IP 101
| [ LiB ] |
IP 101
Intellectual property is one of the United States' main exportsevidence, some would say, that the government achieved its goals in enacting the laws that protect such property.
Congress created laws governing intellectual property that create four major classes: trade secrets, copyrights, trademarks, and patents.
The animating principles behind these laws is threefold:
To encourage innovation by allowing a creator to control and reap the rewards of a creation;
To grant few monopolies in intellectual property, which stifle innovation; and
To protect consumers from brand confusion, where one party's goods are confusingly similar to another's.
Table 5.1. IP Categories and Basic Facts
| Trade Secret | Trademark or Service Mark | Copyright | Utility Patent | |
|---|---|---|---|---|
| What is Protected | Processes, concepts, ideas, software, documents, contract terms, more. | Words, names or symbols, character design. | Computer software, audiovisual elements, music, art, more. | Ideas and concepts made tangible . |
| Requirements | Valuable to competitors , not generally known, secrecy . | Identifies source of goods. | Originality. | Novel and unobvious. |
| How rights are acquired . | Maintenance of secrecy. | Minimal rights acquired by use; federal protection through USPT registration, which requires use or intent to use. | Minimal rights acquired at time of creation; registration through Copyright Office recommended to prove ownership, required to sue for infringement. | Registration with USPTO. |
| Term of Protection | So long as secrecy preserved. | Unregistered marks have minimal protection as long as used. Federally-registered marks: 10 years with right to rene for 10 year terms in perpetuity if mark in use. | Owned by person: life of author + 70 years. Owned by company: lesser of 95 years from the date of publication or 120 years from the date of creation. | 20 years from filing. |
| Infringement | Disclosure or use by party with duty not to disclose or use. | Using mark that creates likelihood of confusion as to source of goods. | Duplication or substantially similar work. | Making, using, selling a de vicecoming within the scope of any patent claim. |
The following is a discussion of United States intellectual property law. Protecting your property abroad is discussed in the section "Protecting Your Assets: Enforcement: International Considerations."
Trade Secrets
Trade secrets give companies a legal right to the secrecy of certain kinds of information. This offers an alternative or supplement for a company that either (i) prefers not to pursue other forms of protection for any number of reasons (cost, disclosure requirements, time and energy) or (ii) fears that the information would not qualify for other forms of protection. For example: copyrights cannot protect ideas and processes; trade secrets can.
Trade secrets protect the confidential information a business collects and creates to enable it to compete . The classic legal example of a trade secret is the formula for Coca-Cola. In game development, trade secrets can run the gamut from source code to contract terms or design documents.
Trade secrets can be combined with other protections like copyrights or patents to offer the maximum level of protection. For example, source code can be registered for a copyright and maintained as a trade secret.
Only certain people have a legal duty to maintain your trade secrets. If a competitor overhears one of your employees chatting to another about a trade secret and the competitor then exploits that information, you have recourse against your employee, but probably not against the competitor who has no obligation to maintain confidentiality of your trade secrets if legally acquired. This reality leads to two requirements of any good trade secret protection program:
-
Creating that legal duty wherever necessary through the use of agreements.
-
Establishing systems of physically protecting the trade secret information.
Trade secret law varies from state to state and country to country, so local counsel is required. A discussion of protecting trade secrets abroad follows in the "Protecting Your Assets: Enforcement: International Considerations" section.
What is a Trade Secret
A trade secret is any information like a formula, compilation, program, method, process, technique, or the like that:
-
Gives a business a competitive advantage.
-
Is not generally known by the company's current or potential competitors and cannot be discovered through legitimate means.
-
Is the subject of the company's reasonable secrecy efforts.
A trade secret can be protected forever as long as each of the above criteria is met. This is one reason some companies elect trade secret protection over patents to protect some IP: the content of patents is made public and expires after 20 years. Imagine if Coca-Cola had patented its formula instead of using trade secrets: it would have lost its primary asset to the public domain years ago.
Competitive Advantage
A trade secret can protect any information that gives the company a business advantage, assuming the information also meets the other two criteria of secrecy efforts and general unavailability of the information. Pretty much anything you don't want other companies to knowobject code, program structure and concepts, results of your QA, business development plans, research and development in progress, project management processes, and so oncan qualify for trade secret protection.
Not Publicly Known
Trade secret protection is not available for information that is publicly or generally available to competitors or customers. This can include:
-
Any materials the company releases without an NDA and the appropriate notices, such as a design or technical document.
-
Information released accidentally , such as a document left on an airplane or overheard from an employee at a restaurant.
-
Data that can be figured out from a released product (in other words, if a product can be reverse engineered, the product can lose its trade secret protection). IP 101
Figure 5.1. Trade secrets, such as the Coca-Cola formula, may be protected indefinitely.

Efforts to Maintain Secrecy
Trade secret protection is also not available for information that the company has not taken reasonable efforts to protect. What is a reasonable effort? Courts have looked to:
-
How valuable the information is
-
The company's resources available to protect its trade secrets and whether they were used
-
How difficult and expensive it would be for a competitor to develop the information
-
How widely the information is known within and without the company
How Do I Qualify for and Obtain Trade Secret Protection?
Unlike the other intellectual property categories, trade secrets do not have to be registered with a government entity to be enforceable. However, for information to meet the trade secret test (gives a competitive advantage, is not generally known or available, is reasonably protected by the company), a company will need to put some thought into information and disclosure processes. The company's trade secret protection program should be developed with your attorney and should be reduced to a written policy and NDA, signed by all employees, contractors, and third parties receiving materials containing trade secrets (like licensees and publications ).
NOTE
CAUTION
Releasing the information to a party who is not under confi dentiality obligations can per manently destroy trade secret protection because that party can make the information pub lic, thereby disqualifying it from the trade secret category.
The core of a trade secret protection program is (i) to create the legal duty not to disclose confidential information in all relevant recipients; and (ii) to provide for physical protection (including software-based measures) of the trade secrets.
Your program should be specific to your company, but will probably include:
-
Creating the legal duty of confidentiality in recipients of confidential information
-
Physically protecting the confidential information
Creating the Legal Duty of Confidentiality
You need to be concerned with any parties who will have access to materials containing trade secrets. This includes:
-
Employees
-
Third parties, including independent contractors, licensees, investors, and others
Employees
Employees are the bricks in your information perimeter wall, so your defense should start there. While all employees have an implied duty at law to protect your confidential information, this implied duty should always be made explicit and explained to the employee with an NDA.
NOTE
CAUTION
It is equally important to protect your company against an employee's illegal ly importing trade secrets from previ ous employers . When recruiting a new employee from a competitor, take a look at the situation: does it seem pos sible that your competitor could con strue the hire as an effort to access its trade secrets? Did you conduct an actual search, or was this the only can didate looked at for the position?
