Certification Objective 10.01Understanding Network Fundamentals
Certification Objective 10.01—Understanding Network Fundamentals
Exam Objective 1.1: Control and monitor network interfaces including MAC addresses, IP addresses, network packets, and configure the IPv4 interfaces at boot time.
To start managing the Solaris network environment, you need to understand the basic terms and concepts in networking. A computer network is a group of computers connected together to share resources such as printers and data. Remember, communication also involves the exchange of data. Under this basic definition, two computers connected together in your garage make a network, and the Internet, with millions of computers connected to it, is also a network. Not only by definition but also by practice, both the networks (the Internet and the garage net) work for the user in the same way—that is, the end user cannot tell whether the communication partner is sitting next door or on the other side of the globe. This experience is made possible because networking technology is based on a set of global standards (protocols) called TCP/IP, and for that reason networking is also called TCP/IP networking.
TCP/IP Networking
From a user's perspective, the Internet is just a big network, even though we know that underneath it is a collection of various kinds of networks. So what makes a collection of heterogeneous networks one uniform network, called the Internet, to the end users connected to the net. The answer is the suite of protocols called TCP/IP, named after the two important protocols included in it—Transmission Control Protocol (TCP) and Internet Protocol (IP). In other words, the Internet is based on open standards called protocols. A protocol is not a piece of software itself; rather, it is a specification of what the software should do and how—the specifications for writing the relevant software.
In the case of TCP/IP protocols, these specifications lay out the syntactic and semantic rules for communication, such as the formats of requests and responses between computers. These specifications are written in a hardware-independent way so that the software based on these specifications will be independent of the underlying hardware. For example, a web browser and a web server are the software written based on the Hypertext Transfer Protocol (HTTP). However, for brevity, the terms like "this protocol is running" or "this protocol does this" are often used. Whenever you read or hear of a protocol running on something or a protocol doing something, always do the mental translation to "the software based on the protocol is running or doing something." A protocol by itself is just a specification; it is the software, written, based on those specifications, that actually does something. Each computer connected to the net has TCP/IP (i.e., the software that implements the TCP/IP suite of protocols) installed on it.
The underlying ideas and principles of TCP/IP were developed during the late 1960s and 1970s as a result of research funded by the U.S. Department of Defense Advanced Research Projects Agency (ARPA), also known as the Defense Advanced Research Projects Agency (DARPA). The TCP/IP internet, also known as the Internet or just "the net," enables hundreds of millions of users around the globe to communicate with each other as though they were connected to one single network. In other words, the Internet appears the same to two communicating users regardless of whether they are connected to the same local area network (LAN) in the same building or to two different LANs on the opposite sides of the globe. A LAN is a network that is confined to a local area, such as a room, a building, or a group of local buildings. Because your Solaris system is more likely than not connected to the net (e.g., connected to a LAN, which in turn is connected to the Internet), you must learn the fundamentals of TCP/IP networking. We begin with looking at how the TCP/IP protocol suite is organized.
Network Protocol Layering Models
In the very beginning of the computer networking era, only computers from the same vendor could communicate with each other because of the different standards (or lack of standards) being used by different vendors. In the late 1970s, the International Organization for Standardization (ISO) created a reference model of Open Systems Interconnection (OSI). The protocols in the OSI model are organized into seven layers. Each layer is a group of related protocols that collectively (or alternatively) solve one part of the whole problem. Any two layers are placed next to each other based on which parts of the problem they solve and how those parts are related to each other. OSI is a very good theoretical model, and TCP/IP (the implementation of it) is the most practical system ever built closest to this model.
The OSI Model
The OSI reference model has seven interrelated layers of protocols shown in Figure 10-1. The data in these layers flows downward on the sender machine and upward on the recipient machine.
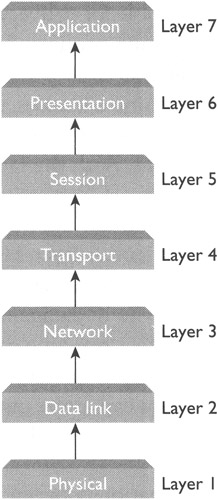
Figure 10-1: The seven protocol layers of the OSI reference model
The seven layers of the OSI model are described here:
Layer 1: Physical The physical layer contains the specifications of the network hardware. In other words, it specifies standards for the physical signal and the media through which the signal travels from one computer to another. You can build all the layers you want, but at the end of the day the data travels on the wire, and the physical layer specifies the "wire." From the communication viewpoint, it has two tasks: to receive bits from other machines and to send bits to other machines on the wire. (By wire we simply mean the media used for transmission; of course there can be wireless media.) Cables, hubs, and connectors are some examples of network hardware specified in the physical layer. However, note that the physical layer supports a wide variety of standards that give rise to heterogeneous physical networks (LANs). For this reason a computer connected to one kind of network cannot communicate with a computer connected to another kind of network. One single task of TCP/IP is to solve this communication problem without demanding the elimination of differences between different LAN technologies. So the data is delivered on the physical media in a stream of bits that must be put together to make sense. This work begins at layer 2.
Layer 2: Data Link The layer 2 protocols specify how the bits of data are organized into a packet and addressed from one machine to another on a given physical network (LAN). In other words, these protocols define standards for data packets, called frames, and machine addresses, called media access (MAC) addresses. A MAC address is also called a hardware address, a physical address, or an Ethernet address (in an Ethernet LAN). The hardware can fail, and as a result transmission errors may occur. The data link layer also deals with transmission errors by providing mechanisms such as cyclic redundancy check (CRC). A network device aware of the MAC addresses (e.g., a switch or a bridge) is said to be operating at layer 2. Most of the LAN standards in the data link layer are defined by Institute of Electrical and Electronics Engineers (IEEE) and are known as IEEE 802.x standards; the varying value of x represents the varieties of physical networks supported at this level. Therefore, the format of the data packets and the frames, including the MAC address, will be different for different kinds of networks. This alone makes it impossible for two machines connected to two different kinds of networks to communicate with each other. This problem is solved by protocols in layer 3.
Layer 3: Network The network layer is responsible for delivery of data packets from a machine connected to one network to a machine connected to another network, even if the two networks are based on different layer-2 standards. This is accomplished by defining uniform standards for machine addresses, data packets, and routing. The machine addresses in this layer are called Internet addresses or IP addresses, and the data packets are called IP datagrams. Both the famous Internet Protocol (IP), one of the two protocols after which the TCP/IP suite is named, and the routing protocols are part of this layer. The network devices that deal with the IP addresses, such as routers, are said to be operating in this layer. However, there are two communication problems that are not addressed in this layer. First, an IP address is an address of a computer. Therefore, it will enable the IP datagram to reach the correct machine, but which application running on that machine should receive the data? The answer from layer 3 is I don't: know. Second, the data delivery service offered by layer 3 is unreliable, which means that data can arrive out of order, can be delayed, and can get lost on the way. These two problems are addressed by layer 4.
