Physical Security
| When planning security for network scenarios, many organizations overlook physical security. In many smaller organizations, the servers, routers, and patch panels are placed as a matter of convenience due to space restrictions. This can cause security issues. Speaking from experience, this equipment ends up in the oddest places, such as in the coat closet by the receptionist 's desk in the lobby, in the room with the copy machine, or in a storage room with a backdoor exit that's unlocked most of the time. Securing physical access and ensuring that access requires proper authentication is necessary to avoid accidental exposure of sensitive data to attackers performing physical profiling of a target organization. When planning physical security, you must take into consideration events such as natural and man-made disasters. If you have space constraints and put the servers in a room with the hot-water heater, how will you deal with the consequences when the hot-water heater springs a leak? How soon will your network be back up and running? If your building is in a flood zone and the most important equipment is in the lowest spot in the building, you need to be prepared when heavy rains come. Man-made disasters can be as simple as a clumsy technician spilling his soda into the most important piece of equipment you have. Many times these types of scenarios are overlooked until it is too late.
Physical access to a system creates many avenues for a breach in security, for several reasons. Many tools may be used to extract password and account information that can then be used to access secured network resources. Given the ability to reboot a system and load software from a floppy disk, attackers may be able to access data or implant Trojan horses and other applications intended to weaken or compromise network security. Unsecured equipment is also vulnerable to social engineering attacks. It is much easier for an attacker to walk into a reception area, say she is here to do some work on the server, and get access to that server in the closet in the front lobby than to get into a physically secured area with a guest sign-in and sign-out sheet. As shown earlier, weak physical controls can also amplify the effects of natural and man-made disasters. In this next section, we cover physical access control, including barriers, facilities, and environments, as well as the different types of social engineering and how to educate your users concerning them. Access ControlPhysical security controls parallel the data controls we discussed in Chapter 2, "General Security Practices." Mandatory physical access controls are commonly found in government facilities and military installations where users are closely monitored and very restricted. Users cannot modify entry methods or let others in because they are being monitored by security personnel. Discretionary physical control to a building or room is delegated to parties responsible for that building or room. In role-based access methods for physical control, groups of people who have common access needs are predetermined, and access to different locations is allowed with the same key or swipe card. Users in this model generally have some security training and are often allowed to grant access to others by serving as an escort or by issuing a guest badge. The security department coordinates the secure setup of the facility and surrounding areas, identifies the groups allowed to enter various areas, and allows them access based on their group membership. When physical security is examined, the most obvious consideration to control is physical access to systems and resources. Your goal is to allow only trusted use of these resources via positive identification that the entity accessing the systems is someone or something that has permission to do so based on the security model you have chosen . When planning for access control, you pay attention not only to direct physical contact with hosts and network hardware but also to line-of-sight access , which means you need to place systems in such a way that you don't allow an attacker with a telescope or binoculars to spy on typed passwords. You also need to consider areas covered by wireless device transmissions, which may be detected at far greater distances than are useful for two-way network connectivity. Even the location of systems in low-traffic, public, or unmonitored areas may pose security risks. You should consider controlling direct access to computer equipment and facilities as well as the computer environment, as discussed in the following sections. Physical BarriersAccess might be controlled by physically securing a system within a locked room or cabinet, attaching the system to fixed, nonmovable furniture using locking cables or restraints, and locking the case itself to prevent the removal of key components . Nonstandard case screws are also available to add another layer of security for publicly accessible terminals. Other secured area considerations include ensuring that air ducts, drop ceilings, and raised floors do not provide unauthorized avenues for physical access. You can have the most secure lock on the door with biometric devices for identification, but if the walls don't go up all the way and ceiling tiles can be removed to access rooms with sensitive equipment in them, someone can easily walk off with equipment and sensitive data. Frosted or painted glass can be used to eliminate direct visual observation of user actions, and very high security scenarios may mandate the use of electromagnetic shielding to prevent remote monitoring of emissions generated by video monitors , network switching, and system operation. Additionally, many modems and network hardware solutions use raw, transmitted data to illuminate activity indicator lights. Direct observation of these may allow an attacker to remotely eavesdrop on transmitted data using a telescope. Security guards , surveillance cameras , motion detectors, limited-access zones, token-based and biometric access requirements for restricted areas, and many other considerations may be involved in access control