Windows Global Flags
| < Day Day Up > |
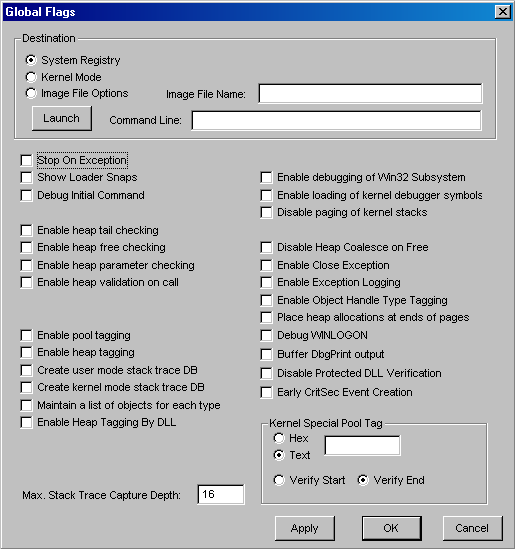
| Windows has a set of flags stored in a systemwide global variable named NtGlobalFlag that enable various internal debugging, tracing, and validation support in the operating system. The system variable NtGlobalFlag is initialized from the registry key HKLM\SYSTEM\CurrentControlSet\Control\Session Manager in the value GlobalFlag at system boot time. By default, this registry value is 0, so it's likely that on your systems, you're not using any global flags. In addition, each image has a set of global flags that also turn on internal tracing and validation code (although the bit layout of these flags is entirely different than the systemwide global flags). These flags aren't documented or supported for customer use, but they can be useful tools for exploring the internal operation of Windows. Fortunately, the Platform SDK and the debugging tools contain a utility named Gflags.exe that allows you to view and change the system global flags (either in the registry or in the running system) as well as image global flags. Gflags has both a command-line and a GUI interface. To see the command-line flags, type gflags /?. If you run the utility without any switches, the dialog box shown in Figure 3-28 is displayed. Figure 3-28. Setting system debugging options with Gflags
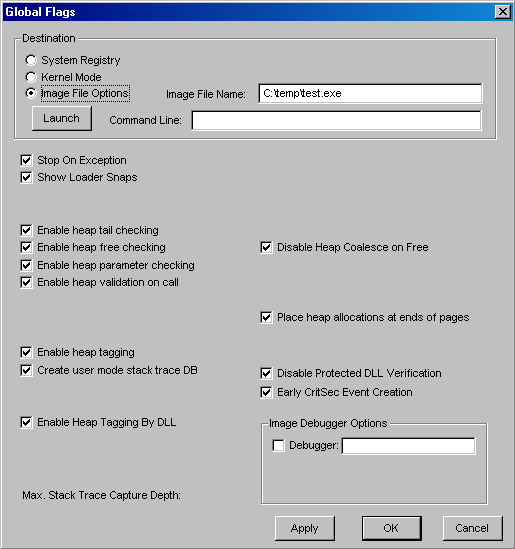
You can toggle between the settings in the registry (by clicking System Registry) and the current value of the variable in system memory (by clicking Kernel Mode). You must click the Apply button to make the changes. (You'll exit if you click the OK button.) Although you can change flag settings on a running system, most flags require a reboot to take effect, and there's no documentation on which flags do and which don't require rebooting. So when in doubt, reboot after changing a global flag. The Image File Options choice requires that you fill in the filename of a valid executable image. This option is used to change a set of global flags that apply to an individual image (rather than to the whole system). In Figure 3-29, notice that the flags are different than the operating system ones shown in Figure 3-28. Figure 3-29. Setting image global flags with Gflags
|
| < Day Day Up > |
EAN: 2147483647
Pages: 158