Layer 4: Transport Layer 4 provides communication between two applications running on two machines connected to possibly two different networks. It accomplishes this task by introducing the concept of a port, which is a unique number assigned to a program running on the machine. A pair made up of an IP address and a port number uniquely identifies a source (or a destination), a program on a machine, and is called an end point or a socket. For this reason it is also said that layer 4 facilitates end-to-end communication. Some protocols in layer 4, such as the User Datagram Protocol (UDP) do not address the reliability issue. Others, however, such as the Transport Communication Protocol (TCP) do implement reliability by using acknowledgments to determine whether the data has been lost and re-transmitting the lost data. The data packets are called segments in TCP, and user datagrams in UDP. Communication using TCP is also called connection-oriented communication, because a virtual connection is established between the two machines that want to exchange data. This simply means that the two machines agree on a few things such as their readiness for communication in the beginning, and they mutually mark the end of communication, which is called closing the connection. In some applications, such as video broadcasts on the web, retransmission of lost data (frames) does not make sense and is not even desired. For such applications, UDP is an ideal choice. Therefore, the protocols in the transport layer enable an application on one computer connected to the net to communicate with another application running on another computer connected to the net from anywhere by using ports. The whole issue arises because there may be multiple applications running on a computer simultaneously. That raises another issue: who will keep the communication data (coming in or going out) of one application separate from the other application on the same computer? This is the responsibility of the next higher layer: the session layer.
Layer 5: Session Layer 5 protocols specify how to establish and maintain a session between two entities (programs) on two computers—for example, how to manage multiple logins to a remote computer. Security-related specifications such as authentication and passwords are dealt with in this layer. Some examples of session-layer protocols and standards include Network File System (NFS) supported by Solaris, Structured Query Language (SQL), and Remote Procedure Calls (RFC). Regardless of what kind of computer (Windows, Linux, or Mac) you are working on, an email message (or a web page) looks pretty much the same on all machines. However, the data does not travel in the same format in which an application (such as email or web browser) sends (or receives) it. Furthermore, different kinds of computers have different internal representations of high-level data such as a character or an integer. Who handles these differences to make the communication among different kinds of computers smooth? The answer is: the next higher layer, called the presentation layer.
Layer 6: Presentation The presentation layer acts as a format translator between the local standards on a specific kind of computer and the global standard that is used for transmission. It also deals with the issue of how the standard data should be formatted. For example, the following standards are part of layer 6: Tagged Image File Format (TIFF), Joint Photographic Experts Group (JPEG), Moving Pictures Experts Group (MPEG), and Rich Text Format (RTF). Remember that all these layers are means to an end: to enable two applications on different machines to communicate with each other. Who determines what kind of an application can use the network and how for communicating with another application? The answer is the protocols in layer 7.
Layer 7: Application A protocol in the application layer specifies how an application program on one machine connected to the net makes a request, and how another program running on another machine connected to the net responds to that request. The Hyptertext Transfer Protocol (HTTP), on which the World Wide Web is based, and the Simple Mail Transfer Protocol (SMTP), which is used to send email messages from one email server to another, are two examples of the many protocols available in the application layer. The World Wide Web (based on HTTP) is so popular that it has become virtually synonymous with the Internet.
The network layer is responsible for delivering IP datagrams across multiple networks (LANs), whereas the data link layer is responsible for delivering frames over the same network.
Each application uses either TCP or UDP in the transport layer and accordingly is identified either by a TCP port or a UDP port. Ports are just 16-bit integer numbers assigned to applications and maintained by the operating system. That means, in principle, you can assign any port number to your application in the range from 0 to 65535, but lower port numbers are reserved for well-known applications. Some of these reserved ports are listed in Table 10-1. The first column lists the protocols on which these applications are based.
| Service Protocol | Port Number | Transport protocol | Number |
|---|---|---|---|
| NETSTAT | 15 | UDP | Used to view a computer's inbound/outbound connections and the packet statistics. |
| FTP | 21 | TCP | File Transfer Protocol. Used to transfer files between two machines. |
| Telnet | 23 | TCP | Telecommunications Network Protocol. Used to work on a remote machine. |
| SMTP | 25 | TCP | Simple Mail Transfer Protocol. Used to carry email messages from client to server and from server to server. |
| DNS | 53 | UDP | Domain Name System. Resolves domain names to IP addresses. |
| TFTP | 69 | UDP | Trivial File Transfer Protocol. Thinned-out version of FTP, having no authentication, and no file system navigation at the remote machine. |
| HTTP | 80 | TCP | Hypertext Transfer Protocol. Provides basis for the World Wide Web. |
| POP3 | 110 | TCP | Post Office Protocol 3. Used by email clients to download email messages from email servers. |
| NNTP | 119 | TCP | Network News Transfer Protocol. Used to transfer (post, distribute, and retrieve) the Usenet messages on the Internet. |
| IMAP | 143 | TCP | Internet Mail Access Protocol. A popular alternative to POP3 with more features. |
| SNMP | 161 | UDP | Simple Network Management Protocol. Used to manage networks remotely. |
| NFS | 2049 | UDP | Network File System. Used to share files on a network. |
The protocol-to-port mapping for services is listed on your system in the /etc/services file, which is actually a symbolic link to the /etc/inet/services file. The link is provided for BSD compatibility.
The OSI model, as elegant as it is, has never been exactly implemented. Nevertheless, the closest working system we have is the Internet which is based on the TCP/IP model.
The TCP/IP Model
Partly because of the way the Internet evolved, the TCP/IP protocols were never developed with the OSI layering model (or any other model for that matter) in mind; instead, a model evolved along with the Internet. Now that we have these protocols functioning together, we can look back and organize them into conceptual layers, and call them based on, say, the TCP/IP or Internet layering model. But there was no such model in front of the designers of the Internet protocols to follow. Most of the experts agree on the comparison between the TCP/IP layering model and the OSI model depicted in Figure 10-2.
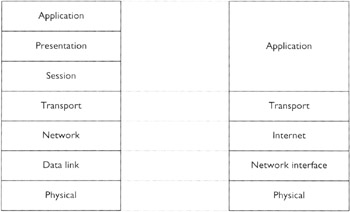
Figure 10-2: The five protocol layers of the TCP/IP layering model corresponding to the seven layers of the OSI model
The five layers of the TCP/IP layering model are listed here:
-
Layer 1: Physical. Layer I deals with the network hardware and corresponds to the physical layer in the OSI model.
-
Layer 2: Network Interface. This layer specifies how to organize data into packets called frames and how to address the machines in a LAN; it corresponds to the data link layer in the OSI model.
-
Layer 3: Internet. This layer specifies the format of data packets called IP datagrams and is responsible for delivering these datagrams across the Internet. This layer corresponds to the network layer in the OSI model.
-
Layer 4: Transport. This layer has protocols that specify end-to-end (application-to-application) communication and corresponds to the transport layer in the OSI model.
