Aftermath... The Investigation
Aftermath The Investigation
It was my eighth year working for the agency; my last seven years had been spent investigating the illegal munitions trading with a particular focus on activities within South Africa and some of the small islands surrounding it, including the Republic of Mauritius. A number of months ago, I was given two case files from a small town in Miami, Florida. The first case file was a missing person s file, with a concluding section that the person s body had been found several weeks later, after the initial claim. The second file was the murder file of Demetri Fernandez, an individual who had apparently been in college with the John Doe from the former case and had seemingly taken him under his wing.
So what? I quizzed the agency clerk who handed me the case folders “ It s just another small town murder from a state I have no jurisdiction in. And then I saw the all too familiar name Knuth .
During the autopsy of Demetri Fernandez, a small crumpled piece of paper was found approximately half way down the throat of Fernandez “ presumably swallowed by Fernandez during his last moments alive . The case file of Demetri Fernandez, and more importantly its reference to the ellusive Knuth, connected the case to an ongoing investigation into a potential fraud that was currently being orchestrated within a group , apparently also associated with an individual known as Knuth, and a bank in the Republic of Mauritius.
Thanks to a number of phone intercepts from another agency, we have been able to track a number within the Republic of Mauritius, dialed by an individual posing as Mr. Knuth on a regular basis. Due to a lack of voice samples from Knuth, we have not, as of yet, been able to corroborate whether the voice on the end of the line is indeed Knuth. After examining a number of cases to which Knuth has been some how attached, it is apparent that Knuth has a thing for leveraging flaws in computer and telephone technologies to either protect his identity, or augment his activities. The John Doe friend of Demetri Fernandez (a John Doe originally, though a name of Charlos was recently made available) was somewhat of a computer genius.
Laura Fernandez, the wife of Demetri who was fortunately not at their apartment at the time of Demetri s death, reported that Charlos had in the past boasted to her that he had taken a $3,000 bounty in return for the retrieval of e- mails sent to the e-mail account of his customer s spouse. Although this is the only case documented in the evidence files provided to me “ I am betting that the activities of young Charlos went much further; dead techies associated with the name Knuth have become all too familiar.
Given the timeline, it is my approximation that Charlos was one of the first hackers who was hired by Knuth. His case is particularly interesting, mostly because he died. This indicates that young Charlos knew something about Knuth which Knuth really didn t want to get out. Further to this, Charlos seemingly told his friend Demetri and viola! “ two stiffs in a morgue. In the other, more recent cases, which I have either investigated, or analyzed the investigations of, Knuth appears to have only used techies who were unwitting agents . In other words, they had been told a cover story, like they were helping the community, or that they were legally helping in legitimate tests of computer networks. It was my original belief that Knuth had learned his lesson after the Charlos incident and was now using wholly unwitting agents “ but no. His most recent acquisition has been a phone hacker (or phone phreaker) based in Iceland, known to his friends and by those in the computer underground as The Don .
The folks over at behavioral science have put together an adversary profile of The Don using some new techniques they have been researching . I believe that their findings are indicative of the kinds of people whom Knuth appears to be acquiring the aid of. My summary of their profile and some of the information provided to me by the behavioural science unit (via a fairly poor quality fax) are as follows .
Background: The following model is used by the team at the agencies behavioral science unit to gage various adversarial preferences to risk based upon the individual's placement in what we refer to as the "Cyber food chain". Note that the data presented in this metric is based upon the current case involving the telephone switch in Egypt.
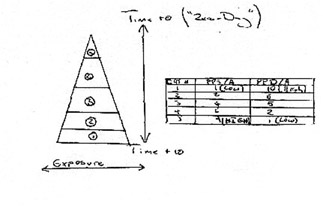
Behavioral Model
From what I have understood from the behavioral science guys, the driving principle behind this particular metric is that the newer a vulnerability, the more likely an attacker is to succeed in their attack “ seemingly obvious to most. The disclosure pyramid is split into five sections. The highest section in the pyramid represents the point at which a vulnerability is discovered and a low vulnerability exposure (in terms of individuals that know about the issue). From what I have read, the second level is typically populated by those in the immediate environment of the individual who discovered the vulnerability, the width of the pyramid increasing, and with it, and the number of individuals who know of the vulnerability. Typically, the lowest point will represent at which information pertaining to vulnerability is considered to be within the public domain. The table to the right of the pyramid (which thanks to our fax has not come out too clearly), attributes various typical adversarial preferences to risk based upon an adversaries typical placing within the pyramid.
For my own notes, I ve redrawn the table:
New Table
| Pyramid Category Value | Perceived Probability Of Success Given Attempt (PP(S) / A) | Perceived Probability Of Detection Given Attempt (PP(D) / A) |
|---|---|---|
| 1 | 1 (Low) | 10 (High) |
| 2 | 2 | 6 |
| 3 | 4 | 5 |
| 4 | 6 | 2 |
| 5 | 9 (High) | 1 (Low) |
The fax continued .
Through assessing an adversary's typical placing in the pyramid, we believe that we are able to gauge an adversary's typical preferences to risk in a given attack scenario. If we are able to observe an adversary's placement within the pyramid, we are also able to hypothesize about what their technological resources may consist of. We are then able to hypothesize how said adversary may reduce the risks associated with an attack through use of the resources to which they have access. In addition to reducing variables such as their perceived probability of detection given attempt variables known as attack inhibitors, they are able to increase variables such as their perceived probability of success given attack attempt and in some cases, yield given attack success and attempt. Although the pyramid metric and its associated scores serve well as a visual aid, the scores are somewhat arbitrary and their weight is on a sliding scale. This is because the risks associated with an attack are almost always a function of the target being attacked something not considered by the pyramid metric. In the case of "The Don", although we consider that his average placement within the disclosure pyramid to be between three and four (indicating a high level of technological resource and typically a high tolerance to attack inhibitors due to his ability to counter inhibitors through the use of his vast resources); in the case of the phone switch in Mauritius the need to use a new or technologically complex attack was uncalled for. In other words due to a lack of attack inhibitors, the only real draw on resource was the acquisition of a stolen cellular phone in order to reduce The Don's perceived probability of detection given attempt and perceived probability of attribution given detection (PP(D)/A && PP(A)/D). To summarize, The Don appears to be both well-resourced and highly skilled. This gives him an extremely high tolerance to any inhibitors introduced into an attack situation and makes for a highly capable adversary. As for his motivation from what we have seen, The Don was traditionally driven by his thrill for the kill, or in this case, the thrill for the hack. Of late, he appears to have demanded an increasingly higher fee for his efforts this only makes for a more motivated and increasingly well resourced adversary. The Don is certainly a force not to be taken lightly. End transmit
Although we remain unaware of The Don and Knuth s true identities; thanks to The Don s phone forwarding antics and our capability to intercept communications in that part of the world, our agency is now able to monitor Knuth s every telephone call to that number. The Don doesn t know it, but he may have just helped us catch one of the most prolific criminals I have encountered in a long while.
EAN: N/A
Pages: 105