planning. Additionally, users must be educated in the need for each measure taken to prevent circumvention to improve ease of normal access. A single propped- open door, a system left logged in when the administrator is away from her desk, or a paper with sensitive data on it thrown in the garbage could undo many layers of protection. FacilitiesBecause a physical security plan should start with examining the perimeter of the building first, this section discusses the various methods used to secure your facilities from the outside of the building. Buildings that house sensitive information and systems usually have an area of cleared land surrounding them. This area is referred to as no-man's land . The purpose of this area is to eliminate the possibility of an intruder hiding in the bushes or behind another building. Intruders often piggyback their way into a building, meaning they wait for someone with proper access to enter the building and then enter behind them before the door closes . Depending on the company policy, the time of day, or the employee, these intruders may never be questioned or escorted out. Having a clear area in the main facility can keep this from happening. The next common deterrent is a fence or similar device that surrounds the entire building. A fence keeps out unwanted vehicles and people. One factor to consider in fencing is the height. The higher the fence, the harder it is to get over. Another factor to consider is the material the fence is made of. It is much easier to remove wooden slats or cut a chain link fence with bolt cutters than it is to drill through concrete or block. One final note: If the fence isn't maintained or the area around it isn't well lit, the fence can easily be compromised. The last physical barrier is a moat . Moats surround part or all of a facility and are excellent physical barriers because they have a low profile and are not as obtrusive as fencing. In this instance, the consideration would be the depth and width. As with all physical barriers, the moat must be well maintained. Here are some additional security measures that can be implemented to help deter unauthorized access:
Table 10.1. Biometric Technologies
Because a physical security plan should start with examining the perimeter of the building first, it might also be wise to discuss what happens when an evacuation is necessary. You don't want intruders plundering the building while employees are haphazardly running all over the place. The evacuation process could be a part of the disaster recovery plan and should include some of the following items:
Make sure that all users understand how these plans function and practice orderly evacuation procedures so that an emergency situation does not leave critical systems unguarded or unsecured. Smoke from a cigarette or a purposefully set flame could create an opportunity for an attacker to gain access to highly secure areas if evacuation planning does not include security considerations. Social EngineeringOne area of security planning that is often considered the most difficult to adequately secure is the legitimate user. Social engineering is a process by which an attacker may extract useful information from users who are often simply tricked into helping the attacker. It is extremely successful because it relies on human emotions. Common examples of social engineering attacks include the following:
Reverse Social EngineeringAnother form of social engineering has come to be known as reverse social engineering . Here, an attacker provides information to the legitimate user that causes the user to believe the attacker is an authorized technical assistant. This may be accomplished by obtaining an IT support badge or logo- bearing shirt that validates the attacker's legitimacy , by inserting the attacker's contact information for technical support in a secretary's Rolodex, or by making himself known for his technical skills by helping people around the office. Many users would rather ask assistance of a known nontechnical person who they know to be skilled in computer support rather than contact a legitimate technical staff person, who may be perceived as busy with more important matters. An attacker who can plan and cause a minor problem will then be able to easily correct this problem, gaining the confidence of the legitimate user while being able to observe operational and network configuration details as well as logon information, and potentially being left alone with an authorized account logged in to the network. TrainingUsers must be trained to avoid falling victim to social engineering attacks. This should be an ongoing process. Human behavior is difficult, if not impossible , to predict. Some guidelines for information to be included in user training may consist of the following points:
As new methods of social engineering come out, so must new training methods. The scope of the training should be done so that management has a different type of training than the users. Management training should focus on the ramifications of social engineering, such as the liability of the company when a breach happens, the financial damage that can happen, and how this can affect the reputation or credibility of the company. Security reviews involving tiger team assessments often begin with many types of social engineering attacks to locate vulnerable areas and to identify common business practices that may be exploited by an attacker. The U.S. Air Force used special groups of security experts to test for vulnerabilities at its bases. This is where the "tiger team" concept originated. The Department of Defense documented the first use of tiger teams to assess computer security in 1973. During the 1980s and early 1990s, tiger teams were used by large companies with complex networks. Since then, tiger teams have evolved into groups that mimic intruders and hackers. They are given permission to target a company's vulnerabilities by a management member, without any notification given to the network administrators or security personnel. This can be a very useful way of assessing vulnerabilities. Speaking from personal experience, it can be real eye- opener .