-
Layer 5: Application. This layer corresponds to layers 6 and 7 in the OSI model.
Conceptually, as shown in Figure 10-3, a message from a sender machine begins at the application layer and travels down through the successive layers of protocol software, goes across networks through routers, eventually arriving at the destination machine at the physical layer and traveling upward to the application layer.
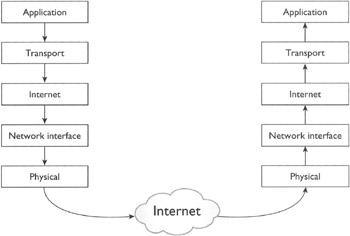
Figure 10-3: The conceptual path taken by a message as it travels through the Internet from an application on a sender machine to an application on the recipient machine
The protocol layers discussed in the OSI reference model and the TCP/IP layering model are summarized in Table 10-2.
| Layer | Protocols/Devices | Main Functionality |
|---|---|---|
| Physical | Hub, NIC, Repeater | Moves the bits of data from one device to another in form of specific signals. |
| Data link Network interface | Switch, Bridge | Organizes data into data packets called frames. Defines hardware (MAC) addresses. |
| Network Internet | Router IP, ARP, ICMP | Delivery of IP datagrams across networks. Organizes data into IP datagrams. Defines protocol (IP) addresses. |
| Transport | TCP, UDP | End-to-tend virtual connection. Defines ports, and optionally implements reliability. |
| Session | NFS, SQL | Creating sessions. |
| Presentation | MPEG, JPEG, UNICODE, ANSI | Presenting data in different formats. Encryption /decryption, compression/decompression. |
| Application | HTTP, FTP, NIS, DNS, LDAP, telnet, SNMP | Specifies applications used by the end user. |
| On the Job | Solaris 10 offers a completely rewritten TCP/IP stack. In previous versions of Solaris, TCP/IP across multiple CPUs was not very efficient and lagged behind the TCP/IP stack on Linux in performance. The Solaris 10 version of TCP/IP stack helps improve performance for all network applications, especially the web services. |
Berkeley Software Distribution (BSD) UNIX released in 1983 from the University of California, Berkeley, was the first operating system ever to have the TCP/IP suite implemented on it. Of course, the TCP/IP protocol suite (containing these layers) is implemented on and is part of your Solaris system, which in turn is a part of a LAN. What kind of LAN?
LAN Topologies
As you already know by now, TCP/IP runs on top of a variety of LANs. These LAN technologies can be grouped into a few categories based on the design of their cable layouts, called LAN topologies. A LAN topology basically determines the pattern used to connect the computers and other devices in the network to each other through cables or other media. Three main topologies are discussed here:
Bus Topology
As shown in Figure 10-4, computers in a network based on bus topology share a single main cable (hence the name bus), and each computer is attached to this cable by using its own individual cable called a drop cable. The ends of the main cable have terminators so that the signal is not reflected back. The disadvantages of this topology are that a single fault in the main cable can bring the whole network down, and it is difficult to troubleshoot.

Figure 10-4: Layout of the bus topology (all computers are attached to a single shared cable)
Another way of connecting computers in a network is to connect a computer directly to another computer rather than through a single shared cable. This is done in ring topology.
Ring Topology
As shown in Figure 10-5, each computer in a network based on ring topology is connected directly to its two neighbor computers—a predecessor and a successor. As a typical example of how a computer in a star topology network communicates with another computer, assume computer A in Figure 10-5 is sending a data packet to computer D. The data packet travels in the ring from A to B, B to C, and C to D. Computer D copies the data and resets a few specific bits in the packet to indicate whether it copied the data successfully or not and puts the entire data back onto the cable. The packet keeps going until it completes the circle and reaches A. Computer A then looks at the bits reset by computer D to determine whether D received the packet correctly. Based on its findings, it may decide to re-send the packet. The point is that each computer and each cable in the ring is a single point of failure. Although a network based on this topology is easy to troubleshoot, it is not fault tolerant and it is difficult to reconfigure.
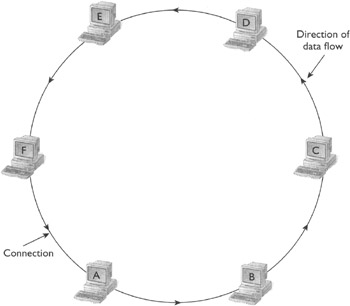
Figure 10-5: Layout of the ring topology (each computer is connected to its two immediate neighbors; the connection may be physical or logical)
If the computers in a ring are not physically connected to each other as shown in Figure 10-5, but nevertheless the data travels in a ring as shown in the figure, the ring is called a logical ring.
Ring networks are not currently in common use. A topology that is commonly used today is the star topology.
Star Topology
As shown in Figure 10-6, all computers in a network based on the star topology are connected to a central device such as a hub. Data from the sender goes to the recipient through the central point. The advantage of this topology is that new computers can be added to the network easily, and troubleshooting is relatively easy. It is fault tolerant in the sense that if a computer goes down or a cable connecting a computer to the central device goes down, the rest of the network still keeps functioning. However, the central device is the single point of failure.
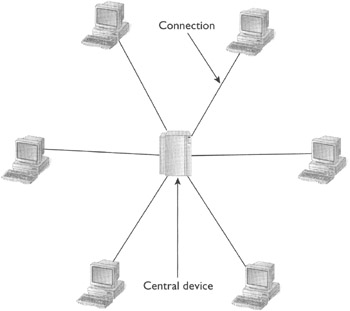
Figure 10-6: Layout of the star topology (each computer is connected to a central device)
Note that a topology refers to the pattern of how the computers in the network are connected to each other through media such as cable. It does not necessarily refer to the actual physical shape of the network. For example, in a star network, all the computers connected to the hub may reside on the same side of the hub, and a snapshot of the network may not depict it as star shaped.
Bus topology and star topology are used by a class of LANs called Ethernet networks, which are the most commonly used LANs.
Ethernet Networks
As you already know by now, the protocols (standards) at the data link layer describe the specific LAN (physical network) technologies and prepare the outgoing data for transmission on a medium, for example, by organizing the data into frames. These protocols also receive the incoming data and, if necessary, pass on what is inside the frame to the appropriate network/Internet layer protocol.
