Security Management
| Security features must be tested early during the first rollout. Security is often overlooked in BI applications or is given superficial attention. Keep in mind that the data in the BI target databases is the same data contained in the operational systems. The common argument that security is not an issue for BI applications because the data is aggregated and summarized holds true only if detailed data is not available through drill-down features. In that case, the security measures for the BI data do not need to be as stringent as the security measures imposed on the same operational source data. However, most BI target databases store a fair amount of detailed data in addition to the summaries. Therefore, the security measures may be relaxed for some of the data but not for all. Security Measures for BI ApplicationsOrganizations that have strong security umbrellas on their mainframes are more likely to pay attention to security measures for their BI applications on multi- tier platforms. Organizations that have very lax security policies for their mainframes are usually prone to treating security casually for their BI applications as well. These organizations may unwittingly expose themselves to security breaches, especially if they plan to deliver information from the BI target databases over the Web. The following is an example of a security requirement that may need to be imposed on a BI application. Suppose an organization wants to give its distributors the ability to analyze their orders and shipments via a multidimensional BI application. To prevent a distributor from searching through other distributors ' sales data, there would have to be a mechanism for restricting each distributor's access to only the sales data pertaining to that particular distributor. In other words, some security lock is required to prevent access to the competitors ' sales data. This is not as straightforward as it sounds.
This example illustrates that the required security measures must be well considered and that the security features of the DBMS and of the access and analysis tools must be well understood and cross-tested. Complete reliance on one comprehensive security package that has the capability to implement any and all types of security measures is not a security solution because such a security package does not exist. To get the security you need, you will most likely have to implement a number of different security measures, including purchased security packages. However, be sure to minimize the number of security packages you implement because one of two things may happen.
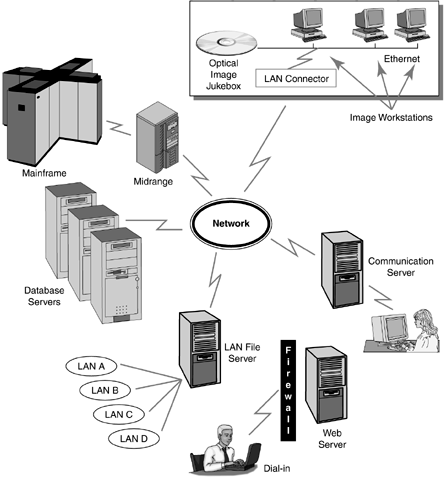
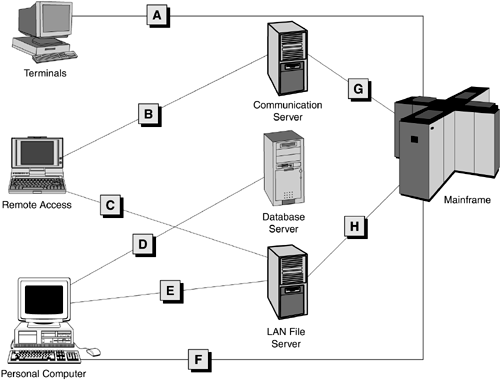
A number of organizations avoid this problem by adopting a single-sign-on scheme, which keeps the frustration level to a minimum but still allows tracking of any security breaches, albeit in a less sophisticated way. Security in a Multi-Tier EnvironmentImplementing security measures in a centralized environment is less complicated than in a multi-tier environment. In a centralized environment, all security measures can be implemented in one location because all the data is in one place. The goal of centralized security is "one entry point, one guard." It is much easier to guard a single door than multiple doors. In a BI decision-support environment, keeping all the data in one central place is not always feasible or desirable. If data needs to be stored in a distributed fashion in a multi-tier environment, implementing security measures becomes much more complicated. The list below briefly describes the steps involved.
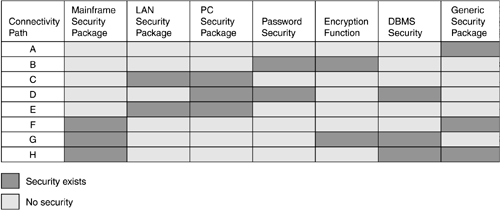
The security gap analysis matrix will help you identify where security is still needed and what type of security is needed. Keep in mind the following points:
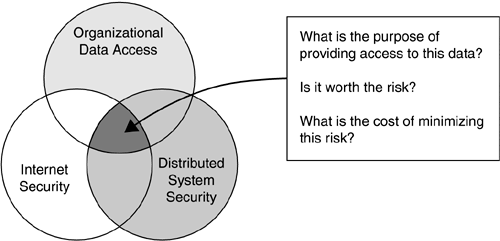
Security for Internet AccessThe Internet enables distribution of information worldwide, and the BI decision-support environment provides easy access to organizational data. Combining the two capabilities appears to be a giant leap forward for engaging in e-commerce. However, carefully consider the implications of combining these technologies before you decide to take the risk of potentially exposing sensitive organizational data (Figure 15.4). Figure 15.4. Security Considerations for Internet Access Many product vendors are enabling Web access to databases in general, and some vendors are allowing access to BI target databases in particular. This complicates the concerns for:
The bottom line on security is that you need to define your security requirements early in order to have time to consider and weigh all factors. If you opt to display the data on the Web, spend extra time and money on authentication and authorization of internal staff and external customers. If you are transmitting sensitive data to and from external customers, consider investing in encryption and decryption software.
|
EAN: 2147483647
Pages: 202