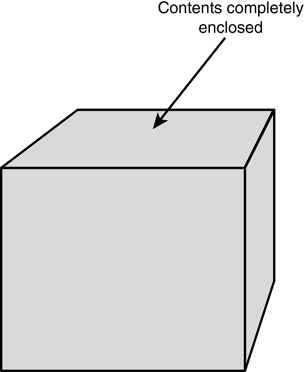
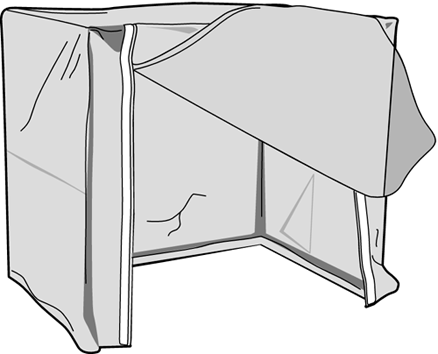
EnvironmentUsers should not be allowed to smoke, eat, or drink around critical hardware to prevent potential damage. Fluids, particulate matter, and smoke should not be allowed to enter keyboards, mice, power supplies , or other forms of hardware. Additionally, food trash can attract vermin and pests that may enter or damage equipment and wiring. Other environmental factors should be considered to protect key systems, including protection from strong magnetic fields near motors and generators as well as isolation from vibration or earth tremors. Extreme cold, high or low humidity, very dusty areas, and even lint in clothing may need to be considered when planning environmental security. Wireless CellsCell phones have become a very important part of our technological lives. Their advances should raise concern for network administrators. Mobile phones now have the capability to allow users to access their desktop systems and download unread email. An intruder with an AC adapter and a PCS phone with unlimited data usage could leak sensitive email to virtually any location in the world. Phones called IP phones operate within a network on an IP address by using Voice over IP (VoIP) technology. The IP address is relatively easy to set up, posing a huge security risk. A policy should be in place in regard to the use of these devices in the workplace. LocationThe location of everything from the actual building to wireless antennas affects security. When picking a location for a building, an organization should investigate the type of neighborhood, population, crime rate, and emergency response times. This will help in the planning of the physical barriers needed, such as fencing, lighting, and security personnel. An organization must also analyze the potential dangers from natural disasters and plan to reduce their impact when possible. When protecting computers, wiring closets, and other devices from physical damage due to either natural or man-made disasters, you must select their locations carefully . Proper placement of the equipment should cost a company little money upfront yet provide significant protection from possible loss of data due to flooding, fire, or theft. ShieldingOne risk that can often be overlooked is that of electronic emissions. Electrical equipment generally gives off electrical signals. Monitors, printers, fax machines, and even keyboards use electricity. These electronic signals are said to "leak" from computer and electronic equipment. Shielding seeks to reduce this output. The shielding can be local, cover an entire room, or cover a whole building, depending on the perceived threat. We're going to look at two types of shielding: TEMPEST and Faraday cages. TEMPEST is a code word developed by the U.S. government in the 1950s. It is an acronym built from the Transient Electromagnetic Pulse Emanation Standard. It describes standards used to limit or block electromagnetic emanation (radiation) from electronic equipment. TEMPEST has since grown in its definition to include the study of this radiation. Individual pieces of equipment are protected through extra shielding that helps prevent electrical signals from emanating. This extra shielding is a metallic sheath surrounding connection wires for mouse, keyboard, and video monitor connectors. It can also be a completely shielded case for the motherboard, CPU, hard drive, and video display system. This protection prevents the transfer of signals through the air or nearby conductors, such as copper pipes, electrical wires, and phone wires. You are most likely to find TEMPEST equipment in government, military, and corporate environments that process government/military classified information. Because this can be costly to implement, protecting an area within a building makes more sense than protecting individual pieces of equipment. A more efficient way to protect a large quantity of equipment from electronic eavesdropping is to place the equipment into a well-grounded metal box called a Faraday cage , which is named after its inventor , Dr. Michael Faraday. The box can be small enough for a cell phone