82.
(Publisher: Wordware Publishing, Inc.)
Author(s): Gil Held
ISBN: 1556225989
Publication Date: 10/01/98
| Previous | Table of Contents | Next |
Chapter 8
Public Key Encryption
In this concluding chapter, I turn your attention to a relatively new field of encryption when examined against the evolution of encryption techniques dating to before Caesar’s time. That field of encryption is referred to as public key encryption, the focus of this chapter.
Unlike the previous coverage of encryption techniques which included a minimal amount of mathematics, any discussion of public key encryption requires an understanding of a considerable number of mathematical operations. Those operations are crucial to understand how public key encryption works. A second difference between this chapter and previous chapters presented in this book concerns the development of programs which will be conspicuous by their omission in this chapter. The reason for this omission is based upon current United States government restrictions on the export of certain types of encryption software. Because neither I nor my publisher can police the sale of this book nor its distribution, it is safer to simply present concepts in this chapter and leave it to you to develop public key software programs if you so desire.
General Operation
Figure 8.1 illustrates the general operation of a public key-based encryption system. In this example, an encryption algorithm (E) is used with a public encryption key (ke) to encipher input (x), producing ciphertext (Eke(x)). Decryption employs a decryption algorithm (D) which operates upon a secret decryption key (kd) such that D(Eke(x)) restores the encrypted input to its original form. Note that the algorithms E and D are public; however, the decryption key (kd) must be kept secret. When public key-based secure communications occur in the opposite direction, another key pair must be created, with the recipient becoming the originator and using an encryption key, while the originator becomes the recipient and uses a secret decryption key. Thus, communication in each direction requires the use of a public-private key pair.

Figure 8.1 Public key encryption.
Authentication Issues
Because the public encryption key is published, anyone can use it to encrypt a message. This means that it becomes possible for a person to use a public key to send a false message which, when deciphered, could appear as a legitimate message. This problem is not normally applicable to conventional private key systems since the distribution of private keys are on a controlled basis. This also means that a public key system normally requires a method of authentication, typically accomplished by the use of a digital signature. However, it is also possible for two persons using a public key system to authenticate one another by placing a random string into their message and requesting the party they are communicating with to return the string in their initial reply. Because the recipient is the only person who can decipher the message, when they encrypt the message in another public key associated with the originator’s private key, the originator can check the message to ensure it was correctly received. Then, this receipt indicates that the recipient is the party they claim to be. Figure 8.2 illustrates how two parties can authenticate one another via the use of a public key system.
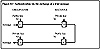
Figure 8.2 Authentication via the exchange of a trial message.
Public vs. Private Key Encryption
In a classic private key cryptosystem, both the sender and receiver of a message must know and use the same secret key. This means both parties must have access to the same key, and if either party should lose or divulge the key, both parties are compromised. Although the use of secret key cryptography dates to before the time of Caesar and is still frequently used in electronic commerce and other business applications, it has several weaknesses in addition to the disclosure of the key compromising messages sent between parties. First, the management of keys can become a daunting task, especially when you have many persons or locations that must communicate with one another and wish to minimize the potential compromise of a key on messages by assigning different keys to each pair of persons or locations that requires secure communications. A second problem associated with secret keys is their distribution. Some organizations initially distribute keys via registered mail, which considerably reduces your ability to promptly respond to changing user requirements. Similarly, if a key should become compromised, the ability to distribute a new key will be dependent upon a telephone call, a courier, or an Express Mail letter, all subject to a security breach.
The Work of Diffie and HellmanIn 1976 the concept of public cryptography was introduced by Whitfield Diffie and Martin Hellman as a mechanism to solve the key management and key distribution problems associated with private key cryptography. In their now- classic paper, they discussed the features of a public key system and noted that such a system should have the following four properties for a given message (M) based upon encryption (E) and decryption (D) procedures:
- 1. D(E(M)) = M
- 2. Both E and D are easy to compute.
- 3. It is computationally unfeasible to derive D from E.
- 4. E(D(M)) = M
The first property simply states that once a message is encrypted the application of a decryption procedure will restore it, in effect the same as the property for a private key system. The second property means that for the cryptosystem to be practical, both encryption and decryption should be computationally fast, which also holds for private key cryptology. It is the third property which signifies the key difference between public and private key cryptology, as this property means that encryption is a one-way function and it is not feasible to invert E unless you already know D. This also means that the encryption procedure E can be made public, and only the person who knows D can decrypt the message.
The fourth property indicates that the mapping is one-to-one, meaning that the application of the decryption procedure to a message (M) can be used to verify the person who sent the message, in effect permitting a digital signature.
Under the Diffie-Hellman concept, each person who requires secure communications obtains a pair of keys. One key is referred to as the public key and can be distributed to any person who requires the ability to communicate securely with the person who holds the secret key. The key, no pun intended, to public key encryption is the fact that no third party can determine the composition of the private key from the public key.
It is important to note that the paper presented by Diffie and Hellman provided a concept or framework for the development of public key encryption techniques. However, Diffie-Hellman does not actually represent a public key encryption technique. Although not an actual technique, the work of Diffie and Hellman considerably influenced the development of public key encryption techniques and represents a significant milestone in the field of encryption.
| Previous | Table of Contents | Next |
EAN: 2147483647
Pages: 92