De-Militarized Zones (DMZs)
The De-Militarized Zone is a concept that comes from war; the concept of a no man's land, meaning that at some point a person must be viewed as an ally or an enemy when they cross a certain boundary. In a firewall boundary, it is a combination of firewalls in which an internal firewall filters the Bastion Host firewall. Figure 21-14 shows the concept of a DMZ. 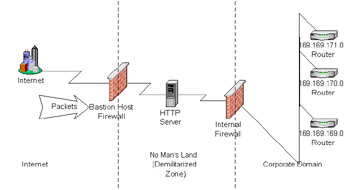 Figure 21-14: DMZ The purpose of the DMZ is to separate the services that communicate to the Internet on a server, or set of servers such as a Web farm, from all the other machines. The HTTP server can communicate to databases or enterprise systems through a secondary firewall. The internal firewall will only accept packets from the organization's designated HTTP server and usually in the form of HTTP; however, it will send and receive on designated ports that are not HTTP. The Bastion Host will only allow packets for the HTTP protocol into the HTTP server. All other packages will be blocked; this scheme keeps all packets narrowed into one protocol and coming from one machine, or a set of machines. In this case, the HTTP server acts as a dual- homed host. A dual-homed host acts as a router between the Internet and the organization's domain. The packets on the Internet can communicate with the server, and the packets on the organization's domain can communicate with the server, however neither can communicate directly. The Bastion Host, in this case, is there to ensure that no packets from the Internet can communicate to any other host except the dual-homed host. In addition, the internal firewall is there to ensure that communication from the organization's domain can only communicate with a separate port specified from the dual-homed host. Even if a hacker does IP spoofing, the response from the organization's domain will only be routed to the dual-homed host. The attacker would have to intercede for the router and route the packets to a different machine to try to bypass the dual-homed host. Another tactic to further confuse possible attackers is to build a fake dual-homed host as a secondary firewall. This host could be further separated by firewalls and given less security so that an attacker would spend his time trying to attack a machine with nothing proprietary on it. This approach is sometimes referred to as the "sacrificial lamb approach" because a machine is sacrificed for the purpose of saving the domain. In this approach, logging is heavily guarded to study the attacker's techniques to be ready for when he moves his attack to the rest of the domain. Proxies can also be used to hide the true identity of the dual-homed host. A proxy gives a host the capability to look like another host and process its request without the user discovering the difference. The proxy can create further security and examine the request; if it appears questionable, the proxy can disregard it. If the request appears valid, the proxy forwards it to the real host and responds to the sender as the actual host. A package called SOCKS is used to help in such deception. SOCKS is an API that helps support proxy-aware servers and clients . SOCKS is considered a circuit-level gateway to allow selected TCP/IP connections through firewalls.
Java Security Solutions ISBN: 0764549286
EAN: 2147483647 Year: 2001
Pages: 222 Authors: Rich Helton, Johennie Helton
flylib.com © 2008-2017. If you may any questions please contact us: flylib@qtcs.net |