Section 11.2. Virtual Private Networks
|
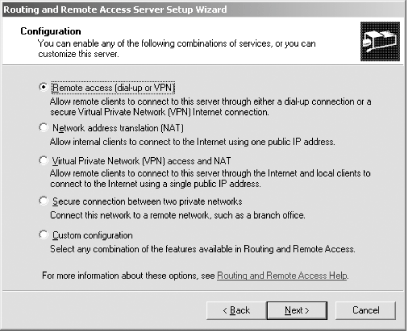
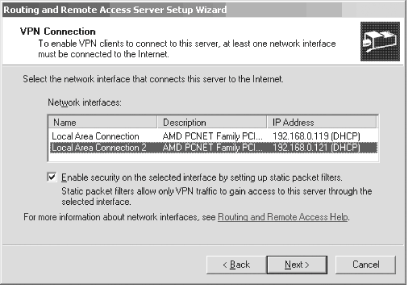
11.2. Virtual Private NetworksA virtual private network, or VPN, provides a secure connection over the public network infrastructure. VPNs give an organization the same access capabilities for remote connectivity as owned or leased connections, but at a much lower cost. (Of course, leased lines have their own benefits, but as far as private access is concerned, VPNs are a good solution.) Today, companies look to VPNs for extranet and wide-area intranet services. 11.2.1. How It WorksVPNs encrypt data before sending it through the public infrastructure, and then they decrypt the data at the receiving end of the network. For additional security, you can encrypt originating and destination network addresses. The VPN provides a point-to-point connection between the remote user's computer, the VPN client, and the organization's server, with data being passed through a "tunnel" that shields the data from the public network. In a sense, the public network's logistics don't matter because the data looks as if you sent it across a dedicated private link. Although the pathway doesn't matter to the VPN user, that pathway's performance does matter. VPNs based on Microsoft technology first used the Point-to-Point Tunneling Protocol (PPTP) to create a secure environment in which to tunnel through the network, while VPNs on Cisco equipment used the proprietary Layer 2 Forwarding (L2F) protocol. However, as the popularity of VPNs grew, each company merged the best parts of its standard with the other, and the Layer 2 Tunneling Protocol (L2TP) was born. L2TP is the modern VPN protocol and will be used in all examples in the remainder of this section. 11.2.2. Configuring the Routing and Remote Access ServerTo begin our exploration of VPNs, let's first set up the Routing and Remote Access Service (RRAS), which controls all remote connections attempting to connect to your server. The RRAS effectively serves as the endpoint to connections coming to and from your servers, routing them through the proper subnets and gateways, answering remote connection requests and sending authentication credentials to trusted sources, and enforcing encryption requirements. Think of RRAS as the manager for all things related to remote connectivity with your server. Your server will need two network cards for a basic, automated VPN configuration: one for connectivity to your internal network, and another for basic IP connections to the Internet. You can configure a VPN with only one network adapter, but you must do so manually. In this section, I will cover the former method, which does require two network adapters. Some of the most common setup scenarios for RRAS are as follows.
Let's begin:
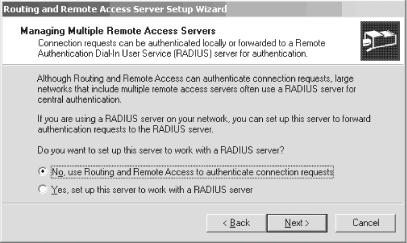
The RRAS service will be stopped and then restarted, and your new settings will be in place. You'll be dumped back to the RRAS console with the service now started and ready for business. Now, just make sure the virtual VPN ports are ready for use by your clients. From the RRAS console, expand the node with your server's name and right-click the Ports entry. Select Properties from the pop-up context menu and you'll see the screen shown in Figure 11-16. Figure 11-16. Double-checking port configuration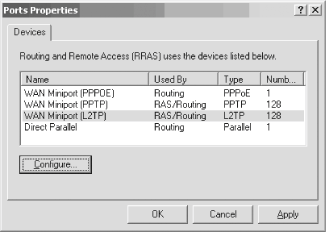 Select the WAN Miniport (L2TP) port, and then click the Configure button to ensure that inbound calls are allowed. You'll see the Configure Device screen appear, as shown in Figure 11-17. Figure 11-17. The Configure Device screen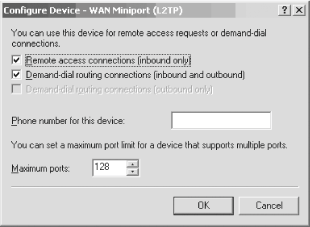 Make sure the first option, Remote access connections (inbound only), is checked. Then, in the Phone number for this device field, enter the public IP address for this VPN server. This address is the one clients will use from their remote locations to connect to your corporate network. You also can adjust upward or downward the number of connections you want to make availableanywhere from 1 to 128 simultaneous VPN tunnels. Click OK when you're finished. Congratulations! Your RRAS server is set up to handle incoming VPN connections. 11.2.2.1 Granting access to usersBefore your users can successfully use a VPN connection to your new RRAS server, you need to give them permission to dial in. You can do this through Active Directory Users and Computers. Simply open the tool and navigate through the console to the user for whom you want to enable access. Then right-click that user and select Properties. Finally, navigate to the Dial-in tab. Click the Allow access option, which will grant access permission to the user. This is shown in Figure 11-18. Figure 11-18. Granting permission to a user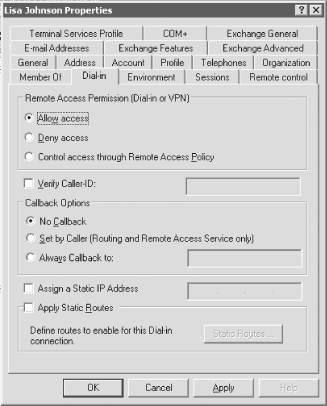 11.2.3. Authentication and Encryption MethodsVPNs in Windows Server 2003 support several different authentication and encryption methods, which you can configure on each RRAS server by right-clicking the server name in the left pane of the RRAS console and selecting Properties. The Security tab is command central for these settings, as you can see in Figure 11-19. Figure 11-19. The Security tab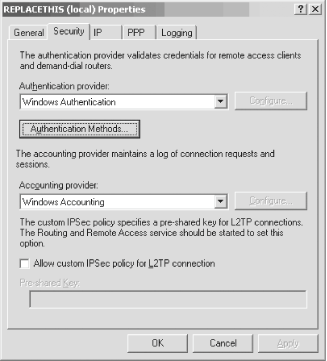 You can choose the different protocols by which to authenticate a user by clicking the Authentication Methods button. Doing so brings up the Authentication Methods screen, as shown in Figure 11-20. Figure 11-20. The Authentication Methods screen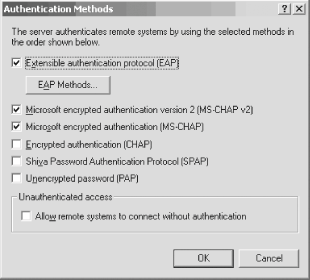 On this screen, you can select the different authentication methods to use when a server is touched by a user attempting to connect. A short discussion of each method follows.
|
|
EAN: 2147483647
Pages: 149