Connecting Your Database through JDBC
JDBC drivers enable clients to perform database connections, database queries, stored procedures, and other operations. JDBC drivers implement the JDBC API that allows for the interaction to the database server. Sun has divided the JDBC drivers into four types: 1, 2, 3, and 4. Types 1 (JDBC-ODBC bridge) and 2 (JDBC-Native API) use additional software, such as a C dynamic link library, that needs to be installed on the client. Types 3 (100% Java JDBC-Network) and 4 (100% Java) are Java implementations that do not require additional software installations. Figure 20-1 shows the difference among the different types of JDBC drivers. 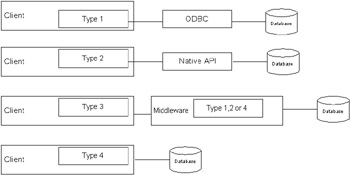 Figure 20-1: Different JDBC driver types Getting a connection to a database resource (and for that matter, any resource) is called a resource sign-on . The user requests a connection, which is established based on that user's security context . As you may recall, the security context has information such as the user's authorization level and access rights. The application provider can choose to let the container manage the database sign-on or may choose to manage it at the application code. Regardless of which you choose, the following three steps are performed:
Using the container-managed sign-on allows principals to be mapped across security domains and adds flexibility to the process. The deployer sets up the resource sign-on and user authorization and authentication information required for database access. Listing 20-1 shows the steps to follow, and Listing 20-2 shows the deployment descriptor for container-managed sign-on. Listing 20-1: Container-managed sign-on
// Step 1. Obtain a JNDI context. Context ctx = new InitialContext(); // Step 2. Obtain a connection factory using a JNDI lookup. javax.sql.DataSource ds = (javax.sql.DataSource) ctx.lookup( theDatabaseJNDIname); // Step 3. Obtain a connection through the factory. // Note: The deployer gives the security information so you // do not need to pass it in. java.sql.Connection dbcx = ds.getConnection();
Listing 20-2: Deployment descriptor for container-managed sign-on
<resource-ref> <description>description</description> <res-ref-name>jdbc/MyDatabase</res-ref-name> <res-type>javax.sql.DataSource</res-type> <res-auth>Container</res-auth> </resource-ref>
Using the application-managed sign-on means that you must implement the resource sign-on at the code level. The difference is in step 3: You pass in the security information at the connection request method of the javax.sql.DataSource . Listing 20-3 shows an example for application-managed sign-on. Listing 20-3: Application-managed sign-on
// Step 1. Obtain a JNDI context. Context ctx = new InitialContext(); // Step 2. Obtain a connection factory using a JNDI lookup. javax.sql.DataSource ds = (javax.sql.DataSource)ctx.lookup( theDatabaseJNDIname); // Step 3. Obtain a connection through the factory. // Note: You need to pass in the the security info java.sql.Connection dbcx = ds.getConnection(userName,userPsswrd);
In addition, you can control access to the application components declaratively or programmatically. When you use declarative access, you describe in a deployment descriptor the rights a user must have to access the methods or system data. You can use security roles to define the access of a user. When you programmatically control access, you check in your code whether the user has the proper rights to access the components. For instance, if you use EJBs, you can use getCallerPrincipal and isCallerInRole to get the caller's security context.
The management of JDBC is typically performed by the Driver class. For security reasons, the JDBC management layer keeps track of the class loader provided by the driver. The DriverManager class keeps a list of Driver classes that have registered (by calling the Driver.Manager.registerDriver ). A Driver class may do so by:
When the DriverManager class opens a connection, it uses only those drivers that come from the local file system or the same class loader as the code issuing the request for the connection.
Java Security Solutions ISBN: 0764549286
EAN: 2147483647 Year: 2001
Pages: 222 Authors: Rich Helton, Johennie Helton
flylib.com © 2008-2017. If you may any questions please contact us: flylib@qtcs.net |