Section A.1. Service Pack 1
|
A.1. Service Pack 1Slated to arrive on the market in the first quarter of 2005, Windows Server 2003 Service Pack 1 (SP1 for the remainder of this appendix) will include not only all the security hotfixes and vulnerability corrections released to date, but also several enhancements to security operations. Those of us with early access to the beta versions of the service pack agree that this release is akin to Windows XP's Service Pack 2, both in scope and in the degree of modification of the OS. The product contains the following fixes to some problems in the release version of Windows Server 2003:
Of course, this list is subject to change, but there are pretty good odds those features will make it into the final version. In fact, the list probably will grow during the first couple of months of 2005. A.1.1. The Security Configuration WizardThe single most important new feature of Windows Server 2003 SP1 is the Security Configuration Wizard (SCW), which provides a roles-based way to lock down the surface of your Windows Server 2003 machines. It's a great way to navigate the maze of services found in the operating system and to safely decide which ones can be turned off without affecting functionality for you or your users. In essence, the SCW uses a backend XML database that is intimately familiar with Windows Server 2003 and all its associated products, including enterprise applications such as Exchange, ISA, Identity Integration Server, and the like. Using this data, the SCW can make intelligent decisions about which services need to be running and which can be turned off. The SCW supports two modes:
The SCW creates files called security policies, which are simply reports of the results the SCW returns when analyzing a machine. The first machine to create a security policy is known as the baseline machine. These security policies can be exported and then applied to any server that matches the configuration of the baseline machine. Another neat feature is the ability to import and export configurations, which makes it a lot simpler to deploy the same configuration to multiple servers nearly simultaneously. Additionally, you can add information about your custom, homegrown applications to the XML database, as can third-party software companies, so the SCW can integrate with non-Microsoft applications as well. Let's briefly walk through the SCW and see how to install it, open it, and apply a configuration. A.1.1.1 Installing the SCWIt's quite simple to add the SCW software to a machine already running Windows Server 2003 SP1. Note that this tool probably will not be supported on Windows Server 2003 machines that have not been upgraded to SP1. To install the SCW, you must be an administratoreither a local administrator or a domain administrator. So:
A.1.1.2 Creating a security policy with the SCWIn this section, I'll describe the process of securing a box running IIS 6.0 with a SMTP virtual server and POP3 services enabled with the SCW. Of course, the results you get when running the SCW might differ depending on what roles your machine is assigned.
First, I'll open the SCW itself. I am greeted with the introductory screen of the wizard, as shown in Figure A-1. Figure A-1. The SCW introduction Clicking Next, I'll choose to create a new security policy, as shown in Figure A-2, and then proceed through the wizard. Figure A-2. Creating a new security policy The next screen, depicted in Figure A-3, asks me to select the server to analyze. This server will be used as the baseline for this new security policy, meaning that I can apply the file generated from the results of this analysis to any similarly configured machine. I'll