NOTE
TIP
Your recruit should sign an agree ment that he will not be revealing any of his employer's proprietary information throughout the hiring process and the employment agreement should contain a rep resentation and warranty by the employee that he will not be using or bringing any intellectual property or proprietary informa tion to the new position.
Agreements
Every employee and contractor (including cleaning services) should sign a confidentiality/ non-disclosure agreement (NDA) promising not to disclose or make unauthorized use of trade secrets and to take actions to prevent disclosure or unauthorized use (See Chapter 4 for a sample NDA).
NOTE
CAUTION
The NDA may be incorporated into the employment agreement or separate, but if the employee is signing a confidentiality or non-compete agreement (see next para graph) as a stand-alone contract after he has been hired , the employer needs to offer something in exchange for the promises of confidentiality, such as $1.00.
Post-Employment Protection
What about after an employee leaves ? This is a somewhat murky area, because even though your NDA may prevent an ex-employee from making direct use of your trade secrets for a certain number of years, there is no way to prevent an ex-employee from having the benefit of working with those trade secrets. In other words, even though an ex-employee may be prohibited from creating a duplicate of a tool, he will probably be able to create a substitution with many of the same benefits as the tool.
Some states (California excepted, unless in connection with the sale of a business) allow employers to create an additional buffer by having employees sign a post-employment non-compete agreement. This agreement prevents the employee from leaving to work for a competitor or start a competing venture for a reasonable duration (one to two years, usually) and in a reasonable geographic area (worldwide is reasonable for game development).
Even if your state does not allow for post-employment non-compete agreements, your company should conduct exit interviews and obtain exit agreements. Exit interviews are meetings with departing employees in which you explain their obligation under the NDA not to use or disclose any trade secrets. Explain that they are not allowed to take or keep (for instance, in an e-mail account or on their home hard drive) any materials containing trade secrets. The degree of invasiveness the employer wishes to use depends on the relationship with the departing employee: some employers terminate e-mail and computer access the instant they hear (or tell) of an employee's departure , others physically examine anything the employee is taking out of the building, others rely on the employee's honor . Given the size and collegial nature of most development houses , it may not be a great idea to get invasive with your departing employees, since it could have the effect of alienating remaining employees, angering the departing one, and ensuring that in the future, everyone grabs what they want before informing the company of their departure.
NOTE
NOTE
All of this should be tempered by the reality that execution is far more important than informa tion, and that fluidity of informa tion is the rule rather than the exception. In other words, evalu ate the true potential damage of a situation before going ballistic .
The exit agreement provides a better alternative (see sample exit agreement at the end of this chapter). With an exit agreement, the departing employee promises that he is not taking any materials containing trade secrets. If the employee refuses (which would be hard to do without looking shady), then the employer is justified in taking more extreme measures.
Figure 5.2. The colonel's trade secret blend of herbs and spices is a mystery that haunts many.

Articulate and Reinforce
Most employees are not IP experts and will need some education in what a trade secret is, why it is important that efforts are made to maintain secrecy, and how to identify new trade secrets as they are created. Regarding the latter, think of your employees as (creative, well-paid, well-treated, highly trained) miners who must be shown an example or two of the gems for which they are digginga diamond in the rough is barely recognizable as a hillbilly cousin of the polished diamond.
Identify main categories of information that are likely to be trade secrets: source and object code, concepts, structures, diagrams, tools, design and technical documents, contract terms, new technology being developed, recruiting plans, and any other information that is not generally known or available and which would be valuable in the hands of a competitor. Ask employees to mark such items "CONFIDENTIAL AND PROPRIETARY" and send them to a designated supervisor and/or your attorney to see if the item qualifies as a trade secret. For information that you know qualifies for trade secret protection (like source code or design documents), it is important to plaster them with notices. A good idea is to embed the following notice on all media containing confidential information, labels, and in the header of each code module during development:
NOTE
[COMPANY NAME ] CONFIDENTIAL AND PROPRIETARY
THIS WORK CONTAINS VALUABLE CONFIDENTIAL AND PROPRIETARY INFORMATION. DISCLOSURE, USE OR REPRODUCTION WITHOUT THE WRITTEN AUTHORIZATION OF [COMPANY] IS PROHIBITED. THIS UNPUBLISHED WORK BY [COMPANY] IS PROTECTED BY THE LAWS OF THE UNITED STATES AND OTHER COUNTRIES . IF PUBLICATION OF THE WORK SHOULD OCCUR THE FOLLOWING NOTICE SHALL APPLY: "COPYRIGHT ( ) 20XX CLAIMANT ALL RIGHTS RESERVED."
If you are pressed for space, the following is acceptable:
NOTE
THIS IS AN UNPUBLISHED WORK CONTAINING [COMPANY] CONFIDENTIAL AND PROPRIETARY INFORMATION. IF PUBLICATION OCCURS, THE FOLLOWING NOTICE APPLIES: "COPYRIGHT ( ) 20XX [COMPANY] ALL RIGHTS RESERVED."
The distinction between "published" and "unpublished" software is discussed further in the "Protecting Your Assets: Enforcement: Notices" section.
NOTE
CAUTION
Over-protection is almost as dangerous as under-protection. A court may refuse to uphold confidential status for any company information if you designate all of it as confidential.
Third Parties
Releasing the information to a party who is not under confidentiality obligations can permanently destroy trade secret protection because that party can make the information public, thereby disqualifying it from the trade secret category.
Simply put: every third party receiving material containing trade secrets must sign an NDA obligating the recipient and all of its employees and contractors to protect the confidential material (see Chapter 4 for a sample NDA). When you sign an NDA with a company, trade secrets are the bulk of what is being protected. Even if you are not releasing hard assets like code, you may be disclosing protected information. Example: Developer A (a famous sim creator) wants to demo an RPG to Publisher B. Developer A cannot protect the idea of an RPG game because it is general ly known , but it may request an NDA to protect the fact that the company is developing an RPG. Competitive strategyin this case, a bet on the RPG marketcan qualify as a trade secret.
Physical Protection of Trade Secrets
-
Mark all trade secret materials and documents containing such materials "CONFIDENTIAL AND PROPRIETARY." Additional notices are highly recommended and are discussed below in the "Protecting Your Assets: Enforcement: Notices" section.
-
Confidential information should be shared on a "need to know" basisit is expected that sometimes this will be everyone in the company.
-
Use passwords and available security measures to protect computer files; keep hard materials (pitch bibles, printed copies of code or files) in a locked file cabinet or in a locked office.
-
Use encryption or other data-protection measures when e-mailing sensitive files and when FTP'ing files.
-
Maintain a clean-desk policy: no confidential materials should be left out while the employee is away from his desk.
-
Enforce a building-security policy that prevents unknown people from entering and circulating through the company. This can be as simple as stationing a receptionist in front of the door and insisting that all visitors be accompanied by an employee at all times.
