| Question 1 | Which of these commands will disable CDP? (Choose two.) -
A. no cdp enable in global configuration mode. -
B. no cdp run in global configuration mode. -
C. no cdp enable in interface configuration mode. -
D. no cdp run in interface configuration mode. -
E. None of these is correct. |
| Question 2 | The VPN software client establishes what parameters during IKE negotiations with the headend? (Choose two.) |
| Question 3 | A 6500-series Layer 3 switch offers the opportunity to add what capability internally? -
A. A NIDS blade , which can then process all traffic passing through the switch fabric. -
B. A VPN accelerator card, to allow IPSec VPN termination. -
C. Both of these are correct. -
D. Neither of these is correct. |
| Question 4 | Unicast Reverse Path Forwarding provides what kind of filter? |
| Question 5 | To configure a PIX for IPSec using Group 2, MD5, and preshared keys, which of these commands is unnecessary? -
A. isakmp policy 13 authentication pre-share -
B. isakmp policy 13 hash md5 -
C. isakmp policy 13 group 2 -
D. None of these is correct. |
| Question 6 | Which of these is not a part of the security wheel? -
A. Secure -
B. Mitigate -
C. Test -
D. Improve -
E. Monitor |
| Question 7 | Port redirection occurs when -
A. Malware sends traffic from one host's port to another's (such as port 80 on host A to port 80 on host B). -
B. Malware sends traffic from one port to another on the same host (such as from port 80 on host A to port 23 on host A). -
C. Malware is ported from one OS (such as Unix) to another (such as Windows). -
D. None of these is correct. |
| Question 8 | NTP references a true clock (such as an atomic clock). What is this called? -
A. Primary clock -
B. First-level clock -
C. Stratum 1 -
D. Stratum 0 |
| Question 9 | When a VPN hardware client is terminating a site-to-site tunnel at a branch, what other services can it provide to the hosts at the branch? (Choose two.) -
A. Stateful firewall -
B. DHCP server -
C. DNS server -
D. NAT (PAT) -
E. WINS server |
| Question 10 | The Cisco Security Agent should be placed on which devices? -
A. Mission-critical hosts -
B. Mission-critical routers -
C. Mission-critical switches -
D. Mission-critical firewalls |
| Question 11 | What is a design alternative in the medium network's Corporate Internet module? (Choose two.) -
A. Add a HIDS monitor to the perimeter router -
B. Add a content-inspection device -
C. Eliminate the perimeter router -
D. Eliminate the router between this module and the Campus module |
| Question 12 | The VPN concentrator can enable remote sites to do what that the router or PIX cannot enable them to do? -
A. Connect to each other in a hub-and-spoke configuration. -
B. Connect to the Internet using split tunneling. -
C. Connect to each other directly (bypassing the headend). -
D. All of these are correct. |
| Question 13 | Which of the following will mitigate port redirection in the small network Corporate Internet module? -
A. NIDS on the switch feeding the DMZ -
B. AAA required for server access -
C. Private VLANs in the DMZ -
D. HIDS on the DMZ servers |
| Question 14 | HIDS and access controls will mitigate what kind of attacks in the small network Campus module? |
| Question 15 | Internal IP spoofing in the medium network Campus module is best mitigated by which of these? -
A. Switched network architecture. -
B. IP protocol filtering. -
C. RFC 2827 filtering. -
D. Strong AAA controlling access. -
E. IP spoofing inside the campus is not a threat. |
| Question 16 | The firewall with VPN in the remote- user network performs which security functions? -
A. Stateful packet filtering. -
B. Basic Layer 7 filtering. -
C. Host DoS mitigation. -
D. Remote site authentication. -
E. Terminate tunnels. -
F. All of these are correct. -
G. None of these is correct. |
| Question 17 | A security policy is developed -
A. At the same time as the network security design. -
B. After the network security design. -
C. Before the network security design. -
D. Before the network security implementation begins but after it is designed. |
| Question 18 | Which of these is a SMR SAFE axiom ? -
A. Network segmentation is the best protection. -
B. Network egress is also an attack's probable ingress. -
C. Networks are targets. -
D. Networks are inherently insecure . |
| Question 19 | What function does a firewall appliance provide in the remote-user model that a router with a software firewall does not? -
A. Stateful packet filtering. -
B. Basic Layer 7 filtering. -
C. Host DoS mitigation. -
D. Remote site authentication. -
E. VPN tunnel termination. -
F. None of these is correct. |
| Question 20 | A design alternative in the small network Campus module is -
A. Adding a small router or firewall between the network-management stations and the rest of the network. -
