Password Security
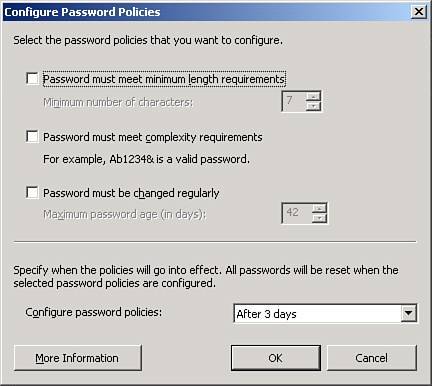
| Password security is a topic that can generate a lot of heated discussions among users and system administrators alike. The lines are generally divided between having passwords that are difficult to guess or crack by a malicious outsider and having passwords that are easy for users to remember without having to write them down (which would make it easier for a malicious outsider to access). Even when these parties agree that more secure passwords should be used, the argument can then turn to enforcement and implementation. SBS 2003 contains several tools to help make managing secure passwords easier for the system administrator. The primary element is the Small Business Server Domain Password Policy group policy object that is applied to the SBS domain. The settings in this policy object can be managed through several SBS wizards. At the end of the Connect to the Internet and the Repair Internet and E-mail Settings Wizards, if the password policies have not been enabled, the user running those wizards is asked whether he wants to enable the password policies. The policies are primarily managed through the Configure Password Policies Wizard found in the Users section of the Server Management Console. Configure Password PoliciesFigure 9.8 shows the Configure Password Policies dialog box. The password policy is broken down into three requirements: password length, password complexity, and password age. Figure 9.8. The Configure Password Policies dialog box allows the administrator to make password restrictions as tough or as lax as desired. Password LengthWhen the Password Must Meet Minimum Length Requirements check box is enabled, all users are forced to have a password with at least as many characters as identified in the setting. The general rule is that the longer the password is, the tougher it is to break, even when password-cracking tools are used. When this setting is enabled, a number from 014 can be used as the minimum length. When the value is set to 0, or if this option is not selected, a user account can have a blank password, which is generally not desired. Just because a password is long does not necessarily mean that it is secure. The password "smallbusinesscompany" would meet a minimum length requirement of 14 characters, but is still not a very secure password. Setting a minimum password length alone is not enough to ensure a secure password. Password ComplexityWhen the Password Must Meet Complexity Requirements check box is enabled, all users must have a password that meets Windows password complexity rules. The Windows rules are made up of two sections. The first part of the rules prevents a user from using all or part of his username or logon ID as part of the password. The second part of the rule is that the password must contain characters from three of the following four character groups:
The Configure Password Policies dialog box gives the password "Ab1234&" as a password that would meet complexity requirements. It contains characters from all four of the character groups, and so long as the account name does not start with "ab" or have "1234" in the ID, it should work for most user accounts. Making a password complex also makes it more difficult to remember. One currently used method to help make complex passwords easy to remember is to use pass phrases or acronyms based on longer passages. For example, you might take a phrase from a Dr. Seuss book, such as "Oh, the places you will go!" and convert that into a pass phrase. With a few tweaks, that phrase might turn into the password "0tpUwg!" which uses characters from all four character groups (the number 0 for the word "oh", upper- and lowercase letters, and a special character "!"). Note Some non-alphanumeric characters can be used in passwords but could cause problems when being accessed from some systems. For example, the "!" and "@" characters have special meanings in most UNIX systems and might not be passed along as part of the password. Again, only setting complexity requirements may not be enough to create a secure password. For example, the password "B0b!" would meet complexity requirements, but because of its length, it might not take long to crack. Password AgeEven the best passwords are of no use of they have been compromised. If a malicious outsider somehow learns a user's password, even if the password is long and complex, the outsider will be able to access that user's account until that password is changed. Thus the notion of changing passwords on a regular basis comes into play. When the Password Must Be Changed Regularly check box is enabled, all users will not be able to keep their passwords longer than the value listed. The Windows default for this setting is 42 days, but the value can be set anywhere from 0 to 999. Many enterprise environments set password expiration between 30 and 90 days depending on their environment and level of risk. Generally, if the risk of password compromise is low, a longer password age can be set. If the risk is high, a shorter password age should be set. Policy EnforcementWhen a change is made to the password policies you can specify when the updated policies will go into effect by selecting a value from the Configure Password Policies drop-down list. The selections range from Immediately, which puts the new policy into effect as soon as you click OK, to 7 days, which gives you a week to alert your users to the new password requirements and give them time to make changes. After the policy goes into effect, a user with a password that does not match the policy will be unable to access the network until the password is changed to one that meets the new requirements. For that reason, it is best to set the policy enforcement out several days to give you and your client time to address any questions or concerns that may arise before the policy goes into effect. Small Business Server Domain Password Policy Group Policy ObjectThe Configure Password Policies Wizard is a friendly front end that modifies the settings in the Small Business Server Domain Password Policy group policy object. Although the best way to modify settings in this object is to use the wizard, an understanding of how the policy looks can help if problems arise related to password issues. The Small Business Server Domain Password Policy object can be found in the Server Management Console, under Advanced Management, Group Policy Management, Forest:, Domains, [internal domain name]. To bring up the policy in the Group Policy Object Editor, right-click on the policy object and select Edit. The settings related to password policy are found under Computer Configuration, Windows Settings, Security Settings, Account Policies, Password Policy, as shown in Figure 9.9. Figure 9.9. The policy elements for the Small Business Server Domain Password Policy object.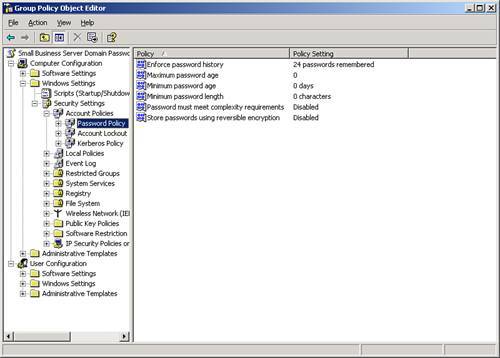 Note For more information about managing group policy objects, see Chapter 20, "Group Policy." You can see in Figure 9.9 that there are more options for password policy in the group policy object than can be set in the Configure Password Policies Wizard. The Enforce Password History, Minimum Password Age, and Store Passwords Using Reversible Encryption elements can be modified only in this environment. The first two of these elements can be used to keep users from changing their password when required and then changing back to a previously used value. Windows systems default to remembering the last 24 passwords that have been used, which is the maximum value. With this setting enabled, a user would have to change his password 24 times before being able to use a previous password again. The Minimum Password Age element specifies how often a user can change his password. With the default value of 0, a user can change a password as many times as desired during the same day. Increasing this value prevents a user from changing a password more than one time on any given day. The intent, of course, is to discourage users from changing their passwords rapidly to get through the stored password history and get back to the password they had been using. The Store Passwords Using Reversible Encryption policy should never be changed from the default value of Disabled. With this setting, passwords are stored in Active Directory using one-way encryption, meaning that if someone were to get a copy of the encrypted password, she could not determine the original password. If this setting is changed to Enabled, the password is stored using two-way encryption, meaning that the original password can be calculated if the encrypted password is captured. Any changes made to the policy object in this interface take effect the next time group policy is updated for the server and workstations, or the update can be forced using the gpupdate /force command on the server and workstations. Any changes made to the password history, minimum password age, and reversible encryption elements will not be changed by subsequent runs of the Configure Password Policies Wizard.
|
EAN: 2147483647
Pages: 253