The most popular LAN technology is called Ethernet, which was originally invented in Silicon Valley, California, at Xerox Corporation's Palo Alto Research Center in the early 1970s and was later adopted by (and now controlled by) the IEEE. Several variations of the Ethernet standards, summarized in Table 10-3, exist; they vary primarily because of the varying physical layer specifications included in the Ethernet standards, such as cable type. As a result the bandwidth and the maximum segment length vary as well. The bandwidth is the maximum data transmission rate that can be achieved and often is limited by the physical properties of the medium. The segment length, also called maximum cable length, is the distance the signal can travel in the cable before it disperses. Devices called repeaters can be used to amplify the signals and hence increase the maximum segment length of a network.
| Ethernet Name | Cable Tybe | Bandwidth | Maximum Segment Length | Comments |
|---|---|---|---|---|
| 10Base5 | Coax | 10 Mbps | 500 meters | 0.5 inch in diameter. Also called Thicknet. Uses vampire taps to connect devices to cable. |
| 10Base2 | Coax | 10 Mbps | 185 meters | 0.25 inch in diameter. Also called Thinnet. Uses BNC connector. Popular choice for Ethernet over coax. |
| 10BaseT | UTP | 10 Mbps | 100 meters | Popular. Uses two pairs of Cat 3. |
| 100BaseTX | UTP | 100 Mbps | 100 meters | Popular. Uses two pairs of Cat 5. |
| 100BaseT4 | UTP | 100 Mbps | 100 meters | Uses four pairs of Cat 3. |
| l000BaseT | UTP | 1 Gbps | 100 meters | Gigabit Ethernet. Cat 5. |
| 10BaseF | Fiber optic | 10 Mbps | 500 meters to 2000 meters | Ethernet implemented over fiber optic. |
| 100BaseFX | Fiber optic | 100 Mbps | 412 meters | — |
| 1000BaseLX | Fiber optic | 1 Gbps | 550 meters to 5000 meters | — |
| l000BaseSX | Fiber optic | 1 Gbps | 220 meters to 5505 meters | — |
| FDDI | Fiber optic | 100 Mbps | 10 kilometers | — |
An Ethernet network has three main components: data packets, media, and media access (MAC) mechanism.
Data Packets
Data packets in data link layer are called frames. Each LAN technology has its own frame format. A frame, just like any other data packet, contains a data portion and a header portion. The header of a frame includes the MAC address of the source (sender) machine and the MAC address of the destination (recipient) machine. Data packets and addresses are described further on in this chapter. The frames travel from one computer to another on a LAN in the form of signals on a cable.
Cable Types
The cable types that you can use to build a network are described in the physical layer specifications included in the Ethernet standards. There are three main types of cable.
Coaxial Cables A coaxial cable (coax) contains two coaxial (one inside another) copper conductors separated by a layer of insulation and surrounded by an outer sheath. The signal travels through the inner conductor, and the outer conductor serves as the cable's ground. There are two types of coaxial cables: RG-58 standard, also called thick Ethernet (Thicknet), which is about 0.5 inch in diameter, and RG-8 standard, also called thin Ethernet (Thinnet), which is about 0.25 inch in diameter. A drop cable from a computer connects to the Thicknet cable by using the so-called vampire tap, which has a meta-tooth that sinks into the cable—hence the name vampire tap. Thinnet uses the Bayonet-Neil-Concelman (BNC) connector. Both types of coaxial cable are used in the bus topology, in which the coaxial cable is the cable shared by all the computers connected to the network. The two ends of the shared cable use terminators to terminate the signal and hence to eliminate the problem of signal bounce, called echo effect. Although coaxial cable is still used for the television network, it is no longer popular as a LAN medium, for which twisted-pair cables are commonly used.
Twisted-Pair Cables A twisted-pair cable has a multiple number of individually insulated copper wires (conductors) twisted together in pairs and surrounded by a sheath. There are two main kinds of twisted-pair cables: shielded twisted-pair (STP), which has a metallic shield around the protective sheath and is used in token-ring networks, and unshielded twisted pair (DTP), which has no outer shield and is used in star topology networks. The UTP cables are graded according to the following categories (also called cats):
-
Category 1. A cable in this category has two twisted pairs (four wires) and can only carry voice. This is actually the telephone cable used in the Plain Old Telephone Service (POTS). It uses the RJ-11 connector.
-
Category 2. A cable in this category has four twisted pairs (eight wires) and is suitable for a bandwidth of up to 4 Mbps. The UTP cables with four pairs use RJ-45 connectors.
-
Category 3. A cable in this category has four twisted pairs (eight wires) and is suitable for a bandwidth of up to 10 Mbps. The Fast Ethernet protocol called 100Base-T4 was designed to use this category to achieve a bandwidth of 100 Mbps. This is made possible by using all the four twisted pairs in the cable, whereas most of other protocols use only two twisted pairs.
-
Category 4. A cable in this category has four twisted pairs (eight wires) and is suitable for a bandwidth of up to 16 Mbps. It is used in token-ring networks.
-
Category 5. A cable in this category has four twisted pairs (eight wires) and is suitable for a bandwidth of up to 100 Mbps. It is in common use today.
-
Category 6 (or 5e). A cable in this category has four twisted pairs (eight wires) and is suitable for a bandwidth of up to 1 Gbps. It is used in Giganet Ethernet.
Fiber-Optic Cables Coaxial and twisted-pair cables provide a segment length from 100 to 500 meters, because after traveling this distance the signal weakens (disperses) so much that it cannot be read accurately. Fiber-optic cable provides the solution to this problem, because it carries a light signal through a glass fiber that can travel up to 120 kilometers before weakening to a point at which it cannot be read.
These cable types are described in Table 10-3. Note that most Ethernet networks use only two pairs in the twisted-pair cable: one for receiving the data and the other for sending it.
Once we have a frame and the cable, we need a mechanism to access the cable in order to send the frame.
Media Access Mechanism: CSMA/CD
The issue of accessing the media for sending data arises because there is more than one computer on the network that would like to send data. In an Ethernet network with a shared medium, there is no central controller to coordinate the transmission from different computers and hence to avoid the traffic collision. The mechanism used for coordinating data transmission is called Carrier Sense Multiple Access (CSMA) and Collision Detection (CD); therefore, Ethernet networks are also called CSMA/CD networks.
To understand the CSMA/CD mechanism, consider an Ethernet network with a shared coaxial cable (Thicknet) as shown in Figure 10-7. Each computer is connected to the shared cable with a transceiver. Computer B wants to send data to computer D, so the transceiver of computer B will determine whether it can receive signal from the shared cable. This is called carrier sensing or listening to the cable. The computer will wait until the transceiver confirms that there is no signal in the cable; then it will start transmitting the data. As shown in Figure 10-7, the signal from computer B will propagate to both ends of the shared cable. The transceiver of each computer on the network will sense the signal; the destination address in the frame header will be compared with the MAC address of the computer; and, if there is a match, the data will be accepted and processed by the computer. All computers that want to send data perform carrier sensing before accessing the cable on their own (without a central controller); hence the name carrier sense multiple access.
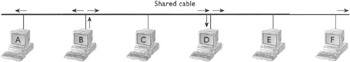
Figure 10-7: Flow of data across a shared Ethernet cable in the bus topology
It can happen that at least two computers are sensing the cable, decide simultaneously that the cable is available, and start transmitting as a result. In this case the signals from the two computers will collide with each other in the cable. In other words, the possibility of a collision is built into the CSMA/CD mechanism. The philosophy behind this mechanism is to let the collision happen but if it does, detect it and recover from it. The transmitting computer detects the collision by comparing the incoming and outgoing signals at the transceiver. If the two (incoming and outgoing) are different, the collision has occurred. That means that the transmitting computer should still be transmitting when the distorted signal (as a result of collision) arrives at the transceiver of the transmitting computer. This is the origin of the requirement of a minimum Ethernet frame size.
