Threat Types
| Whether it comes at you from the outside or from within, the threat to your network can take one of four broad forms:
ReconnaissanceReconnaissance is a word that evokes thoughts of war and military observers scanning for targets through binoculars and then placing the acquired target information on maps used to plan the attack. The analogy is apt; network reconnaissance is indeed the unauthorized discovery, mapping, and monitoring of the systems and services in a network, along with probing for their vulnerabilities. To do all this, an unauthorized person uses target discovery, network commands, ping sweeps and port scans , eavesdropping, and information theft. Target DiscoveryFinding out what is available to be attacked starts at the very broad level: domain names and IP address blocks. The discovery process gradually narrows the target definition, expanding the names and narrowing the address ranges until the person has individual hostnames and addresses. Certain targets are easier to discover than others because some are required to be publicly listed. For instance, DNS records must list the publicly accessible servers and their addresses so that the public can access them ( name resolution must work). But if you create the hypothetical BillyBong Corporation and obtain a registered block of addresses, that block can be learned via the Registry. (Regional Internet Registries are ARIN, RIPE, APNIC, and LACNIC; AfriNIC has been proposed but not yet accepted by ICANN at this time.)
Network CommandsWhen a hacker has a notion of addresses and names, it's time to do some serious probing. Simple utilities built into the TCP/IP stack are where most hackers start:
Some of these utilities are not found in systems running the various versions of Microsoft Windows, but they are generally present in Unix and Unix-derived systems (such as Linux, OpenBSD, or FreeBSD). Ping Sweeps and Port ScansNetwork mapping is much easier when it can be automated. People become bored and make silly mistakes manually repeating a command, but, of course, a computer never gets bored and ( essentially ) never makes mistakes (although code can become corrupted). Ping sweeps check for a reply (an ICMP Echo) from a series of addresses, and scripts to run such a sweep are easily located. Commercial versions are available for network management (as a way to discover unauthorized hosts surreptitiously added to your network); ping sweep scripts also are available at hacker Web sites (run an Internet search for "warez," for example). Port scans test a given address across a range of commonly open ports or across a set range of ports (or even across all 65,535 TCP ports and 65,535 UDP ports, for those so inclined). Most hackers do not scan all possible ports, for two logical reasons. First, it takes some time, and repeated probes for an open port from a single address are likely to get the ISP a phone call, costing the hacker her access. Second, not every port is vulnerable, whereas some ports are almost always openand putting the effort where the reward is likely to be found is as typical of a hacker as it is of anyone else. Commonly probed ports are those used for networking, for typically installed services, and for services left operating by default installations of operating systems or applications. The Internet Storm Center is one site that reports on attack statistics. As this is being written, its most commonly probed ports and associated protocols are as follows (this list rarely changes):
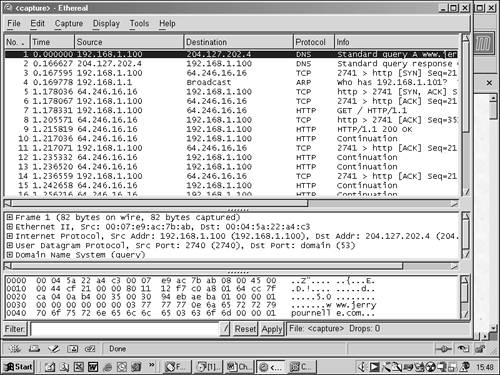
The proportion of probes for each of these ports in North America might be different from the proportion on other continents, but the same ports are generally probed everywhere. The end of the chapter includes a reference where you can check for the most current information in your area of interest. EavesdroppingChildren are generally taught that eavesdropping is not polite, but they learn from experience that it can be a good way to learn things that you weren't supposed to know. That's true of networks as well. Just as with eavesdropping on a spoken conversation, network eavesdropping is the passive monitoring of information flowing back and forth. It is often performed by software collectively known as packet sniffers . Packet sniffers work very simply: They place the network connection on their host in promiscuous mode, where it processes every packet on the wire instead of only those addressed to the physical address (or a configured multicast address). In a shared wire, such as classical Ethernet or a hubbed network, the traffic of many hosts can be observed . Sniffers can filter traffic to capture only those packets bound for certain ports where interesting information can be discovered (for example, traffic bound for POP3 connections might carry plain-text email passwords). Figure 3.1 shows the output of a popular sniffer, Ethereal. Figure 3.1. Web traffic as seen by Ethereal. Notice that you can pick out a particular packet and examine it in more detail. The middle pane shows this to be a DNS request; notice that the "layering" of information is a reverse of the OSI model (the bottom is the application layer, while the physical-layer information is at the top). I also turned on name resolution so that, in the upper pane, I can see the hostname of the destination instead of the IP address. All of this is a simple example of an extremely powerful tool and one that you might well see reference to on the exam. That is because sniffing traffic is a favorite technique of hackers. Packet sniffers are relatively small software packages, with low overhead, which makes them generally unnoticeable because they have little performance impact. This means that any compromised host on the network could become an unnoticed spy if the package could be installed surreptitiously.