or can encompass an entire building. The idea behind the cage is to protect its contents from electromagnetic fields. Two examples of Faraday cages are shown in Figures 10.2 and 10.3. Figure 10.2. Configuration of a Faraday cage that completely encloses the contents. Figure 10.3. Alternate configuration of a Faraday cage. The cage surrounds an object with interconnected and well-grounded metal. The metal used is typically a copper mesh that is attached to the walls and covered with plaster or drywall. The wire mesh acts as a net for stray electric signals, either inside or outside the box. Fire SuppressionFire is a danger common to all business environments and one that must be planned for well in advance of any possible occurrence. The first step in a fire safety program is fire prevention. The best way to prevent fires is to train employees to recognize dangerous situations and report these situations immediately. Knowing where a fire extinguisher is and how to use it can stop a small fire from becoming a major catastrophe. Many of the newer motion- and ultrasonic-detection systems also include heat and smoke detection for fire prevention. These systems alert the monitoring station of smoke or a rapid increase in temperature. If a fire does break out somewhere within the facility, a proper fire-suppression system can avert major damage. Keep in mind that laws and ordinances apply to the deployment and monitoring of a fire-suppression system. It is your responsibility to ensure that these codes are properly met. Fire requires three main components to exist: heat, oxygen, and fuel. Eliminate any of these components and the fire goes out. A common way to fight fire is with water. Water attempts to take away oxygen and heat. A wet-pipe fire-suppression system is the one that most people think of when discussing an indoor sprinkler system. The term wet is used to describe the state of the pipe during normal operations. The pipe in the wet-pipe system has water under pressure in it at all times. The pipes are interconnected and have sprinkler heads attached at regularly spaced intervals. The sprinkler heads have a stopper held in place with a bonding agent that is designed to melt at an appropriate temperature. After the stopper melts, it opens the valve and allows water to flow from the sprinkler head and extinguish the fire. Keep in mind that electronic equipment and water don't get along well. Fires that start outside electrical areas are well served by water-based sprinkler systems. Also keep in mind that all these systems should have both manual activation and manual shutoff capabilities. You want to be able to turn off a sprinkler system to prevent potential water damage. Most systems are designed to activate only one head at a time. This works effectively to put out fires in the early stages. Dry-pipe systems work in exactly the same fashion as wet-pipe systems, except that the pipes are filled with pressurized air instead of water. The stoppers work on the same principle. When the stopper melts, the air pressure is released and a valve in the system opens. One of the reasons for using a dry-pipe system is that when the outside temperature drops below freezing, any water in the pipes will freeze, causing them to burst. Another reason for justifying a dry-pipe system is the delay associated between the system activation and the actual water deployment. Because some laws require a sprinkler system even in areas of the building that house electrical equipment, there is enough of a delay that it is feasible for someone to manually deactivate the system before water starts to flow. In such a case, a company could deploy a dry-pipe system and a chemical system together. The delay in the dry-pipe system can be used to deploy the chemical system first and avoid serious damage to the running equipment from a water-based sprinkler system.
Chemical systems can be wet or dry and have the capability to put out fires more quickly than straight water-based systems. Chemical systems have the added benefit of being able to put out fires involving many types of fuel, including wood, oil, metal, fabric, chemical, and electrical. |
EAN: 2147483647
Pages: 162