After the two computers have detected a collision, the mechanism requires that each of the two computers select a random delay before attempting to re-transmit. If the delay chosen by the two computers happens to be the same, the collision will happen again. Every time this happens, each participating computer doubles the range from which to select the random delay, thereby reducing the possibility of collision. This recovery mechanism is called exponential backoff algorithm.
On a fiber-optic or UTP network, on which a computer has no transceiver, the computer senses the signal on a receive wire, and it assumes that a collision has occurred if it detects signals on both the receive and transmit wires simultaneously.
In a bus topology, the computers are directly connected to a single shared cable. But how do you connect a computer to a cable? In other words what else (other than cables) do we need to connect computers on a network? The answer is that we need network connectivity devices.
Network Connectivity Devices
A computer network is there to connect the computers. A computer connected to a network is called a computer, a machine, or a host. There are several devices other than computers, called network connectivity devices, that help connect different entities on the network (computers, printers, and the like) to one another. As a system administrator, you should be familiar with the various types of network connectivity devices. Some of them are described here.
Network Interface Card (NIC) As the name suggests, the network interface card provides an interface between the computer and the network media in order to connect a computer to the network. In its most common implementation, a NIC is an expansion card that fits into an expansion slot of the computer. However, a NIC can also be built into the computer's motherboard. It provides physical, electrical, and electronic connection for the computer to the network media. In other words, the data travels from the computer to the network and from the network to the computer through this device. On an Ethernet network, a hardware address is burned into a NIC, but the IP address is not. That means if you change the NIC of your computer, the hardware address of your machine changes. A machine may have more than one Ethernet card to connect to more than one network. A router is an example of such a machine. Although the MAC address assigned to different Ethernet cards by the manufacturers may differ, the Solaris system derives the MAC address from the NVRAM chip. Therefore, all the NICs on a Solaris machine will be using the same MAC address. This is not a problem as long as the cards are connected to different networks.
Hub A hub serves as the central device in a network that is based on the star topology. Each computer is connected to a different port on the hub. A hub receives signal on one port and repeats it on all other ports. If it simply provides the electrical connection between ports, it is called a passive hub, and it is typically unpowered. If it amplifies the signal it receives while repeating it on multiple ports, it is called an active port, and it is powered. Why do the hubs repeat received signal on all the ports even if it is supposed to go to only one computer connected to a specific port? That is because hubs have no awareness of hardware (MAC) addresses.
Repeater Repeaters are devices that can be used to amplify or to repeat an existing signal. Each cable type limits the maximum segment length (the maximum cable length between any two computers) of a network. This is because a physical signal can travel only so far before it disperses. Repeaters can be used to extend the segment length of a network by amplifying the weakening signals. As you have seen, a hub simply acts as a multiport repeater by repeating the received signal on multiple ports. A repeater, just like a hub and a NIC, operates at layer 1 (the physical layer).
Transceiver In a thick Ethernet network, each computer is connected to a single shared coaxial cable through a device called a transceiver, which can transmit data (signal) into the cable and receive data from the cable at the same time, hence the name transceiver. This capability of this device allows it to detect signal collision in the cable when it is transmitting data from the computer into the cable.
Switch As opposed to a hub, a switch repeats a received signal only on a port to which the intended recipient of the data is connected. When a switch is powered up, it starts off acting like a hub. However, with each frame it receives it learns the hardware address of the sender from the frame header and starts making a table in which each entry matches a port with the hardware address of the computer attached to that port. The switch then uses this table to repeat a received message only on the port to which the intended recipient is connected. Consequently, a switch knows hardware addresses whereas a hub does not. Because it has to know hardware addresses, a switch operates at layer 2 (data link layer), which defines hardware addresses.
Bridge Consider two networks based on the star topology implemented by a hub with one hub on each network. If you connect these two hubs with a cable, the two networks act like one big network—that is, a signal received from a sender will be repeated on all the ports on both hubs. Now assume that we connect the two hubs together through a device called a bridge. The bridge will stop all the traffic from a sender on one network (segment) from going to the second network (segment) if the intended recipient is not on the second segment. Therefore, a bridge can be used to combine two network segments together, or to split a network into two segments. Note the difference between a bridge and a switch: a bridge divides a network into two segments and stops the traffic from going into the wrong segment, whereas a switch stops the traffic from going to the wrong machine. Because it has to know hardware addresses, a bridge operates at layer 2 (the data link layer).
Router Whereas hubs, switches, and bridges manage the traffic inside a network, a router manages the traffic between two networks. A router receives a frame from a computer (or another router), retrieves the datagram from the frame, figures out (possibly with the help of the routing table) the recipient (which may be a local host or the next hop router), puts it into a new frame, and sends it. Because routers deal with IP datagrams, they are aware of IP addresses whereas bridges, switches, and hubs are not. Note that some of the switches (called layer-3 switches) also have the functionality of a router, which sometimes creates confusion about the term switch. Because it has to know IP addresses, a router operates at layer 3 (the network/Internet layer).
Gateway A gateway is a device (hardware, software, or a combination) that connects two different network environments by acting as a mediator. For example, a gateway may convert the traffic from one LAN protocol into another. An email gateway translates between two different email protocols so that the email servers based on those protocols can communicate with each other through the email gateway. A gateway can be regarded as a protocol translator and it may be operating at any layer depending on which protocols it's dealing with.
| On the Job | Do not confuse the TCP/UDP ports with the physical ports. The TCP/UDP ports are the software ports (the numbers), whereas the physical ports are the hardware ports used for physically connecting devices such as ports on a hub or ports on the back of your computer. |
To sum up, a computer is connected to the network through a network interface, and each network interface must have an address in order to participate in network communication. This is analogous to your having your phone number, email address, and home address so people can communicate with you by using any of these addresses.
Network Addressing
A basic condition for network communication is that each machine on a network must, have a unique address. On a LAN a machine is uniquely identified by its MAC address, and on the Internet a machine is uniquely identified by its IP address.
MAC Addresses
Media access (MAC) address is the address (a number) used to uniquely identify a computer on a LAN. It is also called a physical address, a hardware address, or an Ethernet address (on an Ethernet network). The MAC address on an Ethernet LAN, the Ethernet address, is a 48-bit number. Blocks of Ethernet addresses are purchased by the vendors from the IEEE and burned into the interface cards. That means that if the interface card of a computer changes, its MAC address will change. In general, network interface hardware recognizes three kinds of addresses:
-
Unicast address. This is the unique address of a computer on a LAN.
-
Broadcast address. This is the address used for broadcasting messages on a network. By convention, all 1's in an address make it a broadcast address. For example, if the destination hardware address in an Ethernet frame carries 48 bits, each set to 1, the frame will be delivered to and processed by all the computers on the LAN.
