Protocol Gateways
8.2 Protocol Gateways
You can direct HTTP traffic to gateways the same way you direct traffic to proxies. Most commonly, you explicitly configure browsers to use gateways, intercept traffic transparently , or configure gateways as surrogates (reverse proxies).
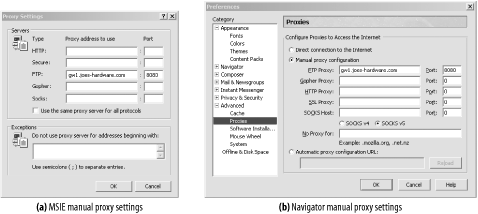
Figure 8-3 shows the dialog boxes used to configure a browser to use server-side FTP gateways. In the configuration shown, the browser is configured to use gw1.joes-hardware.com as an HTTP/FTP gateway for all FTP URLs. Instead of sending FTP commands to an FTP server, the browser will send HTTP commands to the HTTP/FTP gateway gw1.joes-hardware.com on port 8080.
Figure 8-3. Configuring an HTTP/FTP gateway
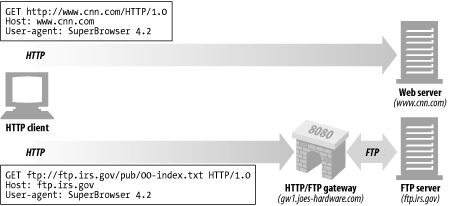
The result of this gateway configuration is shown in Figure 8-4 . Normal HTTP traffic is unaffected; it continues to flow directly to origin servers. But requests for FTP URLs are sent to the gateway gw1.joes-hardware.com within HTTP requests. The gateway performs the FTP transactions on the client's behalf and carries results back to the client by HTTP.
Figure 8-4. Browsers can configure particular protocols to use particular gateways
The following sections describe common kinds of gateways: server protocol converters, server-side security gateways, client-side security gateways, and application servers.
8.2.1 HTTP/*: Server-Side Web Gateways
Server-side web gateways convert client-side HTTP requests into a foreign protocol, as the requests travel inbound to the origin server (see Figure 8-5 ).
Figure 8-5. The HTTP/FTP gateway translates HTTP request into FTP requests
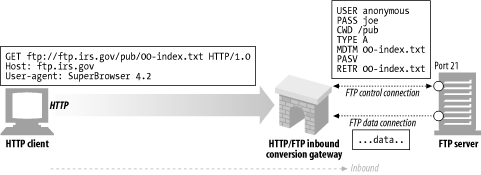
In Figure 8-5 , the gateway receives an HTTP request for an FTP resource:
ftp://ftp.irs.gov/pub/00-index.txt
The gateway proceeds to open an FTP connection to the FTP port on the origin server (port 21) and speak the FTP protocol to fetch the object. The gateway does the following:
Sends the USER and PASS commands to log in to the server
Issues the CWD command to change to the proper directory on the server
Sets the download type to ASCII
Fetches the document's last modification time with MDTM
Tells the server to expect a passive data retrieval request using PASV
Requests the object retrieval using RETR
Opens a data connection to the FTP server on a port returned on the control channel; as soon as the data channel is opened, the object content flows back to the gateway
When the retrieval is complete, the object will be sent to the client in an HTTP response.
8.2.2 HTTP/HTTPS: Server-Side Security Gateways
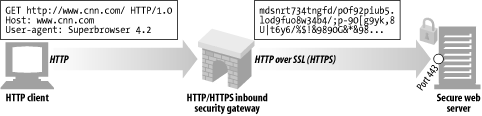
Gateways can be used to provide extra privacy and security for an organization, by encrypting all inbound web requests. Clients can browse the Web using normal HTTP, but the gateway will automatically encrypt the user's sessions ( Figure 8-6 ).
Figure 8-6. Inbound HTTP/HTTPS security gateway
8.2.3 HTTPS/HTTP: Client-Side Security Accelerator Gateways
Recently, HTTPS/HTTP gateways have become popular as security accelerators. These HTTPS/HTTP gateways sit in front of the web server, usually as an invisible intercepting gateway or a reverse proxy. They receive secure HTTPS traffic, decrypt the secure traffic, and make normal HTTP requests to the web server ( Figure 8-7 ).
Figure 8-7. HTTPS/HTTP security accelerator gateway
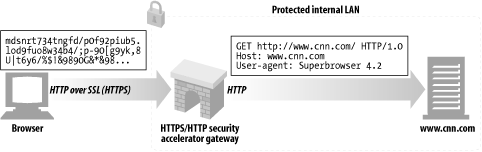
These gateways often include special decryption hardware to decrypt secure traffic much more efficiently than the origin server, removing load from the origin server. Because these gateways send unencrypted traffic between the gateway and origin server, you need to use caution to make sure the network between the gateway and origin server is secure.
EAN: 2147483647
Pages: 294