Securing Your Enterprise with CORBA
As you know, CORBA is a product of the Object Management Group (OMG) used to create, delete, store, and access distributed objects and to allow them to interact with each other. CORBA provides a set of services that makes it easy for objects to be transactional, lockable , secure, and persistent. CORBA solutions are very flexible because CORBA provides a protocol independent of language and platform implementation. Review of CORBAThe Object Request Broker (ORB) is the CORBA object bus that manages the communication between components in the system and even components on other systems. It provides a set of bus- related services such as the following:
The ORB interface is an abstract interface for an ORB to abstract applications from implementation details. This interface provides helper functions such as converting object references to strings. Figure 28-1 shows a generic ORB architecture. The client uses the IDL stub and the implementation (typically known as the servant) uses an IDL skeleton. Both the client and the servant share the ORB interface. 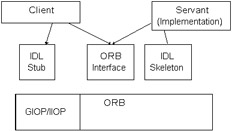 Figure 28-1: Generic ORB architecture When you write a CORBA application, you define a remote interface that describes the interaction between a server and its clients . You use the Interface Definition Language (IDL) to define the object's interfaces to any potential client. This CORBA IDL does not provide implementation details; the methods can be written in any language that provides CORBA bindings such as Java and C++. The interface between the client and its ORB is implemented in a stub, and the interface between a server object and its ORB is the skeleton . This is similar to the concept of stubs and skeletons in RMI. However, in CORBA, the communication is performed by the ORB and not by the stub components themselves . The servant is the implementation of the operations defined in the IDL skeleton. The implementation is built using a language that that provides CORBA bindings such as Java or C++. For remote invocation requests , CORBA provides a common protocol called Internet Inter-ORB Protocol (IIOP). IIOP is the standard General Inter-ORB Protocol (GIOP) with TCP/IP specified as the transport protocol. GIOP is the CORBA standard that defines the messages for inter-ORB communication. CORBA defines a set of services; you may want to take a look at the OMG site ( www.omg.org ) for more information. Table 28-1 describes some of these services.
In addition, OMG has defined an IIOP implementation called Secure Inter-ORB Protocol (SECIOP). SECIOP provides secure connections between CORBA clients and servers, but it is very complex and many vendors provide SSL implementations as an alternative. In addition, you can tunnel IIOP through an HTTPS connection. Overview of CORBA securityThe CORBA Security Service specification includes authentication, authorization and access control, secure communication, auditing, and non- repudiation . It does not include a specification for cryptography services; however, it does mention that the ORB implementation must be able to use local security policies. OMG has defined an overall security framework with different levels and structured into several feature packages (again you can find more information in the Security Specification at the www.omg.org site). Table 28-2 briefly describes these packages, based on the Security Services specification. Authentication and authorization are not specific to CORBA. You can use different methods with CORBA security for authentication and authorization, and you choose which one to use based on your application needs. Message integrity , assuring that your message is not tampered, and message encryption , for confidentiality, are also supported by CORBA but are not specific to it. CORBA security supports many different types of encryption and addresses all the important ones such as GSS, Kerberos, and SSL. These are explained in Table 28-1. Non-repudiation , which provides functionality so that neither the sender nor the recipient can deny sending or receiving the message, is provided in an optional package. CORBA security also provides three different levels of privilege delegation. Privilege delegation refers to the ability to delegate the initiating principal identity beyond the invoked object. As discussed in Table 28-2, these levels are identity-based policies without delegation, identity-based policies with unrestricted delegation, and identity- and privilege-based policies with controlled delegation.
CORBA principalsA principal is an entity that is registered and authenticated to the system. The most common form of authentication is the username and password combination, for humans , or long- term keys associated with the object, for systems. A principal may be associated with different identities for different purposes, such as initiating a message or resource access. In addition, a principal has privilege attributes and the principal may use some or all the attributes at any given session. Some examples of these attributes include the principal's access identity, roles granted to the principal, and the groups the principal belongs to. The attributes can be obtained by delegation from other principals, may be available through authentication, or may be public (that is available to anyone ). These attributes are based on access policies. There are two access policy types. First is the object invocation policy that establishes if the client (based on the current principal) can access the requested operation. The ORB and the security services it uses (for all applications) typically enforce the object invocation policy. The other access policy is the application object access , which is enforced within the client and the target object. The ORB is still required to validate the request parameters and ensure delivery. The object invocations are restricted by security rules, which are based on security policies. These policies include defining whether the client can access the object and perform the operation. Also based on security policies, a client and target object may establish a secure association. Security mechanisms use cryptography to establish the secure association and to protect the data between client and target. Security mechanisms, however, differ in the type of cryptography used. For instance, there are three types of key distribution: secret, public, and hybrid. Keys are assigned to clients, targets, and trusted authorities. The secret key distribution is used for the distribution of keys for principals and for message protection. Public key distribution is used for principal key distribution and may use secret key distribution for message protection. Finally, hybrid key distribution uses secret key technology for principal key distribution within an administration domain, and public key distribution for trusted authorities and between domains. The secure association is affected by underlying security mechanisms such as mutual authentication requirements.
Java Security Solutions ISBN: 0764549286
EAN: 2147483647 Year: 2001
Pages: 222 Authors: Rich Helton, Johennie Helton
flylib.com © 2008-2017. If you may any questions please contact us: flylib@qtcs.net |