Log Files
|
|
Needless to say, consulting log files can help enormously when you're troubleshooting issues with your IIS server. The two main log files you'll be concerned with are the IIS log file (hopefully the W3C, or World Wide Web Consortium Extended version) and the Windows Event Viewer.
About W3C Logging
Since W3C logging has the most complete set of fields that are logged, it is the most useful log to consult when you're troubleshooting issues. If you are not using W3C Extended logging, you may want to switch your logging type temporarily while trying to track down issues, but only if you aren't using site logging data for something important. The W3C Extended log can provide some great information about your site.
Which Account Is a Client Using to Access the Site? If you are troubleshooting permissions issues, it's helpful to know which account the client is using to access the site. If you've set up Integrated Windows Authentication, the browser does not prompt the user for login information, so it is difficult to determine from the user which account they are using. Luckily, it's right there in the log file.
Which Browser Is a Client Using to Access the Site? Some browsers do not support certain features. For example, Integrated Windows Authentication is supported only on Internet Explorer browsers. If you have anonymous access turned off and the client has no other choice but to use Integrated Windows Authentication, only IE users will be able to access the site. Taking a look at the log files, you can see which browsers are being used to access the site.
Which HTTP Status Codes Are Being Transmitted? When IIS sends out an error message, it does not send a specific error message-rather, it sends a general error. This means that the client does not receive the substatus code. If the lockdown policy prevents a client from accessing the file, the client will receive a generic '404 not found' error, while the extended log file will contain the full 404.2 error message. In addition to this, since the stats codes are on the same line as the time/date, user, Internet Protocol (IP), browser, and so on, it is much easier to tie a specific error message to a specific client.
The basic list of HTTP status codes is defined by RFC 2616. These codes are extensible, so different vendors can add to this list. Microsoft has added the substatus codes in its implementation. Table 20-1 lists both sets combined and the basic meaning of each code.
| Code | Meaning |
|---|---|
| 100 | Continue |
| 101 | Switching protocols |
| 200 | OK |
| 201 | Created |
| 202 | Accepted |
| 203 | Non-authoritative information |
| 204 | No content |
| 205 | Reset content |
| 206 | Partial content |
| 300 | Multiple choices |
| 301 | Moved permanently |
| 302 | Found |
| 303 | See other |
| 304 | Not modified |
| 305 | Use proxy |
| 307 | Temporary redirect |
| 400 | Bad request |
| 401 | Unauthorized |
| 401.1 | Unauthorized: Access is denied due to invalid credentials. |
| 401.2 | Unauthorized: Access is denied due to server configuration favoring an alternative authentication method. |
| 401.3 | Unauthorized: Access is denied due to an Access Control List (ACL) set on the requested resource. |
| 401.4 | Unauthorized: Authorization failed by a filter installed on the web server. |
| 401.5 | Unauthorized: Authorization failed by an Internet Server Application Programming Interface/Common Gateway Interface (ISAPI/CGI) application. |
| 401.7 | Unauthorized: Access denied by URL authorization policy on the web server. |
| 402 | Payment required |
| 403 | Forbidden |
| 403.1 | Forbidden: Execute access is denied. |
| 403.2 | Forbidden: Read access is denied. |
| 403.3 | Forbidden: Write access is denied. |
| 403.4 | Forbidden: Secure Sockets Layer (SSL) is required to view this resource. |
| 403.5 | Forbidden: SSL 128 is required to view this resource. |
| 403.6 | Forbidden: IP address of the client has been rejected. |
| 403.7 | Forbidden: SSL client certificate is required. |
| 403.8 | Forbidden: Domain Name System (DNS) name of the client is rejected. |
| 403.9 | Forbidden: Too many clients are trying to connect to the web server. |
| 403.10 | Forbidden: Web server is configured to deny Execute access. |