-
Use common sense and a healthy dose of paranoia in public: don't discuss confidential matters in Starbucks, on a plane, elevator, restaurant, or any public place. This goes double for public places around trade shows and triple for trade show parties. Remind employees that an open bar is a loaded weapon aimed at them.
-
Review speeches employees are scheduled to deliver at public eventsyou might be surprised what can leak out this way.
-
Maintain a work/home separation where possible. Keep confidential material at the office as much as possible, and ask employees to guard the information when working away from the office.
If you believe it is warranted, additional measures may include:
-
Shredding discarded confidential documents
-
Reviewing the file logs for abnormal activity
Enforcing Trade Secret Rights
Violation of trade secrets is punishable by injunctions (preventing a party from doing or not doing something) and money damages. The amount of money damages is based on either the infringer's profits or the infringed party's losses. In really ugly cases, punitive damages (extra fines for behaving badly ) may be awarded.
Strengths and Weaknesses of Trade Secrets
Strengths of trade secrets are
-
Trade secret material can be made public in other forms and maintain its trade secret status. Example: even if a game's object code were somehow publicly released (and not simply distributed in a protected format), the source code would still be entitled to trade secret protection as long as it is not disclosed.
-
Unlike copyrights, they can protect ideas, concepts, and methods, not just a particular expression of those ideas, concepts, and methods. Example: A copyright can only protect the literal source code of a program; a trade secret can protect the ideas and methods underlying the program.
-
Unlike copyrights, trade secrets can also protect special features or components of released software (remember that trade secrets only offer protection for information kept secret and not publicly available), as long as the features are not readily reverse-engineerable.
-
Unlike copyrights and patents, trade secrets have no expiration date. As long as the information meets the qualifications, it is entitled to protection.
Weaknesses of the trade secret are
-
The trade secret only protects against disclosure by parties with a legal duty not to disclose (employees and third parties under NDA), making it vulnerable to loss of protected status through accidental disclosure.
-
Nothing that is reverse-engineerable can be protected as a trade secret.
-
Trade secrets do not defend against a third party's independently developing the same concept or product.
-
Maintaining a system of trade secrets can be a bit like herding squirrels and can become expensive and time consuming.
What Assets can a Trade Secret Protect?
Trade secrets can be used to protect almost anything a developer might create, including source code, object code, machine code, firmware, any concepts, ideas, methods, processes, or documents related to the creation of software or game concepts, including characters , storylines, drawings, business plans and methods, marketing plans or customer lists, databases, and so forth.
Basic Principles of Keeping Trade Secrets
-
Mark all trade secret materials CONFIDENTIAL AND PROPRIETARY.
-
Only show trade secret materials to those who have signed a non-disclosure agreement.
-
Keep trade secret material under lock and key, whether physical or electronic.
-
Obtain exit agreements from departing employees reminding them of their NDA duties .
Copyright
Copyrights are very important to developers, as they protect both software code and art (as well as many other important assets). Not only do you have a "natural copyright" in material you create (insufficient for most business purposes, discussed below in this section)meaning that your legal rights to the created material arise at the time of creationbut registering your copyright to ensure full legal benefits is reasonably inexpensive ($30 per copyright).
NOTE
CAUTION
Copyright registrations look pretty simple, but simple mistakes can make the registration ineffective , so have an IP attorney review your applications.
What is a Copyright?
As the name implies, a copyright gives the owner of a work of authorship, such as a play, musical composition, computer program, drawing, or business plan, the right to dictate how, whether, and for what benefit that work is to be copied . A copyright owner has the exclusive power to use, copy, make derivative works (like later versions of software), sell, or distribute that work. A copyright will protect a work owned by a corporation for 95 years from the date of publication or 120 years from the date of creation, whichever is shorter; for individuals, the copyright will last for the life of the creator plus 70 years.
Control Over Use of Work
The copyright protects the owner's ability to control the use of the work, giving the owner the exclusive right to reproduce, develop derivative works, distribute, sell, license, or publicly use, perform, or display the work. Because most software is distributed as a licensed product, and not actually sold to the customer, the copyright ownership and a good deal of control stays with the developer and/or publisher and any other parties whose copyrights were licensed for the making of the product, like an engine licensor . This gives those parties the ability to impose restrictions on the use of the game that would not be possible if they made an outright sale of a copy of the game to the customer.
Duplication
A purchaser of a copy of a software product would need the copyright owner's permission to make duplicates of the work (except for backups ). Duplication rights also prevent a purchaser from being able to make a verbatim copy of any source or object code; make duplicates of screens or audiovisual elements; or translate the code into another programming language. In limited situations, the purchaser may be prevented from using the code structure, sequence, and organization to create a substantially similar program.
Sale, License, and Distribution
Parties need the copyright owner's permission to distribute, license, or sell copies of the software to the public. The right to "license" the copyright is important because most software is licensed to end users, not actually "sold," because the owner can retain more control over the customer's use of the product. Technically, this means that copyright owner permission is required if you wanted to go to Best Buy, pick up 20 copies of a game and then resell them to your friends . Loan, rental, or lease for commercial purposes is also generally prohibited. The right to sell, license, or distribute is separate from the right to make copies of a work, meaning that the distributor may not be able to manufacture copies of the game; that right may be licensed to another party.
Derivative Works
The copyright also gives the owner exclusive rights to create derivative works , which are works that grow from and are closely related to the original work. This means that no other parties may modify, adapt, or change the copyrighted work for distribution to others except with permission of the owner. Examples of derivative works include: later software versions, translations/ localizations to other languages, ports to other platforms, sequels, projects in other media based on the original copyright, and user -generated "mods" (discussed below in the "Protecting Your Assets: Enforcement: Mods" section). Each of these derivative works needs its own protection, but the right to make them is controlled by the holder of the original copyright.
Copyrights are also available for compilations of other work where there is some level of authorship in the selection and placement of the work. For example, a collection of public domain games from the late 70s may be copyrighted. The compilation copyright would not grant the compiler a copyright to the games , only to that specific selection and order of the games, thus preventing another person from issuing the exact same collection.
Infringement
Unauthorized use of a copyrighted work is known as infringement and the owner may sue the infringer for damages (money) and/or an injunction (prohibiting the infringer from continuing the infringing activity).
Copyrights should be registered with the Copyright Office (www.copyright.gov) to have the greatest power against infringers. Without registration, every creator of a copyrightable work (who is not under a work-for-hire or invention assignment agreement) has what is known as a natural copyright in that work and may affix the notation to the work, but natural copyrights are difficult to prove and enforce against an infringer, and the Copyright Act awards greater damages for registered copyrights.
Idea versus Expression
Copyrights can be flimsy protection because, unlike trade secrets or patents, they can protect only the expression of an idea, not the idea itself. Methods, applied mathematical formulae, applied algorithmsnone of these can be protected with a copyright, only the actual code embodying those concepts.
