Connecting Your Database through the Connector Architecture
The J2EE Connector API provides a generic framework to map data from Enterprise Application Integration (EAI) systems and EIS systems. A good site for information is the J2EE Connector architecture discussion in the java.sun.com/j2ee/connector/ site, on which some of this discussion is based. Some of the benefits of the Connector API include connection management , security management , and transaction management . The J2EE Connector architecture defines the following three system-level contracts (between an application server and EIS):
The J2EE Connector architecture defines a Common Client Interface (CCI) for EIS access that defines a standard client API for application components. The purpose of the CCI is to provide a generic Connector implementation independent of the application server. This connection is not aware of the security management, the transaction management, or the connection management. Figure 20-2 shows where the CCI is used. 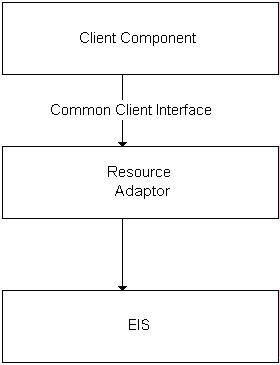 Figure 20-2: The Common Client Interface
In the example code of Listing 20-3, I used the JDBC javax.sql.DataSource and java.sql.Connection interfaces for database connections. The connection and connection factory are defined for the CCI with the interfaces javax.resources.cci.ConnectionFactory and javax.resources.cci.Connection . The ConnectionFactory creates (or finds in a pool) a ManagedConnection that has an associated transaction.
The authentication is specified in the <authentication-mechanism-type> tag of resource adapter's deployment descriptor, which allows the resource adapter to get the information about the credential. As with JDBC, the security context is propagated and principals are passed through the subject during the getConnection .
As noted earlier, the communications between the EIS and the application server are subject to attacks. These threats include data modification and man-in-the-middle attacks. Therefore, securing the communication is important and can be done with SSL, and some EISs can support the GSS-API. The GSS-API is the Generic Security Services Application Programming Interface . The application server uses the createManagedConnection when it requests a resource adapter to create a new connection. It can pass in the subject by using either the application-managed sign-on (the application component passes the subject to the resource) or container-managed sign-on (application server fills in the subject ). A subject represents a grouping of related information for a single entity. This information includes the subject's identity, passwords, and cryptographic keys. A subject may have multiple identities, which are the principals within the subject. A subject may have credentials that are the security- related attributes; the sensitive credentials are stored within a credential set. Credential sets can be public (intended to be shared) or private. For sign-on:
Java Security Solutions ISBN: 0764549286
EAN: 2147483647 Year: 2001
Pages: 222 Authors: Rich Helton, Johennie Helton
flylib.com © 2008-2017. If you may any questions please contact us: flylib@qtcs.net |