B. Replacing the Layer 2 switch with a Layer 3 switch to distribute internal traffic. -
C. Both of these are correct. -
D. None of these is correct. |
| Question 21 | When the VPN concentrator pushes an update to a client, how does the software client handle it differently from the hardware client? (Choose two.) -
A. The software client receives an update notice and an address from which an administrator can download the new software version to install. -
B. The hardware client receives an update notice and an address from which an administrator can download the new software version to install. -
C. The software client receives an automatic update via TFTP, after which the host reboots. -
D. The hardware client receives an automatic update via TFTP, after which it reboots. |
| Question 22 | Port redirection can be mitigated in the small network Campus module via |
| Question 23 | In Figure 15.1, to configure the PIX for NAT, which of these commands are used? (Choose two.) -
A. nat (inside) 1 172.20.32.0 255.255.255.0 -
B. nat (inside) 3 172.20.32.0 255.255.255.0 -
C. global (outside) 1 192.168.47.3 -
D. global (outside) 2 192.168.47.3 Figure 15.1. Router-to-PIX tunnel with NAT on each end. 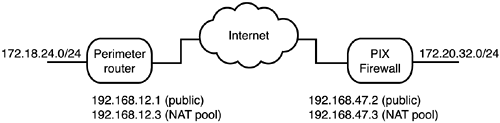 |
| Question 24 | Which of these commands would correctly allow all IP traffic from the PIX's inside network in Figure 15.2 to be encrypted for transit to the other network? -
A. access-list exam permit ipx 172.20.32.0 255.255.255.0 172.18.24.0 255.255.255.0 -
B. access-list exam permit ip 172.20.32.0 255.255.255.0 172.18.24.0 255.255.255.0 -
C. access-list exam permit ip 172.20.32.0/24 172.18.24.0/24 -
D. access-list exam permit tcp 172.20.32.0 255.255.255.0 172.18.24.0 255.255.255.0 Figure 15.2. Router-to-PIX tunnel with NAT on each end. 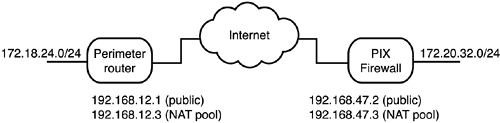 |
| Question 25 | A design alternative in the medium network's Campus module is -
A. Eliminate the building switches, connecting all hosts directly to the core switch. -
B. Replace the NIDS appliance with a NIDS blade on the core switch. -
C. Replace the core switch with a Layer 2 switch and perform Layer 3 operations on a router. -
D. All of these are correct. |
| Question 26 | The VPN concentrator offers what additional means of key creation compared to a PIX or a router? (Choose two.) -
A. DH Group 3 -
B. DH Group 5 -
C. DH Group 7 -
D. DH Group 9 |
| Question 27 | HIDS protects against which of these attacks in the medium network Corporate Internet module? |
| Question 28 | To encrypt and authenticate packets on the router or the PIX, you must specify in the IPSec configuration: (Choose two.) -
A. DES or 3DES as the encryption algorithm. -
B. 3DES only as the encryption algorithm. -
C. SHA-1 or MD5 as the HMAC. -
D. SHA-1 only as the HMAC. -
E. DH Group 2. -
F. You must use AH as well as ESP. |
| Question 29 | Man-in-the-middle attacks are mitigated through which of these? |
| Question 30 | The software VPN client in the remote-user network performs which security functions? -
A. Host DoS mitigation. -
B. Tunnel termination and remote site authentication. -
C. Stateful and basic Layer 7 filtering. -
D. All of these are correct. -
E. None of these is correct. |
| Question 31 | Internal threats have what advantages over external threats? (Choose two.) -
A. They are more numerous . -
B. They have fewer inhibitions. -
C. They operate from trusted accounts. -
D. They already possess some knowledge of the network. -
E. They have no particular advantages over external threats. |
| Question 32 | If SNMP must be used, it is preferable to use a _____ community. |
| Question 33 | Which of these is a design objective or fundamental of the SAFE SMR Blueprint? -
A. Security implementation performed to secure the edge first and then the core. -
B. Network and security management use the same resources, in parallel. -
C. A security breach in one module should never be allowed to penetrate another module. -
D. Security implementation through the infrastructure. |
| Question 34 | The Cisco 3000-series VPN concentrator supports what range of maximum simultaneous users? |
| Question 35 | Which of these is a SMR SAFE axiom? -
A. Secure management and reporting -
B. Secure accounting -
C. Secure device access for all critical devices -
D. Secure ingress and egress |
| Question 36 | What are the recommended responses for IDS devices? (Choose two.) -
A. NIDSalarm, drop, and reset -
B. HIDSalarm, drop, and ( optionally ) reset -
C. NIDSalarm -
D. HIDSalarm |
| Question 37 | What is a difference between the medium network as a branch and the medium network as a headend? (Choose two.) -
A. If a WAN link is used, the Corporate Internet module shrinks to only a VPN terminus. -
B. If a WAN link is used, all management traffic can flow over that. -