The government's goal with this policy is to avoid monopolies in ideas except in extremely inventive works (patents). Copyrights do not grant their owners any control over the idea underlying the copyrighted work, only that particular manifestation of the idea. Taking the example of a compilation of late 70s games, the compilation copyright holder would be dismayed to find that he had no recourse against a copycat compilation containing 7 of the same 10 games. By slightly but meaningfully altering the copyrighted work, another party may obtain a separate copyright. Another example: a competitor who sees a design document for your next game may create a game copying most, if not all, of the ideas and concepts in the document (though none of the actual text or artwork).
A related difficulty with copyrighting software is what is known as merger . Merger is what is said to happen when the idea is inseparable from its expression, making the expression uncopyrightable. An idea is inseparable from its expression when there is really only one way to express it, meaning that giving someone a copyright on the expression would give them a copyright on the idea. Example: the forward-back-left-right buttons on a handheld controller cannot be copyrighted because they are inseparable from the function and purpose (to allow the user to manipulate a screen-based entity in various directions) of a controller.
There are limited ways to use copyrights as a form of idea protection in pitch meetings, for instance, which will be discussed in the following "Enforcing Copyrights" section.
How Do I Qualify for and Obtain Copyright Protection?
First, be sure that the company has taken the appropriate measures to gain clear title (ownership) to the work.
Next, analyze whether the material qualifies for a natural copyright:
-
The work must be fixed in a tangible medium from which the work can be retrieved (for example, a composition can be written or recorded, a computer program can be printed out or saved to disk).
-
The work must be original (created by the author). Note that original does not mean innovative, groundbreaking, unique, or worthy of note. Simply, something new.
-
The work must contain some level of creativity. Again, the bar is quite low: software documentation is considered creative enough to fit this criteria.
Works qualifying for copyright protection include almost every tangible, fixed expression of an idea with even a modicum of innovation. Aside from the more familiar realms like artistic works and computer programs, copyrights can protect seemingly un-creative works like sound effects and business documents like design and technical specifications, software documentation, budgets , and so forth.
Finally, consider federal registration of the copyright, which will provide you with maximum protection of your assets.
Figure 5.3. The Resident Evil property has spawned many derivative copy rights, shown in Figures 5.4 through 5.6.

Ensuring Company Ownership of Copyrights
Before a company thinks about protecting its copyrights, it needs to make sure that it owns them. The Copyright Act grants certain rights to the creator of a work, and an employer must be careful to structure its relationships with the creators (employees and contractors) for smooth transfer of all ownership rights to the employer.
NOTE
NOTE
Droit Morale. Some countries and a few jurisdictions in the U.S. give authors "moral rights" to prevent any modifi cation, distortion, or mutilation of their work that would be prejudicial to the author's honor or reputation (can you tell this idea originated in France?), even after it has been assigned. Be sure that these rights are waived in all assignment and license agreements.
Employees
Under the Copyright Act, an employer automatically owns most works created by employees acting within the scope of employment as a work made for hire . Employees should nonetheless sign an assignment of invention agreement (see Chapter 4, "Staffing Up") to avoid disputes over whether a worker is an employee and whether or not the work was created in the scope of employment. Furthermore, some forms of work may not qualify as a work for hire, and an assignment agreement will transfer ownership of these works to the employer.
Contractors
Unless a contractor signs an agreement to the contrary, work created under contract will probably be owned by the contractor, with the client having a license to use it, if anything. Needless to say, this is generally not a desirable outcome. To avoid it, have a contractor sign an agreement stating that (i) the work is a work made for hire and (ii) to the extent any work produced during the contractor's employment does not qualify as a work made for hire, the contractor assigns all other rights in and to the work to your company. The latter language is required because the "work made for hire" category is limited and sometimes your contractor will be creating work that does not quite fit the definition but for which you still require all rights. Software, for example, is generally outside of the work made for hire definition. IP 101
Figure 5.4. Books.

Licensees
What if you license technology to another company for incorporation into a game? Typically, the licensor retains all ownership to the licensed technology, and the licensee retains all ownership to the developed game except for the licensed technology. Some licensors insist on owning any modifications created by a licensee; some co-own it with an irrevocable, royalty-free , non-exclusive license to both parties; some licensors allow licensees to retain ownership of their modifications only to the extent separable from the licensed technology.
Federal Registration
Intelligent copyright management requires that a company register its copyrights. It's cheap ($30 per copyright), it's pretty easy, and it makes enforcing your rights against infringers much easier. The main benefits of federal registration are
-
While the natural copyright creates legal rights for owners who can prove that they created their work before an infringer, this is not always easy to prove. A registered copyright is proof of ownership.
-
The owner must first register the copyright in order to sue.
-
If the registration follows the original work's initial publication date by more than three months, the owner can only recover actual, provable damages (money) from the infringer.
-
Finally, and most important, you may only recover attorney's fees (which can pack a wal-lop in an infringement case) and statutory damages if your copyright was registered within three months of the work's initial publication. Statutory damages are automatically set money awards for infringement set out in the Copyright Act, currently $30,000 for every separate instance of ordinary infringement and $150,000 for every separate instance of willful infringement (more on this in the "Enforcing Copyrights" section).
Software Registration
You will need to file a copy of the work (and of each subsequent version or revision) with the Register, which will make it available to the public. For computer programs, there are two sets of rules.
For programs that do not contain trade secrets: you must send in one copy of identifying portions of the program (first 25 and last 25 pages of source code), or the whole megillah if your program is shorter than 50 pages.
For programs that contain trade secrets, you must send in a letter explaining your need to protect trade secret elements of the program, along with your choice of
-
First 25 and last 25 pages of source code with portions containing trade secrets blocked out
-
First 10 and last 10 pages of source code alone, with no blocked out portions
-
First 25 and last 25 pages of object code plus any 10 or more consecutive pages of source code, with no blocked out portions
-
For programs 50 pages or less in length, entire source code with trade secret portions blocked out
There are two limitations on your ability to block out code: (1) the blocked out portions must be proportionately less than the material remaining; and (2) the visible portion must represent an appreciable amount of original computer code.
Screen Displays
Fortunately, you don't have to register a separate copyright for every art asset in the game. The Copyright Office allows you to submit one registration for the entire computer program, including audiovisual displays, which protects the sound and visuals. You must identify the material you want to copyright, generally with a written synopsis of the game and the material you wish to copyright along with a half-inch VHS tape of all the audiovisual elements you want to protect.
Figure 5.5. A movie.

Notice
Put a copyright notice on everything. It is not required under U.S. law, but it is so simple and creates so many advantages that there is no reason not to. A copyright notice consists of the word "copyright" or the symbol, the owner's name, year(s) of publication, and the phrase "All rights reserved." This deters infringement on two counts: first, potential infringers will see that the owner understands copyright law and is likely to enforce its rights; and second, infringers will not be able to escape liability by arguing unknowing infringement.
