Chapter 4: Introducing Windows Authentication
This chapter focuses on the most fundamental security service of any operating system: authentication. Before an entity is given access to a resource on a Windows system, the operating system must validate the entity’s identity and check whether it can access that particular resource. The latter process is known as authorization, and it is discussed in greater detail later in this book. The first process is known as authentication and is the topic of discussion in this and the following chapters. The primary purpose of authentication is to prove and validate an entity’s identity; it answers the question: to whom or what is the system talking?
The chapter starts off with a general explanation of authentication infrastructure terminology. Then it looks at the Windows authentication architecture and more detailed Windows authentication topics such as the NTLM authentication protocol, the secondary logon feature, credential caching, and strong authentication options for Windows.
4.1 Authentication infrastructure terminology
In an authentication infrastructure, users trust a set of authentication authorities to provide trustworthy authentication services. Authentication authorities are represented by one or more authentication servers. Authentication authorities are also referred to as authentication trusted third parties (TTPs). Every authentication authority reigns over a set of resources located on machines that are part of the authentication authority’s kingdom. I will call this “kingdom” from now on a “domain” (in NT terminology)—but you may as well call it a “realm” (in Kerberos terminology) or a “cell” (in DCE terminology)—it does not really matter. Anyhow, when a user logs on successfully to the authentication authority’s domain, he or she can transparently access all resources in the domain, without reauthenticating to every individual resource server.
Note the different authentication infrastructure–related terms:
-
An authentication infrastructure refers to a set of authentication servers and authentication authorities, providing outsourced authentication services.
-
Authentication servers are the physical machines performing the authentication functions.
-
Authentication authorities are a logical trust-related concept: They are the entities that are trusted by users to perform reliable authentication functions.
In order to authenticate, a user shares a set of “credentials” with the authentication authority. The authentication authority stores its copy of the credentials in a secured database. For the moment, very popular types of credential databases are LDAP-accessible directories. Depending on the type of credentials, the user can simply remember them or “safeguard” them in some other way (e.g., store them on a smart card).
During a typical authentication process (like the one illustrated in Figure 4.1), a user submits his or her credentials (in the earlier example, a user ID and a password) or the result of a cryptographic operation involving his or her credentials to the authentication authority (which is represented by an authentication server). The authentication authority then validates the credentials using the data stored in its credential database. If the credentials supplied by the user and the ones stored in the database match or if the result of a cryptographic operation on the credentials stored in the database equals the information supplied by the user, the user’s identity is considered authentic. Consequently, the user is given or denied access to the authentication authority’s kingdom. To prove that the user has been authenticated, the authentication authority will issue a cryptographic token to the user. This token is used as proof of authentication in subsequent accesses to other resources in the authentication authority’s kingdom.
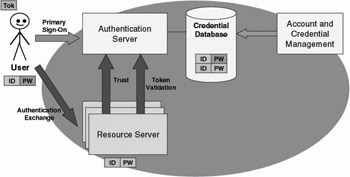
Figure 4.1: Authentication Infrastructure terminology.
EAN: 2147483647
Pages: 137
- Structures, Processes and Relational Mechanisms for IT Governance
- Linking the IT Balanced Scorecard to the Business Objectives at a Major Canadian Financial Group
- Technical Issues Related to IT Governance Tactics: Product Metrics, Measurements and Process Control
- Governing Information Technology Through COBIT
- The Evolution of IT Governance at NB Power