Information TheftHaving discovered some useful information, such as hostnames and IP addresses, usernames and passwords, and possibly other information, it becomes time to make use of that information. Posing as a legitimate user , the hacker can copy confidential data, make changes (even worseindustrial espionage could become industrial sabotage ), use the account to create another user account known only to the hacker, and so on. The last possibility means that the hacker now can steal information even if the current user changes his password or that user account is terminated . Unauthorized AccessThat leads to Cisco's second type of security threat: unauthorized access. However an unauthorized person gains access, when that person has even the most basic access, it is common to make efforts to escalate the access into that with more privileges. One means is to crack the master password list, such as the Unix/Linux /etc/shadow or the Windows NT SAM hive (actually, the passwords are not decrypted; instead, the cracking routine matches a retrieved hash by creating one using the same encryption algorithm known to be used by the OS). If that seems farfetched, utilities are available in the hacker community to do this for either OS. For passwords to offer real instead of phantom protection, the organization must have and enforce a strong password policy. The Unix "r commands" rlogin , rsh , rcp can be used to exploit trusted computing relationships among systems, just as trust relationships among Windows domains can be exploited. After getting into a system via a compromised account of exploited trust relationship, a hacker seeks to gain access to an account with more privileges (greater access, in terms of both scope of access and depth of access). This is known as escalating privilege . Escalating privilege, whether through obtaining the password or exploiting trust, is intended to gain the hacker control: the privileges of the Unix/Linux root account or the Windows Administrator account.
Another means of gaining unauthorized access is social engineering , the process of obtaining the information needed because people give it up on their own (sometimes just because they were asked for it). This exploits trust, too, but it is the trust we have of people rather than the trust among computer systems. Social-engineering attacks will never be prevented by technology because no technology is really involved. Many of the protocols used in a network are insecure ; they operate on an assumption of trust and do not protect the information they pass. Protocols such as Telnet, NTP, SNMP, and CDP can be exploited to manipulate the network devices, which are the nervous system of the organization. Cisco strongly recommends that, as much as possible, insecure protocols should be replaced with secure ones, such as replacing Telnet with SSH (Secure Shell). Network-management protocols should use the strongest version available, with authentication and/or encryption. Remember, unauthorized access to networking devices provides the hacker with far more opportunities for mischief than access to a single host. Therefore, control over access to routers and switches often needs to be stronger than that used to protect the average host. Denial of ServiceOf course, if the hacker can't get in, he can try to ensure that no one else can, either. This is the denial-of-service attack, usually just known as DoS. We tend to think of DoS as flooding a line with packets; that is indeed one method of denying service. Others are to fill a buffer (such as filling a mail queue with spam) or to request more processes than the maximum allowed for a service, thereby cutting off that service from real users. These are all instances of resource overload ; when a critical resource is overloaded, other (legitimate) users of the resource must be denied . Typical DoS attacks are listed here:
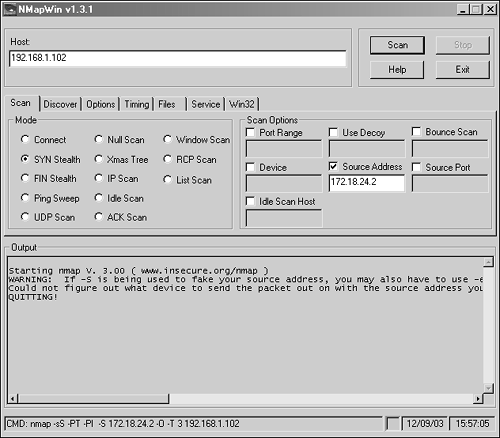
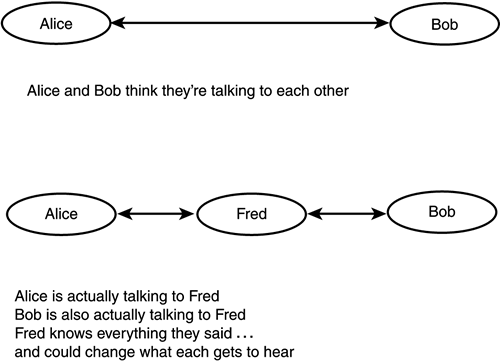
Although DoS attacks do not try to obtain information directly, bear in mind that, depending on which item crashes under the load, their effect can expose other resources that were previously protected. One average desktop system can output a surprising number of packets with which to attack; combining attacks from several systems can overwhelm even robust networks. The combined attack is known as distributed denial of service , or DDoS. A simple form of DDoS attack sends a series of pings from several systems to a network broadcast address. The source IP for these pings is forged to appear to be that of the machine that is the actual DDoS target. The members of the network all obligingly reply to each ping they receive, and the TCP/IP stack of the target is overwhelmed with replies to a request that it did not send (but it must process each reply somewhat just to learn what it was, when the address reveals that this system is indeed the proper recipient of each packet). And that forging leads to the final threat type: data manipulation. Data ManipulationData manipulation can take many forms. Because targets are not likely to take attacks upon them kindly, it is common to manipulate the source IP address of a packet sent by a hacker. This is surprisingly easy to do; Figure 3.2 is a screenshot of NMapWin, a Windows version of the nmap tool. Notice the opportunity (in the middle right of the GUI) to forge the source IP address. Figure 3.2. Spoofing the source IP address. Conveniently, NMapWin even tells you the command-line syntax to use to implement this the old-fashioned way (look at the status bar along the bottom). IP headers are not the only address elements forged; much spam is created with false email headers to make tracing the spammer more difficult. Another form of data manipulation is the man-in-the-middle attack, in which a system interposes itself between the two parties in a dialogue, pretending to each of them that it is actually the other party rather than a third party. In this manner, the third party receives both sides of the conversation and can manipulate what each intended recipient sees. The idea behind this is shown in Figure 3.3. Figure 3.3. Man-in-the-middle attack. Somewhat similar is the session replay or session hijacking form of data-manipulation attack. The difference here is that the hacker is the endpoint of your conversation, even though he pretends to be the other party (the other party isn't actually involved). A session replay reuses information, some of which can be altered , to create a new action (a new payment, for instance, in a larger amount or to a new payee). Session hijacking redirects traffic in an actual system data exchange, diverting it from the real other party to a hacker posing as that party. This can be done by noting the pattern of TCP sequence numbers and their change, and then interposing a packet with the predicted sequence number. Finally, data can be diverted from its proper destination to a bogus one, such as a Web browser session being diverted to a good forgery of a Web page ( rerouting ); likewise, one party to an actual transaction might deny that the transaction ever took place. The latter is called repudiation and can be done to prevent a third party (such as the debt collector) from proving that the transaction occurred. Although the data itself is not necessarily manipulated, its validity as it currently exists is questioned because it cannot be proven that it was not manipulated. This makes repudiation a case of requiring proof of a non-event, that there was no attack. This is much more difficult to prove , and the methods for handling nonrepudiation ensure that it is reasonably provable. |
EAN: 2147483647
Pages: 177