NOTE
CAUTION
Because some countries do not recognize the legal validity of any notice not marked with the symbol , it will save administrative work later on to use the symbol. Notices embedded in code should use (C), since there is no ASCII symbol for copyright. Furthermore, many Latin American countries require the use of the phrase All Rights Reserved for an effective notice, so make your life easy and only use the legend " [Company] [years of copyright].All Rights Reserved"
Enforcing Copyrights
Before enforcing a copyright, it must be registered with the Copyright Office.
There are four remedies available in a copyright suit: injunctions (preventing the infringer from doing or not doing something), criminal penalties, impounding and destroying the infringing material, and money damages. Money damages are measured by actual damages, statutory (preset by law) damages, and attorney's fees, the latter two being available only to owners who registered the copyright within three months of initial publication.
A party can pursue actual or statutory damages, but not both. Actual damages are those losses that can be documented and proved (for example, if sales of an album were consistently 100,000 per month and dropped to 50,000 per month when a pirated version became available). Actual damages can be difficult to prove, making them a less popular choice except in cases where actual damages far exceed statutory damages. Statutory damages are the fines set by the Copyright Act for each individual act of infringement, $30,000 for ordinary infringement and $150,000 for willful infringement.
If you think your copyright has been infringed, you may prove your case by simply showing that
-
The alleged infringer had access to your copyrighted work; and
-
The allegedly infringing work is substantially similar to your work.
While it is not necessary to provide direct evidence of copying, proving any infringement other than literal copying can be time-consuming and costly to show in court. In response to this, owners of valuable and easily alterable copyrights like software have come up with a creative way to prove copying: they insert a few lines of garbage code. If the garbage code shows up in another party's work, it is significant evidence of copying.
Sometimes, what looks like infringement is actually what is known as fair use . Fair use enables limited use of copyrighted materials for purposes that are in the public interest such as teaching, satirizing, criticizing, or reporting news. Naturally, the "fair use exception," as this right is called, can be abused by parties seeking to cloak commerce in a greater social purpose. When assessing whether a particular situation qualifies for the fair use exception, the court will usually look to see if the use is commercial and whether it cannibalizes or diminishes the value of the copyright to its owner; if so, the court is unlikely to grant a fair use exception.
NOTE
TIP
Keep at least two hard copies of all releases and their documentation for the duration of their presence in the marketplace , in case they are needed for an infringement investigation or registrations.
Some examples of fair use: Example One: Showing a brief clip of GTA3 during a news clip on violence in games. Example Two: The fair use exception was denied to a Kinko's, who had been photocopying and selling copyrighted articles for college classes, in a case brought by publishers. The court found Kinko's guilty of infringement because even though the photocopied materials were being used in college classes, Kinko's use and copying was for commercial purposes.
Figure 5.6. Strategy guides.

Strengths and Weaknesses of Copyrights
Strengths of the copyright include:
-
It offers broad protection to many types of information and work.
-
It provides inexpensive protection.
-
Software can be registered with trade secret portions blocked out to maintain confidentiality.
Weaknesses of the copyright include:
-
Copyrights do not protect ideas, concepts, or methods, which are often key to software's value.
-
In most cases, copyrights only protect literal copying, enabling competitors to clone with impunity.
What Assets can a Copyright Protect?
Copyrights protect a broad array of developer assets, anything that can be fixed in a tangible medium (including computer media), covering everything from source, object, and machine code to automated databases (using some element of selection or arrangement of data to artwork to design docs, budgets, and business plans, and in some instances a program's structure, sequence, and organization and certain elements of the user interface.
Trademark
At one of the scariest meetings I've ever attended, a (Prada -clad) advertising guru leaned back in his (Aeron ) chair and decreed that a brand was "a set of characteristics united by a badge of reassurance." At first, this struck me as hilarious, but it sums up the reason that companies pour millions into their brands: to make a consumer feel safe purchasing the item, a feeling sometimes referred to as "goodwill" and tabulated on a balance sheet.
NOTE
NOTE
Trademarks, like GE for light bulbs , protect makers of goods; service- marks like GE Capital, protect providers of services. Because the law regarding the two is so similar, this section will refer only to trademarks but applies equally to servicemarks.
When you buy a Callaway golf club, you know that you are buying a carefully constructed , perimeter-weighted hunk of metal with a nice rubber grip. When you buy a Powerbar, you know you will be getting at least 100 percent of your RDA of niacin. But what if you couldn't be sure that the branded product you were buying had been made by the brand owner? Then you wouldn't be sure about that hunk of metal or the niacin content of your candy bar. That safe feeling would dissipate. Hence, trademarks.
Figure 5.7. Sample of rights flow in a video game.
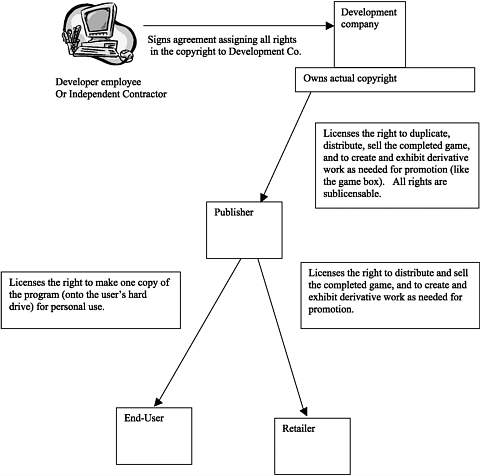
Figure 5.8. The trademark of status.

What is a Trademark?
A "mark" is any word, phrase, sound, or device; a "trademark" is a mark that identifies a product as being made by one company and not another. To qualify as a trademark, it must (i) identify the product and (ii) distinguish the product from competing products. This does not mean that the trademark need bear any descriptive relation to the actual good or servicein fact, the more descriptive the mark, the less likely the U.S. Patent and Trademark Office (USPTO) will allow it full trademark protection.
Examples of trademarks and the products they represent include the name "Nike," the "swoosh" logo representing athletic apparel and footwear, and the product name "Air Jordan," or the name "Sony" and the "? ? ? x " logo representing "PlayStation" and "PlayStation2" products.
If maintained correctly, trademarks do not expire.
What a Trademark Does and Does Not Protect
Trademarks protect the reputation of a brand by preventing other parties from using the trademark or one confusingly similar to it. While a mark may acquire some rights merely through use, trademarks must be registered with the USPTO to enjoy full legal rights. Unlike the Copyright Register, which functions more as a cataloguing entity keeping track of registered works, the USPTO rigorously examines every application to decide if it qualifies as a legitimate trademark and will usually fire back questions, required changes to the application, or a flat-out denial of registration.
NOTE
NOTE
Denials are most commonly due to the proposed mark being either too similar to an existing trademark (example: a "GameBox" console would probably be too similar to both "Xbox" and "GameCube") or too descriptive (exam ple:"Hardwood" for a flooring compa ny) and thus not trademarkable, both of which are discussed in this section.