choose the current server and then I'll click Next. Figure A-3. Selecting a baseline machine The system will trundle for a bit, and then, when the processing is finished, I will be notified. I'll click Next to view the roles assigned to this machine. This is shown in Figure A-4. Figure A-4. Selecting the current roles for the server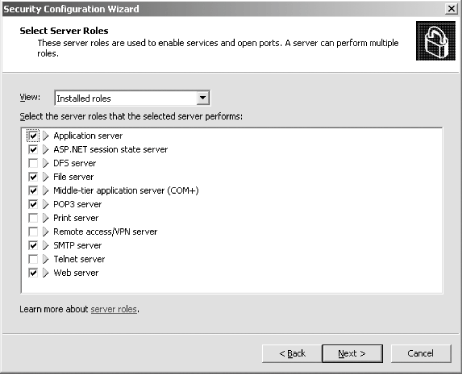 The wizard has correctly detected that I'm running IIS 6.0 with ASP.NET support, as well as with SMTP and POP3 services. Using the View list box at the top of the screen, I can toggle between seeing the roles currently installed on the machine, the roles not installed on the machine, all roles available, or the roles currently selected. Because the list is correct, I'll click Next to proceed. The next screen I see, shown in Figure A-5, asks me to select the services provided to clients by this machine. This also is detected during the initial analysis of the machine. Again, you can toggle, using the View list box, between viewing the detected features, all features, only the selected features, or the features not selected. Figure A-5. Selecting client features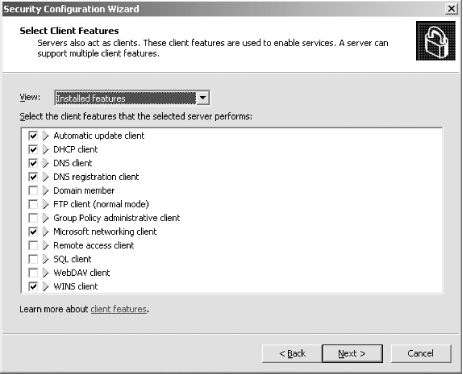 Because that list is correct, I'll click Next. Then I'm prompted to select the administration options, as shown in Figure A-6. Figure A-6. Selecting administration options The SCW will use this list to make sure the correct ports are opened up for remote administration tools and other purposes. Again, you can change your views the same way you could with the previous two screens. This list is correct for my box, so I'll click Next. Next, the wizard lists the services it detected that it doesn't know about by default. You can choose to turn these on or off on this screen, shown in Figure A-7. Figure A-7. Additional services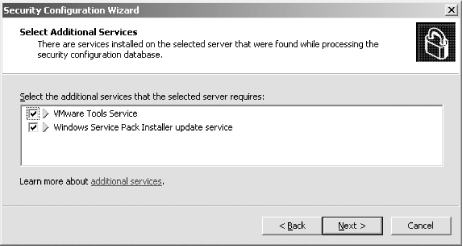 Then the wizard will ask you what to do when it finds other services that it doesn't know about. You can choose to either disable those services, or leave their default activity alone and deal with it later. I've chosen to leave the services alone, as you can see in Figure A-8. I'll click Next to continue. Figure A-8. Handling unspecified services Then the wizard wants you to confirm the changes you've outlined in the SCW thus far. This is shown in Figure A-9. Figure A-9. Confirming service changes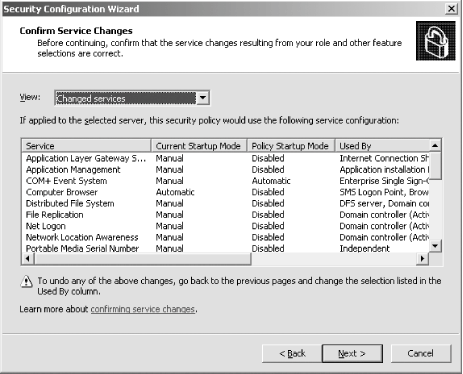 I'll click Next to continue. At this point, the wizard branches off into several sections, asking you to approve applications running on your machines, enable certain security features such as SMB signing and secure transmissions, open or close ports as required, change registry settings, modify your auditing policy, and (because I have IIS installed on this machine) make sure IIS itself is configured securely. I've taken a gallery of screenshots from the SCW for each section, and included them as Figures Figure A-10, Figure A-11, Figure A-12, Figure A-13, Figure A-14, and Figure A-15. Figure A-10. Opening ports and approving applications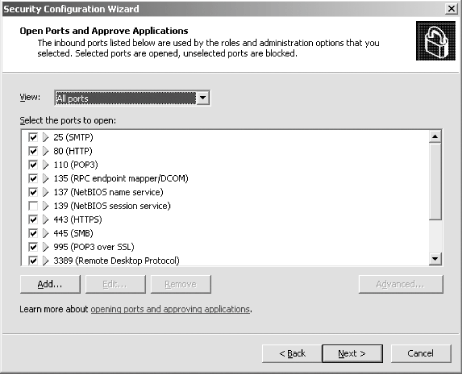 Figure A-11. Confirming the states of ports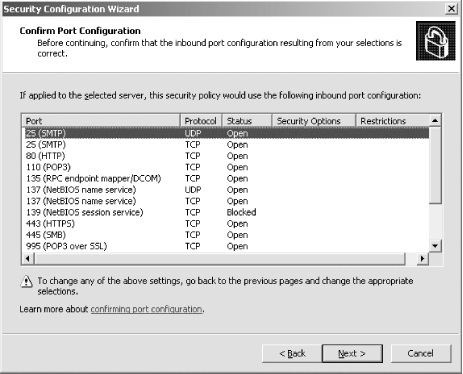 Figure A-12. Examining security settings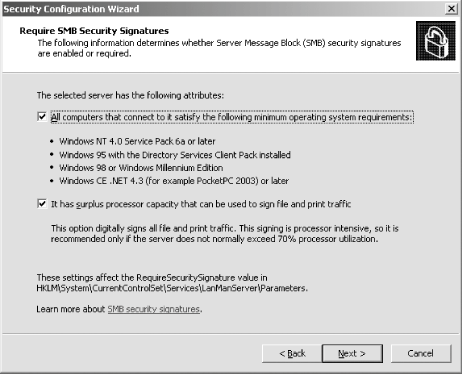 Figure A-13. Securing the registry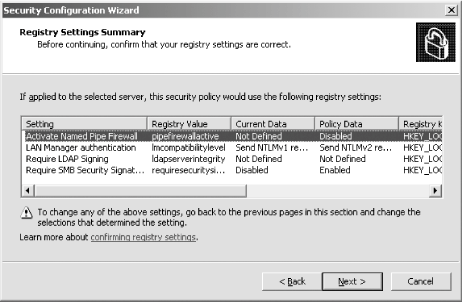 Figure A-14. Modifying the audit policy of your system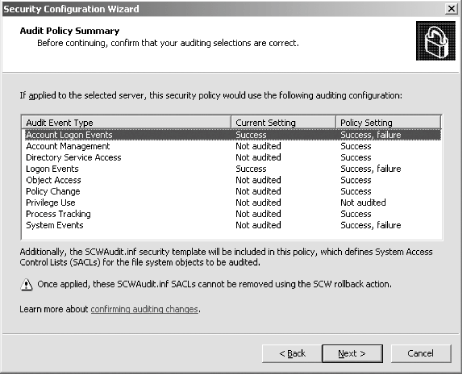 Figure A-15. Confirming security settings for IIS 6.0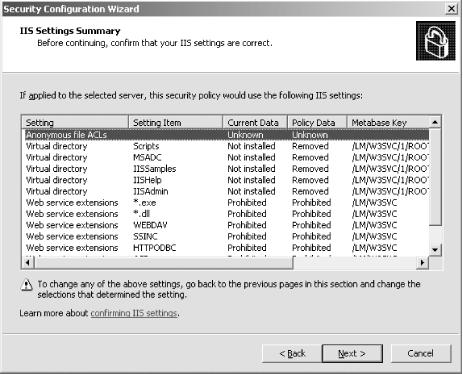 As you can see, the SCW is a much-needed addition to Windows Server 2003 and appears at this point to be a worthy effort to help administrators harden their machines. |
|
EAN: 2147483647
Pages: 149