in permit icmp host 192.168.200.1 host 192.168.100.1 fwsm-a(config)# access-group acl_out in interface outside fwsm-a(config)# access-group acl_in in interface inside fwsm-a(config)# route outside 0.0.0.0 0.0.0.0 192.168.100.1 1 fwsm-a(config)# route inside 192.168.199.0 255.255.255.0 192.168.200.1 1 ________________________________________________________________ Firewall(config)# hostname fwsm-b fwsm-b(config)# nameif vlan100 outside security0 fwsm-b(config)# nameif vlan200 inside security100 fwsm-b(config)# ip address outside 192.168.100.4 255.255.255.0 fwsm-b(config)# ip address inside 192.168.200.4 255.255.255.0 fwsm-b(config)# icmp permit 192.168.100.0 255.255.255.0 outside fwsm-b(config)# icmp permit 192.168.200.0 255.255.255.0 inside fwsm-b(config)# static (inside,outside) 192.168.199.100 192.168.199.100 netmask 255.255.255.0 0 0 fwsm-b(config)# static (inside,outside) 192.168.200.1 192.168.200.1 netmask 255.255.255.255 0 0 fwsm-b(config)# static (inside,outside) 192.168.100.1 192.168.100.1 netmask 255.255.255.255 0 0 object-group icmp-type ICMP fwsm-a(config-icmp)# icmp-object echo fwsm-a(config-icmp)# icmp-object echo-reply fwsm-a(config-icmp)# icmp-object time-exceeded fwsm-a(config-icmp)# icmp-object unreachable fwsm-a(config-icmp)# exit fwsm-b(config)# access-list acl_out permit icmp host 192.168.100.1 host 192.168.200.1 fwsm-b(config)# access-list acl_out permit tcp any host 192.168.199.100 eq telnet fwsm-b(config)# access-list acl_out permit tcp any host 192.168.199.100 eq www fwsm-b(config)# access-list acl_out permit icmp any host 192.168.199.100 object-group ICMP fwsm-b(config)# access-list acl_in permit ip 192.168.199.100 255.255.255.255 any fwsm-b(config)# access-list acl_in permit icmp host 192.168.200.1 host 192.168.100.1 fwsm-b(config)# access-group acl_out in interface outside fwsm-b(config)# access-group acl_in in interface inside fwsm-b(config)# route outside 0.0.0.0 0.0.0.0 192.168.100.1 1 fwsm-b(config)# route inside 192.168.199.0 255.255.255.0 192.168.200.1 1 ________________________________________________________________ Firewall(config)# hostname pix-c pix-c(config)# interface gb-ethernet0 1000full pix-c(config)# interface gb-ethernet1 1000full pix-c(config)# nameif gb-ethernet0 outside security0 pix-c(config)# nameif gb-ethernet1 inside security100 pix-c(config)# ip address outside 192.168.100.5 255.255.255.0 pix-c(config)# ip address inside 192.168.200.5 255.255.255.0 pix-c(config)# icmp permit 192.168.100.0 255.255.255.0 outside pix-c(config)# icmp permit 192.168.200.0 255.255.255.0 inside pix-c(config)# static (inside,outside) 192.168.199.100 192.168.199.100 netmask 255.255.255.0 0 0 pix-c(config)# static (inside,outside) 192.168.200.1 192.168.200.1 netmask 255.255.255.255 0 0 pix-c(config)# static (inside,outside) 192.168.100.1 192.168.100.1 netmask 255.255.255.255 0 0 pix-c(config)# object-group icmp-type ICMP pix-c(config-icmp)# icmp-object echo pix-c(config-icmp)# icmp-object echo-reply pix-c(config-icmp)# icmp-object time-exceeded pix-c(config-icmp)# icmp-object unreachable pix-c(config-icmp)# exit pix-c(config)# access-list acl_out permit icmp host 192.168.100.1 host 192.168.200.1 pix-c(config)# access-list acl_out permit tcp any host 192.168.199.100 eq telnet pix-c(config)# access-list acl_out permit tcp any host 192.168.199.100 eq www pix-c(config)# access-list acl_out permit icmp any host 192.168.199.100 object-group ICMP