The strength of a trademarkin other words, how likely a court is to find that similar marks infringe on the originaldepends on how distinctive the association between the mark and the described product is. The idea is that the more distinctive the trademark, the clearer it is to a court that any association between the product and the mark is the product of the company's efforts.
An inherently distinctive mark is one with no meaning within its product category. The three kinds of inherently distinctive marks are
-
Arbitrary marks. These are real words that have nothing to do with the product, like Snickers candy bars.
-
Fanciful marks. These are invented words, like Twix candy bars.
-
Suggestive marks. These marks suggest a characteristic of the product but do not describe it, like Mounds or Flake candy bars.
Descriptive marks are just that: they describe characteristics of the product. One reason there is no candy bar named "Super Chocolatey Goodness" is that it probably wouldn't qualify for trademark protection. Praise (Best Chocolate), geographic origin (Swiss Chocolate), and proper names (Cadbury Chocolate) are all considered descriptive. Descriptive marks may be placed in what is known as the secondary register in the hopes that they will one day ascend to trademark status if they acquire secondary meaning , in which people come to associate the descriptive mark with a particular company's products. Example: The descriptive mark "Kool" for menthol cigarettes eventually acquired secondary meaning sufficient for a trademark.
Trade dress . Trademarks can also protect trade dress, which is a fancy name for packaging that is ornamental, not functional. The distinctive Chanel No. 5 perfume bottle is a protected mark, as is Coca-Cola's hourglass-shaped bottle .
How Do I Qualify for and Obtain Trademark Protection?
As with copyrights, there are certain rights that arise from use of the mark, but you must register the property with a government agency to receive the fullest legal protection. You can register with the state in which you are operating, but that will only protect you against subsequent users of the name within that particular state. A federal trademark is effective throughout the 50 United States.
NOTE
NOTE
You may (and should) use the ¢ or SM symbols if you are claiming rights to a mark, but you may only use the sym bol, which indicates a federally regis tered mark, after the USPTO has actu ally registered your mark.
Table 5.2. Relevant Trademark and Servicemark Classes
| International Class Number | Products Included in Class |
|---|---|
| Trademarks | |
| 16 (paper) | Paper, cardboard and goods made from these materials, not included in other classes; printed matter; bookbinding material; photographs; stationery; adhesives for stationery or household purposes; artists ' materials; paint brushes; typewriters and office requisites (except furniture); instructional and teaching material (except apparatus); plastic materials for packaging (not included in other classes); playing cards; print-ers' type; printing blocks. |
| 21 (housewares and glass) | Household or kitchen utensils and containers (not of precious metal or coated therewith); combs and sponges ; brushes (except paint brushes); brush-making materials; articles for cleaning purposes; steel wool; un-worked or semi-worked glass (except glass used in building); glassware, porce-lain and earthenware not included in other classes. |
| 24 ( textiles ) | Textiles and textile goods, not included in other classes; bed and table covers. |
| 25 (clothing) | Clothing, footwear, headgear. |
| 28 (toys and playthings) | Games and playthings; gymnastic and sporting articles not included in other classes; decorations for Christmas trees. |
| Servicemarks | |
| 41 (education and entertainment) | Education; providing of training; entertainment; sporting and cultural activities. |
| 42 (computer, scientific, and legal) | Scientific and technological services and research and design relating thereto: industrial analysis and research services; design and development of computer hardware and software; legal services. |
Figure 5.9. The distinctive appear ance of the Chanel No. 5 bottle is protect ed "trade dress."

Rights Gained from Use
U.S. trademark law grants ownership to the first party to use an inherently distinctive mark in commerce, unlike other nations who afford ownership to the first party to register the mark (giving rise to piracy and strategy concerns discussed below in the following "Protecting Your Assets: Enforcement: International Considerations" section). The first user of a trademark gains certain rights as long as the use is in good faith, meaning that the user is unaware of any prior owners of the mark or one confusingly similar to it. These rights are very flimsy, however, unless the mark is then registered.
NOTE
TIP
The USPTO can extend the intent-to- use grace period up to 36 months if the owner shows good cause for the delay.
To register a mark with the USPTO, you must either show commercial use of the mark or file an intent-to-use application. An intent-to-use application confers the same privileges of registration, but the registration may be deemed abandoned (lapse) if the owner does not prove that it started using the mark in commerce within six months from the date of registration.
NOTE
NOTE
A goal of the trademark laws is to ensure that trademarks are actual ly used in commerce, not bought and "parked" to prevent other par ties from using them.To this end, trademarks are a use-it-or-lose-it proposition. Even after successful registration, a mark will be deemed abandoned if it is not used in commerce for two continuous years.
Federal Registration Process and Benefits
Federal trademarks are administered by the U.S. Patent and Trademark Office. A company gains the following legal benefits by registering a trademark in the Principal Register of the USPTO:
-
Evidence of ownership of the trademark.
-
The exclusive right to use the mark on or in connection with the goods or services set forth in the registration.
-
Inability of infringers to claim innocent infringement (the law presumes that all parties are aware of all valid federal trademarks).
-
The ability to use your U.S. registration as the basis for foreign registrations.
-
The ability to use the symbol after your mark.
-
The ability to prohibit the importation of any goods bearing the mark, and receipt of U.S. Customs assistance to enforce this prohibition (which is very helpful in anti-piracy efforts).
-
After five years of continuous use, a federally registered trademark is declared incontestable, making it unlikely that another party will be able to successfully challenge your ownership of the mark.
Registration
To register a trademark in the Principal Register of the USPTO, an application is submitted for one or more classes of goods and/or services. A word trademark (Teenage Mutant Ninja Turtles), design (the appearance of the character Donatello), and slogan (Turtle Power) are all considered separate trademarks and must be registered separately in all relevant classes. Because this can add up quickly, many companies only trademark their name, which protects against other parties using the same name on the same products in either plain text or as a logo. There are 42 classes of goods and services.
NOTE
TIP
Because the federal registration process can take several months, many companies elect to file a state trademark registration to provide interim protection.
The application includes a description and display of the mark if it is a drawing or particular font. The applications are not cheap ($335 in filing fees per class) and are of sufficient complexity that an attorney is used by most applicants . Trademarks must be renewed every 10 years except for the affidavit of use, which happens between years 5 and 6.
An additional expense is the trademark search, in which specialized companies comb through state, federal, and international (as required) trademark databases for identical or confusingly similar marks. They can also conduct what are known as common law searches to ferret out any parties using the mark who have not yet registered it. The common law search is worthwhile because those same parties can contest a registered trademark and may win if they can prove that they used the trademark first. The trademark search is worth the investment to prevent your company from building goodwill in a mark that it may have to abandon later. Furthermore, if you are sued for infringement, a trademark search record is good evidence that the infringement was unintentional.
