Protect Your Web Server
|
|
Protecting your web server is of the utmost importance in the age of the Internet. Hackers, crackers, computer viruses, and other malicious little beasts are out there trying to gain entry into whatever system they can. A vulnerable web server is just too easy an opportunity for these types of attackers to pass up. Fortunately, you can take steps to help keep your system secure.
Protect Your Web Server from Internal Mishaps
You may be surprised to learn that you need to protect your web server from internal forces. After all, anything internal is supposed to be safe, right? Again, we get into that reduce-the-possibilityof-accidents mode. Internally, you have developers who have access to the web server. If your security model isn't tight, you may have people who aren't developers who have access to the web server and its directories. Although the former isn't as bad as the latter, both open the possibility for disaster.
When it comes to server permissions and rights, give only those who need them the least amount of privilege they need to do their job. This means that you restrict rights to those groups and individuals who need them. Accounting doesn't need access to the web server's live directory. And developers don't usually need access to the accounting package folders. Following that logic, all your developers probably don't need access to the live web server, but they do need access to the development server.
After a long, hard shift of programming while trying to meet a tight deadline, a mapped drive to the live folder looks an awfully lot like any other folder, as you can see in Figure 17.2. The figure looks like any other folder view; which is exactly the point. We could have accidentally overwritten or deleted a folder on the live server if we weren't alert.
Figure 17.2: A mapped drive to the live server can be dangerous unless you're very alert
| Tip | A good rule of thumb that you should adopt before installing new software or launching a new version of your website is back up the old version and data first! You don't want to accidentally lose updates to your tables or a tweak that someone made on the live site (against policy, mind you, but a tweak that works) that didn't make it to development code. Plus, in case something goes wrong and the new version doesn't work as you expect, you can replace it quickly with a backup. Making a backup of a website generally involves copying only the website folder and its database. So make sure you include this step in your new-version-release policy. |
If you need to delegate responsibilities and need one or more developers to move files live on a regular basis, give those one or two developers security rights and permissions to do so. Remove the possibility of accidental deletion or overwriting of the files by disallowing access to everyone else. Remember, you generally want to give everyone the least amount of privileges with which they can accomplish their job. The "least privilege rule" may make you seem like an inflexible controller, but when it comes to securing your live web presence, a little explanation about why the rule is in place generally assuages any concerns your colleagues may have.
Protect Your Web Server from External Attacks
Needless to say, a greater number of possible attacks lurk outside your office than inside. New methods by which hackers, crackers, and computer viruses gain access are revealed almost weekly. With more than 60,000 identified computer viruses out there in Net land, you will learn that a good antivirus scanner is your friend if you don't already know it. You'll also come to find that a properly configured firewall will be your first defense against unauthorized intrusion. But one of your first tasks is to make sure you have the latest patches and security fixes for the operating system you use.
Operating systems are complex pieces of software. With hundreds of millions of lines of code, there are going to be weaknesses somewhere. (After all, humans wrote the software, and humans make errors.) Even though software companies run extensive beta tests on their software, invariably there will be flaws and security holes somewhere that a cracker will find and exploit. Once flaws are discovered, software companies are generally quick to fix them and release patches to their systems that plug these holes.
| Note | Patches are files that you can usually download or receive on a CD that fix flaws in a piece of software without your having to reinstall the complete piece of software again. Patches generally don't interfere with how you've configured your software, which usually makes application of the patch seamless and trouble free. |
Companies, and open-source movements as well, have tried to make patches easily accessible. For example, Microsoft even has an automated patching system called Windows Update to which they built a link in Internet Explorer, shown in Figure 17.3, that you can access from the Tools menu. When you launch Windows Update, your browser takes to you windowsupdate.com, the Windows Update site, shown in Figure 17.4.
Figure 17.3: Microsoft has made it quick and easy to get patches through Internet Explorer.
Figure 17.4: Windows Update will scan your system and report the patches that are available for your system.
Sun has patches available for the Sun Linux products available at their Sun Linux Support page, shown in Figure 17.5 and found at http://sunsolve.sun.com/patches/linux.
Figure 17.5: You can find Sun's offering of patches for Linux at their patches site
Apple has patches for OS X on their support page-see Figure 17.6-found at www.apple.com/support. Regardless of the operating system you use, always obtain and apply the latest patches regularly.
Figure 17.6: Apple also has downloadable updates for its easy-to-use operating system.
Install a Good, Industry-Standard Antivirus Program
A networked computer without an antivirus scanner is like an automobile without headlights: sure you can operate the machine without them, but it's dangerous, and you're probably going to crash hard if you do it for long. As we mentioned, more than 60,000 documented computer viruses are floating around on the Internet. Everything from Melissa to Code Red is still alive out there; it's just that with new patches to operating systems and programs that prevent their exploits, along with antivirus scanners, they're not much of an inconvenience any longer. Naturally, new viruses frequently crop up (according to Trend Micro, more than 400 a month) and demand your attention and treatment. To protect your computer systems and servers, you can take some basic steps to remain virus-free.