-
Multicast address. This is the address that is used to broadcast a message to a subset of the computers on a network, and the subset is called a multicast group. When the destination hardware address in the frame header is a multicast address, all the computers that have been assigned that address will accept and process the frame.
A MAC address is a layer-2 address and cannot uniquely identify a machine on the Internet.
IP Addresses
An Internet Protocol (IP) address is used to uniquely identify a machine on the Internet. IP (version 4) addresses are 32-bit numbers. In other words, think of the Internet as a big network (like a LAN) on which each machine is uniquely identified by a 32-bit integer. To understand IP address, note the following points:
-
Each IP address has a structure—that is, it's composed of two parts, netid and hostid. All the computers on the same network (e.g., LAN) have the same netid but different hostids.
-
The four bytes of an IP address are split between netid and hostid. The different ways we can split this address space between netid and hostid groups IP addresses into five categories called classes: class A, class B, class C, class D, and class E.
-
The class of an IP address is identified by at most the first 4 bits of the address.
| On the Job | In order to route a datagram on its way from source to destination, the routers use only the netid of the destination IP address. Using the network address and not the host address of a destination helps to reduce the size of the routing tables. |
In a class A address, the first byte (8 bits) belongs to the netid and the last three bytes belong to the hostid. In a class B network, the first two bytes belong to the netid, and the last two bytes belong to the hostid. In a class C network, the first three bytes belong to the netid and the last one byte belongs to the host ID. The class information is coded in the first few bits of an IP address. Look for the first appearance of a 0 bit in the address. It appears at the first (most significant) place in a class A address, at the second place in a class B address, and at the third place in a class C address. This information is summarized in Table 10-4.
| Class | netid | hostid | Fixed bits |
|---|---|---|---|
| A | First one byte | Last three bytes | First bit: 0 |
| B | First two bytes | Last two bytes | First 2 bits: 10 |
| C | First three bytes | Last one byte | First 3 bits: 110 |
| D | — | — | First 4 bits: 1110 |
| E | — | — | First 4 bits: 1111 |
Class D addresses are multicast addresses, and class E address space is reserved for future use. Note that the first few bits (one for class A, two for class B, and three for class C) of the first byte of an IP address are reserved to identify the class.
The netid part of an IP address of a machine identifies the network of the machine to which it is connected. The common way of presenting IP addresses is called dotted decimal notation. In this notation, an IP address is written in four decimal integers separated by a dot, where each integer is the decimal value of the corresponding byte in the address. For example, consider the following IP address in binary format composed of four bytes:
10000100 00011100 00000011 00010100
Convert each byte into a decimal number individually and separate the decimal number by a dot and you obtain the following IP address in dotted decimal notation:
132.28.3.20
The network address is the IP address with the hostid replaced by all 0s. How would you know which bytes belong to the hostid? The bytes that do not belong to the netid belong to the hostid. But which bytes belong to the netid? That you determine from the class of the IP address. The first 3 bits of the IP address in our example are 100. The first 0 appears at the second place, hence it is a class B network address; as a result; the first two bytes belong to the netid. Therefore, the network address of the network to which the machine with this IP address (132.28.3.20) is connected is:
132.28.0.0
In class A addresses, the first byte belongs to the netid, and the first bit of the first byte is always 0. Therefore, the lowest non-zero netid is 00000001 (or 1) and the highest netid is 01111111 (or 127). However, the netid 127 is reserved for what is called a loopback address (used to test the TCP/IP stack on a machine), so the valid highest netid is 126. Therefore, the range of class A network addresses is: 1.0.0.0 to 126.0.0.0. Similarly, you can calculate the ranges for network addresses for the other classes, as listed in Table 10-5.
| Class | Lowest Network Address | Highest Network Address |
|---|---|---|
| A | 1.0.0.0 | 126.0.0.0 |
| B | 128.1.0.0 | 191.255.0.0 |
| C | 192.0.1.0 | 223.255.255.0 |
| D | 224.0.0.0 | 239.255.255.255 |
| E | 240.0.0.0 | 255.255.255.254 |
It is only the network addresses that are assigned by the Internet Corporation for Assigned Names and Numbers (ICANN). The network administrator is free to choose the hostid for a machine in the network. As you have already seen, all bits in a hostid set to 0 represent a network address, Furthermore, all bits in the hostid set to one represent a broadcast address. Therefore, an IP address with the hostid of all 0's or all 1's is not a valid IP address. Now let's do another exercise to understand the IP addresses. Consider again the IP address 132.28.3.20 in our example, and ask What is the maximum number of computers that can be connected to a network to which this computer with IP address 132.28.3.20 is connected? We have already determined that it is a class B network; therefore, the last two bytes belong to the hostid. That means you have 16 bits to make a hostid. Each hostid must be unique. How many unique numbers can you make with 16 bits? That would be 2^16 = 65536. Because all 0's and all 1's are not allowed in a hostid, the maximum number of machines that can be connected to a class B network is 65534.
What we have discussed is called the original IP addressing scheme, or a classfull addressing scheme, in which one network address is assigned to one LAN and each LAN has a class. In practice, these days, several LANs may be hidden behind one network address assigned by CANN. This is called subnetting and is accomplished by locally allotting a few bits from the hostid to represent several LANs for a given network address. However, discussion of this issue is beyond of the scope of this book.
Now that you know how the original IP addressing scheme works, see the next page for some practical scenarios and their solutions.
Having two addresses (IP and MAC) for a machine connected to a network may confuse a beginner. The right question to ask is How do we use both of these addresses? The point to remember is that an IP datagram is always addressed by an IP address, and a frame is always addressed by a MAC address. These addresses are resolved into each other when necessary.
| SCENARIO & SOLUTION | |
|---|---|
| One of the machines connected to a TCP/IP network has an IP address of 195.23.3.16. What is the network address of this network? | The first byte 195 is 11000011 in binary. The first zero appears at the third significant place. So, it's a class C network, which means the first three bytes belong to the netid. Therefore, the network address is 195.23.3.0. |
| What is the maximum number of computers you can connect to this network? | There are 8 bits available for the hostid, which cannot contain all 0's and all 1's. Therefore, the maximum number of computers = 2^8-2 = 254. |
| What is the IP address on this network for broadcasting an IP datagram? | All 1's in the hostid makes the broadcast address 195.23.3.255. |
Address Resolution
You can build as many layers of protocols as you want, but ultimately the data will travel in some medium; it will always be delivered on a LAN in the form of a frame, and the frame is addressed by a hardware address. Consequently, it is always a frame that is delivered on a LAN. However, a frame cannot travel across networks. What travels across networks is the IP datagram, which is addressed by the IP address of the ultimate destinations and the original source. The IP datagram from original source to ultimate destination travels from router to router (i.e., from network to network) inside frames. The key point is that a router has more than one network interface—that is, it is connected to more than one network. It accepts the frame on one network, takes the IP datagram out of the received frame, puts it into another frame, and delivers it to the next router on the other network to which it is also connected. The new frame is compatible with the hardware of the network on which it will be delivered to the next router. This procedure is repeated until the datagram reaches its ultimate destination.