Rejected?!
The most common reasons trademark examiners reject applications are
-
Likelihood of Confusion. If the examiner finds prior filed or registered marks that are either identical or confusingly similar in the Federal registry, it will reject for likelihood of confusion. To persuade the examiner that there is no likelihood of confusion, you must show that the mark is dissimilar, or if the marks are similar, that the respective goods or services in question are too different to be confused .
-
Mere Descriptiveness. If the examiner thinks that the mark is only descriptive of the product, it will deny you exclusive use of the mark. You may prevail if you can prove that your mark is recognized by the relevant public or consumer, or that your mark has acquired secondary meaning by being well known in its industry, through many years of operation, sales, and advertising.
-
Generic Word. If the examiner finds that your mark is a generic description of the product (instead of the source of the product, which is what a trademark protects), it will deny your application. Example: "Ball Games" would probably not be allowed for a sports equipment manufacturer, since it would prevent all others in that market from using the word "ball" in their marks.
-
Indefinite Description. This rejection has to do with the application, not the mark. Indefinite description means that you have not clearly and concisely identified the product or service to be protected. Fortunately, the examiners usually give you a suggested modification that would be acceptable to them.
Enforcing Trademarks
Trademark rights require some maintenance: registrations must be renewed every 10 years, and if a third party can prove your failure to use the mark for 2 continuous years, it may be deemed abandonment and given to another party. Furthermore, failure to police the use of your trademark may allow it to lapse into generic ( unprotected ) status. Aspirin was once a trademark but did not protect against generic use of its mark and lost its registration. Other trademarks that have become generic in daily useKleenex, Band -aid, Xeroxhave maintained their trademark status thanks to active monitoring and enforcement by their owners.
Figure 5.10. Protecting the Sims.

If you want to assert your trademark rights against an allegedly infringing party, you must be able to prove that the allegedly infringing mark is similar enough to yours that potential customers would likely be confused as to the source of the product. This is known as the likelihood of confu sion doctrine. This is simple enough in a pure counterfeit matter, but what of a situation where a party puts out a social simulation game called "The Syms" that looks similar, but not identical to the original trademark? Unfortunately, at that point you are looking at costly litigation where a court would have to decide whether or not the allegedly infringing mark creates a likelihood of confusion in the consumer's mind.
A court will look to the following factors in determining whether the two trademarks are confusingly similar:
-
The existence of actual confusion in the marketplace between the two marks
-
Similarity of the marks in terms of appearance, sound, and meaning
-
Similarity of the goods or services being identified by the two marks
-
The strength of the prior mark
-
The sophistication of the consumers who buy the particular products or services
-
The similarity of the channels of distribution of the products or services (that is, whether they are both sold in the same type of stores)
-
The degree of commercial competition between the two trademark users
-
The distinctiveness of the trademarks (that is, whether they are somewhat descriptive or arbitrary and fanciful)
Remedies available in a trademark infringement case include injunctions, impounding and destruction of infringing material, and monetary damages.
Strengths and Weaknesses of Trademarks
Strengths of the trademark include:
-
Prevents others from marketing or selling confusingly similar products or entertainment
-
Can protect character names and designs
Weaknesses of the trademark include:
-
Registration is costly, subject to maintenance and continued use
-
May not protect against sale of similar product under different mark
What Assets can a Trademark Protect?
Trademarks protect branding devices that establish a product as coming from your company and no other. Aside from your company name and the name of your games and technology, if you have a distinctive sound that plays at initialization of your game, a logo, a mascotall of these can be trademarked. The names, character designs, and slogans of original IP, characters, weapons, and other valuable marks that are vulnerable to exploitation by others (in other words, whatever could generate revenue through merchandising or entertainment) should be trademarked (example: Conan the Barbarian).
Patent
A patent is the boss of the IP world. It gives its owner a monopoly over a new technology, which can be a powerful lever against other companies. Unlike copyrights, the patent protects the ideas and even applied algorithms, not just the set of code used to implement them. Unlike trade secrets, a patent protects against a third party independently developing the same technology; with a patent, you can prevent any other third parties from using your technology.
The price an inventor pays for the exclusivity, which lasts 20 years for software, is that the patent is published and its inner workings made available for the public to see. There are three main ways a patent can backfire:
-
A competitor may read the patent application and be able to manipulate it to create a new technology that does not infringe, but still achieves the benefits of the patented advance.
-
The U.S. generally awards patents to the first inventor, not the first to file. A company may apply for and publish a patent only to have it overturned by another company who can prove they invented it first and had been using it under trade secret protection.
-
If a company is not proactive about its international patent portfolio , registration pirates may register the patents abroad, forcing the company to buy its patents back to do business abroad.
Because of their exclusionary nature, patents tended to have a bad name in the software development world, which emphasizes sharing and developing knowledge. The brouhaha over "business method" patents that many believe were not original enough to merit a monopoly, like Amazon's "One click" shopping or Priceline's binding bids, has contributed to this taint . For these reasons and the relatively high cost of applying for patents (at least $10,000), many software developers rely on trade secrets and copyrights to protect their source code, even for technologies like engines.
There are still many proponents for patenting software. They argue that:
-
There is no substitute for exclusive protection of the concepts, methods, and ideas, because the copyrights are easily violable.
-
A patent owner may always elect to give royalty-free licenses, but for business purposes should have the option of excluding competitors from using its innovation.
-
Compared with the cost of developing the asset, a patent is a cheap way to protect it.
-
Owning a patent still has cachet with investors, as it shows a legally responsible company that has a lock on a competitive advantage (depending, of course, on the quality of the patented technology.
-
Patents are a good defense against infringement suits from competitors, enabling a company to cross-sue and settle by the two parties agreeing to a royalty-free license of the oth-ers' patent.
Keep in mind that the animating principle behind patents is to award inventors and to spur greater advances by publishing the invention's design so that other parties may see it and benefit from the learning.
What is a Patent?
A patent is a property right granted by the USPTO that allows the inventor of a process or other invention to exclude others from making, using, or selling the invention in the United States. It also prohibits importing the invention into the United States. Once the patent is granted, the USPTO publishes the application so that other parties can see how the invention works. There are two major kinds of patents: design patents, which cover ornamental designs not essential to function like the iMac's CPU box, and utility patents, which protect useful inventions like the computer mouse (though the iMac's original hockey puck mouse would be eligible for a design patent). Utility patents are generally good for 20 years from the application date, design patents for 14 years.
Figure 5.11. The DualShock2 con troller contains patented vibration technology.

How Do I Qualify for and Obtain Patent Protection?
For an invention to qualify for a patent, it must fit the following four criteria by being:
-
Of patentable subject matter. There are four categories of patentable subject matter for utility patents: machines (like a Flowbie), processes (like treating a metal to make a new alloy), articles of manufacture (like a Phillips-head screwdriver), or composition of matter (like a new hair gel formula). A design patent need only be repeatable.