First, purchase a good, industry-standard antivirus program such as Trend Micro's suite of products or McAfee's or Symantec's products. Other antivirus scanners are available, but these products are the top three in the industry. Each suite offers various features that protect your entire enterprise, as well as the individual desktop. They're highly customizable, and some even provide informative reports on virus attack attempts, desktops in the enterprise that have been infected, and so forth. If you only need to protect a single machine, obtain the individual desktop version of the antivirus software.
Generally, you can configure the antivirus software, such as Trend Micro's PC-cillin, to automatically clean viruses from files when it finds one. If PC-cillin is unable to clean the file, you can tell it to perform other actions such as delete the file or quarantine it so that you can deal with the file later. Quarantining a file prevents any automatic deletion of what may be an important file that just happened to get infected. Once you know the file is infected, you can take steps to extract the information that you need from the file before removing it from your system.
You may be wondering how viruses get into your computer system. Code Red debuted the first virus that exploited every known method of spreading infection-through e-mail, through networked drives, and through the Internet. Figure 17.7 shows a diagram that illustrates potential security breaks. Many computers connect to your server internally. The server is communicating with the Internet using TCP/IP and retrieving e-mail, browser pages, and so forth. You need a virus scanner that can protect all these points of entry into your network. You need protection not only from the Internet, but also for each machine on your network. Your colleagues may be transferring files from work to home and vice versa in order to get their work done. An infected home computer will transfer the virus to the floppy or other disk that is used to port the files. Once the user sticks the infected disk into their work computer, your network could become infected. This is why desktops, e-mail servers, file servers, and web servers need up-to-date antivirus protection.

Figure 17.7: Viral infection can come from many sources.
Make Sure You Have a Good, Properly Configured Firewall in Place
Firewalls are so named because they help keep something from spreading, much like an architectural firewall keeps fire from spreading to other parts of an inflamed building. They consist of either software or hardware devices that sit between your system and the Internet, much as Figure 17.8 shows. Firewalls mask your system from the Internet and allow you to halt communication across certain TCP/IP ports and your network. Hackers, crackers, and viruses can take advantage of various ports and exploit their weaknesses in certain operating systems and in web and mail servers.
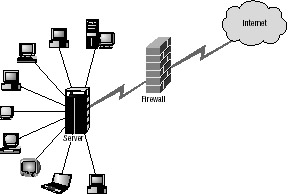
Figure 17.8: A typical firewall placement
Ports, in reference to the Internet, are basically communication points (think of phone lines) that allow various types of programs to work across the Internet. For example, port 80 is the common HTTP (Hypertext Transfer Protocol) port that allows you to see a page when you load your browser. Port 21 is commonly used for FTP (File Transfer Protocol), and port 25 is used for e-mail. And, of course, many other ports are in use.
There are as many configurations of firewalls and network systems as there are companies that employ them. Some use two or more firewalls, depending on their server configuration and which groups need access to the varied TCP/IP ports available. For example, company policy may be that no one should be able to play RealPlayer files, and the system administrator blocks those ports through the firewall. However, marketing may need access to those types of streaming media files in order to keep an eye on the competitor. A different firewall configuration would allow one group access to ports restricted from the company as a whole.
Following along these lines, to really lock down your network, turn off all unneeded ports. That is, you might want to close off every port and just open those that you know you'll use, such as ports 80, 25, 110, and so forth. You'll need a good understanding of how ports and firewalls work before you start configuring them. This job, needless to say, is typically left to your network or system administrator.
For those of you who are interested in finding out whether your system is open and vulnerable, check out Gibson Research Center's Shields Up page, found at http://grc.com. The GRC has made a name for itself pointing out and offering workarounds for security and privacy flaws in Internet software. Figure 17.9 shows the beginning of a sample result screen of the Shields Up test. Your computer's IP address will normally appear in the center of the page where we've masked our IP. You'll get feedback on what ports might be open and what it might mean to your security if they are.

Figure 17.9: Gibson Research Center offers a quick-check security tool that will give you an idea of how secure your computer is.
|
|
EAN: 2147483647
Pages: 214
- Step 1.1 Install OpenSSH to Replace the Remote Access Protocols with Encrypted Versions
- Step 2.1 Use the OpenSSH Tool Suite to Replace Clear-Text Programs
- Step 3.2 Use PuTTY / plink as a Command Line Replacement for telnet / rlogin
- Step 3.4 Use PuTTYs Tools to Transfer Files from the Windows Command Line
- Step 6.3 X11 Forwarding