The Four Options
| The four options listed in the SMR Blueprint for this model are as follows :
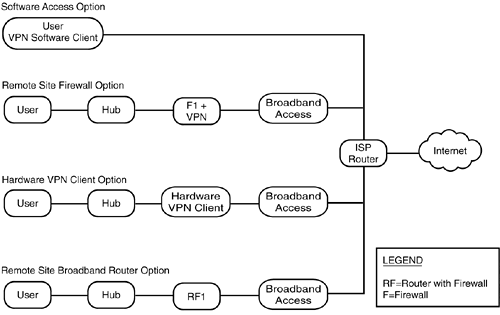
The options should look familiar because we discussed them briefly earlier. Here they are again, in Figure 12.1. Figure 12.1. The remote- user network options. The Software Access OptionThis is simultaneously the simplest option (topologically) and the most dangerous to the organization. There is no additional hardware between the user's host and the Internet access. This access can be dialup or broadband (while traveling, for instance). All safety precautions for the host must be present on the host. These include antivirus software, regular software (OS and application) maintenance, and a personal (software) firewall. The software firewall must perform all filtering (for IP spoofing and unauthorized access). The software VPN client authenticates the host to the headend and provides IPSec termination. After authentication and the pushdown of policy settings (such as access rights), the remote host can receive a virtual IP address from the headend's block and the addresses of DNS and WINS servers. In other words, it operates as though it were part of the LAN. The headend can enable or disable split tunneling during this configuration pushdown ; the SAFE SMR recommends disabling it. This makes sense when you consider the rather direct path from the Internet through the host to the corporate network when it is enabled (if the personal firewall settings were incorrect, for instance). The Remote Site Firewall OptionWith this option, the incoming broadband enters through its access device (often called a DSL or cable modem) and then immediately passes through a stateful firewall. From there, the data flow passes through a hub (or switch) to the actual host. This configuration is suitable for a teleworker or a small branch office with few hosts . Threat mitigation on the host need be only the (usual) antivirus software and maintenance of the OS and applications (patching). The bulk of the threat mitigation occurs in the stateful firewall, which provides both the filtering functions and IPSec tunnel termination. Address filtering should mitigate any attempted IP spoofing inbound to the remote user, and the protocol filtering limits any network reconnaissance. The two types of filtering together mitigate unauthorized access. If desired, split tunneling is more reasonable in this configuration because the stateful firewall segregates the connections that it passes. IP addresses used behind the firewalls at different remote sites should not overlap unless NAT is being used on their firewalls. The second principal function of the firewall, IPSec tunnel termination, provides secure, encrypted communications to the headend, mitigating man-in-the-middle attacks (and ordinary snooping).
Configuration of the tunnel provides access control and authorization into the corporate network for the users behind the firewall. The remote firewall and tunnel configuration parameters can be managed via a tunnel from the headend, again alleviating end users from needing to perform any configuration tasks (and making their authentication and authorization subject to better control from the headend). Note that the firewall provides device-level authentication to the headend but does not itself provide any user-level authentication. The Hardware VPN Client OptionThe third option looks much like the second, except that the firewall has been replaced by a hardware VPN client. Although this device is optimized for setting up and managing the VPN connection, it lacks some of the other (quite useful) features of a true firewall. It does not provide stateful connection management, so a personal firewall on the host (on every connecting host, if there is more than one) is needed along with the antivirus software (and software maintenance). Disabling split tunneling would somewhat alleviate the need for a personal firewall by forcing all Internet connectivity to travel via the tunnel. Unfortunately, using the tunnel does not prevent foolish downloads from being acquired and placed on the hosts; the software firewall is recommended even if split tunneling is disabled. Again, all connection management can be done from the headend, although the hardware client uses an SSL tunnel for this purpose (remember, its management is GUI-based, using a Web browser). Access and authorization are centrally controlled at the headend, but, as with the firewall option, the device is authenticated, not the user who happens to be accessing the headend. The Remote Site Broadband Router OptionThis option is very like the firewall option. The differences lie in the differing capabilities of a router versus a firewall. With a software firewall as a part of the router's software, stateful connection management is available, but you also gain the possibilities of the other router software features. This includes the capability to handle other protocols and QoS. The router also might be the broadband access device (these are sometimes sold or provided by ISPs that are differentiating their service). In this case, you will not likely be able to manage the router from your headend. In such a case, you will need some other termination device (including possibly the software client) for your tunnel. |
EAN: 2147483647
Pages: 177