C. If IPSec tunneling is used, almost all management traffic can flow over it. -
D. If IPSec tunneling is used, all management traffic can flow over it. |
| Question 38 | A switched infrastructure is the best protection in the medium network Corporate Internet module against |
| Question 39 | Which of these is a design objective or fundamental of the SAFE SMR Blueprint? -
A. Management of system devices must be closely controlled. -
B. Secure management and reporting. -
C. Security Policy depends on risk tolerance. -
D. Attack mitigation is preferable at the edge rather than in the core. |
| Question 40 | Denial-of-service (DoS) attacks can be mitigated in the medium network Corporate Internet module via -
A. Switched network architecture. -
B. NIDS. -
C. CAR at the ISP's edge router and TCP setup controls at network ingress. -
D. Strong AAA controlling access. |
| Question 41 | Private VLANs in the medium network Corporate Internet module mitigate what threat? |
| Question 42 | Unauthorized access in the medium network Campus module is best mitigated by which of these? (Choose two.) |
| Question 43 | What is the default IPSec SA lifetime on the router? -
A. 3,600 seconds (1 hour ) -
B. 14,400 seconds (4 hours) -
C. 28,800 seconds (8 hours) -
D. 43,200 seconds (12 hours) -
E. 86,400 seconds (24 hours) |
| Question 44 | Which of these is a SAFE axiom? -
A. Routers are targets. -
B. Routers may be compromised. -
C. Routers must be locked down. -
D. Routers are a hacker's first target. |
| Question 45 | Information assets do not include which of these? (Choose two.) |
| Question 46 | Which of the following is not a threat to a network? |
| Question 47 | What is one difference between the small network as a branch and the small network as a standalone network? -
A. Absence of servers (all servers are at the main location) -
B. Fixed IP addresses from gaps in the headend's pool -
C. Absence of a WAN module -
D. Absence of management servers |
| Question 48 | Which of these is a valid IPSec command on the PIX? -
A. ipsec crypto transform-set exam esp-des esp-md5-hmac -
B. crypto ipsec transform-set exam esp-sha1 esp-md5-hmac -
C. crypto ipsec transform-set exam esp-des esp-md5-hmac -
D. crypto ipsec map 113 transform-set exam esp-des esp-md5-hmac |
| Question 49 | Unicast RPF filters traffic against what criteria? (Choose two.) -
A. Ingress port -
B. Egress port -
C. Routing table -
D. ARP cache |
| Question 50 | Network reconnaissance in the remote-user network is mitigated by which of these? |
| Question 51 | What is a difference between the medium network as a branch and the medium network as a headend? (Choose two.) -
A. If IPSec is used, the extra expense must be justified in the name of security. -
B. If IPSec is used, arrangements must be made for extra tunneling to support any traffic other than IP unicast. -
C. If IPSec is used, split tunneling can save on uplink bandwidth by allowing local Internet access. -
D. If IPSec is used, bandwidth must increase to compensate for the additional overhead. |
| Question 52 | Which of these is not a threat type? -
A. DoS -
B. Data manipulation -
C. Spam -
D. Reconnaissance -
E. Unauthorized access |
| Question 53 | Which of these is an advantage of taking a modular approach to security? -
A. Implementation can be done in stages. -
B. Smaller projects are easier to sell to management. -
C. Device configuration is typically simpler. -
D. Rolling back to a prior architecture is easier, if that becomes necessary. |
| Question 54 | Which of the following will mitigate unauthorized access in the small network Corporate Internet module? -
A. NIDS on the switch feeding the servers. -
B. HIDS on the DMZ servers. -
C. Filtering at network ingress. -
D. All of these are correct. |
| Question 55 | Which of the following will mitigate network reconnaissance in the small network Corporate Internet module? -
A. Protocol ingress filtering -
B. Antivirus on the DMZ servers -
C. NIDS on the server- facing switch -
D. Private VLANs |
| Question 56 | Private VLANs in the small network Campus module mitigate what kind of attack? |
| Question 57 | Port redirection in the medium network Campus module is mitigated by which of these? |
| Question 58 | Which two devices can be at the ingress to the small business Internet module? |
| Question 59 | Password attacks in the medium network Campus module are best mitigated by which of these? |
| Question 60 | Which of these is a design objective or fundamental of the SAFE SMR Blueprint? -
A. Security and attack mitigation based on policy. -
B. Policy must be based on the organization's mission. -
C. Policy without management endorsement is limited in its effect. -
D. The security policy must make reasonable accommodation for users. |