Tools and Logs Available to You
Microsoft Windows 2000, COM+, IIS, and Microsoft SQL Server all record various security-related information to log files. It's imperative that you use these logs and appropriate logging and analysis tools to help resolve your issues. Failure to use these tools will lead to wasted time and much frustration.
Using MMC to Its Fullest
The Microsoft Management Console (MMC) allows you to add administration tools to a single administration console. Using this functionality, you can create tools customized for security. For example, one of the authors created an administration tool that has the following snap-ins installed:
- Event Viewer
- Custom view of the Event Viewer, filtering success and failed logon and logoff events in the security log
- Custom view of the Event Viewer, filtering COM+ events in the application log
- Custom view of the Event Viewer, filtering Distributed COM (DCOM) events in the system log
- Custom view of the Event Viewer, filtering SQL Server events in the application log
- A Web page with a URL that points to the SQL Server log files
- A Web page with a URL that points to the IIS log files
The tool is shown in Figure 11-1.
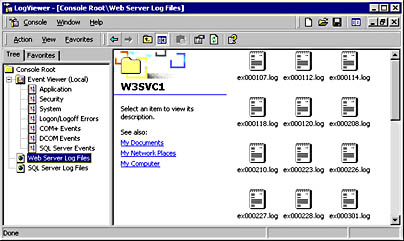
Figure 11-1. The author's LogViewer tool, which is a collection of Event Viewer views and log file locations in MMC.
You can create the tool by performing these steps:
- Click Start, and then click Run.
- Type mmc.exe, and press Enter.
- Choose Add/Remove Snap-in from the Console menu.
- Click Add.
- Scroll and select the Event Viewer snap-in, and click Add.
- Click Finish, click Close, and then click OK.
Next, we need to add a custom Logon/Logoff view of the Security log:
- Right-click the Security log, and choose New Log View from the context menu.
- Press F2, and type Logon/Logoff Errors. Then press Enter.
- Right-click Logon/Logoff Errors, and choose Properties from the context menu.
- Click the Filter tab.
- Select the Information, Warning, and Error check boxes. Make sure that the Success Audit and Failure Audit event types are selected.
- Select Security in the Event Source drop-down list box.
- Select Logon/Logoff in the Category drop-down list box, and click OK.
To create a custom view for COM+ events, DCOM events, and SQL Server events, repeat these steps but use the options shown in Table 11-1. Note that in each case the event types are not changed; use the default settings.
Table 11-1. Custom Event Viewer views.
| View Name | Event Log | Event Source | Category |
|---|---|---|---|
| COM+ events | Application | COM+ | All |
| DCOM events | System | DCOM | All |
| SQL Server events | Application | MSSQLServer | All |
Now we need to add the SQL Server log view and the Web server log view. To do so, perform these steps:
- Choose Add/Remove Snap-in from the Console menu.
- Click Add.
- Scroll to the Link To Web Address snap-in, and click Add.
- Enter the URL location of the SQL Server log files. By default, it is file://c:\mssql7\log for SQL Server 7 and file://c:\Program Files\Microsoft SQL Server\MSSQL\log for SQL Server 2000.
- Click Next, and type SQL Server Log Files.
- Click Finish.
- Highlight Link To Web Address, and click Add.
- Enter the URL location of the Web Server log files. By default, it is file://c:\winnt\system32\logfiles\w3svc1.
- Click Next, and type Web Server Log Files.
- Click Finish.
- Click Close and then OK.
Finally, save the log viewer settings by performing these steps:
- Choose Save As from the Console menu.
- Enter the filename—for example, LogViewer.msc.
- Click Save.
NOTE
You can also add extra event log snap-ins that point to each server. For example, if you have five servers—ServerA through ServerE—you can open the Security Event Logs on each machine from a single MMC instance. It makes cross-referencing distributed security much easier.
Other Helpful Tools
You can use a number of other tools to troubleshoot problems. Some are part of Windows 2000, and others are in included in the Microsoft Windows 2000 Server Resource Kit. Table 11-2 gives a brief overview of each tool.
