Edge Modules
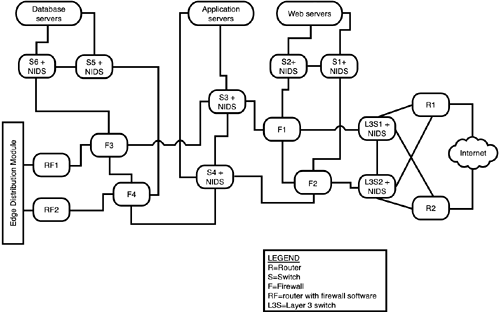
| The edge, of course, consists of the portions of your network that interact with the outside world, whether that outside is an ISP, the telephone system, or a leased line. It can also include customers, people who actually want to send you money for your goods and services. Of course, when money is involved, the security requirementsand the reliability requirementsbecome very important. Therefore, it helps to separate commercial activity from the rest of your interactions with the outside world. Even among the others, different kinds of security problems arise with different kinds of connectivity, so the Enterprise SAFE Blueprint addresses each type in a separate module. E-Commerce ModuleThe E-Commerce module is fully redundant. It is shown in Figure 6.3; the various server sets are, indeed, multiple servers, each of whom is connected to both switches of the pair serving them: Figure 6.3. E-Commerce module. Ingress for customer traffic from the Internet can come over either of two routes, from ISP A or ISP B, as represented by the perimeter routers R1 and R2. Three types of servers sets exist:
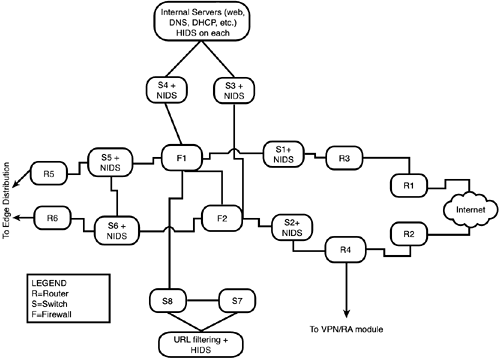
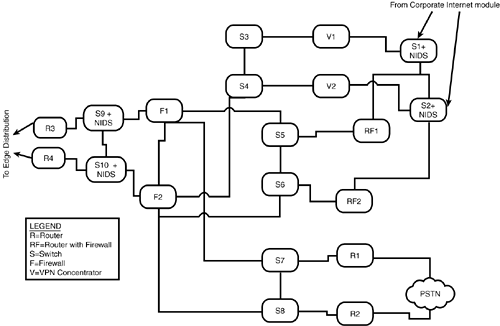
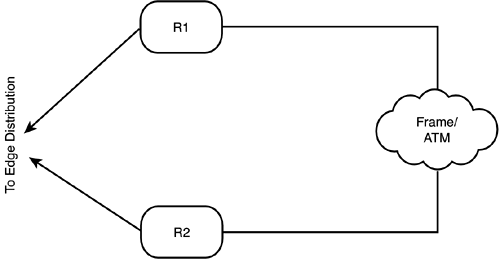
The server types are isolated from one another, not only by switches, but by firewalls as well. A compromised Web server will not easily infect an application server or a database server. Speaking of switches and firewalls, these are redundant as well (with a pair serving each distribution point), along with the perimeter routers at the two module edges (the Internet and the Edge Distribution module). Firewalls connect to single switches instead of to both members of a redundant set (to simplify firewall data-passage rules). Each switch has an associated NIDS device, while the Layer 3 switches at the Internet- facing edge have NIDS installed (Layer 3 switches are used in addition to the routers for traffic load handling in hardware, leaving the routers to do what they do best: route traffic). Each of the Layer 2 switches segregating server sets can implement private VLANs to force traffic between devices to pass through Layer 3 for inspection and filtering. Finally, before any traffic is sent to the Edge Distribution module, it must also pass through a router with a software firewall set installed. This might seem like a "belt-and-suspenders" approachin fact, the entire system might seem overdonebut this module is most likely to be attacked, both early and often. At the same time, performance matters to customers, so functions are highly segmented: Each device has only a limited number of functions to perform, enabling you to optimize it to perform them securely at speed (they should not cause congestion or be a choke point). Different security techniques make this frequently attacked and potentially compromised module unlikely to provide an attack path into the corporate network. Both redundancy and resiliency are built in. Design AlternativesThe simplest design alternative to this module is to let someone else handle it: Offload the e-commerce infrastructure to a service provider. If this is done, the connection to manage the e-commerce resources will take place over the Internet connection, requiring the capability to secure that (such as encrypted tunnels or private lines to the e-commerce management access). In addition, depending on the sensitivity of the commerce conducted (high monetary value, for instance), it might be desirable to use additional firewalls to isolate devices further. Security generally is enhanced if different firewall types are used, limiting the utility of a single exploit. Corporate Internet ModuleUnlike the E-Commerce module, the Corporate Internet Module is about internal access out (while e-commerce is about external access in, into a very specially protected space called the DMZ). Of course, replies to internal-out traffic are permitted, but unsolicited external-origin traffic is extremely limited, if it is permitted at all. The internal structure of the Corporate Internet module is shown in Figure 6.4. Figure 6.4. Corporate Internet module. This module is simpler, needing less