Each router on the way determines the IP address of the next router from the routing table, but to send the frame it needs the MAC address of the next router. So it broadcasts an address resolution protocol (ARP) message, which basically says Any machine on this network whose IP address is this, please give me your MAC address. The next router responds to the sending router with its MAC address. This is how an IP address is resolved to a MAC address by using ARP.
Not just a router but any computer on a network can run ARP; as it learns the hardware addresses of other computers, it enters them into a table so that the next time it wants to send something to a computer it does not have to run ARP again. Because an ARP request is a broadcast, it consumes significant bandwidth. You can view the ARP table (the mapping of IP addresses to MAC addresses) maintained by a computer by executing the arp command on that computer.
Finally, note that the addresses are assigned to network interfaces, and a computer may have more than one network interface, which means more than one (hardware and IP) address. Consider an address as the address of a network connection for a computer. Computers need addresses so that they can send and receive data packets, also called network packets.
Network Packets
Computer networks are called packet-switched networks, because instead of transferring data as a string of bits, they deliver it organized into blocks called packets. In other words, a packet is a unit of delivery. A packet has two main parts—data and header, which is information about data—that is, how to interpret the data, who is the sender, where the data is going, and so forth.
Understanding Packets
Each layer in the protocol layering has its own view of the data packet. As shown in Figure 10-8, each layer on the sender machine gets a packet from the upper layer, prepends its own header to it, and passes it down to the next layer. As shown in Figure 10-9, each layer on the receiver machine does exactly the opposite; it receives a packet from the lower layer, removes the header (that the same layer prepended on the sender machine), and passes the packet on to the upper layer. Each layer has its own name for the packet—for example, IP datagram for the network layer and frame for the data link layer.
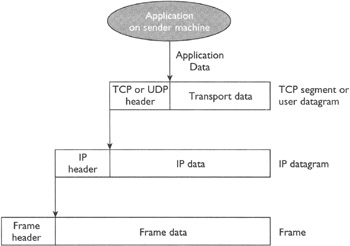
Figure 10-8: Data encapsulation on the sender machine (a packet in a layer becomes the data part for the packet in the lower layer)
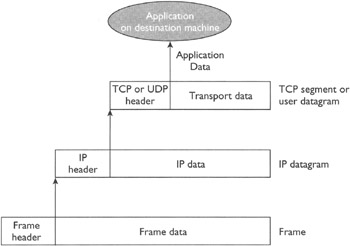
Figure 10-9: Data decapsulation at the recipient machine (a layer removes its header before passing the packet to the upper layer)
As listed here, each layer has a different name for its packet:
-
TCP segment and UDP datagram. A data packet in the transport layer is called a TCP segment if it is composed by TCP, and it is called a user datagram or UDP datagram if it is composed by UDP. The most important header fields are the source port number and the destination port number, which uniquely identify the communicating applications at the sender machine and the destination machine, respectively. The TCP header has additional fields to implement reliability, such as acknowledgment number.
-
IP datagram. A data packet in the network/Internet layer composed by IP is called an IP datagram. The most important fields in the IP datagram header are the source IP address, the destination IP address, and time to live (TTL). The source IP address and destination IP address are the addresses of the sender machine and the recipient machine, respectively. The TTL is a number that represents the maximum number of routers that a datagram can hop before it bites the dust. This is basically a protection against the datagrams becoming lost on the Internet (for example, put into loops), not going anywhere but wasting bandwidth.
-
Frame. The data packet in the data link layer is called a frame. Its format depends on the hardware network technology being used by the LAN. The most important header fields in an Ethernet frame are source hardware address, destination hardware address, and cyclic redundancy check (CRC). The CRC field is calculated (from the content of the frame by using an algorithm) at the source machine and at the destination machine; if the two values are different, the data is probably corrupted.
Now that you have an understanding of network packets, you need to know how to monitor them on your Solaris system.
Monitoring Packets
You can view the packet statistics on your machine by using the netstat command. For example, issue the following command to display the packet statistics on your machine that has the IPv4 TCP/IP stack installed on it:
netstat -f inet
The output will look like the following:
Local Address Remote Address Swind Send-Q Rwind Recv-Q State ---------------------------- host49.850 host19.nfsd 49640 0 49640 0 ESTABLISHED host49.38063 host19.32782 49640 0 49640 0 CLOSE_WAIT host49.38146 host41.43601 49640 0 49640 0 ESTABLISHED
If you have trouble accessing another machine on the Internet or on your own network, you can use the ping (packet Internet groper) command, a utility based on Internet Control Message Protocol (ICMP), to determine whether the remote host is running or is dropping packets. You can issue the ping command by using the following syntax:
ping <host> [<timeout>}
The <host> argument specifies the remote host name and the <timeout> argument is the time in seconds for the ping command to continue trying reaching the host. The default value is 20 seconds. The ping command has several options. As shown here, you can use -s option to determine whether the remote host is dropping packets:
ping -s <host>
The output of this command will look like the following:
PING host1.domain6 : 56 data bytes 64 bytes from host1.domain6.COM (197.17.21.63): icmp_seq=0. time=70. ms 64 bytes from host1.domain6.COM (197.17.21.63): icmp_seq=1. time=72. ms 64 bytes from host1.domain6.COM (197.17.21.63): icmp_seq=2. time=75. ms 64 bytes from host1.domain6.COM (197.17.21.63): icmp_seq=3. time=73. ms 64 bytes from host1.domain6.COM (197.17.21.63): icmp_seq=4. time=73. ms 64 bytes from host1.domain6.COM (197.17.21.63): icmp_seq=5. time=72. ms ^ ——host1.domain6 PING Statistics—— 6 packets transmitted, 6 packets received, 0% packet loss round-trip (ms) min/avg/max = 72/73/75
These statistics indicate whether the host has dropped packets. Note that depending on the <host>, the command may involve a network other than your network. In case the ping command fails, you can check the status of your network by using the netstat and ifconfig commands.
From the netstat command you know that the packets are being exchanged, and if you see a problem in communication, you can use the ping command for trouble-shooting. Now, suppose you get more ambitious and want to snoop into a packet. In technical terms, you want to monitor the data transfer by snooping into headers of the packets at various layer levels. You can do that by using the conveniently named snoop command. Without any specified option, only the application layer information is displayed; for example, for an NFS packet, only the NFS information will be displayed. However, you can turn on the appropriate verbose mode to receive the information about the UDP datagram, IP datagram, or frame. For example, if you want to inspect the telnet traffic coming to your system (assuming that the telnet application runs on TCP port 23), you would issue the following command:
snoop -v tcp port 23
This will start displaying the information from the TCP header, the IP header, and the frame header of packets from or to the first non-loopback interface of your machine. To halt the process, press CTRL-C.