Table 11-2. Useful tools to aid in security troubleshooting.
| Tool | Location | Comments |
|---|---|---|
| IPSecMon | Windows 2000 | IPSecMon displays the active security associations between computers. It's useful to help diagnose Internet Protocol Security (IPSec) failures. |
| SQL Server Profiler | SQL Server | SQL Server Profiler monitors events produced through SQL Server. It's useful to determine which user account is accessing SQL Server and which queries are being used. |
| Network Monitor | Windows 2000 | Network Monitor captures and displays network data packets received and sent by a computer running Windows 2000. Network administrators can use Network Monitor to detect and troubleshoot networking problems. Network Monitor identifies many protocols, including HTTP, SMB, TPC, UDP, IP, RPC, and many more. |
| ElogDmp | Resource Kit | ElogDmp displays any of the Windows 2000 logs. When used in conjunction with the Windows 2000 FindStr command, it allows you to query for specific event log entries. |
| CyberSafe Log Analyst | Resource Kit | CyberSafe Log Analyst is an MMC snap-in that analyzes the Windows 2000 Security Event Log. The tool allows you to organize and interpret a computer's Security Event Log, providing more effective, systemwide user activity analysis. |
| Dumpel | Resource Kit | Dump Event Log is a command line tool that dumps an event log for a local or remote system into a tab-separated text file. When used in conjunction with the FindStr command, it's useful for finding that elusive "needle-in-the-haystack" information in a large log. |
| RPings and RPingc | Resource Kit | This tool confirms remote procedure call (RPC) connectivity between RPC servers and clients on a network. RPC Ping checks to see if RPC services are responding to RPC requests from client computers. It is very handy if you suspect an RPC or DCOM connection is failing due to RPC/DCOM configuration settings. |
| RPCdump | Resource Kit | This command line tool queries RPC endpoints for status information. RPC Dump interrogates the endpoint mapper database to obtain a list of every registered endpoint. Optionally, the tool pings each endpoint to determine whether the service that registered the endpoint is listening. This tool can help to isolate network troubles involving RPC. |
| ShowGrps | Resource Kit | This command line tool shows the groups to which a user belongs. It's useful if you don't have immediate access to Windows 2000 administration tools. |
| WhoAmI | Resource Kit | This tool, discussed in detail in Chapter 3 ("Windows 2000 Security Overview") displays information about the current user and optionally extra information from the user's token such as group membership and privileges. |
| W3Who | Resource Kit | W3Who is an Internet Server Application Programming Interface (ISAPI) application that works within an IIS Web page to display information about the calling user and the configuration of the Web server. It is somewhat similar in principle to WhoAmI. |
The Value of TimeIf you're going to be analyzing multiple log files from multiple computers, you should synchronize the time on each computer; otherwise, hunting down issues will be much harder because log entries will have differing date stamps. If you're running a Windows 2000 environment with a Windows 2000-based domain controller and computers running Windows 2000 in the same domain, the Windows Time Service synchronizes time automatically. If your client computers are not running Windows 2000, you can use either the net time command or a tool that synchronizes with the domain controller by using the Simple Network Time Protocol (SNTP).
A Little-Known Troubleshooting Trick
It's often useful to determine the identities processes are using, especially when dealing with complex access denied errors. One tool for doing this is Plist.exe in the Microsoft Windows 2000 Server Resource Kit. Another method is to use Terminal Server. When Terminal Server is installed, it adds a process identity option to the Task Manager tool, as shown in Figure 11-2. You can enable this option from the View menu.
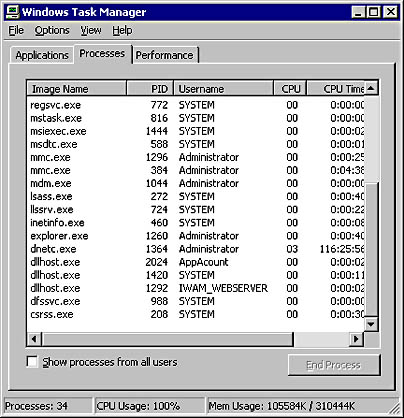
Figure 11-2. Task Manager displaying process identities when Terminal Server is installed.
EAN: N/A
Pages: 138
- Challenging the Unpredictable: Changeable Order Management Systems
- The Second Wave ERP Market: An Australian Viewpoint
- A Hybrid Clustering Technique to Improve Patient Data Quality
- Relevance and Micro-Relevance for the Professional as Determinants of IT-Diffusion and IT-Use in Healthcare
- Development of Interactive Web Sites to Enhance Police/Community Relations