firewalling (although all traffic to or from the Internet must pass through a firewall). As with the E-Commerce module diagram, Internet access via R1 and R2 passes through the ISP modules (which are not shown, to keep the diagram at a manageable size). In addition to NIDS with most of the switches, the servers themselves have HIDS. The "doubling" of routers at the Internet edge might seem superfluous, but the goal again is efficiency: The perimeter routers (R1 and R2) perform fundamental filtering and rate limiting, while R3 and R4 perform traffic distribution, including to the VPN/Remote Access module. The switches again use private VLANs to protect individual devices. The NIDS are usually appliances attached to the relevant switch; if throughput is an issue, a Layer 3 switch can use a dedicated blade for a NIDS and take advantage of the greater throughput of the switch's backplane. Design AlternativesThe NIDSs on the path from the Internet to the firewalls record potential attacks that the firewalls might silently discard. This is useful information. However, if no basic filtering is being done at Internet access (on R3 and R4), these NIDSs might be overwhelmed. One other design alternative is to eliminate the "extra" routers at the Internet edgeR3 and R4and collapse their functions into R1 and R2. This depends on how comfortable you are with the performance of your devices at R1 and R2, as well as how much work they have to do (how busy your Internet connections are and how much filtering is actually done at your ISPs before the traffic gets to your edge). VPN/Remote Access ModuleThe VPN/Remote Access module needs to accommodate incoming traffic from three different sources: remote sites (via the Corporate Internet module, passing into a router/firewall), remote users (also via the Corporate Internet module, but passing into a VPN concentrator), and dialup users (via the PSTN). Tunnels can be GRE, IPSec, L2TP, or PPTP. The router/firewall and VPN concentrator are both capable of handling tunnel termination for many tunnels; the router handling termination of dialup access need not handle so many. By segregating the ingress of the three types, the load on each ingress device is manageable; the structure is shown in Figure 6.5. Figure 6.5. VPN/Remote Access module. Layer 2 switches distribute the traffic, but paths through the firewalls are kept discrete as much as possible while maintaining redundancy. The device roles are quite similar to what you have seen in previous modules. One item to remember is that VPNs using IPSec might need IKE (UDP port 500) and ESP (protocol 50), plus UDP port 10000 if the ESP traffic must be tunneled inside UDP because of firewalling or NAT traffic management between the two endpoints. Segregating the traffic limits how many openings you need on the ingress devices. As a further note, remember that the dialup users should always be required to authenticate with CHAP rather than PAP. Design AlternativesDesign alternatives for this module are discussed in a separate whitepaper , the VPN SAFE Blueprint, which we cover (though not deeply) in Chapter 7. WAN ModuleThe WAN module is very simple, consisting of ingress from the service providers' networks and filtering on the ingress routers. It is shown in Figure 6.6. Figure 6.6. WAN module. Design AlternativesThe simpler the design, the fewer the points from which you can diverge to an alternative. In the case of such a simple design as the WAN module, the only alternative is to protect even further the data traveling over private circuits through encryption (IPSec). Edge SummaryThat is the enterprise edge, a group of modules that are designed to filter and analyze traffic, segregating it into portions of like type that can be processed by devices optimized for just that task. Internally, these modules use segregation again to mitigate the effects of any attack that penetratestechniques such as a switched architecture, to minimize the knowledge that can be gained with packet sniffers; private VLANs, to minimize the opportunity to leverage a compromise of one host into the compromise of others; and stateful firewalls. That leaves the heart of the network, the enterprise campus. |
EAN: 2147483647
Pages: 177