You can also use the host names to capture the traffic between two hosts as in the following command:
snoop <hostName1> <hostName2>
| On the Job | You should use the snoop utility frequently to become familiar with normal system behavior. For analyzing packets carefully, you can capture the output of the snoop command in a file by specifying the file name as a command argument. For example, the following command will save the output of the snoop command in the /tmp/snoopDump file:
snoop /tmp/snoopDump |
By now, you know that the hardware and the IP addresses of a machine define the network identity of the machine. The hardware addresses are burned into the interfaces, but the IP addresses have to be assigned. In other words, the network interfaces must be configured.
Configuring and Managing IP Network Interfaces
Configuring network interfaces basically means assigning IP addresses to them and defining some parameters such as whether the interface is up (online) or down. You get the first opportunity to configure the interfaces on your machine during the Solaris installation process. The installation, program configures the first interface, and if it finds additional interfaces, it prompts you to configure. You can configure them then, or you can choose to configure them later. The configuration information is saved in a set of files that are used to configure the interfaces every time you boot the system.
Configuring an IP Network Interface at Boot Time
Every time you boot a Solaris system, the ifconfig utility is used to configure the interfaces; it uses the information from the configuration files described in the following list:
-
The /etc/nodename file. This file contains one entry. For example, a system with the host name tomdelay will have one entry in the /etc/nodename file: tomdelay.
-
The /etc/hostname.<interf ace> file. This file represents a physical interface to the system. Each functional (configured) physical interface on the machine must have its own /etc/hostname.<interface> file. The <interface> specifies the physical interface name which can be determined by using the prtconfig or sysdef commands. The names look like <type><n>, where <type> specifies the interface type and <n> specifies the interface number of a given type. For example, your machine may have two interfaces with names hme0 and hme1. The host name files corresponding to these interfaces will be: /etc/hostname.hme0 and /etc/hostname.hme1, respectively. What should be inside each of these files? Again, just one entry, the host name or the IP address of the host. For example, the /etc/hostname.hme0 file may have an entry tomdelay0, and the /etc/hostname.hme1 file may have the entry tomdelay1. These files contain the information that the interfaces hme0 and hme1 are installed on the machine and are associated with the host names tomdelay0 and tomdelay1, respectively.
-
The /etc/inet/hosts file. Now you have one file for each interface on your machine that contains the host name (or the IP address information) associated with that interface. Maybe you want to give a nickname to the host, or maybe you want to know the host names (and IP addresses) of the other machines on the system. The /etc/inet/hosts file let you organize that information. Each entry in this file contain the following fields:
-
<IPAddress>. Contains an IPv4 address corresponding to a host name, which in turn corresponds to a physical interface.
-
<hostname>. Contains the host name corresponding to this IP address.
-
<nickname>. Nickname for this host.
-
#. Comments
-
-
The /etc/inet/ipnodes file. This file stores both IPv4 and IPv6 addresses. If you need to add (or change) the IPv4 address of your Solaris 10 system, you must make this change to both the hosts and the ipnodes files. If you are going to add an IPv6 address, you need to edit only the ipnodes file.
As an example, following are the contents of the /etc/inet/hosts file that exists on the machine with host names tomdelay0 and tomdelay1, corresponding to two interfaces that this machine has.
# Little Network on the Hill # 127.0.0.1 localhost # 192.168.2.1 tomdelay0 tomy0 #This machine 192.168.2.2 tomdelay1 tomy1 #This machine # 192.168.2.3 nancy # Nancy's machine. No nick name. 192.168.2.4 hillary smart # Hillary's machine 192.168.2.5 barbara boxer #This is Barbara's machine
The first entry corresponds to loopback address 127.0.0.1, which does not belong to any real physical interface and is used only to test TCP/IP installation on the machine. The entries with IP addresses 192.168.2.1 and 192.168.2.2 belong to the machine on which this file resides. The other entries with IP addresses 192.168.2.3, 192.168.2.4, and 192.168.2.5 belong to other machines on the network.
The /etc/inet/hosts file on your system needs entries about other machines only if the network is using the local files for the name service. Usually the network uses the NIS and DNS name services, which maintain host names and addresses on one or more servers. You will learn more about this in Chapter 11.
| On the Job | During the installation process, the Solaris installation program creates the /etc/hostname.<interface> file for the first interface that it finds during the installation. If the installation program finds additional interfaces, you will be prompted to configure them. You can choose to configure them then, or you may postpone it until later. |
The ifconfig command configures each interface on the machine during boot time by using the corresponding configuration files. What if you want to change the configuration after booting, or you want to configure a new interface? You can do that as well with the ifconfig command.
Monitoring IP Network Interface Configuration
As you know by now, the ifconfig command configures each network interface at boot time. You can also use the ifconfig command manually to monitor the interface configuration after the system has been booted. Monitoring includes discovering the configuration information and changing the configuration. In other words, you can use the ifconfig command to manually assign an IP address to an interface and to manually configure the interface parameters.
By using the ifconfig command, you can get the following information about the interfaces:
-
Device names of all interfaces on the system
-
IP addresses assigned to an interface
-
Whether an interface is currently configured or not
For example, to get information about all the interfaces, issue the ifconfig command with the -a option, as shown here:
ifconfig -a
It will display information about each interface, including the interface name, its hardware address, and its IP address. It will also tell you whether the interface is up (meaning configured and online), or down (meaning shut down). You can obtain information about a particular interface by specifying its name, say hme1, as shown here:
ifconfig hme1
If the interface is down, you can bring it up by issuing the following command:
ifconfig hme1 up
On the other hand, if it is up and you want to shut it down, you can issue the following command:
ifconfig hme1 down
To assign (or change) an IP address to an interface, you can issue the ifconfig command in the following format:
ifconfig <interfaceWame> <ipAddress>
<interfaceName> specifies the interface name such as hme1. and <ipAddress> specifies the IP address to be assigned, such as 192.168.2.3.
Exercise 10-1: How to Monitor Packets by Using the snoop Command
To monitor network packets by using the snoop command, perform the following steps:
-
On your local host machine, become superuser.
-
You can use the snoop command without any argument to obtain the packet information from the first non-loopback interface, or you can specify an interface by its IP address. To find the IP addresses assigned to the interfaces, you can issue the following command:
ifconfig -a
-
Issue the snoop command by specifying the file as an argument:
snoop /tmp/snoopDump
This will capture the packet information and store it into the file /tmp/snoopDump.
-
To display information about a specific interface of your choice, specify its IP address in the command argument. For example, the following command will display packet information from the interface with IP address 192.168.5.7:
snoop 192.168.5.7
-
Once you issue the snoop command, it starts capturing the information about the packets to and from the specified interfaces. To terminate the process, press CTRL-C.
Now we have computers connected to the network through their interfaces, and the interfaces are all configured. Why would we go to all that trouble? Well, either to share or to use the shared resources, and resources are shared and used by offering and using network services.
EAN: N/A
Pages: 168