| 403.11 | Forbidden: Password has been changed. |
| 403.12 | Forbidden: Client certificate is denied access by the server certificate mapper. |
| 403.13 | Forbidden: Client certificate has been revoked on the web server. |
| 403.14 | Forbidden: Directory listing is denied on the web server. |
| 403.15 | Forbidden: Client access licenses have exceeded limits on the web server. |
| 403.16 | Forbidden: Client certificate is ill-formed or is not trusted by the web server. |
| 403.17 | Forbidden: Client certificate has expired or is not yet valid. |
| 403.18 | Forbidden: Cannot execute requested URL in the current application pool. |
| 403.19 | Forbidden: Cannot execute CGIs for the client in this application pool. |
| 403.20 | Forbidden: Passport logon failed. |
| 404 | Not Found |
| 404.1 | File or directory not found: Web site not accessible on the requested port. |
| 404.2 | File or directory not found: Lockdown policy prevents this request. |
| 404.3 | File or directory not found: Multipurpose Internet Mail Extensions (MIME) map policy prevents this request. |
| 405 | Method not allowed |
| 406 | Not acceptable |
| 407 | Proxy authentication required |
| 408 | Request timeout |
| 409 | Conflict |
| 410 | Gone |
| 411 | Length required |
| 412 | Precondition failed |
| 413 | Request entity too large |
| 414 | Request Uniform Resource Identifier (URI) too large |
| 415 | Unsupported media type |
| 416 | Requested range not satisfiable |
| 417 | Expectation failed |
| 500 | Internal server error |
| 500.11 | Server error: Application is shutting down on the web server. |
| 500.12 | Server error: Application is busy restarting on the web server. |
| 500.13 | Server error: Web server is too busy. |
| 500.14 | Server error: Invalid application configuration on the server. |
| 500.15 | Server error: Direct requests for GLOBAL.ASA are not allowed. |
| 500.16 | Server error: Universal Naming Convention (UNC) authorization credentials incorrect. |
| 500.17 | Server error: URL authorization store cannot be found. |
| 500.18 | Server error: URL authorization store cannot be opened. |
| 500.19 | Server error: Data for this file is configured improperly in the metabase. |
| 500.20 | Server error: URL authorization scope cannot be found. |
| 500.100 | Internal server error: ASP error. |
| 501 | Not implemented |
| 502 | Bad gateway |
| 503 | Service unavailable |
| 504 | Gateway timeout |
| 505 | HTTP version not supported |
The Windows Event Viewer
The Windows Event Viewer can also log events that pertain to IIS. The Event Viewer has three-or four, if DNS is installed-components:
-
The Application log Contains information about the applications that are running on the server. Most Component Object Model (COM) objects will send informational and error messages to the Application log.
-
The Security log Contains all the auditing information that the server collects. We'll set that up in a moment.
-
The System log Contains information about the operating system itself. Services also send information to the System log.
-
The DNS server log Present only if the Microsoft DNS server component is installed, and contains events pertaining to the DNS server.
Note Applications can add their own logs as well. The list of logs you have may vary, depending on any other applications you may have installed. For example, the DNS server log only appears if the DNS server component is installed.
Some of the Event Viewer messages you will see include the following:
-
Service start and stop
-
Application errors
-
COM object activity
-
Service errors
-
Application Pool errors
-
News feed information
You can also set up auditing and view the information in the Security log. You can set up auditing in a security policy and Group Policy Objects. Here's how to set up auditing in the Local Security Policy for an individual server.
-
Open Start | Administrative Tools | Local Security Policy.
-
In the Local Security Settings window shown in Figure 20-1, select Local Policies, and then select Audit Policy.
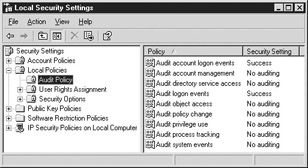
Figure 20-1: Audit Policy in the Local Security Settings window -
To enable auditing for an item, double-click the item in the right pane.
-
Choose to audit Success, Failure, or both.
-
Click OK.
|
|
EAN: 2147483647
Pages: 193