-
Useful and operational. The bar is low on what is considered useful, but any machines or design must work. A non-functioning design is not patentable.
-
Repeatable. The patented invention must be repeatable by a third party using the application as a source document.
-
Novel. Qualitatively, if software provides new uses, functions, or capabilities not found in prior art, it may qualify as sufficiently novel. Technically, an invention will be considered novel if it is not patented, known, described in a publication, or used by other parties in the United States or any other country either (i) before the date of invention; or (ii) more than one year prior to the patent application. Example: An inventor has proof that he invented a widget in Year One, but doesn't get around to patenting it until Year Four. If another party used or published a description of the widget in Year Two, the invention does not qualify as novel and is not eligible for a patent.
The invention must also not be an obvious extension of or cosmetic adjustment to prior technology.
Patents do not protect ideas or suggestions as such, only machines, processes, or other instrumentalities embodying those ideas or suggestions. Patents are not available for laws of physics or nature, or mathematical principles like pure algorithms. However, applying an algorithm to create a useful, tangible result is patentable subject matter. This means that patents may be sought for software instructing a processor to convert data into figures on a screen (like a console game).
The USPTO Patent Application
Acquiring a patent is a long, expensive process that often takes more than two years and costs over $10,000, including attorney's fees. The application fees alone range from $375 to $750. The patent application is very complex and requires significant specific knowledge, making it almost a requirement that an experienced patent attorney (preferably with experience in drafting the kind of patent you're after) prepare your application. The application will describe the invention and include some illustration. The claim of the patent is whatever elements you seek to have protected. Claims must be written according to very particular standards, and generally require the assistance of an attorney.
NOTE
NOTE
Unlike copyrights and trademarks, only the inventor may actually apply for the protection; the inventor may then assign the registration to a company who will own the patent.
NOTE
NOTE
If the code must be disclosed in the application, it will lose its trade secret protection, but can be protected with a copyright.
Some software applicants are eligible for a protected application that can maintain the trade secrecy of their source code (which is normally obviated by the publication of a patent). Where the code is not required to understand the invention, the applicant may be able to demonstrate the invention using pseudo code, block diagrams, and/or flow charts .
Table 5.3. Employee-Creator's Rights in Different Categories
| Copyrights | Trademark | Patent | Trade Secret | |
|---|---|---|---|---|
| Creator's | Creator owns copyright unless the work qualifies as a work for hire (created within scope of employment; subject of written agreement; falls within one of nine work categories). | Rights acquired through use, so generally only the company acquires rights. | Inventor owns the invention, but may be legally required to assign to employer in some situations. | Work created within scope of employment generally belongs to employer; otherwise , to employee. |
| Some categories ofwork are ineligible forwork for hire status | ||||
| Documents required for company to acquire ownership | Written, signed assignment of invention. WFH (employment agreement assumed) | None. WFH (employment agreement assumed) | Written, signed assignment of invention. WFH (employment agreement assumed) | Assignment of invention. WFH (employment agreement assumed) |
Provisional Patent ApplicationsIf you're not sure whether you want to invest all of the attorney's fees and your time into patenting a particular technology, you can buy yourself some time by filing what is known as a provisional application. The provisional application costs between $80 and $160 but most important, it does not require you to state claims for the patent or provide a prior art disclosure, which is where most of your and the attorney's time goes.The application gives you one year to file a full application, with the benefit of the early filing date.You may use the term "Patent Pending" for property under provisional application. Even better, your 20 year patent period only starts running from the date of your full application, so you don't lose any of the protected period. Howeverand this is importantthe provisional application does start the clock on your deadline for filing international applications under the Paris Convention (see the following "Protecting Your Assets: International Considerations" section). |
Searching for Prior Art
Prior art is patent terminology for previous inventions that affect your claim that the invention is novel and non-obvious. Example: If I get an idea that having adhesive on the back of notes in my notepad is a great idea and I should get a patent, a search for prior art would turn up Art Fry and Spencer Silverman's invention of the Post-it note. Insufficient prior art searches cause massive heartache and financial waste for inventors who invest in the application process only to be turned down by the patent examiner due to prior art. Prior art includes both patented and public domain technology, so it is advisable to hire a professional search firm that can search both categories rather than just searching the USPTO's online patent databases yourself.
NOTE
NOTE
Another wrinkle in the search for prior art is the ability of foreign applicants to rely on activities occurring in WTO signatory countries (after January 1, 1996) to prove dates of ownership.This means that a foreign party could contest your application by showing that they invented the technology before you in another country .There are restrictions on this situation arising, but if you think that you have competitors in WTO signatory countries, advise your search firm.
Prosecution
After a patent application has been submitted, a patent examiner is assigned to determine if the invention is patentable. During prosecution , the examiner works with the applicant to modify the application so that it may be patented. Because prosecution can take more than two years, many inventors will just start selling their invention with a "patent pending" notice. The danger, of course, is that the examiner will turn up prior art that your invention infringes after you have been selling your invention.
Figure 5.12. The patented invention of Velcro revolutionized kindergarten develop ment curricula everywhere.

Publication
A patent application may be published before it is accepted as a patent, but it will not be published for 18 months from date of application unless the applicant agrees otherwise. An applicant can also prevent the publication of the application by stating that foreign applications will not be filed (if this is indeed correct). Once the patent is issued, the application is published.
Competing Claims
Where two inventors independently create the same invention, the USPTO generally awards ownership to the "first to invent," not the "first to file." Therefore, documentation of invention processes becomes very valuable. Ongoing records of research and development progress should be kept and need to be signed and dated by the inventor as well as a witness not involved in the invention process. One exception to the "first to invent" rule is that if an inventor does not attempt to reduce his invention to practice within a reasonable amount of time after the invention, the patent may be awarded to the other party. "Reducing to practice" means either producing a working prototype or filing a patent application describing the invention in enough detail that a third party could reproduce it.
Enforcing Patents
Patent infringement is punishable by injunctions (forcing the infringer to do or not do something) and money damages in cases of innocent infringement, and attorney's fees and tripled damages if the infringement was willful.
Strengths and Weaknesses of Patents
Strengths of the patent are
-
The ability to protect ideas, methods, and concepts as well as their embodiments
-
The ability to prevent others from using the patented property, even if they developed it independently
Weaknesses of the patent are
-
It is a long, expensive, uncertain process.
-
There are pitfalls attached to the application process that require close monitoring by an experienced attorney.
-
The practice is controversial within the game development community.
What Assets can a Patent Protect?
Patents may protect many different aspects of a technology: program algorithms, display presentation, menu arrangement, editing functions, control functions, user interface features, compiling techniques, program languages, translation methods, utilities, formulae to control program execution or process data, and more.
| [ LiB ] |
EAN: 2147483647
Pages: 63