pix-c(config)# access-list acl_in permit ip 192.168.199.100 255.255.255.255 any pix-c(config)# access-list acl_in permit icmp host 192.168.200.1 host 192.168.100.1 pix-c(config)# access-group acl_out in interface outside pix-c(config)# access-group acl_in in interface inside pix-c(config)# route outside 0.0.0.0 0.0.0.0 192.168.100.1 1 pix-c(config)# route inside 192.168.199.0 255.255.255.0 192.168.200.1 1 Outside CSS FWLB ConfigurationThe outside CSS unit is configured with three firewalls and three static routes. Notice that each of the static routes lists the internal (secure) network as the destination and has each firewall as a next-hop gateway address. Firewall keepalive probes are sent and are expected every 3 seconds by default. The configuration commands are as follows: (config) interface ethernet-1 (config-if) description "Outside public network" (config-if) bridge vlan 10 (config) circuit VLAN10 (config-circuit) description "Circuit to the outside network" (config-circuit) ip address 192.168.1.2 255.255.255.0 (config-circuit-ip) enable (config) interface ethernet-2 (config-if) description "Firewall farm outside" (config-if) bridge vlan 100 (config) circuit VLAN100 (config-circuit) description "Circuit to the firewall farm" (config-circuit) ip address 192.168.100.1 255.255.255.0 (config-circuit-ip) enable (config) ip route 0.0.0.0 0.0.0.0 192.168.1.1 (config) ip firewall 1 192.168.100.3 192.168.200.3 192.168.200.1 (config) ip firewall 2 192.168.100.4 192.168.200.4 192.168.200.1 (config) ip firewall 3 192.168.100.5 192.168.200.5 192.168.200.1 (config) ip route 192.168.199.0 255.255.255.0 firewall 1 1 (config) ip route 192.168.199.0 255.255.255.0 firewall 2 1 (config) ip route 192.168.199.0 255.255.255.0 firewall 3 1 (config) ip route 192.168.200.0 255.255.255.0 firewall 1 1 (config) ip route 192.168.200.0 255.255.255.0 firewall 2 1 (config) ip route 192.168.200.0 255.255.255.0 firewall 3 1 Inside CSS FWLB ConfigurationThe inside CSS unit is also configured with the inside addresses of the three firewalls. Notice this time that three static routes have been configured as default routes to reach the outside public network. Each one has a different firewall as a next-hop gateway address. Firewall keepalive probes are sent and are expected every 3 seconds by default. The configuration commands are as follows: (config) interface ethernet-1 (config-if) description "Firewall farm inside" (config-if) bridge vlan 200 (config) circuit VLAN200 (config-circuit) description "Circuit to the firewall farm" (config-circuit) ip address 192.168.200.1 255.255.255.0 (config-circuit-ip) enable (config) interface ethernet-2 (config-if) description "Inside private network" (config-if) bridge vlan 400 (config) circuit VLAN400 (config-circuit) description "Circuit to the inside network" (config-circuit) ip address 192.168.199.1 255.255.255.0 (config-circuit-ip) enable (config) ip firewall 1 192.168.200.3 192.168.100.3 192.168.100.1 (config) ip firewall 2 192.168.200.4 192.168.100.4 192.168.100.1 (config) ip firewall 3 192.168.200.5 192.168.100.5 192.168.100.1 (config) ip route 0.0.0.0 0.0.0.0 firewall 1 1 (config) ip route 0.0.0.0 0.0.0.0 firewall 2 1 (config) ip route 0.0.0.0 0.0.0.0 firewall 3 1 Displaying Information About CSS FWLBTable 8-4 lists the CSS commands that you can use to display helpful information about CSS FWLB configuration and status.
|
|
|
EAN: 2147483647
Pages: 120